Instructions to candidates:
- Write your name and index number in the spaces provided at the top of this page
- Sign and write the date of examination in the spaces provided above
- This paper consists of TWO sections; A and B
- Answer ALL questions in section A
- Answer question 16 and any other THREE questions from section B
- All answers should be written in the spaces provided on the question paper
- Students should check to ascertain that all pages are printed
For Official Use only
|
Section |
Question |
Maximum Score |
Candidate’s Score |
|
A |
1-15 |
||
|
B |
16 |
||
|
17 |
|||
|
18 |
|||
|
19 |
|||
|
20 |
|||
|
Total score |
100 |
|

QUESTIONS
SECTION A [40 MARKS]
Answer ALL questions in this section in the spaces provided
- State three features of fifth generation computers (3 marks)
- Using relevant examples distinguish between a formula and function (3 marks)
- A publisher intends to use a desktop publishing programme to create a publication which is to have many graphics State three ways in which the graphics may be acquired for this purpose (3 marks)
- The management of an organisation intends to purchase a printer State three factors that they should consider during the purchase (3 marks)
- State three reasons why it is important to define data types of fields in a database correctly (3 marks)
- An engineering company requires a computer system to design roads and bridges (2 marks)
Explain one suitable choice for:- Output device;
- Software
- State three circumstance under which the use of wireless communication would be preferred in data communication (3 marks)
- Headache, back and neck pain may result from the use of computers State how each of them can be minimized (2 marks)
- Headache
- Back and Neck Pain
- Explain the importance of each of the following in word processing:
- tab stops; (2 marks)
- Section breaks (2 marks)
- State three problems associated with using e-mail technology for communication (3 marks)
- State two ways in which each of the following can be prevented
- Software errors (1 mark)
- Computer fraud (1 mark)
- Differentiate between analogue data and digital data as used in computers (2 marks)
- State four properties that an operating system displays about file (2 marks)
- State the functions of each of the following keys on the computer keyboard [2 marks]
- backspace;
- insert (ins)
- Give three file organization methods in a computer (3 marks)
SECTION B [60 MARKS
Answer question 16 and any other three questions from this section in the spaces provided
-
- State three ways in which a programmer can make program code easy to follow (3 marks)
- Outline two disadvantages of low level programing languages (2 marks)
- Differentiate between compilers and interpreters as used in programming (2 marks)
- A trader bought a car from a manufacturer and later sold it to another person Write a pseudocode for a program that will accept the buying price and the selling price of the car, determine whether the trader made a profit/or loss, calculate the profit/loss and display it (4 marks)
- Draw a flowchart for the above pseudocode (4 marks)
-
- Subtract 01112 from 10012 (2 marks)
- Using two’s compliment, subtract 7 from 4 and give the answer in binary notation (4 marks)
- Convert
- 91C16 to octal (3 marks)
- 3778 to hexadecimal (3 marks)
- 962510 to binary (3 marks)
-
- Explain three circumstances under which observation method may be preferred during data collection (6 marks)
- State three activities that may be carried out during system implementation (3 marks)
- Explain three approaches that may be used to replace an old system with a new computerized system (3 marks)
-
- What is meant by each of the following terms as used in data security and controls? (2 marks)
- Confidentiality
- Industrial espionage
- Jane a form four student was advised to partition a hard disk for her computer Explain two reason that may have necessitated this (4 marks)
- If one table in a database contains the field: EMPLOYEE - ID, LAST – NAME, FIRST – NAME and HIRE – DATE and another contains the fields DEPARTMENT, EMPLOYEE – ID and SALARY, it is possible to establish a relationship between the two tables (6 marks)
- Name the type of such a database
- What type of relationship can be established between the tables? (1 mark)
- Provided the most appropriate data types for each of the fields (3 marks)
- A publishing firm designed the following publication using a DTP software,

- Give two reasons why the firm prefer using DTP instead of Word Processors (2 marks)
- Identify four formatting features used in the designing the publication (2 marks)
- What is meant by each of the following terms as used in data security and controls? (2 marks)
-
- State the function of each of the following
- Network Interface Card (1mark)
- Modem (1mark)
- Repeater (1mark)
- State any three reason why the fibre optic cable is preferred for data transmission over the other cables (2 marks)
- State two functions of networking operating systems other than providing network security (2 marks)
- Explain four advantages of networking (4 marks)
- The figure below shows a network topology Use it to answer the questions that follows:
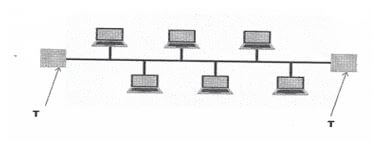
- What is the name of the topology? (1mark)
- What is the work of the part labelled T (1 mark)
- Highlight one disadvantage of the above topology identified in 20(e) (1 mark)
- State the function of each of the following

MARKING SCHEME
- State three features of fifth generation computers. . [3 marks]
- Have very high processing power
- Support complex programs
- Have increasingly become small
- Connectivity to internet
- Superior hardware.
