Questions
INSTRUCTIONS TO CANDIDATES
- This paper has TWO sections; A and B.
- Answer ALL the questions in section A
- Answer question 16 and any other three questions from section B.
Section A
Answer all questions from this section
- State 2 measures to put in place in the computer lab to safeguard users health 2marks
- Distinguish between embedded and dedicated computers 2marks
- State 2 limitations of entering data into a computer system using a touch sensitive input device 2marks
-
- Differentiate between dynamic and static RAM 2marks
- Define Solid-state storage and give two examples. 2marks
- State 3 ways in which barcode readers may be used in schools 3marks
- State 3 circumstances under which voice input would be preferred over other methods of data capture 3marks
- In relation to DTP state the purpose of frames 1mark
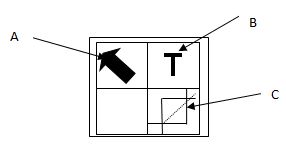
- The figure shows toolbar for a DTP package
State functions of tools labeled A,B and C (3marks) - Describe the following 2marks
- Master file
- Transaction file
- State any 3 benefits that a company would gain from distributed processing as their data processing method 3marks
- State two
- Functions of an email software 1mark
- Protocols used in sending and receiving emails 1mark
- A school has been advised to employ a database administrator state 3 responsibilities of this personnel in the school 3marks
- What is the difference between a Gas Plasma Display and Liquid Crystal Display 2marks
-
- Explain how a pixel affects the resolution of a monitor. 1mark
- List two types of computer output on microform (COM). 2marks
- Differentiate between high definition multimedia interface and Firewire interface. 2marks
- A warranty is an agreement between the buyer and the seller. It spells out terms and conditions after selling a product in case of failure or malfunction. Describe any three basic requirements a good warranty should cover. 3marks
Section B
Answer Question 16 (Compulsory) and Any other 3 Questions from this section.
-
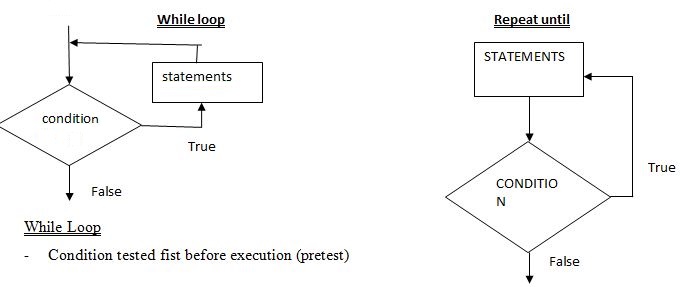
- With the aid of a flowchart differentiate repeat until from while loop control structures 4marks
- State 2 types of translators used in programming 1mark
- On the Nairobi-Nakuru highway, the Kenya Police have put speed cameras at a certain point to read the time a vehicle passes a point (A) on the road and then reads the time it passes a second point (B) on the same road. (Points A and B are 200 meters apart). The speed of the vehicle is calculated using:
Speed = 100 (Km/ hr)
time at point B-time at point A
The maximum allowed speed is 100 kilometers per hour.
500 vehicles were monitored using these cameras over a 1-hour period.
Write a pseudo code, which: 5marks- Inputs the start time and the end time for the 500 vehicles that were monitored
- Calculates the speed for each vehicle using the formula above.
- Outputs the speed for each vehicle and a message if the speed exceeded 100 km/hour.
- >=100km/hr “High Speed”
- <100km/hr “Normal Speed”
- Draw a flow chart for the above pseudo code. 5marks
-
- State any three advantages of using computers in computer aided design (CAD) 3marks
- The training department of an international airline has introduced computer based training (CBT) to teach foreign languages to its cabin crew. Give TWO advantages of using CBT. 2marks
- The airline also trains its pilots.
- What type of training is most appropriate to train pilots to manage dangerous situations? 1mark
- Give TWO benefits of using this type of training. 2marks
- A student set up a spreadsheet to compare share prices in six companies over five years.
