COMPUTER STUDIES
Paper 1
INSTRUCTION TO CANDIDATES
- This paper consists of Two sections A and B
- Answer ALL questions in section A
- Answer question16 and any other THREE questions from section B

Questions
SECTION A (40 MARKS)
Answer ALL the questions in SECTION
- State three functions of the control panel (3marks)
- Use the passage below to answer the questions that follows
- Mention three paragraph formatting features used in the passage above (3marks)
- With an aid of examples describe three text formatting features applied in the above passage (3marks)
- As regards to communication within computer network , what do you understand by the following terms (2marks)
- Point –to-Point
- Broadcast
- Describe three components of video conferencing (3marks)
- With reference to Desktop publishing describe the following terms (2marks)
- Gutter
- Stroke
- Lindah does not understand why computers are said to be Automatic at the same time they have No Intelligent Quotient (IQ) (2marks)
- State the difference between private university and public university (2marks)
- Ronaldo a student from Lenana School lives in a house with full internet access. She spends most of her time on phone and Desktop computer. State any three social issues associated with doing this (3mks)
- Mention three factors to consider when choosing a file organization method (3marks)
- Give two reasons to justify why many computer users today prefer saving their documents in the google drive (2marks)
- Computerization and automation are the great innovations of the 21st century. Describe how introduction of computers in the work place affected the job market (3marks)
- Describe three challenges affecting eLearning in most schools in Kenya (3marks)
- Use illustrations to explain two ways of implementing FOR loop (2mks)
- Explain the function of the following as used in data security and control (2marks)
- Patches
- Firewall
- The office has a fast internet connection for transferring information. However sometimes the internet run slowly. Give two reasons why this could be the case (2mks)
SECTION B (60 MARKS)
Answer Question 16 (Compulsory) and Any other THREE in this Section
-
- Describe the following qualities of an algorithm (3marks)
- Definiteness
- Finiteness
- Syntax
- State three differences between Assembly language and Machine language (3mark)
- Study the Pseudo code below and use it to answer the question that follows
- Draw a flowchart for the above algorithm (9marks)
- Describe the following qualities of an algorithm (3marks)
-
- Study the table below and answer the questions that follow
A B C D E F G 1 Student Name Math English Computer Total Average Grade 2 James Pesa 24 22 52 3 Maureen Kamau 60 17 71 4 James Jared 24 41 10 5 Mary Anna 52 63 81 6 - Write down the formula that
- Calculate the total marks for Maureen Kamau (2marks)
- Calculate the total marks for students with more than 50 and above in Maths (2marks)
- Get the mean score for Computer (2mark)
- The grading system is a shown in the table below .Write a function that will assign grades as reflected in the table below (3marks)
Average Grade 80-90 A 70-80 B 60-70 C 50-60 D 0 - 49 E - Write a formula using named reference that counts the total number of students who have scored more than 50 in computer (2marks)
- Write down the formula that
- Describe three features that make spreadsheet application suitable for mathematical applications (3marks)
- A formula = B$2+$C2 was typed in cell C2 the copied to cell C3 and the finally to D3. State how the formula will appear in D3 (1mark)
- Study the table below and answer the questions that follow
-
- What is the binary equivalent of 2412/32 base 10 (3marks)
- Convert 5BA2H to Binary (3marks)
- Using 8-bits twos complement subtract 1910 from 1410 (3marks)
- Given that the left most digit is a sign bit work out the decimal equivalent of the following binary numbers 001110101102(2marks)
- 1011012 is a negative use two compliment to get its Decimal equivalent (2marks)
- Describe two coding schemes used by computers to represent data in a computer (2marks)
-
- Study the tables shown below and use them to answer the questions that follow
Table 1
Table 2Admission No. Name Guardian ID Date of Birth Class Hall County 0978 Peter Kilulu P0023 12-12-1999 Form Three Moi Kiambu 4678 John James P0045 07-08-1999 Form Two Kenyatta Murang'a 6754 Luke Kenya P0023 06-01-2000 Form One Uhuru Migori
Guardian ID Name Address Telephone County P0023 John Mayi P.O Box 123 Kisumu 0723567453 Kisumu P0045 Jerry Watu P.O Box 2341 Nairobi 0745897654 Nairobi - Choose the most appropriate key field for Table 1 and 2 (2marks)
- Identify the most suitable data types Admission No and Date of Birth (2marks)
- Describe how a relationship can established between Table 1 and 2 (3marks)
- Write an expression to validate Date of Birth to allow dates that following in the year 1999 only (2marks)
