SECTION A (40 MARKS)
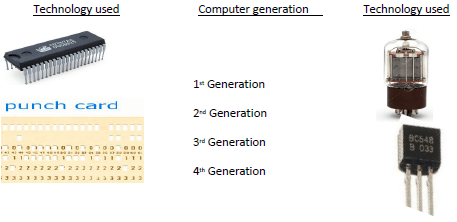
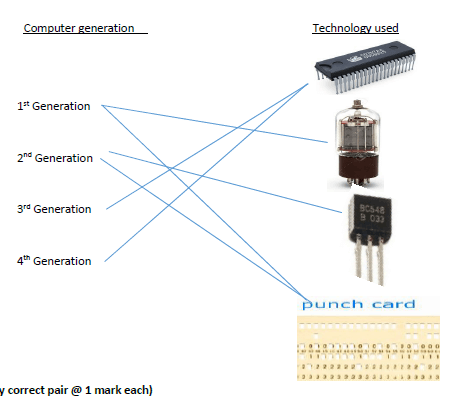
- Match the generation of computers to technology that was used by the generation by drawing straight lines. (2 marks)
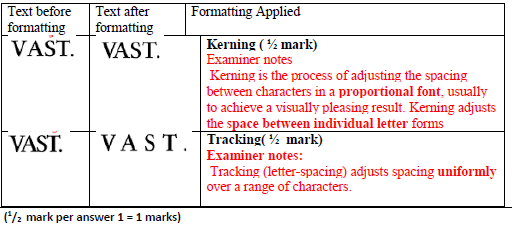
- The following image shows text in its original form and after it has been subjected to Desk Top Publishing formatting. One text was subject to kerning and the other to Tracking. Complete the column with the heading “Formatting Applied” by indicating which of the two formatting has been applied each text. (1 mark)
- State one difference between a web-conference and a video-conference. (1 mark)
- Explain why an email system should be configured to prevent spam email. (2 marks)
- When a new system is being developed analysis takes place. One method of researching the current system is interviewing.
- List two other methods of researching the current system. (1 mark)
- Explain two drawbacks of using interviews. (2 marks)
- State the meaning of the term data communication. (2 marks)
- Describe three benefits of a doctor using an expert system to help diagnose a patient’s illness. (3 marks)
- The use of ICT at workplace has enable a change in work pattern. For instance, employees are able to compress their working hours or make the working hours flexible.
- Differentiate between compressed and flexible working hours (2 marks)
- State one way through which ICT has enabled job sharing. (1 mark)
- Differentiate between a black hat hacker and a white hat hacker..(2 marks)
- Systems can be implemented in different ways; one of these is direct changeover.
- Describe three other methods of implementation. (3 marks)
- For One method described in (i) above, give an advantage when compared with direct changeover (1 mark)
- Illustrate a bus computer network. (2 marks)
- One of the computer lab use safety and precaution is that of not allowing students to eat or drink while in the computer room. Give two reasons why this rule is enforced in a computer laboratory (4 marks)
- A new system has been developed and documentation has been produced. There are two types of documentation; user and technical. Explain what technical documentation is used for.
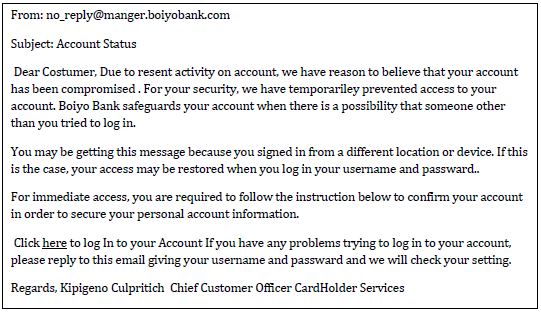
- This email has been received by a bank customer who believes it may be fraudulent.
