SECTION A (40 MARKS)
Attempt ALL questions from this section
- What is meant by Data Communication Equipment (DCE)? (1 mark)
- List threeexamples of Data Communication Equipment. (3 marks)
-
- Name three types of graphics used in a word processor (3 marks)
- Distinguish between subscript and section breaks (2 marks)
- List any three protocols used in sending and receiving of emails (3 Marks)
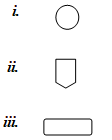
- State the use of each of the following flowchart symbols (3 marks)
- State any two techniques used by a network administrator to detect and prevent computer crimes. (2marks)
- State two transmission media used in wireless transmission (2 marks)
- With the aid of a diagram describe the Hierarchical Database Model ( 2 marks)
- List any three factors that should be considered when developing a database application and give reasons why each should be considered. (3 marks)
- Nameany three types of validation checks during data entry (3 marks)
-
- Differentiate between primary key andindex key as used in databases. (2 marks)
- Differentiate between hardware and software portability. (2 marks)
- State three ways in which computer virus infection can be prevented otherthan through restricting the usage of removable storage media. (3 marks)
- State two advantages ofreal time data processing mode. (2 marks)
- State two roles of an information system (2 marks)
- A company in town wishes to link its offices together; the linking may be through wireless or fibre optic network media.State two benefits that the company would gain from the use of metropolitan area network (MAN) (2 marks)
SECTION B (60 MARKS)
Answer question 16 and any other THREE questions from this section B
-
- State fourguidelines followed when designing a flowchart. (2 marks)
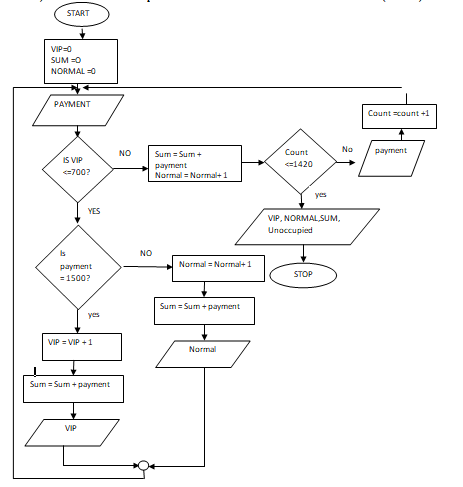
- A concert was organized in a hall with a capacity of 1500 people. The first 700 people to buy thetickets at ksh. 1500 were reserved a seat at the VIP section while the others who bought their tickets at ksh. 1000 sat at normal hall outside the VIP section. Assuming that only 1420 tickets were sold;
- Write a program pseudocode that would be used to determine the sitting arrangements of ticket holders i.e VIP or Normal, the number of VIP, Normal and Unoccupied seats and finally display the total amount of money collected from the concert. (6 marks)
- Draw a flowchart for the pseudocode above (7 marks)
-
- Differentiate between a selectquery and actionquery as used in databases. (2 marks)
- Explain four elements of database (4 marks)
- Explain the use of each of the following field properties as used in databases (3 marks)
- Validation rule
- Input mask
- Indexed
- Kiprono has been experiencing a lot of problems in his computer while using it. As a result, he was advised to do the following in order to avoid the problems.
- Compress the disk files
- Defragment the disk.
Explain the difference between the two terms above (2 marks)
- Differentiate between Multi-user operating system and Multithreading operating system. (2 marks)
- State two roles of a programmer in system development life cycle (2 marks)
-
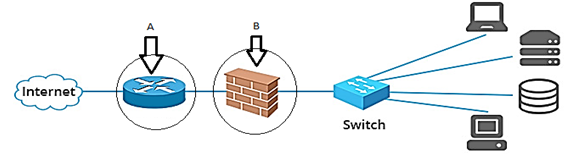
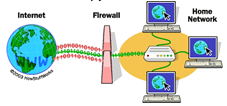
- The diagram below shows a network arrangement that includes a network security feature to protect data and information. Use it to answers the questions that follow.