- Using relevant examples distinguish between a formula and function. [3 marks]
- Formula is a mathematical expression that creates a relationship between cells to return a new value like
= A2 + A3 + A4 - Functions are inbuilt formula that the used can quickly use instead of having to create a new each time a calculation has o be carried out like = sum (A2:A4)
(Correct difference @ 2 marks
(Examples @ ½ mark)
- Formula is a mathematical expression that creates a relationship between cells to return a new value like
- A publisher intends to use a desktop publishing programme to create a publication which is to have many graphics. State three ways in which the graphics may be acquired for this purpose. [3mark]
- Using digital camera
- Scanning the graphics from other sources
- Downloading from the internet
- Drawing from scratch/Drawing tools
- Clip art
- The management of an organisation intends to purchase a printer. State three factors that they should consider during the purchase. [3 marks]
- Volume of work to be printed.
- Maintenance cost below e.g. consumables like toners should be affordable.
- Speed of printing.
- Type of work to be printed; type of paper, paper size, use needs/range of capability.
- Type of printout whether color us required or not.
- Compatibility with the existing hardware
- Initial cost
- Availability of in the market
- State three reasons why it is important to define data types of fields in a database correctly. (3 marks)
- Memory use optimization when the program is loaded;
- Assist in trapping errors during data input;
- So that appropriate computation can be performed
- Increase speed of processing. (correc @ 3 marks)
- An engineering company requires a computer system to design roads and bridges. (2 marks)
Explain one suitable choice for:- Output device: A plotter because it prints large size drawings to high precision.
- Software: A CAD software because it facilitates in the design of engineering drawings.
- State three circumstance under which the use of wireless communication would be preferred in data communication. [3 marks]
- When the targeted recipients are many and diverse e.g. different platforms, devices, geographical locations.
- When the sender or receiver is mobile and it in practical to use wired media.
- When there is no space or it is inconvenient to lay cables e.g. in a congested town.
- When the distance of travel is very big e.g. extraterrestrial communication.
(Correct @ 1 mark each)
- Headache, back and neck pain may result from the use of computers. State how each of them can be minimized. [2 marks]
- Headache
- Use of filters/antiglare
- Proper lighting
- Regular break
- Back and Neck Pain
- Proper/correct furniture for the computer
- Correct position of the screen
- Correct sitting posture
- Taking a break
(Correct @ 2 marks)
- Headache
- Explain the importance of each of the following in word processing:
- tab stops; (2 marks)
- When tab stops are set, they allow aligning of the text into columns
- Section breaks. (2 marks)
- Section breaks allow splitting of a document into different sections so that different formatting styles can be applied on different sections.
(Correct @ 2 marks)
- Section breaks allow splitting of a document into different sections so that different formatting styles can be applied on different sections.
- tab stops; (2 marks)
- State three problems associated with using e-mail technology for communication. (3 marks)
- Threats to privacy
- Organization: system admn” can snoop into peoples’ mails
- Email can be unsolicited/spam mail
- Messages can be sent to masses of people without their consent
- Vulnerability to machine failure
- Email can be overwhelming when many messages are received leading to email overload and going through each of them can be taxing
- Email can be faked
- Email attached can be a source of viruses
- Email technology not available to all/Technology illiteracy
- Encourage illicit communication such as immoral behavior
(Correct @ 3mrks)
- State two ways in which each of the following can be prevented
- Software errors (1 mark)
- Use of anti-virus software
- Update system frequently
- Purchase software from authentic sources
- Test the software from authentic sources
- Test syntax/logic
- Proper training
- Proper enactment of laws
(Correct @ 1 mark)
- Computer fraud (1 mark)
- Data encryption
- Password protection
- Audit trail
- Surveillance system
(Correct @ 1 mark)
- Software errors (1 mark)
- Differentiate between analogue data and digital data as used in computers. (2 marks)
- Analogue data uses values that changes continuously between instances while digital data are values that change from one value to the next in step by step sequence
(Correct @ 2 marks)
- Analogue data uses values that changes continuously between instances while digital data are values that change from one value to the next in step by step sequence
- State four properties that an operating system displays about file. (2 marks)
- File size
- Date modifies
- File type
- File name
- Author
- Date created
- Time created
- Hidden
- Archived
(Correct @ 2marks)
- State the functions of each of the following keys on the computer keyboard. [2 marks]
- backspace;
- Move the display cursor one position backwards, deletes the character at the position and shifts back the text after that position by one position
(Correct @ 1 mark)
- Move the display cursor one position backwards, deletes the character at the position and shifts back the text after that position by one position
- insert (ins)
- When insert is selected, keys add characters to the screen at the cursor (insertion point) without deleting those already there
(Correct @ 1 mark)
- When insert is selected, keys add characters to the screen at the cursor (insertion point) without deleting those already there
- backspace;
- Give three file organization methods in a computer. (3 marks)
- Serial (heap)
- Sequential
- Random
- Indexed sequential
(Correct @ 3 marks)
-
- State three ways in which a programmer can make program code easy to follow. (3 marks)
- Using modules or short blocks of program/functions/procedures; making internal documentation/comments;
- Using meaningful variable names and user word in the program;
- Using indent to represent nested statement:
- Using blank liens o separate blocks of code stamen;
- Test formatting of reserved words e.g. bolding (Correct @ 3marks)
- Outline two disadvantages of low level programing languages. (2 marks)
- Difficult and cumbersome to use and learn
- They require highly trained experts to develop and maintain programs
- Removing errors (debugging is difficult
- Are machine dependent i.e. are now transferrable from one hardware of software platform to another.