Give four reasons why the customer may be suspicious. (4 Marks) - State two reasons why after systems implementation, a system must undergo constant review and maintenance. (4 Marks)
SECTION B 60 MARKS
(Answer question 16 and any other three questions)
-
- Python is an object oriented high level programming language: State the meaning of each of the following terms:
- Programming language..(1 mark)
- High level Programming language. (1 mark)
- Object oriented programming language. (1 mark)
- A program is required that would prompt a user to key in three integers. If the user does not key in three integers, the program should display the message “You must key in three integers... Press any key to retry” then allow the use to key in the integers again. Upon successful keying in of the three integers, the program should compare them –two integers at time- to determine the largest integer. The program should then display the largest integer. After the display of this integer, the program should prompt the user with the message “Compare another set of three integers (Y/N)...” If the user selects “Y”, the program should allow the keying in of another set of three integers, if the selection is “N”, the program should stop. However, if neither “Y” nor “N” is selected; the program should display the message “Invalid choice... try again” then present the message “ Compare another set of three integers (Y/N)...” again. The largest integer should be displayed if only one the keyed in integer is the largest. The program should display the message “No large integer found..” if the largest integer does not exist.
- Write a pseudocode for this program (6 marks)
- Draw a flowchart for this program (6 marks)
- Python is an object oriented high level programming language: State the meaning of each of the following terms:
-
- State the meaning of the term computer system? (2 marks)
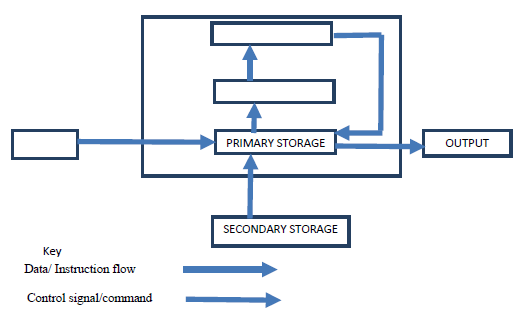
- Computers have both primary and secondary storage.
- Give two reasons by secondary storage in needed. (4 marks)
- Give two reasons by Primary storage in needed. (4 marks)
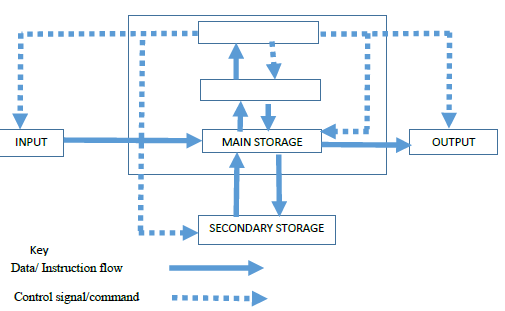
- Complete the following diagram of a layout of a computer system
-
- Computer operating systems have developed since early computers used Command Line Interfaces (CLI). Many computers now use Graphical User Interfaces (GUI), some of which are capable of using touch screen technology.
- State the meaning of the term touchscreen technology?(1 mark)
- State four differences between CLI and GUI operating system?(4 marks)
- State one difference between a multi-tasking and Single-tasking operating system.(2 marks)
- Explain one benefit of the following disk management activities
- Partitioning. (2 marks)
- Regularly carrying out Diagnosis (2 marks)
- Explain two ways through which an operating system can enhance safety of users’ of a computer system. (4 marks)
- Computer operating systems have developed since early computers used Command Line Interfaces (CLI). Many computers now use Graphical User Interfaces (GUI), some of which are capable of using touch screen technology.
-
- Mrs. Kongoi Missing is a secretary for Cairnballoch Cars. She has been asked to prepare a letter to be sent out to customers notifying them that their vehicles are due to be booked in for a service. She has to send this letter to one hundred customers. As the customer letters contain similar information – apart from their names and date of services, she will use standard letter then insert the details specific to each customer.
- Name the word processing feature that will enable her prepare each letter for the clients very fast (½ Mark)
- As she types her letter she realizes that when she reaches the end of a line, the word processor automatically moves her cursor to the next line.
Name the feature of the word processor that does this. (½ Mark) - Mrs. Missing has finished typing the letter. Print Preview shows that it is more than one page long. State two way in which the letter could be made to fit on one page.