- The networking device labeled A is used to connect computers to a WAN (Internet). Name the deviceused for this purpose. (1 mark)
- The part labeled B is a security feature used to protect data traffic in the network. Identifyand explainthe function of this part. (2 marks)
- Define a networknode. (1 mark)
- State any twofunctions of a network operating system. (2 marks)
- The internet has been embraced as great a great resource for information and a variety of applications. State two ways in which a book publisher can make use of the internet (2marks)
- Name and explaintwotypes of twisted pair cable used in data transmission. (3 marks)
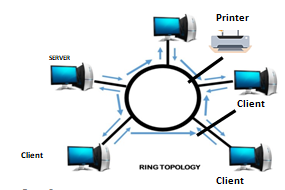
- With aid of a labeled diagram, describe ring network topology; statingone disadvantage of such network. (4 marks)
- The diagram below shows a network arrangement that includes a network security feature to protect data and information. Use it to answers the questions that follow.
-
- Convert each of the following numbers to decimal equivalent; given that the left most bit is a sign bit.
- 0101011 (2 marks)
- 111110101 (2 marks)
- Differentiate between enhanced BCD and ASCII-8coding scheme of representing data in computers. (2 marks)
- Compute the following binary arithmetic expressions.
- 1010.101 + 11.011 (2 marks)
- 1010.101 - 11.011 (2 marks)
- Convert 0.4210 to 6-bit binary notation. (2 marks)
- Using 8-bit twos complementation, perform the following binary operation. (3 marks)
1110102 - 2710
- Convert each of the following numbers to decimal equivalent; given that the left most bit is a sign bit.
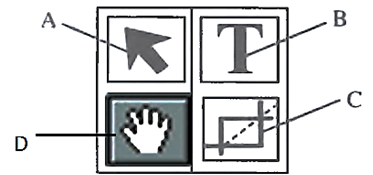
- The figure below is a toolbar for a DTP
- Name and state the functions of the tools labeled A, B, C and D. (4marks)
- Using relevant examples give four advantages of using desktop publishing software. (4 marks)
- State fouradvantages of automated production. (4 marks)
- Most industries use computers for process control. Give any threebenefits of this.(3marks)

MARKING SCHEME
- what is meant by Data Communication Equipment (2 marks)
Devices that facilitate the movement of data along a communication channel in a network. - List three examples of Data Communication Equipment. (3 marks)
Modem
Hub
Switch
Brouter
Router
Bridge - Name three types of graphics used in a word processor (3 marks)
Drawing objects
Pictures
Templates- Distinguish between subscript, superscript and section breaks: (3 marks)
A subscript is a number, figure, symbol, or indicator that appears smaller than the normal line of type and is set slightly lower it. e.g. 10th
A superscript is a number, figure, symbol, or indicator that appears smaller than the normal line of type and is set slightly above it. e.g. 10th
Section breaks are used in word processing to create various layouts in a document. It can be within a page or between pages. Common breaks used are section breaks, page breaks or column breaks.
- Distinguish between subscript, superscript and section breaks: (3 marks)
- List any three protocols used in sending and receiving of emails (3 Marks)
Post office protocol, POP
Simple Mail Transfer Protocol, SMTP
Multi Purpose Internet Mail Protocol (MIME)
- State two roles of a programmer in system development life cycle. (2 marks)
Write program codes
To test the system
- State the use of each of the following flowchart symbols (3 marks)
- connector, links two parts of a flow chart together
- off page connector
- Process box. Shows the activities in a box
- State any two techniques used by a network administrator to detect and prevent computer crimes. (2 marks)
Audit trails
Intruder detection systems/softwares
- State two transmission media used in wireless transmission (2 marks)
Radio waves
Infra Red
- the aid of a diagram describe the Hierarchical Database Model ( 2 marks)
In a hierarchical model, records are arranged in an inverted tree. A child record can have only one parent record but a parent record can have one or more child records.
