INSTRUCTION TO CANDIDATES
- Write your name and index number in the spaces provided above
- This paper consists of Two sections; A and B.
- Answer ALL questions in section A.
- Answer question 16(compulsory) and any other THREE questions from section B.
- All answers should be written in the spaces provided on the question paper
FOR OFFICIAL USE ONLY
|
SECTION |
QUESTIONS |
CANDIDATES SCORE |
|
A |
1-15 |
|
|
B |
16 |
|
|
17 |
||
|
18 |
||
|
19 |
||
|
20 |
||
|
TOTAL SCORE |
QUESTIONS
SECTION A
- Define the following terms as used in word processing. (3 marks)
- Word wrap
- Justification
- Drop cap
- State three advantages of using computers in performing day to day’s tasks. (3marks)
- Wanja operates a bookshop in a town. Lately he is finding the task of managing daily transactions manually overwhelming.
- Identify the type of management information system that Wanja should acquire (2 marks)
- State two benefits that Wanja will gain from using such a system (2 marks)
- State three hardware considerations that need made before installing an operating system (3marks)
- Before the end of every month an electricity service provider sends out field officers to take consumer meter readings. The data collected by the officers is then keyed into the computer. The system then generates utility bills which are printed and sent to the consumers.
- State two transcription errors that are likely to occur during meter reading or input (2 marks)
- State two ways such errors can be avoided (1 mark)
- State three editing tools that are available in most standard word processing software (3 marks)
- Information security should be enforced both physically and logically.
- Differentiate between the two security mechanisms (2 marks)
- State two physical security techniques (2 marks)
- Explain three types of system buses found on the computer system board (3 marks)
- State the four disk management tools found in most operating systems. (3 marks)
- Highlight the dangers associated with the following:
- Exposing computers to high humidity (1marks)
- Purchasing software before assessing requirements (1marks)
- Using foreign flash disks on the computer. (1marks)
- Differentiate between a filter and a query in a database (1 marks)
- The payroll system is both a financial system and a human resources system. Explain this statement. (2marks)
- Explain the importance of the following spreadsheet operations.
- Freezing columns (1mark)
- Data validation (1 mark)
- List two ways in which computer technology can be used in law enforcement (1 marks)
- In reference to aviation technology, state two advantages of using simulation in training pilots (2mks)
SECTION B (60 MARKS)
Answer question 16(compulsory) and any other THREE questions from this section.
- State the stage of program development in which: (4 marks)
-
- A flowchart would be drawn
- The programmer would check whether the program does as required
- The user guide would be written
- The requirements specifications would be written
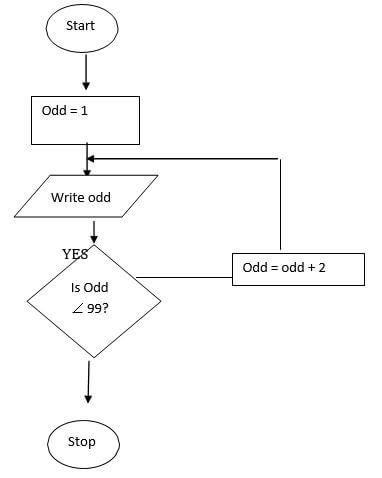
- A programmer uses program design tools to design a program that can list the odd numbers between 0 and 100.
- Write a pseudo code for this problem. (5mks)
- Draw a flow chart for the pseudo code in 16 b) (i) above. (6mks)
- Study the follow flowchart then answer the questions that flow. (4 marks)
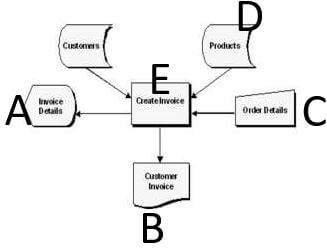
Figure 1 Flowchart 2- Name all the flowchart symbols used in this flowchart. (4 marks)
A: ..
B: ..