- A school’s examinations officer has decided to develop a database to store Students’ details and the examinations they are due to sit in the year 2021. They are going to use a relational database. The tables are to hold information as follows:
- Students details table shall contain students’ personal information such as name
- Exam details table shall contain details of the exam such as exam date
- Student exam registration details table shall contain details of students and exams they are enrolled for.
Examination_ID Name_of_Subject Examination_Level Date_of_EXAM 0201 Kiswahili KCSE 12/04/2021 0101 English KCSE 11/06/2021 0102 English KCPE 01/06/2021 0202 Kiswahili KCPE 28/06/2021 - Based only on the examination details above and on additional information that there are only two types of examination levels-KCSE and KCPE, complete the figure below, stating the most appropriate data type for each field.
Figure 1: Exam details table design (1 mark)Field Name Data Type Examination_ID Name_of_Subject Examination_Level Date_of_Exam - Write the search criteria to search for all examinations which will be sat after 26/06/2018. (1 mark)
- Using a figure similar to one used in (i) above, design the tables that will contain Students details and Student exam registration details. (2 marks)
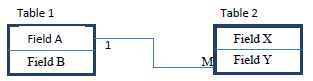
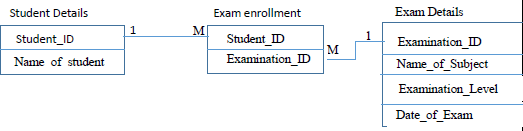
- When designing a relational, the database developer may use the illustrations shown in figure below to show the relationship between two tables. The letter M Stands for Many; it represents the many side of a relationship. The Number 1 represents the one side of a relationship. The rectangles represent tables. Tables names are labelled above the table and the field names are labelled inside the table as indicated. In this illustration Field A in Table 1 is used to create a relationship between Table 1 and Table 2 by linking it to Field Y in Table 2. The relationship between these tables is a one to many.
Figure 2: An illustration of a relationship between two tables in a relational database
Using the above illustrations method, show the relationship between the three tables in the school database clearly showing the fields that are used to link the tables and the relationship between the tables. (2 marks)
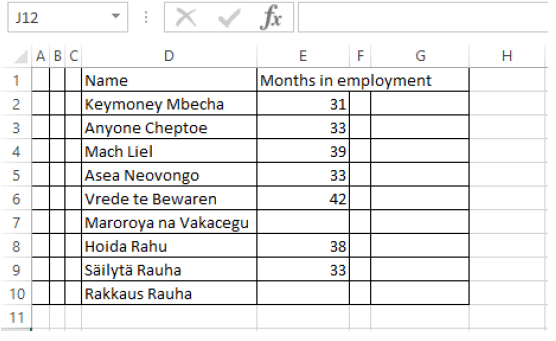
- Keeprope has created a spreadsheet showing the following data.
- Write down the formula that would be entered in cell G2 that would display the total number of employee who have been on employment for 33 months and below. (2 marks)
- Explain how the formula entered in cell G2 works. (2 marks)
- Keeprope subtracts the value that is displayed by the formula he entered in cell G2 in from 9. He thinks this will tell him the number of workers who have been in employment for more than 33 months. Explain why his reasoning may not work. (2 marks)
- Mrs. Kongoi Missing is a secretary for Cairnballoch Cars. She has been asked to prepare a letter to be sent out to customers notifying them that their vehicles are due to be booked in for a service. She has to send this letter to one hundred customers. As the customer letters contain similar information – apart from their names and date of services, she will use standard letter then insert the details specific to each customer.
-
- Give three reasons by computers use binary numbers to represent data. (3 marks)
- Subtract negative 7 from negative 8 using twos complement. Leave you answer in base ten.) (6 marks)
- Distinguish between the following data processing terms:
- Mechanical and Manual data processing modes
- Sequential and Serial file organization methods (2 marks)
- Interactive and real-time electronic data processing modes.