- List any three factors that should be considered when developing a database application and give reasons why each should be considered. (3 marks)
Size of the database
Security features
Cost of developing and maintenance
- Name three types of validation checks during data entry (3 marks)
Range validation
Date validation
Data type validation - Differentiate between primary key and index key (2 marks)
Primary key identifies records uniquely in a table while an index key is a field chosen to order and match/locate record addresses in an index table.- Differentiate between hardware and software portability (2 marks)
Hardware portability refers to the ability of a hardware device to fit/work in different computers while software portability refers to the ability of a program/software to operate on different platforms (hardware and operating systems) - State three ways in which computer virus infection can be prevented other through restricting the usage of removable storage media (3 marks)
Creating firewalls via anti-viruses
Disconnecting computers from the Internet
- Differentiate between hardware and software portability (2 marks)
- State two advantages of real time data processing mode. (2 marks)
Fast and instant processing
Good for instant decision making
- State two roles of an information system (2 marks)
Creates operational excellence
Assists managers in decision making
- A company in town wishes to link its offices together; the linking may be through wireless or fibre optic network media. State two benefits that the company would gain from the use of metropolitan area network (MAN) (2 marks)
MANs are private networks hence confidentiality is a plus
Being private means firewalls can built to resist various security threats
- State Two rules followed when designing a Flowchart (2 marks)
- There should be only one entry/starting point and one exit point
- Use correct symbols at each stage in the flowchart
- The logical flow should be clearly shown using arrows
A concert was organized in a hall with a capacity of 1500 people. The first 700 people to buy the tickets at ksh. 1500 were reserved a seat at the VIP section while the others who bought their tickets at ksh. 1000 sat at normal hall outside the VIP section. Assuming that only 1420 tickets were sold;
- Write a program pseudocode that would be used to determine the sitting arrangements of ticket holders i.e VIP or Normal, the number of VIP, Normal and Unoccupied seats and finally dispay the total amount of money collected from the concert.
START
VIP=0
SUM=0
NORMAL= 0
FOR COUNT =1 TO 1420 DO
INPUT payment
WHILE VIP<700 DO
IF payment = 1500 THEN
VIP = VIP + 1
SUM = SUM + Payment
PRINT “ VIP ticket sold for seat No.” VIP
ELSE
SUM = SUM + payment
Normal = normal +1
ENDFOR
Unoccupied = 1500 – (VIP + Normal)
PRINT “ TOTAL No. of VIP seats:”VIP
PRINT “ TOTAL No. of Normal seats:”Normal
PRINT “ Unoccupied seats:”Unoccupied
STOP 6 Marks - Draw a fwochart for the pseudocode above (7 marks)
- Differentiate between a select querry and Action query as used in Data base (2 mrks)
A Select query is a query that asks a question about the data stored in your tables and returns a result set in the form of a datasheet—without changing the data.
An action query is a query that copies or makes changes to or moves many records in just one operation. - Explain four elements of database (4 marks)
tables
queries
forms
macros
programming module - Explain the use of each of the following field properties as used in data bases (3 marks)
Validation rule
It allows you to create an expression or a formula that will test data when being entered into the field.
It automatically rejects faulty/flawed entries, e.g., entering very large or very small figures in the Age or Salary fields.
Input mask
Lets you define a pre-formatted pattern for the entry of data into a Date or a Text field. The data in that field must conform to a pattern.
Required.
It controls the entry of important fields.
When this option is set to YES, an entry must be made within that field, i.e., it ensures that the field is not left blank. - Kiprono has been experiencing a lot of problems in his computer while he is using it. As a result he was advised to do the following in order to avoid the problems.
Compress the disk files
Defragment the disk.
Explain the difference between the two terms above (2 marks)
Disk compression refers to the process of squeezing files and folders in a storage media to create more space for data storage
Disk defragmentor refers to the process of re-arranging of scattered files and folders in noncontiguous sectors of a disk to create a space and fast reading of data - Differentiate between Multi-user operating system and Multithreading operating system (2 marks)
Amulti-useroperatingsystemis one that allows formultiple users to usethe same computer at the same time and/or differenttimes.In computernetworking, amulti-usersystem is a term commonlyusedto definea computer capable of allowingmultipleusers to connect to anetwork. Theoperatingsystem must makesurethat the requirements of thevarious users arebalanced, and that each of theprograms theyareusinghas sufficient and separate resources so that a problem with one user doesn'taffect the entire communityof users.