C:
D:
- Name all the flowchart symbols used in this flowchart. (4 marks)
-
- Define the term
- Network topology. (1 mark)
- Clearly illustrate the following types of network topologies. (5mks)
- Bus topology
- Mesh topology
- Star topology
- Explain two factors you would consider before enrolling for an ICT course in a college. (2mks)
- Differentiate the function SUM and SUMIF as used in spreadsheet. 2mks
- State two advantages of using fiber optic cables. (2mks)
- In system development, testing is one of the critical stages. Give three reasons why the testing phase is critical to the systems developer. (3 marks)
- A systems analyst has been asked by a doctor to computerize the records she keeps about her patients. He must first of all collect information about the existing system.
-
- Describe four methods he could use to collect this information. (4mks )
- Once the whole system has been designed it will need to be implemented.
- Describe two methods of implementation that could be used. 2mks
- Write down two reasons why one of the methods you gave in (b) (i) is better than the other. ( 2 marks)
- After a system is implemented, it is evaluated. Give two reasons why a system should be evaluated. ( 2mks)
- State one difference between system flowchart and program flowchart. (2 marks)
-
-
- Describe each of the following data processing methods and give an example of where they are used. (6mks)
- Online processing
- Batch processing
- Real-time
- Differentiate between the following: (6mks)
- Logical file and physical file –
- Master file and back-up file –
- Random and indexed sequential file organization methods.
- An organization is facing threats to data integrity. Explain three ways how the threats can be minimized. (3mks)
- Describe each of the following data processing methods and give an example of where they are used. (6mks)
-
-
- Give one reason why data and information in a computer system needs to be converted to other number systems other than binary. (1mks)
- Explain one reason for use of binary in digital technology. (1mks)
- Using twos complement, workout : 1510 - 810 in binary form. (4mks)
- Using BCD coding system convert 796 to binary. (3mks)
- Convert each of the following to the number system indicated:
- 111.1012 to decimal; (3 marks)
- 14.687510 to binary [3 marks]
-
MARKING SCHEME
- Define the following terms as used in word processing. (3 marks)
- word wrap
- it is a formatting feature which makes the text to move to the next line automatically
- Justification
- It is an alignment feature where both left and right are aligned
- Drop cap
- word wrap
- State three advantages of using computers in performing day to day’s tasks. (3marks)
- It has high speed of processing tasks
- It is flexible
- Has high storage space
- Wanja operates a bookshop in a town. Lately he is finding the task of managing daily transactions manually overwhelming.
- Identify the type of management information system that Wanja should acquire (2 marks)
- electronic
- State two benefits that Wanja will gain from using such a system (2 marks)
- High storage
- High processing speed
- Efficiency
- Identify the type of management information system that Wanja should acquire (2 marks)
- State three hardware considerations that need made before installing an operating system (3marks)
- Compatibility
- Availability
- User need
- User friendliness
- Before the end of every month an electricity service provider sends out field officers to take consumer meter readings. The data collected by the officers is then keyed into the computer. The system then generates utility bills which are printed and sent to the consumers.
- State two transcription errors that are likely to occur during meter reading or input (2 marks)
- Transposition
- Misreading
- State two ways such errors can be avoided (1 mark)
- Dry checking
- Using of test data
- Using debugging utilities
- State two transcription errors that are likely to occur during meter reading or input (2 marks)
- State three editing tools that are available in most standard word processing software (3 marks)
- Do and redo
- Spelling and grammar checker
- Thesaurus
- Insert mode
- Type over mode
- Information security should be enforced both physically and logically.
