SECTION A (40 Marks)
Answer all the questions in this section
- Differentiate between master file and transaction file. (2 mark)
- Give two reasons why smaller computers like laptops tend to be more expensive than desktop computers. (2marks)
- List two disadvantages of using traditional file management method. (3marks)
- List three sources of graphics that can be used in Microsoft word. (3marks)
- Mention two things that are likely to cause eye strains. (2marks)
- State two reasons why magnetic tapes are not commonly used as computer data storage medium today. (2marks)
- Explain the difference between Gas Plasma Display and Liquid Crystal display Monitors. (2marks)
- Differentiate between logical and syntax errors encountered in programming. (2marks)
- What is a computational error? Give an example to illustrate. (2marks)
- Anne was working on her computer studies project. She was worried of the media to use for storing her data.She settled on a media that used serial file organization.
- How are files organized on a storage medium using this method? (2marks)
- List two advantages offered by this type of file organization. (2marks)
- Define the following terms in relation to computer security: (4marks)
- Data Encryption
- Firewall
- State what is meant by each of the following and give an example of where each is used.
- Magnetic Ink Character Recognition (MICR) (1 mark)
- Optical mark reader (OMR) (1 mark)
- Describe the term data integrity. (2 marks)
- State four situations in which data may lose integrity. (2 marks)
- State three advantages of using robots in manufacturing of goods. (3marks)
- State three ways in which ICT can be used in shipping control. (3 marks)
SECTION B (60 Marks)
Answer Question 16(Compulsory) and any other three questions in this section
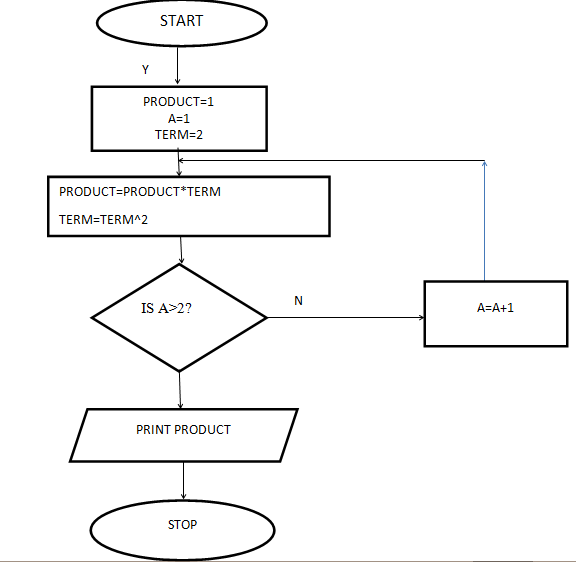
- Study the flowchart below and answer the questions that follow.
- State the main type of control structure used in the flowchart. (1 mark)
- Dry run the flowchart and give the expected output. (5 marks)
- What will be the value of product when printed in the following flow chart? Show how you arrive at your answer. (5 marks)
- Explain what happens when the expression A = A+1 is changed to A = A-1 (2 marks)
- Give two benefits of structured programming (2 marks)
- Study the flowchart below and answer the questions that follow.
- State three reasons why it is difficult to detect and prevent computer crimes. (3marks)
- State three characteristics of a suitable password. (3marks)
- What is a spyware? (2marks)
- A school intends to set up an e-learning system. List three problems that are likely to be encountered (3marks)
- What is a search engine? (1mark)
- Give two examples of search engine. (1mark)
- Differentiate between internet and intranet. (2marks)
- State three standard data coding schemes used in computing and electronic systems. (3marks)
- Convert each of the following numbers:
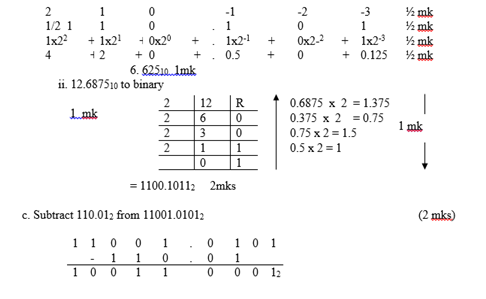
110.1012 to decimal (3marks)
12.687510 to binary (3marks) - Subtract 110.012 from 11001.01012 (2marks)
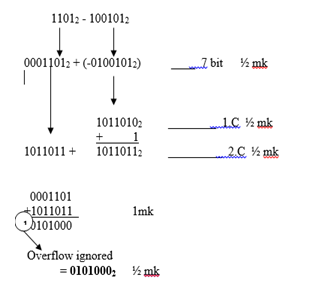
- Using seven-bit twos compliment, perform the following binary arithmetic leaving the answer in binary notation.