A B C D E F G H 1 Name of
companyShare price Share price Share price Share price Share price Average
Share priceHighest
Share price2 Year 2005 2006 2007 2008 2009 3 Global Oil 81 190 305 130 140 169 305 4 GSD 619 722 622 325 324 522 722 5 KLN 60 71 71 63 45 62 71 6 Nesto 316 418 522 600 640 499 640 7 Takkco 149 316 394 202 122 237 394 8 Uniway 122 135 254 365 570 289 570 - What formula is in cell G5 to find the mean share price for KLN? 1mark
- What formula is in cell H5 to find the highest share price for KLN? 1mark
- If the data in cell E4 was changed to 425, which cells would be automatically updated? 1mark
- State the cells that are needed to create a line graph to show the share prices for years 2006 to 2008. 2marks
- The student wants to extend the spreadsheet to include share prices for 2010. Describe how the student would do this. 2marks
-
- The following are some of the phases in the system development life cycle SDLC system analysis, system design, system implementation, system review and maintenance, state 3 activities that are carried out during the system implementation phase 3marks
- Give 3 reasons why system maintenance phase is necessary in SDLC 3marks
- Various considerations should be made during input design and output design. State two considerations to be made for each case. 4marks
- Input design
- Output design
- In relation to database
- Differentiate between bound and unbound controls 2marks
- Outline 2 features of a primary key 2mark
- What is a composite key 1mark
-
- Explain 2 ways in which operating system provides data security in a computer system 2marks
- Differentiate between pull down and pop up menu as used in graphical operating system 2marks
- Describe the following wireless communication devices. 3marks
- Access point (AP)
- Wireless Antenna
- PCMCIA cards
- Mr. Bill, the Principal of a school wishes his school to have an internet connection in a bid to improve its service delivery. Mention four internet connectivity requirements that must be present to enable the connection. 2marks
-
- Failure of information systems is a major concern in the security of data in computing systems. State two causes of such failure. 2marks
- Explain the following computer crimes.
- Fraud 1mark
- Industrial espionage 1mark
- Excluding passwords, state two other security control measures used to guard against unauthorized access to computers in a network. 2marks
-
- Write in full
- ASCII 1mark
- EBCDIC 1mark
- Convert each of the following binary numbers to decimal equivalent given that the leftmost digit is a sign bit
- 00101101 2marks
- 11001001 2marks
- In a certain coding scheme a letter P was coded as 11011001 how would letter K be represented in the same scheme 4marks
- Using 6 bits and twos complement subtract 23 from 17 leaving your answer in decimal notation 5marks
- Write in full
Marking Scheme
- State 2 measures to put in place in the computer lab to safeguard users health 2marks
- Standard furniture
- Good lighting
- Avoid flickering monitors
- Avoid overcrowding
- Insulate the cables
- Distinguish between embedded and dedicated computers 2marks
- Embedded – special purpose computer found within another machine to control it and cannot be directly accessed
- Dedicated- a general purpose computer that specializes in one of the tasks thus being more committed in its area of specialization
- State 2 limitations of entering data into a computer system using a touch sensitive input device 2marks
- Not suitable for inputting large amounts of data.
- Not very accurate - selecting detailed objects can be difficult with fingers.
- Tiring to use for long periods.
- More expensive than alternatives such as a mouse.
- Not robust - can soon become faulty if misused.
-
- Differentiate between dynamic and static RAM 2marks
Dynamic Static Slower to access faster to access Requires refreshment does not require refreshment Cheaper to buy expensive to buy - Define Solid-state storage and give two examples. 2marks
- A non-volatile storage that employ integrated circuits rather than mechanical, magnetic or optical technology. They are referred to solid state because they do not have movable parts in its read/write storage mechanism.
- Differentiate between dynamic and static RAM 2marks
- State 3 ways in which barcode readers may be used in schools 3marks
- Take inventory of items in the school
- Keep track of employee login log out
- Used to transact business in the library
- Used to keep track of movement of goods
- State 3 circumstances under which voice input would be preferred over other methods of data capture 3marks
- When the hands of the user are engaged;
- When the user has physical disabilities;
- When faster input is required;
- When the user is not good in keying skills
- In relation to DTP state the purpose of frames 1mark
- Frames allow the multiple Web pages to all show up in the same page.
- Frames are rectangular areas meant for inserting graphics and text. They allow users to place objects wherever they want to on the page.
- The figure shows toolbar for a DTP package
State functions of tools labeled 3marks- A-selection tool for selecting choosing /highlighting objects on the work area
- B-text tool for enabling typing/editing or insertion of text
- C-cropping tool to trim graphics
- Describe the following 2marks
- Master file
- Main file that contains relatively permanent/ semi permanent records about a particular items or entries
- Transaction file
- Used to hold input data during transaction processing. The file is later used to update the master file and audit daily, weekly or monthly transactions.
- Used to update the master file.