- Differentiate between the two security mechanisms (2 marks)
- Physical security ensures the content is not tapered with while logical security refers to securing the meaning of the information
- State two physical security techniques (2 marks)
- Burglar proofing
- Security personnel
- Security cameras (cctv)
- Differentiate between the two security mechanisms (2 marks)
- Explain three types of computer buses found on the computer system board (3 marks)
- Control bus
- Address bus
- Data bus
- State four disk management tool found in most operating systems (3 marks)
- Defragmentation
- Partitioning
- Disk Scanning
- Disk formatting
- Disk compression
- Disk backup
- Disk diagnostic
- Highlight the dangers associated with the following:
- Exposing computers to high humidity (1marks)
- Rusting of the parts of the metallic computer
- Purchasing software before assessing requirements (1marks)
- May be a pirated software
- Using foreign flash disks on the computer. (1marks)
- May multiply viruses
- Exposing computers to high humidity (1marks)
- Differentiate between a filter and a query in a database (1 marks)
- Filter if a formatting tool that extract part of the record from the table while query is a database object used to extract information from the database
- The payroll system is both a financial system and a human resources system. Explain this statement. (2marks)
- It is used to perform finance calculations and what if analysis and also used to update and provide financial records for the workers
- Explain the importance of the following spreadsheet operations.
- Freezing columns (1mark)
- It enable the use to view only required records at atime
- Data validation (1 mark)
- Ensures the records are valid as per the user need
- Freezing columns (1mark)
- List two ways in which computer technology can be used in law enforcement (1 marks)
- Surveillance, crime detection and prevention
- Scene monitoring by the police
- Storage of biometric information for investigation of crimes
- In reference to aviation technology, state two advantages of using simulation in training pilots (2mks)
- Safety
- Less costly
-
- State the stage of program development in which:
- A flowchart would be drawn Design
- The programmer would check whether the program does as required Testing
- The user guide would be written Documentation
- The requirements specifications would be written Analysis
- A programmer uses program design tools to design a program that can list the odd numbers between 0 and 100.
- Write a pseudo code for this problem. (5mks)'
- Start Marks award
Odd=1 * Start/ stop – 1 mk
Repeat Repeat/ until -1 mk
Write odd correct statements -3 mks
Odd= Odd+2 *Also accept use of other control statements
Until odd =99 such as while…DO
- Start Marks award
- Draw a flow chart for the pseudo code in 16 b) (i) above. (6mks)
Any one at 2 marks. Difference must be shownSystem flowchart
Program flowchart
A program flowchart details the flow through a single program
A system flowchart will show the flow through a system(A is made up of many programs).
. Each box in the flowchart will represent a single instruction or a process within the program
Each box will represent a program or a process made up of multiple programs.
A system flow chart describes the flow of data through a complete data-processing system
describe the flow of data through a particular computer program in a data processing system
Describe the relationship between inputs, processing, and outputs for a system.
Describe the sequence of logical operations performed in a computer program.
- Study the follow flowchart then answer the questions that flow.
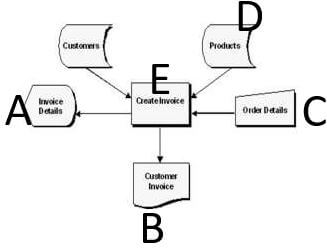
- Identify the type of flowchart that is represented by the flowchart in figure2
- System flow chart ( ½ mark)
- Name all the flowchart symbols used in this flowchart.
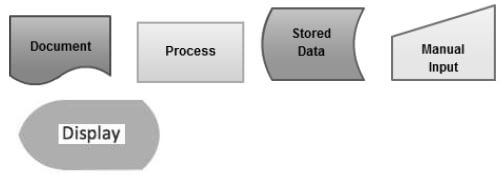
@ ½ mark each. Each name must be associated with the appropriate symbol. (2 ½ marks)
- Identify the type of flowchart that is represented by the flowchart in figure2
- Write a pseudo code for this problem. (5mks)'
- State the stage of program development in which:
-
- Define the term network topology . Network topology can be viewed in two ways . Name and Explain the two ways. (5mks)
- Network topology:
Refers to the way computers and other devices have been arranged on a network or how data passes from one computer to another on a network.
refers to the physical arrangement of the network, especially the location of the computers, other devices and how the cables are run between the devices.