- Peter Kipasi is the system analyst for Finaly group of companies. The Company Management automated their operations to have a competitive advantage over other companied in the same field. Peter received a memo from the CEO requesting him to consider changing the current information system. State what might have necessitated this (3mark)
- State three qualities of a good system analyst (3marks)
- Study the tables shown below and use them to answer the questions that follow
-
- Mention four limitations of computer networking (4marks)
- Explain how fibre optic transmit data signal and yet the core can only allow light signals to pass through (3marks)
- State the function of the following Communication devices
- Router (1mark)
- Switch (1mark)
- Bridge (1mark)
- NIC (1mark)
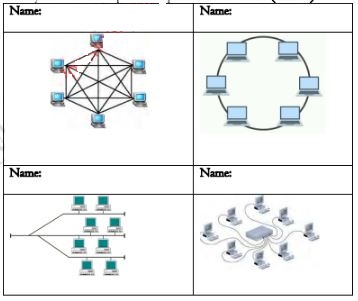
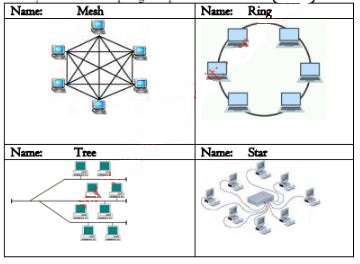
- Identity the Network topologies represented in the table (4marks)

Marking Scheme
- State three functions of the control panel
- Installing a program
- Installing a new hardware
- Changing the regional settings
- Creating and securing user accounts
- Updating the computer drivers
- Adjusting the monitor settings
- Use the passage below to answer the questions that follows
- Mention three paragraph formatting features used in the passage above
- Drop cap
- Indent
- Alignment
- Line spacing
- Character spacing
Award 1mark each max 3
- With an aid of examples describe three text formatting features applied in the above passage
- Bolding making the character darker than other characters in the document like White Teeth
- Underline is placing a line beneath a line of texts like Jane Nandwa
- Italicizing making a text to slant forward for example Broadly
- Mention three paragraph formatting features used in the passage above
- As regards to communication within computer network , what do you understand by the following terms
- Point –to-Point
- This is a type of communication where the communicating devices are directly linked to one another
- Broadcast
- A single message is delivered to all the nodes in a network
- A single message is delivered to all the nodes in a network
- Point –to-Point
- Describe three components of video conferencing
- Internet connectivity provide a path for sending signals to participants in remote sites
- Camera input device that capture data and presentation
- Speaker output device that project the sound
- Microphone input device that fed the system using audio signals
- Software a set of introduction provide a platform for compatibility and ensuring that there is smooth communication within the system
- Communication Terminal this can be inform of a computer, tablet and mobile phone
- With reference to Desktop publishing describe the following terms
- Gutter
- The inside margins closest to the spine of a book or the blank space between two facing pages in the center of a newsletter or magazine is known as the gutter. The gutter space includes any extra space allowance needed to accommodate the binding of books,
- Stroke
- Refer to a line style
- Refer to a line style
- Gutter
- Lindah does not understand why computers are said to be Automatic at the same time they have No Intelligent Quotient (IQ)
- Auto is short for automatic, which is a term used to describe anything that happens without user interaction
- NO IQ because a computer purely depend on the installed program without the programs the computer cannot any task
- State the difference between private university and public university
- Private university refer to universities owned by individuals, Churches and None governmental organizations while Public University is established by the government and it is run by government appointed team of managers ▪ Award 2marks max 2
- Private university refer to universities owned by individuals, Churches and None governmental organizations while Public University is established by the government and it is run by government appointed team of managers ▪ Award 2marks max 2
- Ronaldo a student from Lenana School lives in a house with full internet access. She spends most of her time on phone and Desktop computer. State any three social issues associated with doing this
- Dehumanization
- Internet addiction
- Access to inappropriate content
- Flaming
- Intrusion to private information through hacking and cracking
- Drug trafficking
- Cyber terrorism
- Mention three factors to consider when choosing a file organization method
- Storage media
- Method of access
- Frequency of update
- File activity
- Give two reasons to justify why many computer users today prefer saving their documents in the google drive
- Google drive more secure
- The content of the google drive can be access anywhere provided there is internet connectivity
- Mass storage
- Computerization and automation are the great innovations of the 21st century. Describe how introduction of computers in the work place affected the job market
- Job creation introduction of computer in the work place have created new job opportunities that used not to exist like System Analyst, Programmer, Software Engineer, Computer Trainer etc.