Marking Scheme
-
-
-
Web conference Video-conferencing an online meeting that involves audio and, may be video communication between participants an online meeting that involves audio and, definitely video communication between participants Mainly meant for host/panelist only to present material All participants have an equal chance at presenting material Main meant for content sharing Mainly meant for group discussion Participants listens mainly listen to presenter Every participant is a presenter and every presenter is a participant. Presenter doesn’t see participants Presenter and participants see each other over video screen - 1st two from:
- Spam could contain viruses
- Spam could contain spyware that record your key depressions ->.this could send messages out to alert others that the email address is live
- Spam can fill up your inbox
- Spam may have links to fraudulent websites
(1st one @ 2 marks. Must be explained.)
-
-
- Observation
- Questionnaire
- Examination of documents
(1st two @ ½ mark=1 mark)
-
- The interviewee may be uneasy with the questioning -.as it is not anonymous
- Time consuming to interview all the users− the interviewers are carried out one at a time
- Both the interviewee and the interviewer have to be free at the same time - which can cause time problems
- May be a language problem-this increases the time explaining all sections
- May give an answer they think the interviewer is trying to elicit- the interviewer could be biased/leading questions
- Disillusioned workers may give an answer that jeopardises the project-they could give a biased view/too vocal
- They cannot give the answer they want - as the interview is not anonymous/due to peer pressure
- Costly to the employers -time for the worker being off job (1st One explained at 2 marks: 1mark for description, 1 mark for reason)
-
- Transmission of data between two or more computers within a computer
-
- An expert system may help the doctor make a more accurate diagnosis
- An expert system uses data from many experts therefore it contains more knowledge than a single doctor
- Cheaper than regularly re-training the doctor
- The expert system's knowledge may be more up to date than the knowledge of a single doctor
- Cheaper than employing many specialists
- The diagnoses given are more consistent
(1st three @ 1 mark = 3 marks)
-
- Compressed hours
- The worker completes the normal working hours per week − but works for fewer days
- For example, a 40-hour week compressed into 4 days not 5
Flexible hours - Workers complete the same number of hours over a working week but can choose when to start and end in agreement with the manager
- Allows for workers to complete the school run or miss rush hour
(2 marks MAAW, difference must be shown)
-
- By working on the same task collaboratively/ interactively over the internet/network
- By enabling distribution of task to different individuals online
- Enabling workers who are physically/ globally far apart work on the same task/document collaboratively (1st one @ 1 mark)
- Compressed hours
- Some hackers are criminals and use their computer skills to harm or damage computer systems. These people are called black hat hackers. White hat hackers, on the other hand, use their computer skills to perform ethical hacking.
Ethical Hacking
Ethical hacking can determine vulnerabilities in a computer system. The goal of ethical hacking is to determine how to break into a system owned by a company, in order to prevent others from attacking it. If a white hat hacker can break into a system, a black hat hacker may be able to do the same. - 1 mark for method, 1 mark for appropriate advantage.
Parallel running.: Running old and new system concurrently for a while till new system stabalises
...has a backup of the data
Pilot running: Implementing the new system in section/branch of an organization then rolling it out to all other sections after is passes all trials successfully
...only affects one branch if system goes wrong/other branches can learn from the branch's mistakes
Phased implementation.: replacing old system portion by portion with the new system until entire system is replaced
.. ...if system fails still have most of old system to fall back on «staff can be trained gradually -
- Drinks can spill and cuase short circuits that my damange comptuers
- Food particles get into spaces between keys jamming them
- Food may distract learning in the lab
- Risk of food getting contaminated with hazardous materials in the lab such as cleaning liquids
- Slippery food items may fall on the floor leading to accidents
- Food wrapping make the lab dirty
- Learners touching keyboard with stick food items such as chocolate making them sticky and unfreidly to the next users
- Designed to help programmers/systems analysts…
- to improve a system.
- to maintain a system.
- to upgrade a system.
-
- Spelling errors
- Information requested that the bank would not ask for e.g. password and username
- personal information Not personalised – name or part of account number
- Hyperlink not usually given
- Inconsistency i.e. manager and Chief Customer Officer
- Allow examples of the data from the email
-
-
- A programming language is a set of symbols and patterns that are used following a predetermined syntax and logic to write/issue computer instructions.
