Instruction to candidates
- This paper consists of two sections A and B.
- Answer all the questions in section A.
- Answer question 16 and any other three questions from section B.
- All answers should be written in the space provided in the question paper.
- Candidates should answer the questions in English.
For Examiner’s Use Only
|
Section |
Question Number |
Candidate’s Score |
|
A |
1-15 |
|
|
B |
16 |
|
|
17 |
|
|
|
18 |
|
|
|
19 |
|
|
|
20 |
|
|
|
Total |
|
|

QUESTIONS
SECTION A (40 MARKS)
Answer ALL questions in the spaces provided
- Differentiate between embedded computer and dedicated computer (2 marks)
- The current monitor technology uses LED back lit technology. Give two advantages of using TFT monitors over CRT monitors (2 marks)
- A Form four student wants to send a large document to a printer.
- State the name for the area of memory that the document is sent to immediately from RAM. (1 mark)
- As the printer runs out of paper during printing, the operating system sends a signal back to the computer to stop temporarily. Name this function of the operating system (1 mark)
-
- Differentiate between a flash memory and compact disk as used in computer storage devices. (2 marks)
- People like using DVDs overcompact disks yet they are of the same physical size. State threereasons that justifies this. (3 marks)
- For a monitor to display images, it must be connected through video port to a video adapter or controller mounted on the mother board. What is the role of a video adapter? (2 marks)
- Name four categories of input devices (2 marks)
- State any two physical measures taken to protect a computer laboratory from unauthorized access. (2 marks)
- Most word processors have some automated features such as word wrap and type over modes. Describe these features (2 marks)
- Differentiate between proofreading and formatting a document as used in word processing (2 marks)
- Most computerized systems in different organizations face a lot of unauthorized access such as Eavesdropping, Surveillanceand Industrial espionage. State a control measure against each vice. (3 marks)
- A world wide web is a vast virtual space in the internet where information is made available such as web portals and blogs. Different between a web portal and a blog. (2 marks)
- Differentiate between filtering and hiding of rows/columns as used in spreadsheets (2 marks)
- Industrial plants use computer systems in different ways such as Computer Aided design, manufacturing, Simulation and process control. Explain how computers are used in the mentioned areas above. (4 marks)
-
- Differentiate between Job displacement and Job replacement. (2 marks)
- State three advantages of using automated production in manufacturing plants. (3 marks)
- Due to high demand and dynamic nature of computers and information systems, there is need for qualified computer trainers. What are the roles of computer trainers? (3 marks)
SECTION B (60 MARKS)
Answer question 16 (compulsory) and any other THREE questions from this section.
-
- By use of a Flowchart construct, differentiate between a while loop and FOR loop (4 marks)
- Study this flowchart and use it to answer the questions that follow
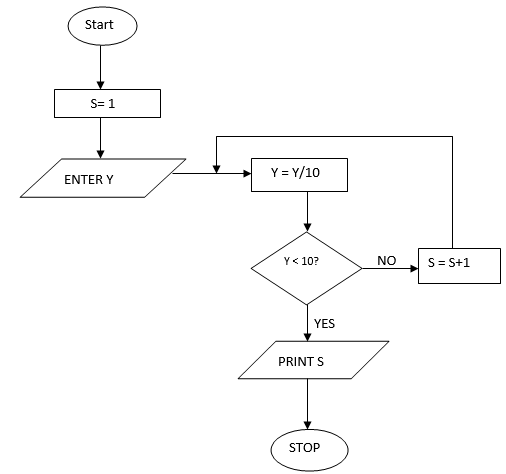
- Give the expected output from the flowchart when the value of Y is: (4 marks)
- 48
- 800
- Write the pseudocode that can be used to create a program represented by the above flowchart. (7 marks)
-
- Differentiate between a primary key and a foreign key as used in databases. (2 marks)
- State four factors to be considered when designing a good database (4 marks)
- Explain the use of each of the following field datatypes as used in database (3 marks)
- OLE object
- Lookup wizard
- Memo
- Kibet has been experiencing a lot of problems in his computer. As a result, he decided to format his computer and re-installed a new operating system.