- Job displacement here an employee is moved to another section or department
- Job replacement introduction of computer in the workplace have rendered some people jobless since the computer is used to perform task that they use to do and therefore they declared redundant and their services are no longer required by the organization
- Describe three challenges affecting eLearning in most schools in Kenya
- High initial cost
- Lack of internet connectivity
- Lack of ICT infrastructure
- Lack standard
- Inadequate ICT skills
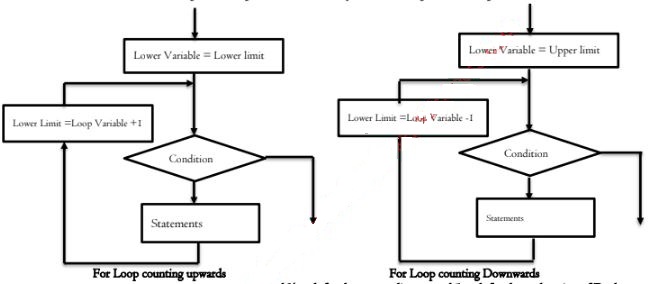
- Use illustrations to explain two ways of implementing FOR loop
- The for loop is used in circumstances where the execution of the chosen statements has to be repeated a predefined number of times. For loop can be implemented in two ways that is For lop that count upwards and the one that counts downward
- The for loop is used in circumstances where the execution of the chosen statements has to be repeated a predefined number of times. For loop can be implemented in two ways that is For lop that count upwards and the one that counts downward
- Explain the function of the following as used in data security and control
- Patches
- Patches are software and operating system (OS) updates that address security vulnerabilities within a program
- Firewall
- A Firewall is a network security device that monitors and filters incoming and outgoing network traffic based on an organization's previously established security policies.
- A Firewall is a network security device that monitors and filters incoming and outgoing network traffic based on an organization's previously established security policies.
- Patches
- The office has a fast internet connection for transferring information. However sometimes the internet run slowly. Give two reasons why this could be the case
- High network traffic
- The distance from the router
- Device protocol and setup
-
- Describe the following qualities of an algorithm
- Definiteness
- Each step of an algorithm must be precisely defined; the actions to be carried out must be rigorously and unambiguously specified for each case
- Finiteness
- An algorithm must always terminates after a finite number of steps
- An algorithm must always terminates after a finite number of steps
- Definiteness
- State three differences between Assembly language and Machine language
- Machine language is written in binary logic while Assembly language represent program instructions using mnemonics
- Machine language doesn’t require translation since machine codes are in a form that the computer directly understand while Assembly codes must be translated to machine readable using assembler
- Machine codes cannot easily be understood by human while Assembly language codes can easily be read, write and maintain
- Study the Pseudo code below and use it to answer the question that follows
- Draw a flowchart for the above algorithm using a Repeat.... Until
- Draw a flowchart for the above algorithm using a Repeat.... Until
- Describe the following qualities of an algorithm
-
- Study the table below and answer the questions that follow
- Write down the formula that
- Calculate the total marks for Maureen Kamau
- =Sum(B3:D3)
- =B3+C3+D3
Award 2marks max 2
- Calculate the total marks for students with more than 50 and above in Maths
- =Sumif(B2:B5,”>=50”)
- =Sumif(B2:B5,”>=50”)
- Get the mean score for Computer
- =Average(D2:D5)
- =Average(D2:D5)
- Calculate the total marks for Maureen Kamau
- The grading system is a shown in the table below .Write a function that will assign grades as reflected in the table below
- =IF(G2>=80,”A”,IF(G2>=70,”B”,IF(G2>=60,”C”,IF(G2>=50, “D”, “E”))))
- =IF(G2>=80,”A”,IF(G2>=70,”B”,IF(G2>=60,”C”,IF(G2>=50, “D”, “E”))))
- Write a formula using named reference that counts the total number of students who have scored more than 50 in computer
- Let the range D2 to D5 be given a name over90
- =countif(over90,”>50”)
- Write down the formula that
- Describe three features that make spreadsheet application suitable for mathematical applications
- Inbuilt formula
- Automatic recalculation
- Spreadsheet layout which is in row and columns
- A formula = B$2+$C2 was typed in cell C2 the copied to cell C3 and the finally to D3. State how the formula will appear in D3 (1mark)
- = C$2+$C3