- Master file
- State any 3 benefits that a company would gain from distributed processing as their data processing method 3marks
- Reliability, high fault tolerance: A system crash on one server does not affect other servers.
- Scalability: In distributed computing systems you can add more machines as needed.
- Flexibility: It makes it easy to install, implement and debug new services.
- Fast calculation speed: A distributed computer system can have the computing power of multiple computers, making it faster than other systems.
- Openness: Since it is an open system, it can be accessed both locally and remotely.
- High performance: Compared to centralized computer network clusters, it can provide higher performance and better cost performance.
- State two
- Functions of an email software 1mark
- Facilitates mail creation
- Facilitates reading mails
- Facilitates sending mails
- Maintaining a mailing list
- Keeping track of number of emails
- Editing and composing mails
- Advertising
- Creating email accounts/ social networking list
- Maintain contacts / address list
- Deleting mails
- Protocols used in sending and receiving emails 1mark
- SMTP, IMAP, POP3, MIME, HTTP
- Functions of an email software 1mark
- A school has been advised to employ a database administrator state 3 responsibilities of this personnel in the school 3marks
- Determine storage needs of users
- Managing the collection of data
- Carry out backup of databases
- Carrying out recovery of lost data incase of system failure
- Ensuring the security and integrity of the system
- Adding new users and managing user’s accounts
- What is the difference between a Gas Plasma Display and Liquid Crystal Display 2marks
- Gas plasma display does not suffer from angle distortion while Liquid crystal display suffers from angle distortion. (2 marks or 0 mark)
-
- Explain how a pixel affects the resolution of a monitor. 1mark
- A pixel is the smallest unit of a digital image or graphic that can be displayed and represented on a digital display device. The higher the number of pixel, the clearer and excellent images formed on the screen. Less pixel results to less clearer and poorer display on the screen.
- List two types of computer output on microform (COM). 2marks
- Microfiche
- Microfilm
- Differentiate between high definition multimedia interface and Firewire interface. 2marks
- High definition interface is an interface used for transmitting digital audio and video data from computer to a projector, TV or audio device.
- Firewire It is similar to USB but has a higher transmission rate hence it is suitable for streaming video from digital cameras to a computer (2 marks or 0 mark)
- Explain how a pixel affects the resolution of a monitor. 1mark
- A warranty is an agreement between the buyer and the seller. It spells out terms and conditions after selling a product in case of failure or malfunction. Describe any three basic requirements a good warranty should cover. 3marks
- Scope of cover for example 4 months, 2years
- Callout response and liability agreement. For how long should the supplier take to repair a fault or replace the product and if he/she delays who beams the cost.
- Preventive maintenance for example regulating of service at intervals.
(First 3, 1 mark each)
-
- With the aid of a flowchart differentiate repeat until from while loop control structures 4marks
Repeat until
Execution done at least once before condition is tested (posttest) - State 2 types of translators used in programming 1mark
- Assembler
- Translator
- Compiler
- On the Nairobi-Nakuru highway, the Kenya Police have put speed cameras at a certain point to read the time a vehicle passes a point (A) on the road and then reads the time it passes a second point (B) on the same road. (Points A and B are 200 meters apart). The speed of the vehicle is calculated using:
- Speed = 100 (Km/ hr)
time at point B-time at point A
The maximum allowed speed is 100 kilometers per hour.
500 vehicles were monitored using these cameras over a 1-hour period.
Write a pseudo code, which: 5marks- Inputs the start time and the end time for the 500 vehicles that were monitored
- Calculates the speed for each vehicle using the formula above.
- Outputs the speed for each vehicle and a message if the speed exceeded 100 km/hour.
>=100km/hr “High Speed”
<100km/hr “Normal Speed”
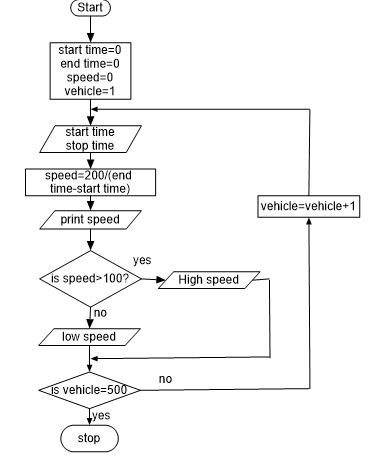
Start
Starttime=0
Endtime=0
Speed=0
For Vehicles=1 To 500 Do
Input Start Time
Input Stop Time
Speed =200/(End Time-Start Time)
Print Speed
If Speed >100 Then
Print High speed
Else
Print Normal Speed
ENDIF
END FOR
STOP
- Speed = 100 (Km/ hr)
- Draw a flow chart for the above pseudo code. 5marks
- With the aid of a flowchart differentiate repeat until from while loop control structures 4marks
-
- State any three advantages of using computers in computer aided design (CAD) 3marks
- Easy to store and retrieve drawings.