- What is formatting in relation to the above context (2 marks)
- What precaution must Kibet observe before formatting his computer (1 mark)
- You are required to purchase an operating system. State three factors that you should consider before acquiring the software. (3 marks)
-
- Define the following terms as used in networking (3 marks)
- Broadband
- Bandwidth
- Multiplexing
- List four elements of networking (2 marks)
- Most institutions are moving towards the use of fibre optic cables. State three reasons why fibre optic is preferred (3marks)
- Differentiate between Hub and Bridge as used in networking. (2 marks)
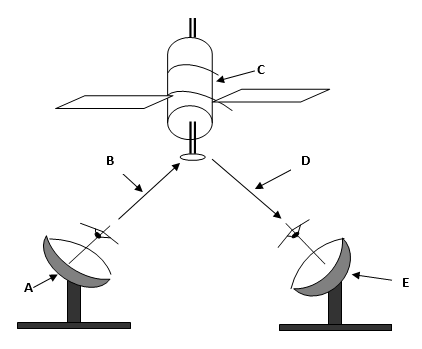
- The diagram below represents a signal transmission from point A to point E. Name the parts labeled A, B, C, D, E (5 marks)
- Define the following terms as used in networking (3 marks)
-
- Binary systems have been used to develop most electronic devices. Give three advantages of using binary. (3 marks)
- Convert the following number systems (4 marks)
- 37.62510 to binary
- BCD.EF16 to Octal
- Using twos complement, perform the following arithmetic operation leaving your answer in decimal notation. (4 marks)
3910 – 1910 - A student was developing a file. List any four attributes that the operating system will assign the file (2 marks)
-
- A system analyst in Changamwe preferred using phased changeover to implement a new system. State three reasons for this preference. (3 marks)
- State three reasons why an organization may change an information system. (3 marks)
- Different students were asked to state the characteristics of a system. The responses were:
- They are holistic
- They are open or closed systems
- They have a boundary and environment.
Explain each of the above responses. (3 marks)
- Explain the following data collection stages as used in data processing (3 marks)
- Data preparation
- Media conversion
- Input validation
- State three ways a data entry clerk may use to reduce threats to data integrity (3 marks)

MARKING SCHEME
- Differentiate between embedded computer and dedicated computer (2 mrks)
- Embedded computers are special purpose computer used inside another device and usually dedicated to specific functions.
- Dedicated computer is a general purpose computer designed to perform a specific task.
- The current monitor technology use LED back lit technology. Give two advantages of using TFT monitors over CRT monitors (2 mrks)
- Images formed in TFT do not suffer from angle distortion
- TFT have low power consumption than CRT
- TFT have a higher resolution than CRT
- A Form four student wants to send a large document to a printer.