- = C$2+$C3
- Study the table below and answer the questions that follow
-
- What is the binary equivalent of 24 1232 base 10
- 24.375
24 =11000 Whole number 1
0.375 x 2 =0.75 Fraction part 1
0.75 x 2 = 1.5 Answer 1
0.5 x 2 = 1.0
11000.0112
- 24.375
- Convert 5BA2H to Binary
- 5= 0101 Getting binary equivalent ½ max 2
B= 1011 answer 1
A= 1010
2 = 0010
0101101110100010
- 5= 0101 Getting binary equivalent ½ max 2
- Using 8-bits twos complement subtract 1910 from 1410
- 14+(-19) Binary equivalent ½ max 1
00010011 1C ½
11101100 +1 =
11101101 2C ½
0001110 Answer 1
11111011
- 14+(-19) Binary equivalent ½ max 1
- Given that the left most digit is a sign bit work out the decimal equivalent of the following binary numbers
- 001110101102
- 8 7 6 5 4 3 2 1 0 Assign place value 1
1 1 1 0 1 0 1 1 0 addition 1
256+128+64+16+4+2 = +470 Correct with a sign 1
- 8 7 6 5 4 3 2 1 0 Assign place value 1
- 101001110102
- 10 9 8 7 6 5 4 3 2 1 0 Assign place value 1
1 0 1 0 0 1 1 1 0 1 0 Addition 1
1024 + 256+32+16+8+2
-1338 Correct with a sign 1
- 10 9 8 7 6 5 4 3 2 1 0 Assign place value 1
- 001110101102
- Describe two coding schemes used by computers to represent data in a computer
- American Standard Code for Information Interchange (ASCII) represent both numeric and non-numeric characters using 7bits and can represent up to 128 characters
- Extended Binary Coded Decimal Interchange Code (EBCDIC) represent both numeric and non-numeric characters using 8 bits. Maximum number of characters that can be represented is 256
- Binary Coded Decimal (BCD) represent numeric characters only using 4bits
Award 1 mark each max 2
- What is the binary equivalent of 24 1232 base 10
-
- Study the tables shown below and use them to answer the questions that follow
- Choose the most appropriate key field for Table 1 and 2
- Table 1 Admission No
- Table 2 Guardian ID
- Identify the most suitable data types Admission No and Date of Birth
- Admission N0 – Text
- Date of Birth –Date and Time
- Describe how a relationship can established between Table 1 and 2
- Link Guardian ID in table 2 to Guardian ID in table 1 which is a foreign
- Relationship established will be One to Many
- A guardian can have many students
- Write an expression to validate Date of Birth to allow dates that following in the year 1999 only (2marks)
- >=#01/01/1999# AND <#01/01/2000#
- Choose the most appropriate key field for Table 1 and 2
- Peter Kipasi is the system analyst for Finaly group of companies. The Company Management automated their operations to have a competitive advantage over other companied in the same field. Peter received a memo from the CEO requesting him to consider changing the current information system. State what might have necessitated this
- To exploit new opportunities
- The system have some problems
- Directives
- State three qualities of a good system analyst
- Good problem solving skills
- Good communication skills
- Technical skills
- Innovative and creative
- Study the tables shown below and use them to answer the questions that follow
-
- Mention four limitations of computer networking
- High initial cost
- Security threat
- Network failure
- Spread of terrorism and drug trafficking
- Moral and cultural effects
- Explain how fibre optic transmit data signal and yet the core can only allow light signals to pass through ▪ At the sending station data signals are converted to light signal using LED
- Data signals in form of lights are propagated along the cable
- At the receiving end the light signals are converted back to data signal using photodetector Award 1 mark each max 3
- State the function of the following Communication devices
- Router
- A router is a networking device that forwards data packets between computer networks.
- Switch
- Is a communication device used to connect nodes in a network and forwards the packets directly to the address node without broadcasting
- Bridge
- A Bridge divide a network into segments to reduce network traffic
- NIC
- Create a physical link between the computer and the transmission media
- Router
- Identity the Network topologies represented in the table (4marks)
- Mention four limitations of computer networking
Download Computer Studies Paper 1 Questions and Answers - Maranda Mocks 2021/2022 Exams.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students