These areOperatingsystems that allow differentparts ofasoftwareprogram to run concurrently. Multithreadingis the abilityof aprogram oran operatingsystem to manageits use bymorethan oneuser atatime and toeven managemultiple requestsbythe same userwithouthavingtohave multiple copies ofthe program runningin the computer. Each user request foraprogram or system serviceis kept track of as a threadwith a separateidentity. - State two roles of a programmer in system development life cycle (2 marks)
Design and code applications solving business issues.
Develop diagrams and flow charts on computer operation process.
Develop, test and analyze programming applications.
Determine, develop and document software specifications throughout production lifecycle.
Analyze and rectify software errors and present precise status reports on time.
Build and develop applications using computer languages such as XTML, JAVA, ABAP, Visual Basic and C++.
Upgrade and offer patches to existing computer systems.
Develop technical documentation to support application maintenance.
support programmers and analysts to conceptualize and develop new software programs.
Plan software development lifecycle phases.
Prepare and document software specifications and requirements.
Research and document software users’ requirements.
Guide re-engineering of applications responding to customer requests.
Offer input to SDLC documentation specialists and edit documentation.
Resolve programming issues by applying problem solving skills.
- Differentiate between a select querry and Action query as used in Data base (2 mrks)
- The diagram below shows a network arrangement that includes a network security feature to protect data and information. Use it to answers the questions that follow
- The networking device labeled A is used to connect computers to a WAN (Internet). Name the deviceused for this purpose. (1 mark)
Router/Proxy/gateway - The part labeled B is a security feature used to protect incoming data traffic in the network. Identifyand explainthe function of this part. (2 marks)
- ===Firewall is a hardware device or software system that filters the data & information exchanged between different networks by enforcing the access control policy of the host network.
A firewall monitors & controls access to or from protected networks. People (remote users) who do not have permission cannot access the network, and those within cannot access sites outside the network restricted by firewalls.
It inspects each individual “packet” of data as it arrives at either side of the firewall. It determines whether it should be allowed through or it should be blocked. - Define a networknode. (1 mark)
Any device connected to a network. - State any threefunctions of a network operating system. (3 marks)
Provides access to network resources, e.g., printers and folders.
Enables nodes on the network to communicate efficiently with each other.
Enables the various processes on the network to communicate with one another.
Responds to requests from application programs running on the network.
Supports network services such as network card drivers & protocols.
Maintains security, ensuring that only authorized users are allowed access the computer system.
Produces logs, i.e., a record of all the programs as they are run
Organises the use of storage, since this has to be shared among different users.
Works out the resources used by each program. If the user is paying for the service, then the computer works out the cost of running the program & charges the appropriate account. - The internet has been embraced as great a great resource for information and a variety of applications. State two ways in which a book publisher can make use of the internet. (2 marks)
Communication with other organizations, with your members, with your staff, with your supporters and donors through e-mails, messenger, web pages, mail lists, web site message boards. The Internet greatly offers rapid communication on a global scale. It even delivers an integrated multimedia entertainment that any other mass medium cannot offer.
Publishing your message to the world using online books, journals, press releases, workshops, conferences, lectures. Websites with conference proceedings, PDF (Portable Document Format) files of your publications, blogs, newsfeeds etc..support publishing.
Customer support - the people you are helping through your organization. It can help them when you aren't there: email, messenger, web pages, mail lists, and web site message boards. With video-conferencing, podcasting and other great web tools, you can even have workshops and classes online.
Researchon news, issues, papers and literature relevant to your cause. Use of search engines to find materials world-wide, mail lists e.t.c.