- Easy to make changes
- Easy to test since most packages come with features for testing designs.
- Saves on costs since models can be used to draw construction schedules.
- Stored design can be sued to produce control instructions for machines which will make the product.
- Quick production of drawings and plans. (First 3, 1 mark each)
- The training department of an international airline has introduced computer based training (CBT) to teach foreign languages to its cabin crew. Give TWO advantages of using CBT. 2marks
- Any two from:
- user can work at their own speed
- user can learn in their own time/when/where they want
- user can re-run sections of training package whenever they wish
- user can pause the training at any point
- user gets immediate feedback/analysis (on their performance)
- there is no need to have teachers or classrooms
- less expensive for the airline/ training department
- Any two from:
- The airline also trains its pilots.
- What type of training is most appropriate to train pilots to manage dangerous situations? 1mark
- flight simulator/simulating/simulation
- Give TWO benefits of using this type of training. 2marks
Any two from:- can be much safer
- less expensive than building/crashing the real thing
- repetition of scenarios (e.g. potential crashes)
- different scenarios/situations available
- no need for an instructor
- What type of training is most appropriate to train pilots to manage dangerous situations? 1mark
- A student set up a spreadsheet to compare share prices in six companies over five years.
- What formula is in cell G5 to find the mean share price for KLN? 1mark
- = AVERAGE(B5:F5) or = AVERAGE(B5,C5,D5,E5,F5) or = SUM(B5:F5)/5 or = (B5+C5+D5+E5+F5)/5 (1 mark)
- What formula is in cell H5 to find the highest share price for KLN? 1mark
- = MAX(B5:F5) or = MAX(B5,C5,D5,E5,F5) (1 mark)
- If the data in cell E4 was changed to 425, which cells would be automatically updated? 1mark
- G4, (H4) (2 marks)
- State the cells that are needed to create a line graph to show the share prices for years 2006 to 2008. 2marks
- A3:A8, B3:E8, or A3:E8 (2 marks)
- The student wants to extend the spreadsheet to include share prices for 2010. Describe how the student would do this. 2marks
- – add column between F and G/insert column before G/insert column after F
- – change the formula(s) to allow 2010 data to be added (2 marks)
- What formula is in cell G5 to find the mean share price for KLN? 1mark
- State any three advantages of using computers in computer aided design (CAD) 3marks
-
- The following are some of the phases in the system development life cycle SDLC system analysis, system design, system implementation, system review and maintenance, state 3 activities that are carried out during the system implementation phase 3marks
- File conversion
- System changeover
- Training installation
- Module testing
- Security control measures
- Give 3 reasons why system maintenance phase is necessary in SDLC 3marks
- Correct errors that may have escaped during design
- Meet changes in the technology
- Changes in policies e,g from government
- Change in operating environment
- Various considerations should be made during input design and output design. State two considerations to be made for each case. 4marks
- Input design
- Data capture method
- Input interface between user and system
- Volume of input
- Frequency of input
- Output design
- Form of output designed hard/softcopy
- Output layout
- Purpose of output
- Target audience
- Input design
- In relation to database
- Differentiate between bound and unbound controls 2marks
- Bound control -A control whose source of data is a field in a table or query . You can use bound controls to display values that come from fields in your database. ...
- Unbound control -A control that doesn't have a source of data (such as a field or expression)
- Outline 2 features of a primary key 2mark
- There can only be one primary key for a table.
- The primary key consists of one or more columns.
- The primary key enforces the entity integrity of the table.
- No NULL columns are allowed.
- The primary key uniquely identifies a row.
- What is a composite key 1mark
- A composite key is a candidate key that consists of two or more attributes that together uniquely identify an entity occurrence.
- A compound key is a composite key for which each attribute that makes up the key is a foreign key in its own right.