- State the name for the area of memory that the document is sent to immediately from RAM(2 mrk)
- Input buffer
- As the printer runs out of paper during printing, the operating system sends a signal back to the computer to stop temporarily. Name this function of the operating system (1 mrk)
- Interrupt handling
- State the name for the area of memory that the document is sent to immediately from RAM(2 mrk)
-
- Differentiate between a flash memory and compact disk as used in computer storage devices (2 mrks)
Flash memory
Compact disk
Solid state device
Optical media
Plugs directly to the USB port
Requires a disk drive
Fast access of data
Slow access of data
Uses circuitry access
Has moveable read and write head
- People like using a DVD over a compact disk yet they are of the same physical size, state three reasons that justifies this (3 mrks)
- A DVD has a higher storage capacity
- A DVD offers a better sound and picture quality than a CD
- Differentiate between a flash memory and compact disk as used in computer storage devices (2 mrks)
- For a monitor to display images, it must be connected through video port to a video adapter or controller mounted on the mother board. What is the role of a video adapter (2 mrks)
- It determines the resolution and clarity of the monitor
- Name four categories of input devices (2 mrks)
- Keying in devices
- Pointing devices
- Scanning devices
- Automated method
- Name any two physical measures taken to protect a computer lab from unauthorized access.(2 mrks)
- Burglar proofing the room
- Use of alarms
- Use of padlocks
- Use of special cards
- Employing security guards
- Most word processors have some automated features such as word wrap and type over modes. Describe these features (2 mrks)
- A wordwrap is a feature that enables the cursor to move automatically to the start of a new line/page
- Type over mode (overwrite mode) enables the user to edit an individual character of a word in a text document
- Differentiate between proofreading and formatting a document as used in word processing (2 mrks)
- Proofreading is the process of checking whether the document has typographical or grammatical errors
- Formatting a document refers to enhancing the appearance of a document to be attractive and appealing to the eye of the reader
- Most computerized systems in different organizations face a lot of unauthorized access such as Eavesdropping, Surveillance and Industrial espionage. State a control measure against each vice (3 mrks)
- Eavesdropping: refers to tapping or listening into a communication channels to get information
- Surveillance: Refers to monitoring use of computer system and networks using background programs such as spyware and cookies
- Industrial espionage: it involves spying on competitor to get information that can be used to cripple the competitor
- A world wide web is a vast virtual space in the internet where information is made available such as web portals and blogs. Different between a web portal and a blog (2 mrks)
- Web portal: it is a specialised websites that offer restricted services such as e-learning, searching, e-mail, and sports to registered user updates, financial news and links to selected websites.
- Blog: It is a website that contains personal information which can easily be updated
- Differentiate between filtering and hiding of rows/columns as used in spreadsheets (2 mrks)
- Filtering is the process of finding and working with a subset of related worksheet.this will display only the rows that meet the condition or criteria specified.
- Hiding columns: it the process of making a columnl not be shown on the display or printed when you print the worksheet. The column is not deleted.
- Industrial plants use computer systems in different ways such as Computer Aided design, manufacturing, Simulation and process control. Explain how computers are used in the mentioned areas above (4 mrks)
- Computer Aided design: it is an integrated system that allows products that have been designed using design application software
- Simulation: it allows some activities that would otherwise be expensive and dangerous in real life to be put under test
- Process control: it refers to the use of a computer system to control an ongoing physical process.
-
- Differentiate between Job displacement and Job replacement (2 mrks)
- Job replacement implies that the employees who are computer illiterate lose their jobs and replaced by computer literate people
- Job displacement is where the computer illiterate workers are moved from a department with computers to another place which does not require computer literacy.
- State three advantages of using automated production in manufacturing plants (3 mrks)
- Increased efficiency due to the balancing of workload and production capacity
- Improved customer service
- Efficient utilization of resources such as raw materials
- Differentiate between Job displacement and Job replacement (2 mrks)
- Due to high demand and dynamic nature of computers and information systems, there is need for qualified computer trainers are required. What are the roles of computer trainers(3 mrks)