- Network topology:
-
- Logical/Signal topology.
- Deals with the way data passes from one device to the next on the network. Examples of logical topologies are Ethernet and token ring.
- Physical topology.
- Refers to the physical layout arrangement of components on the network.
- The most common physical topologies are the bus, the star, the ring and the mesh.
- Logical/Signal topology.
- Explain two factors you would consider before enrolling for an ICT course in a college. (2mks)
- Cost.
- Job opportunities.
- Where the examinations offered are recognized.
- The organization offering the course.
- Differentiate the function SUM and SUMIF as used in spreadsheet. 2mks
- SUM :- Adds values in a range of cells and returns the results
- SUMIF :- Adds values in a range of cells that meets the specified condition and returns the results.
- State two advantages of using fiber optic cables. (2mks)
- Noise resistance: It is immune to EMI.
- Less signal attenuation: signal can run for miles without requiring regeneration.
- Higher bandwidth: fibre optic cable can support dramatically higher bandwidths (and hence data rate) than all other cables.
- Smaller and lighter than copper cable hence space limited situations.
- Can be used in hazardous (highly flammable) places because they do not generate electrical signals.
- Very fast (in light form)
- In system development, testing is one of the critical stages. Give three reasons why the testing phase is critical to the systems developer. [3 marks]
- Helps to ensure that the logical ad physical designs and environment are to the users satisfaction
- Help to detect and correct errors
- Gives proof to those skeptical about the working of the system
- Helps to establish how the system works under various conditions.
- Define the term network topology . Network topology can be viewed in two ways . Name and Explain the two ways. (5mks)
- A systems analyst has been asked by a doctor to computerize the records she keeps about her patients. He must first of all collect information about the existing system.
- Describe four methods he could use to collect this information. 4mks
Any four from:- Observation
- Questionnaires
- Interviews
- Collecting documents/document review @ ½ mark each (2 marks)
- Once the whole system has been designed it will need to be implemented.
- Describe two methods of implementation that could be used. 2mks
Described Any two from:- parallel running
- direct changeover
- pilot running
- phased implementation. @ 1 mark each (2 marks)
- Write down two reasons why one of the methods you gave in (b) (i) is better than the other.
- parallel running/pilot running
two form
there is a backup/fallback system
In case of malfunction
time can be taken in correcting malfunctions
can train staff gradually - direct changeover
two form
time is not wasted in changeover
cheaper as you don't have to pay two sets of staff
system is tested rigorously before implmentation
less likely to malfunction - Phased implementation
two form
If system malfunctions only small part of business affected
don't have to pay two sets of staff
can make sure system workd before extending it
( 2 marks)
- parallel running/pilot running
- Describe two methods of implementation that could be used. 2mks
- After a system is implemented, it is evaluated. Give two reasons why a system should be evaluated.
Any two from: ( 2mks)- to make sure user requirements have been met
- to identify any shortcomings
- to identify possible improvements
- State one difference between system flowchart and program flowchart. (2 marks)
System flowchart Program flowchart- A program flowchart details the flow through a single program A system flowchart will show the flow through a system(A is made up of many programs).
- Each box in the flowchart will represent a single instruction or a process within the program Each box will represent a program or a process made up of multiple programs.
- A system flow chart describes the flow of data through a complete data-processing system describe the flow of data through a particular computer program in a data processing system
- Describe the relationship between inputs, processing, and outputs for a system. Describe the sequence of logical operations performed in a computer program.
Any one at 2 marks. Difference must be show.
- Study the following flowchart then answer the questions that follow.
- Identify the type of flowchart that is represented above in figure2
System flow chart ( ½ mark) - Name all the flowchart symbols used in this flowchart (e) figure 2 above.
@ ½ mark each. Each name must be associated with the appropriate symbol. (2 ½ marks)
- Identify the type of flowchart that is represented above in figure2
- Describe four methods he could use to collect this information. 4mks
-
- Describe each of the following data processing methods and give an example of where used. (6mks)
- Online processing – Data is processed immediately it is received e.g. internet banking, online payment system using credit card.