- Differentiate between bound and unbound controls 2marks
- The following are some of the phases in the system development life cycle SDLC system analysis, system design, system implementation, system review and maintenance, state 3 activities that are carried out during the system implementation phase 3marks
-
- Explain 2 ways in which operating system provides data security in a computer system 2marks
- Access controls authentication of users in order to access files
- Performing regular patches of updates
- Creating secure accounts with required privileges
- Scrutiny of all incoming and outgoing packets of data through a firewall
- Encryption of data during transmission stage password/biometric analysis
- Log files to detect any breach
Any 3x1 mark
- Differentiate between pull down and pop up menu as used in graphical operating system 2marks
- A pull down is a list of commands that appear as a list from the menu bar going down which is invoked by the click or alt key
- Po up menu is a list that appears anywhere on the screen when there is a right click
- Describe the following wireless communication devices. 3marks
- Access point (AP)
- It provides an entry into a bounded network for people who have a wireless device such as Personal digital assistants (PDA’s), laptops and computers with wireless links
- Wireless Antenna
- It is a device that has antennas in order to detect signals in the surrounding. In most cases they have two antennas so that the one that receives the best signal at any particular time can be used
- PCMCIA cards
- It is an add on card inserted into a device such as personal digital assistants or a laptop in order to enable wireless communication between the devices and wired network server.
- Access point (AP)
- Mr. Bill, the Principal of a school wishes his school to have an internet connection in a bid to improve its service delivery. Mention four internet connectivity requirements that must be present to enable the connection. 2marks
- Transmission/Telecommunication/Network media
- Data Terminal Equipments - A TCP/IP enabled computer with a web browser.
- An account with an Internet Service Provider (ISP).
- Networking equipment such as a modem, router or switch to connect the computer transmission media.
-
- Failure of information systems is a major concern in the security of data in computing systems. State two causes of such failure. 2marks
- Hardware failure due to improper use.
- Unstable power supply as a result of brownout or blackout and vandalism.
- Network breakdown
- Natural disaster
- Program failure/crash
- Explain the following computer crimes.
- Fraud 1mark
- Fraud is the use of computers to conceal information or cheat other people with the intention of gaining money or information
- Industrial espionage 1mark
- Involves spying on a competitor to get or steal information that can be used to finish the competitor or for commercial gain. The main aim of espionage is to get ideas on how to counter by developing similar approach or sabotage.
- Fraud 1mark
- Failure of information systems is a major concern in the security of data in computing systems. State two causes of such failure. 2marks
- Excluding passwords, state two other security control measures used to guard against unauthorized access to computers in a network. 2marks
- Audit trails
- Firewalls
- Proxy servers
- Log files/security monitors
- Encryption
- User access levels/Multilevel access
- Biometric security
- Explain 2 ways in which operating system provides data security in a computer system 2marks
-
- Write in full
- ASCII 1mark
- American standard code for information interchange
- EBCDIC 1mark
- Extended binary coded decimal interchange code
- ASCII 1mark
- Convert each of the following binary numbers to decimal equivalent given that the leftmost digit is a sign bit
-
- 00101101 2marks
00101101
Leftmost = 0 – a positive number
Number = 0101101
32+8+4+1 = +4510Number 0 1 0 1 1 0 1 Place value 26 25 24 23 22 21 20 Absolute 0 32 0 8 4 0 1
- 00101101 2marks
-
- 11001001 2marks
11001001
Leftmost = 1 = a negative number
Number 1001001
Number 1 0 0 1 0 0 1 Place value 26 25 24 23 22 21 20 Absolute 64 0 0 8 0 0 1
- 11001001 2marks
-
- In a certain coding scheme a letter P was coded as 11011001 how would letter K be represented in the same scheme 4marks
- P 11011001
K
K L M N O P = 5 STEPS
CHANGE 5 TO BINARY – 101
Since from P to K you go backwards you subtract the binary
11011001
- 101
11010100
- P 11011001
- Using 6 bits and twos complement subtract 23 from 17 leaving your answer in decimal notation 5marks
- 17-23
Convert to binary
17 = 10001
23 = 10111
Into 6 bits
17 = 010001
23 = 010111
Negate
010111 = 101000
Add 1 to LSD
101000
+ 1
101001
Add binary
101001
010001
111010 (change to decimal)
=-32+16+8+2Number 1 1 1 0 1 0 Place value -25 24 23 22 21 20 Absolute -32 16 8 0 2 0
=-32+26
=-6
- 17-23
- Write in full
Download Computer Studies Paper 1 Questions and Answers - KCSE 2021 Westlands Mock Exams.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students