- Differentiate between compilers and interpreters as used in programming. (2 marks)
- An interpreter translates the source program one statement at a time while a compiler translates the entire source code at one before execution
- Interpreted programs are slower than compiled program
- Interpreted programs takes less memory compared to compiled program. (Correct @ 2 marks)
- A trader bough a car from a manufacturer and later sold it to another person. Write a pseudocode for a program that will accept the buying price and the selling price of the car, determine whether the trader made a profit/or loss, calculate the profit/loss and display it. [4 marks]
START
ENTERR “Buying Price) (Bp), Selling price (Sp)”
IF “Bp, Sp THEN
Profit = Sp-Bp
PRINT Profit
Else
Loss=Bp-Sp
PRINT Loss
Endif
STOP - Draw a flowchart for the above pseudocode. (4 marks)
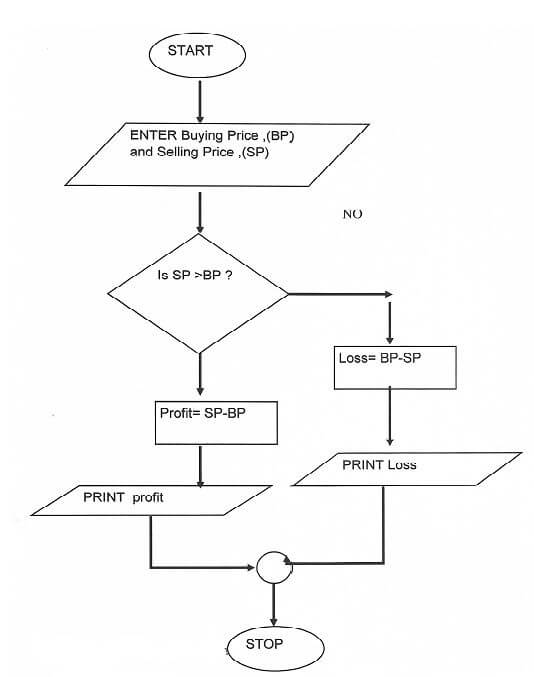
- State three ways in which a programmer can make program code easy to follow. (3 marks)
-
- Subtract 01112 from 10012 (2 marks)
- 00102
- Using two’s compliment, subtract 7 from 4 and give the answer in binary notation. (4 marks)
- 7 = 1112
- 4 = 1002
- -4 in two’s compliment is 100
- ∴ 111
100
+1011
The resulting answer is 011 since the overflow is ignored in decimal notation that is 310
- Convert
- 91C16 to octal (3 marks)
9
1
C
1001
0001
1100
100
100
011
4
4
4
3
91C16 =44348
- 3778 to hexadecimal (3 marks)
3
7
7
011
111
111
0000
1111
1111
0
F
F
3778 = FF16
- 9.62510 to binary (3 marks)
9 = 1001
0625 x 2 = 1.25 WRITE 1
0.25 x 2 = 0.5 WRITE 0
0.5 x 2 = 1.0 WRITE 1
- 91C16 to octal (3 marks)
- Subtract 01112 from 10012 (2 marks)
-
- Explain three circumstances under which observation method may be preferred during data collection. (6 marks)
- When the subjects that are being observed need not be made aware of the fact
- When there is need to collect data without interfering with the working of the subjects
- When there is need to directly see what subjects do rather than rely on what they tell you
- When nature of data can only be collected via observation e.g. traffic flow
- When collecting data in situation that subjects may be unwilling to give information
- State three activities that may be carried out when during system implementation. [3 marks]
- File conversation
- Staff training
- Change over strategies
Type of maintenance that is done to make the system to adapt the hanging technology e.g. changing the system because of new operating system
- Explain three approaches that may be used to replace an old system with a new computerized system (3 marks)
- Direct approach
- Parallel approach
- Phased approach
- Pilot approach
(with correct explanation)
- Explain three circumstances under which observation method may be preferred during data collection. (6 marks)
-
- What is meant by each of the following terms as used in data security and controls? [2 marks]
- Confidentiality
- Sensitive data that belongs to an organization or government should not be accessed or disclosed to unauthorized persons.