A programming language is a vocabulary and set of grammatical rules for instructing a computer. (1 MK) - A high-level language (HLL) is a programming language such as C, FORTRAN, or Pascal that enables a programmer to write programs that are more or less independent of a particular type of computer architecture.
Language written in English like statements./written using syntax that is close to human language and intuitive hence human friendly (1 Mark) - Programing method in which data and procedure/instructions that work on the data are stored together into a container called an object
- A programming language is a set of symbols and patterns that are used following a predetermined syntax and logic to write/issue computer instructions.
-
-
- Electronic components that work together to receive data, process it into information using programs , the output the information..
( Evidence of componetns ½ , evidence of input ½ , evidence of processing ½ , evidence of output ½ , evidence of programs/control ½ marked in pairs upto maximum of 2) -
-
- If computer is switched off, work in RAM is lost but backing storage stores data for future use
- More likely that data is accidentally deleted in RAM- the copy in the secondary storage can be retrieved
- RAM is more expensive than backing storage per unit of memory - storing most information/information that is currently not being processed; in secondary storage is therefore cost effective
- RAM is bulkier than secondary storage per unit of memory - to store a lot of information will required huge devices
- Software package may be so large that it is physically impossible for RAM to store it- only a portion required for processing/execution will be uploaded into RAM and the rest remains on the secondary storage such as HDD.
- Operating system may be so large that it is physically impossible for ROM to store it.- can only be therefore store in secondary storage
- Data may need to be transferred from one computer to another and can’t do that with RAM Any 2 @ 2 marks.
-
- ROM Contains Firmware – enables computer to configure itself for use by e.g., running BIOS
- RAM hold instructions that are currently being executed
- There needs to be memory that holds the work that is being currently done by the user
- here needs to be memory that holds the software that is being currently used by the user
any two @ 2 marks each
-
-
- Electronic components that work together to receive data, process it into information using programs , the output the information..
-
-
- Touchscreen technology is an electronic visual display that a user can control by touching the screen with one or more fingers. (1 mark)
-
CLI GUI 1. User type command statements
2. Requires less memory
3. Users must memorise commands
4. Ideal for use with devices with small screens
5. Faster operating system due to low resource demand
6. Only needs keyboard to operate1. Use click on icons for commands
2. Require more memory
3. Users need not memorise commands as icon act as mnemonics
4. Require devices with large screens for icons to occupy
5. Slower operating system due to high resource requirements
6. Needs both keyboard and mouse to operate
-
-
- Running more than one OS on your system.
- Separating valuable files to minimize corruption risk.
- Allocating specific system space, applications, and data for specific uses.
- Storing frequently used programs and accessed data nearby to improve performance.
(1st one at 2 mark)
-
- Minimize risk of system crush – by marking bad sectors thus preventing data from being stored in those sectors
- Check defragmentation status so as to determine a need to defragment the disk thus increase performance in access.
-
- Authenticating users: user names and passwords so as to only allow genuine users
Utilities: provide utilities that enable users clear malware, diagnose and fix system threats
Automation: Automate locking of the system if left idle by user.
Timer locking: be able to lock/disable system if an attempt to log into the system fails after a given number of attempts
Keep log of system activity so as to enable auditing of the computer system
(First 2 @ 2 marks each =4 marks)
-
-
-
- Mail merge (½ Mark)
- Word wrap (1/2 mark)
-
- Alter margin size
- Decrease font size
- Change font
(1st two and 1 mark each)
-
-
(½ mark per each correct pair X 2 = 1 mark)Field Name Data Type Examination_ID Text Name_of_Subject Text Examination_Level Boolean Date_of_Exam Date - Date_of_exam>26/06/2021 or Date_of_exam>=27/06/2018
( 1 mark for Date_of_exam>26/06/2021 or Date_of_exam >=27/06/2021)
NB: Ignore absence of # tags before and after the dates. - Student table
Field Name Data Type Student_ID Text/Number Name_of_Student Text
Award mark only if
The table has be clearly labeled as student table
Contains at least two fields
Must contain a key field
The second field must be relevant.