- Training people on how to use a computer and various application programs
- Developing training reference materials
- Guide learners on how to acquire knowledge through carrying out research
- Advising the learners on the best career opportunities in the field of ICT
- Preparing learners for ICT examinations
-
- By use of a Flowchart construct, differentiate between a while loop and Repeat… Until loop (4 mrks)
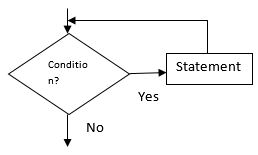
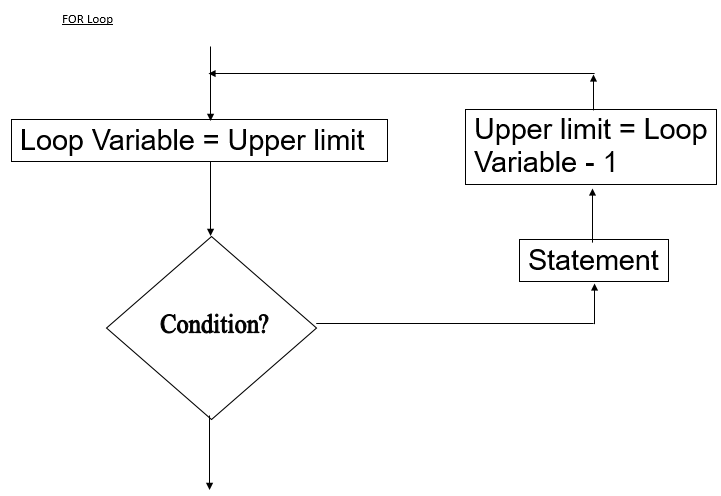
- In the WHILE Loop, the condition is tested before the execution of statements while REPEAT loop statements are executed before the condition is tested
- In WHILE loop, statements are executed until the condition becomes FALSE the you exit while in REPEAT loop, you exit when the statement is true
- In WHILE loop,statements may exit without any statement being executed while in REPEAT loop atleast one execution of statements must be done
- Study this flowchart and use it to answer questions that follows

- Give the expected output from the flowchart when the value of Y is (4 marks)
- 48 S=1
Y=4.8 - 800
S=2
Y=8
- 48 S=1
- Write the pseudocode that can be used to create a program represented by the above flowchart (7 marks)
START
S=1
READ Y
REPEAT
Y=Y/10
S=S+1
UNTIL Y<10
PRINT S
STOP
- Give the expected output from the flowchart when the value of Y is (4 marks)
- By use of a Flowchart construct, differentiate between a while loop and Repeat… Until loop (4 mrks)
-
- Differentiate between a primary key and a foreign key as used in Database (2 mrks)
- Primary key is a special index that enforces uniqueness in a table
- Foreign key is a field in a table that matches the primary field in another table
- State four factors to be considered when designing a good database (4 mrks)
- Carefully study the requirements of the user in order to define all the data inputs, outputs and relationships required
- Design a draft database on the paper to determine the number of files or tables required
- Divided the information into separate fields, records and tables to allow flexibility in manipulating the database
- Define a field for each table that will be used to identify each record uniquely
- Give the most important fields the first priority
- Design data entry forms needed for the database
- Explain the use of each of the following field data types as used in database (3 mrks)
- OLE object
- It is used for storing graphical objects such as pictures
- Look up wizard
- It is a field displays the data as a drop down list so that the user can select the desired value from the list
- Memo
- It is a field in database that contain alphanumeric data and can accommodate a maximum of 32000 characters
- OLE object
- Kibet has been experiencing a lot of problems in his computer. As a result, he decided to format his computer and re-installed a new operating system.
- What is Formatting in relation to the above context (2 mrks)
- It is the process of preparing a new storage media by imprinting empty sectors and tracts on the surface of the disk so that the operating system can recognize and make it accessible
- What precaution must kibet observe before formatting his computer (1 mrk)
- Make a backup of all the documents to avoid losing them
- What is Formatting in relation to the above context (2 mrks)
- You are required to purchase an operating system. State three factors that you should consider before acquiring the software (3 mrks)
- Hardware configuration
- The type of computer in terms of of size and make
- The application software intended for the computer
- User-friendliness
- Documenmtation available
- Cost of the operating system
- Reliability and security provided by the operating system
- Differentiate between a primary key and a foreign key as used in Database (2 mrks)
-
- Define the following terms as used in networking (3 mrks
- Broadband
- An analog signal sent over the transmission medium using a particular frequency
- Bandwidth
- It is the maximum amount of data that a transmission medium can carry at any one time
- Multiplexing
- It is the process of sending multiple data signals over the same medium
- Broadband
- List Four elements of networking (2 mrks)
- data communication media
- communication devices
- networking software
- data signals
- Most institutions are moving towards the use of Fibre optic cables. State three reasons why Fibre optic is preferred (3 mrks)
- It is immune to interference and eavesdropping
- It is fast and support high bandwidth
- Large distance can be covered because it has low attenuation
- Can be used in hazardous places (highly flammable) because they do not generate electrical signal it is smaller and lighter than the copper cable hence ideal for space limited situation
- Differentiate between a Hub and a Bridge as used in Networking (2 mrks)
- A Hub is a component that connects computers on a network and is able to relay signals from one computer to another on the same network.