- Batch processing – Data is accumulated as a group then it is processed as one/ a group. Eg in payroll system
- Real-time – Computer processes the incoming data as soon as it occurs, up to dates the transactions file and gives an immediate response, that would affect the events as they happen e.g. making reservations for airlines seats, hotels etc.
- Make a clear difference between:- (6mks)
- Logical file and physical file – Viewed in terms of what data items it contain and details of what processing operations may be performed on the data items. Physical files is one that is viewed in terms of how data is stored on a storage media and hoe the processing operations are made possible.
- Master file and back-up file – Master file is the main file that contains relatively permanent records about particular items or entries. Back-up file is used to hold copies of data or information from the fixed storage (hard disk)
- Random and indexed sequential file organization methods.
Random – Also direct file organization records are stored randomly but accessed directly on a storage medium. Indexed sequential records are stored and accessed in a particular order using an index used to enable the computer to locate individual records on storage media.
- An organization is facing threats to data integrity. Explain three of how the threats can be minimized. (3mks)
- Backup data preferably on external storage media.
- Control access to data by enforcing security measures.
- Design user interface that minimize unauthorized access.
- Using error detection and correction software when transmitting data.
- Use devices that directly capture data from the source such as bar code readers.
- Digital cameras, optical CR.
- Describe each of the following data processing methods and give an example of where used. (6mks)
-
- Give one reason why data and information in a computer system needs to be converted to other number systems other than binary.(1mks)
- Higher number systems are used in computing to reduce the streams of binary into manageable form.
- Help to improve the processing speed.
- Optimize memory usage.
- Explain one reason for use of binary in digital technology. (1mks)
- It is easier to develop devices that understand binary language.
- Device a designed using binary logic are simple more reliable and consume the energy.
-
- Using twos complement, workout : 1510 - 810 in binary form. (4mks)
= 15+(-8)
Convert 810 to its binary equivalent then write its two’s complement
15 = 11111 ,
To 8 bit =00011111
8= 1000
To 8bit = 00001000
11110111 BitwiseNOT of 8 =1’C
2’C = 11110111+1 = 11111000
00001111
+ 11111000
( 1) 00000111
Overflow is ignored = 000001112
And in binary form the difference Is a positive number (000001112 (710) - Twos complement is the most popular way of representing negative numbers in computer Systems. Give an advantage of using this method.
- There are no two ways of representing a zero as in the case with the other two methods
- Effective addition and subtraction can be done even with numbers that are represented with a sign bit without a need for extra circuitries to examine the sign of an operand.
- Using BCD coding system convert 796 to binary. (3mks)
79610 = 01111001011022 7 rem 2 9 rem 2 6 rem 2 3 1 2 4 1 2 3 0 2 1 1 2 2 0 2 1 1 0 1 2 1 0 0 1 0 1
- Using twos complement, workout : 1510 - 810 in binary form. (4mks)
- Convert each of the following to the number system indicated:
- 111.1012 to decimal; (3 marks)
- 111=1x22+1x21+1x20=4+2+1 = 710
0.101 = 1x2-1+1x2-2+1x2-3
= 0.5+0.25+0.125
= 0.62510
⁖111.1012 = 7.62510
- 111=1x22+1x21+1x20=4+2+1 = 710
- 14.687510 to binary [4 marks]
- 14 = 11102
0.6875x2 = 1.375
0.375x2 = 0.75
0.75x2 = 1.50
0.50x2 = 1.00
Decimal portion
0.10112
1110.10112
- 14 = 11102
- 111.1012 to decimal; (3 marks)
- Give one reason why data and information in a computer system needs to be converted to other number systems other than binary.(1mks)
Download Computer Studies Paper 1 Questions and Answers - Lanjet Joint Mock Exams 2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students