11012 - 1001012 (4marks)
- Give three benefits of using a DTP software in publishing over a Word processor (3 marks)
- Robots are introduced in a factory which makes car engines. Mention three ways this could affect the workers. (3 marks
- Name any two computer related courses that are offered at public universities in Kenya. (1 mark)
- List two duties performed by each of the following personnel.
- Database administrator (2 marks)
- Computer trainer. (2 marks)
- Briefly describe the two types of spreadsheets (4 marks)
- Define a system. (1mark)
- Explain system entropy. (1mark)
- Describe three circumstances that can lead to development of new information system. (3marks)
- Distinguish parallel changes over from straight change over as used in system implementation.(2marks)
- Explain two fact finding methods used during system analysis and design. (2 marks)
- Name any two types of cables used in data communication (2 marks)
- State four differences between LAN and WAN (4 marks)

MARKING SCHEME
- Differentiate between master file and transaction file. (1mk)
Master file contains relatively permanent data while transaction file contain data that frequently change.
- Give two reasons why smaller computers like laptops tend to be more expensive than desktop computers. (2mks)
They are portable.
Technology behind it is very expensive
Does not rely on constant power/rechargeable battery
- List two disadvantages of using traditional file management method.(3mks)
Information takes up much space.
It is not easy to update or modify information.
It is slow in accessing of data.
It is prone to errors.
It does not guarantee security.
- List three sources of graphics that can be used in Microsoft word. (3mks)
Microsoft clip gallery.
Import from another file.
Drawing using drawing tools available in M/s word.
Digital camera
- Mention two things that are likely to cause eye strains. (2mks)
Poor lighting of the room.
Bright monitors.
Flickering monitors.
very bright wall paints that reflects much light.
- State two reasons why magnetic tapes are not commonly used as computer data storage medium today. (2mks)
Are slow when retrieving data.(serial access)
Do not fully use their recording surface due to inter-record gaps.
Limited storage capacity
Not supported by modern devices
- LCD – monitor that are a special liquid called crystal.
Gas plasma – Resemble LCD but use gas instead of liquid crystal. Images displayed in gas plasma do not suffer from angle distortion.
- Logical errors
Not detectable by the translation
Syntax
Emanate from improper use of language rules such as grammatical mistakes.
- Errors that occur when an arithmetic operation does not produce expected result.
Overflow (illustrate using ones or twos complement)
Underflow
Truncation
Rounding errors.
- Anne was working on her computer studies project.She was worried of the media to use for storing her data.She settled on a media that used Serial file organization.
- How are files organized on a storage medium using this method?
Serial file are stored and accessed one after another on a storage medium. - List two advantages offered by this type of file organization.
Advantages – simple, cheap.
Data Encryption
This is where data that is on transit is mixed up in a form that only the sender and receiver can be able to understand.
Firewall
A hardware or software system that filters the data and information exchanged between different networks by enforcing the lost networks access control policy.
- How are files organized on a storage medium using this method?
- Magnetic Ink Character Recognition (MICR) (1 mark)
Are devices used to read characters written using magnetic ink example used in reading cheques at the bank - Optical Mark Reader (OMR) (1 mark)
A device that use light to read presence or absence of data done through shading on special forms (OMR forms).
A device thatis used for reading multiple choice options in form like KCPE examination, lotteries
- Magnetic Ink Character Recognition (MICR) (1 mark)
- Describe the term data integrity. (2 marks)
Refers to the accuracy and completeness of data entered in a computer or received from the information system - State four situations in which data may lose integrity. (2 marks)
During data entry and there are no validation rules to control data
During data entry and data is misread
Technical threats like malware and power surge can change data
Failure to use devices that capture data directly.
Failure to secure the data
Poorly designed interface for data capture
- Describe the term data integrity. (2 marks)
- State three advantages of using robots in manufacturing of goods. (3 marks)
Have the ability to perform tasks that are unpleasant, dangerous or complex and tedious to assign to human beings
Are more accurate
Are diligent, i.e. can work without getting tired etc NB. Do not accept answers like effective, efficient - State three ways in which ICT can be used in shipping control. (3 marks)
(Avoid statements like efficiency, effective etc. these are too general. Look for specific terms. Award marks for full mention of ICT advantage + shipping control.)
Run the inventory systems accurately
Enhance communication thro Networking the operations
Accurate Navigation of the ships (GPS)
s keeping database for the firm
SECTION B (60 Marks)
Answer question 15 and any other three questions
- State the main type of control structure used in the flowchart (1 mark)
Iteration (looping) (DENY REPEAT UNTIL OR WHILE DO) - Dry run the above flowchart (5 marks)
PRODUCT
A
TERM
1
1
2
2
2
4
8
3
16
128=FINAL PRODUCT
256
- What will be the value of product when printed in the following flow chart? Show how you arrive at your answer
- State the main type of control structure used in the flowchart (1 mark)
- Explain what happens when the expression A=A+1 is changed to A =A-1 (2 marks)
Indefinite loop –execution will not come to an end since the value of A will never be greater 2 - Give two benefits of structured programming
highly legible code
easy maintenance
re-usability of code
faster program development
easy to identify errors and debug
each sub program can be tested separately
- State three reasons why it is difficult to detect and prevent computer crimes.(3mks)
Crimes are very complex and it will take a long time before anyone discovers it.