A place to do business and many other commercial activities;.E.g. e-bay, amazon.com, e.t.c. - Name twotypes of twisted pair cable used in data transmission. (2 marks)
shielded twisted pair
Unshielded twisted pair. - With aid of a labelled diagram, describe ring network topology; statingone disadvantage of such network. (4 marks)
In a ring topology, the computers are connected to one another in the shape of a closed loop using a single cable.
Data flows from one computer to another in one direction, and each computer actively participates in data transfer from one station to the other. In other words, each workstation acts as a booster by regenerating and retransmitting the signals around the network to its neighbour
A token is used to exchange data from one station to another. A tokencan be viewed as an envelope or a bag where data is placed for transmission and carried around the network.
- The diagram below shows a network arrangement that includes a network security feature to protect data and information. Use it to answers the questions that follow
- Convert each of the following numbers to decimal equivalent; given that the left most bit is a sign bit.
- 0101011 (2 marks)
(0)101011√ ½ mk
(1x25) + (0x24) + (1x23) + (0x22) + (1x21) + (1x20)½ mk
32 + 0+8+0+1 = 43½ mk
Ans = 4310½ mk - 111110101 (2 marks)
(1)11110101 ½ mk
(1x27)+(1x26)+(1x25)+(1x24) + (1x03)+(1x22) + (1x00)½ mk
128+54+32+16+8+1 = 2419½ mk
Ans = -24910½ mk
- 0101011 (2 marks)
- Differentiate between enhanced BCD and ASCII-8coding scheme of representing data in computers. (2 marks)
Enhanced BCDIs a 6-bit representation scheme, which can represent numeric characters. This allows 64 characters to be represented. a new version of ASCII-8 which makes use of256 characters.
ASCII-8- A new version of ASCII-8 which makes use of 256 characters. - Compute the following binary arithmetic expressions.
1010.101 + 11.011 (2 marks)
1
1
1
1
1
0
1
0
.
1
0
1
1
1
.
0
1
1
√
1
1
1
0
.
0
0
0
√
1010.101 - 11.011 (2 marks)
1
0
1
0
.
1
1
1
1
.
0
1
1
√
1
1
1
.
0
1
1
Ans: 1110.000
Ans: 111.011 - Convert 12.62510 to a binary representation. (2 marks)
Binary12 = 11002√
0.625 x 2 = 1.25√
0.25 x 2= 0.5
0.5 x 2 = 1.0
Ans: 1100.101 - Using 8-bit twos complementation, perform the following binary operation. (3 marks)
1110102 - 110112
Ones complement 00011011 – 1100100 √
00111010
11100100√
(1)00011110
+ 1√
00011111 ans: 000111112√
- Convert each of the following numbers to decimal equivalent; given that the left most bit is a sign bit.
- The figure below is a toolbar for a DTP package. Name and state the functions of the tools labelled A, B, C and D. (4marks)
A:Selection/Pick tool – Used to select objects
b: Text tool –Used to enable the insertion or add text into objects in the page or design.
C: Crop tool – To cut out/hide unwanted parts of a graphic.
D: Hand tool: Used to move the page to work on specific parts.
(b)State Four advantages of automated production. (4 marks)
- Increased efficiency due to the balancing of work load and production capacity.
- Improved customer services, adequate and quality goods are produced on time.
- Efficient utilization of resources such as raw materials.
- Increased productivity.
- Increased safety as tasks can be handled automatically e.g mechanized operations.
- Less human errors.
- Improved quality of output.
- Reduced direct human labor costs and expenses.
(c ) Most industries use computers for process control. Give any THREE benefits of this (3mks)
- Sound alarm and if necessary shut off process on extreme conditions i.e. some process can be very dangerous and fires or explosions might otherwise occur.
- Monitor and maintain quality control, e.g. where it is critical that the right mix of ingredients go into a drug.
- Keep a record of the process – so that machine performance can be assessed. This helps planned maintenance and replacement decisions.
Provide the best or optimum output at the lowest price
Download COMPUTER PAPER 1 - 2019 MOKASA II MOCK EXAMINATION.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students