- A Bridge selectively determines the appropriate network segment for which a message is meant for delivery through address filtering
- Define the following terms as used in networking (3 mrks
- The diagram below represents the a signal transmission from point A to point E. Name the parts labeled A, B, C, D, E (5 mrks)
- Binary systems has been used to develop most electronic devices. Give three advantages of using binary (3 mrks)
- It is difficult to develop devices that can understand or process natural languages directly it is easier to develop electrical circuits based on binary ON/OFF
- All forms of data can be represented in binary system format
- Binary devices are more reliable
- They became smaller in size
- They use less energy
- Convert the following number systems (4 mrks)
- 37.62510 to binary
Using long division get the binary of 3710 =1001012
get the binary of the decimal by multiplying repeatedly by two i.e 0.62510=0.1012
Add the binary of the whole number and the decimal
1001012+0.1012=100101.1012
HEXADECIMAL
B
C
D
E
F
BINARY
1011
1100
1101
1110
1111
To octal 5715.7368Group In terms of three 101,111,001,101.111,011,110
- 37.62510 to binary
- Using twos complement, perform the following arithmetic opration leaving your answer in decimal notation (4 mrks)
3910 – 1910- using long division get the binary of:
3910 = 1001112
1910= 100112
write the binary of 1910 in 8-bits 1910= 000100112
ones complement of the binary of 1910=11101100
twos complement ones complement =11101101
add the binary of 3910 to the twos complement of 1910
11101101
+0100111
(1)00010100 ignore the overflow
(1x24)+(1x22)=2010
- using long division get the binary of:
- A MOKASA student was developing a file. List any four attributes that the student must consider in the development process (2 mrks)
- Key field
- The data type
- The lenghth of each field
- Back up and recovery strategies
- Binary systems has been used to develop most electronic devices. Give three advantages of using binary (3 mrks)
-
- A system analyst in changamwe prefers using phased change over to implement a new system. State three reasons for this preference (3 mrks)
- To enable the analyst to test the system in phases
- The operations and results of both systems are compare and evaluated
- Errors can be identified and corrected before the old system is abandoned
- State three reasons why an organization may change an information system (3 mrks)
- New opportunities
- Incase of problems in the current system
- New directives
- Different students were asked to state the characteristics of a system. The responses were as follows:
- They are holistic
- They are open or closed systems
- They have a boundary and environment.
- Explain each of the above responses (3 mrks)
- Holistic system: the different components of a system are grouped together to make a whole
- Open or Closed: open system receives input from and gives out to the environment and can adopt to changes in the environment.
- Boundary and Environment: it is a space within which the component operates.
- Explain the following data collection stages as used in data processing (3 mrks)
- Data preparation
- It is the process of converting data from source documents to machine readable format
- Media conversion
- This is where the data is converted from one medium to another
- Input validation
- It is the process taken during data entry to prevent wrong data from being processed by subjecting to validity checks
- Data preparation
- State three ways a data entry clerk may use to reduce the threat to data integrity (3 mrks)
- Back up data
- Control access to data by enforcing security measures
- Design user interfaces that minimizes chances of invalid data entry
- Using error detection and correction software when transmitting data
- Using devices that directly capture data from the source
- A system analyst in changamwe prefers using phased change over to implement a new system. State three reasons for this preference (3 mrks)
Download Computer Studies Paper 1 Questions and Answers - Nyeri Mocks 2021 Exams.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