Its difficult to find ideal trail of evidence leading to the guilty party.
No witness to computer crimes.
Not many people in the management and law enforcement know enough about technology to help prevent computer crimes. - State three characteristics of a suitable password. (3mks)
Should be unique.
Should be easy to remember.
Should not be too long or too short.
Should not be obvious.
Should not give a hint. - What is a spyware? (2mks)
It is a computer program that obtains information from a user’s computer without the user’s knowledge or consent. - A school intends to setup an e-learning system, list three problems that are likely to be encountered. (3mks)
Lack of capital.
Lack of skilled manpower.
Spread of computer viruses.
Availability of pornographic materials and literature to students from the internet. - What is a search engine? (1mk)
A special program that collects and stores links to information websites allowing users to search its database for them. - Give two examples of search engines. (1mk)
Google
Yahoo
Bing - Differentiate between internet and intranet. (2mks)
Internet refers to interconnection of many large networks to enable different computers world-wide to communicate.
Intranet is the interconnection of computers within an organisation to form a network.
- State three reasons why it is difficult to detect and prevent computer crimes.(3mks)
- (BCD) Binary Coded Decimal
(ASCII) – American Standard Code for Information Interchange
(EBCDIC) – Extended Binary Coded Decimal Interchange Code - i. 110.1012to decimal
- (BCD) Binary Coded Decimal
- Give three benefits of using a DTP software in publishing over a word processor
Every item on the page is contained in layered frame and can be edited and formatted independently
Content can be contained in a single frame or threaded between several frames
Frames need not flow in logical order, eg content on page one can be continued on page 8
In most DTPs, special pages known as master pages are used to set common layout which may be repeated on several pages e.g logo, page numbers
Provide wide ranges of templates
Multiple stories from different authors can be handled with ease
Publication artworks can be produced in a form suitable for commercial printing - Robots are introduced into a factory which makes car engines. Describe three ways this could affect the workers. (3 marks)
job replacement
job creation
job displacement - Name any two computer related courses that are offered at public universities in Kenya. (1 mark)
BSC Computer Science
BSC Information Technology
BSC Hardware and Software Engineering - List two duties performed by the following personnel
- database administrator (2 marks)
Designing and developing database applications.
Setting up security measures needed to control access to data and information.
Keeping databases up to date by adding new records, modifying or deleting unnecessary records. - Computer trainer (2 marks)
Training people on how to use the computer and application programs.
Developing training reference materials.
Guide learners on how to acquire knowledge
Preparing learners for ICT exams
- database administrator (2 marks)
- Describe two types of spreadsheets
Manual: traditional type, used by book keepers as ledger book with many sheets of ppers divided into rows and columns on which figures are entered manually using a pen
Electronic: it is prepared using a computer program enabling the user to enter values in rows and columns using the keyboard and enables one to manipulate them using a formulA
- Give three benefits of using a DTP software in publishing over a word processor
- Define a system. (1mk)
Is a set of organized components which intersect in a given environment and within a specific boundary to achieve collective goals. - Explain system entropy. (1mk)
It means decay where a system slowly becomes useless to the user due to improvement in user requirements.
- Define a system. (1mk)
- State three circumstances that can lead to development of new information systems. (3mks)
New opportunity.
Problems in the existing systems
Directives from higher authority - Distinguish parallel changes over from straight change over as used in system implementation. (2mks)
Parallel changeover both old and new systems are run concurrently for sometimes until users have confidence in the new system while in the straight the old system is stopped and discarded and the new system comes into use immediately. - Discuss two fact finding methods. (4mks)
Interviews-it is carried out with relevant stakeholders in order to get views about the current system.
Questionnaires-special purposes document that allows a person to collect information and opinions from people who receive and respond to it.
Observation –Requires the observer to participate or watch closely as a person performs actives in order to learn about the system.
Automated method-Used when one wants to get actual data which may be difficult to get through interview, observation or questionnaires. - Name any two types of cables used in data communication (2 marks)
Twisted pair
Coaxial
Fibre optic
Open wire - State four differences between LAN and WAN (4 marks)
LAN
WAN
This is a network localized to a room or a building
It’s a world wide network(Global network)
Cheaper to set up than WAN
Expensive to setup and run
Faster data communication
Slower in data communication
Better data security
Less data security
Download COMPUTER PAPER 1 - 2019 LAINAKU JOINT MOCK EVALUATION EXAMINATION.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students