- Industrial espionage
- Spying on your competitor to get information that you can use to counter of finish the competitor
- Confidentiality
- Jane a form four student was advised to partition a hard disk for her computer. Explain two reason that may have necessitated this. (4 marks)
- Install two operating systems
- Use one portion for backup
- If one table in a database contains the field: EMPLOYEE - ID, LAST – NAME, FIRST – NAME and HIRE – DATE and another contains the fields DEPARTMENT, EMPLOYEE – ID and SALARY, it is possible to establish a relationship between the two tables. (6 marks)
- Name the type of such a database
- Relational database
- What type of relationship can be established between the tables? (1 mark)
- One to one
- provided the most appropriate data types for each of the fields. (3 marks)
- EMPLOYEE – ID TEXT
- LAST – NAME – TEXT
- FIRST – NAME – TEXT
- HIRE – DATE – DATE/TIME
- DEPARTMENT – TEXT
- SALARY – CURRENCY/NUMBER
- Name the type of such a database
- A publishing firm designed the following publication using a DTP software,

- Give two reasons why the firm prefer using DTP instead of Word Processors. (2 marks)
- DTP has wide range of templates
- Master pages can be used to set up a common layout
- Every item is contained in a frame and can be formatted independently
- Identify four formatting features used in the designing the publication. (2 marks)
- Bolding
- Underlining
- Drop cap
- Bullets
Font (style, size and type)
- Give two reasons why the firm prefer using DTP instead of Word Processors. (2 marks)
- What is meant by each of the following terms as used in data security and controls? [2 marks]
- State the function of each of the following
-
- Network Interface Card (1mark)
- A device that creates a physical link to the computer and the transmission media
- Modem (1mark).
- Modem converts a signal from digital to analogue from for the purpose of transmission over the transmission media
- Repeater (1mark)
- Receive signal from one section of a network, clean it to remove any distortion, boosts/amplifies it and sends it to another section
- Crimping tool
- Used terminate a cables/used to attach RJ 45 to cable
- Network Interface Card (1mark)
- State any three reason why the fibre optic cable is preferred for data transmission over the other cables. (2 marks)
- Fiber optic transmission is faster
- Fibre optic transmission can cover greater distances
- Fiber optic cables are impervious to electromagnetic interference (EMI)
- Save space and enhance cable management
- Fiber optics are future-proof
- Extremely High Bandwidth
- Low Security Risk
- Light Weight
- State two functions of networking operating systems other than providing network security. (2 marks)
- Provide access to network resources;
- Supporting network services like protocols;
- Support communication;
- Respond to requests from applications;
- Explain four advantages of networking. (4 marks)
- Improves reliability e.g. in case one computer breaks down, users can still access data and information from other computer on network
- Resources sharing i.e. data/information, files, printers, modems, programs etc. can be attached to the network for access by all users
- Distributed processing facilities
- Remote communication i.e. transfer of data signals between two communication devices located differently
- Cost effectiveness. Although initial cost of laying down the network components may be expensive the savings experienced and the value added to service delivery make them cost effective
- The figure below shows a network topology. Use it to answer the questions that follows:
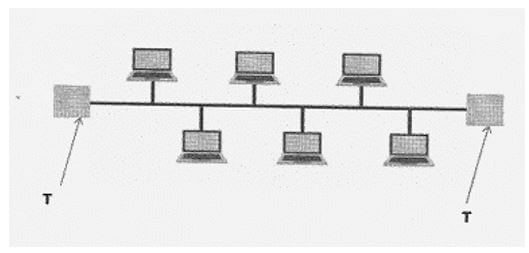
- What is the name of the topology? (1mark)
- Bus topology
- What is the work of the part labelled T. (1 mark)
- Terminator in a backbone is used to prevent data signal from bouncing back/absorb signals.
- Highlight one disadvantage of the above topology identified in 20(e). (1 mark)
- Cable break of backbones cable brings down the whole network
- Limits the number of computers that can be connected
- What is the name of the topology? (1mark)
-
Download Computer Studies Paper 1 Questions and Answers - Arise and Shine Mock Exams 2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students