(Award 1 mark for both appropriate name and data type MAAW)
Student exam registration details
Field Name Data Type Student_ID Text/Number Examination_ID Text
Award mark only if
The table has be clearly labeled as student table
Contains at least two fields
Must contain a key field
The second field must be relevant.
The examination_id data type MUST identified in b(i)
(Award 1 mark for both appropriate name and data type MAAW)
To award mark, the following basics must be met
Student detail table and at least the student_id included
Enrollment table included with at least the fields student_ID and Examination_ID
Exam details table included with at least the field Examination_ID
Lines linking the tables are included.
Link between student and exam enrollment table is on student_id fields
Link between exam enrollment table and exam details table is based on examination_id field.
(Award 1 mark per relationship X 2 = 2marks)
-
-
- =COUNTIF(E2:E10,"<=33")
Function name [1], range and criteria [1] (function name must be valid for range and criteria to earn mark) - FOUR from:
Countif functions have a range and a criteria argument [1]
In this example the range is A2:A10 [1]
The criterion is <31 [1]
It searches through the range A2:A10 [1]
Counts the number of cells/values… [1]
…that contain numeric values… [1]
…that have a value less than 31 [1]
Returns/displays that count. [1]
(Any 4 @ 1 mark a pair up to a maximum of 2 marks) - 9-4 is 5 [1]
But this 5 now includes the blank cells/includes those who haven’t worked at all /The blank cells are not greater than 33 but are still included [1] (2 marks)
- =COUNTIF(E2:E10,"<=33")
-
-
- Computer is a by-state device
1 is used to represent one state, 0 is used to represent the other state
Combination of 1’s and 0’s are used to generate code that represent data
Eight bits, represent a byte
A byte represents a character.
( First 3 @ 1 mark each) -
Using eight bits Using five bits -Conversion of 7 to binary equivalent i.e. 111 ( ½ )
-Padding to eight bit 00000111 ( ½ )
Determining ones complement: 11111000 ( ½ )
Determining twos complement : 11111001 ( ½ )
conversion of 8 to binary equivalent i.e., 1000( ½ )
Padding to eight 00001000 ( ½ )
Determine one’s complement 11110111 ( ½ ) Determine two’s complement 11111000 ( ½ )
Add the two complements 11111000+11111001=111110001( ½ )
Ignore overflow = 11110001 ( ½ )
Get denary equivalent
Subtract 1 = 111110000 ( ½ )
Flip 000001111( ½ )
Convert to denary
23+22+21+20 = 15( ½ )
Hence ans =-15 ( ½ )
(Award up to a maximum of 6) Conversion of 7 to binary equivalent i.e. 111 ( ½ )
Padding to five bits 00111( ½ )
Determining ones complement: 11000 ( ½ )
Determining twos complement 11001 ( ½ )
conversion of 8 to binary equivalent i.e., 1000( ½ )
Padding to eight or five bits 01000( ½ )
Determine one’s complement 10111( ½ )
Determine two’s complement 11000( ½ )
Add the two complements 11000+11001=110001 ( ½ )
Ignore overflow = 10001 ( ½ )
Get denary equivalent
Subtract 1 = 10000 ( ½ )
Flip 01111( ½ )
Convert to denary
23+22+21+20 = 15( ½ ) Hence ans =-15 ( ½ )
(Award up to a maximum of 6) -
- Mechanical : use to machines with moving parts to process data such as typewriters
Manual: use of pen and paper to process data ( 2 MKS) - Sequential: data stored in a predetermined order usually based on key field of a record; serial data store in the order in which it’s created. (2mks)
- Interactive: processing of data and presentation of output is immediate but requires human response to the output for any further activity whereas in real time processing of data and presentation of output is immediate but does not require human response to the output for further activity as the systems automatically responds to the output accordingly. (2mks)
- Mechanical : use to machines with moving parts to process data such as typewriters
- Computer is a by-state device
Download Computer Studies Paper 1 Questions and Answers - Kapsabet Mocks 2020/2021.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students