Instructions to Candidates
- This paper consists of two sections A & B
- Answer all the questions in section A
- Answer question 16 and any other three questions in section B
QUESTIONS
SECTION A(40 MARKS)
Answer ALL questions in this section in the spaces provided
- Define term artificial intelligence (1mk)
- List three roles of system analyst (3mks)
- Outline three way IEBC will use technology to ensure free and fare election (3mks)
- Write the following acronymes in full
- WIFI
- HDMI
-
- List two reasons why USB interface has become popular than other interfaces(2mks)
- Give three disadvantage of using serial file organisation (3mks)
- Name three common malicious programs that are harmful to computers (3mks)
- Define the term deadlock as used in operating system (1mk)
- Give any three categories of functions that are available in ms excel (3mks)
- Differentiate between count and count if functions as used in ms excel (2mks)
- Explain why liquid-based powder fire extinguishers are discouraged in a computer laboratory (2mks)
- Explain the following terms as used in computer crimes (2mks)
- Piracy
- Industrial espionage
- List three advantages of using fibre optic cable in networking (3mks)
- Explain two database models (4mks)
-
- Give three ways in which ICT can be used to conserve forests (3mks)
- Give three factors to consider when selecting ICT related career (3mks)
- List four sub categories of system software (4mks)
SECTION B (60 MARKS)
Answer question 16 and any other three questions in this sections
-
- List two examples of
- Third generation languages (2mks)
- Object oriented programming languages (2mks)
- Differentiate between source code and object code (2mks)
- Draw a flow chart that will take two numeric values X and Y compare the two numbers to give the following output:
If X is more than Y, the program should compute the difference of the two numbers
If X is less than Y, the program should compute the sum of the two numbers
If X is equal to Y, the program should compute the product of the two numbers (7mks) - List two repetitive control structures (2mks)
- List two examples of
-
- Differentiate between the following as used in data communication
- Baseband and broadband (2mks)
- Multi-plexing and demulti-plexing (2mks)
- ABC company intends to start their operations across all the East African Countries
- Recommend to them the most ideal computer network that they should use (1mk)
- List three challenges the company is likely to encounter while using the network(3mks)
- With an example state three networking elements that the company will need for them to implement the network (6mks)
- Give one advantage of using unbound media for networking (1mk)
- Differentiate between the following as used in data communication
- Study the worksheet below and answer the questions that follow
1
A
B
C
D
E
F
2
SKY WAYS AGENCIES
3
Product
Region 1
Region 2
Regions 3
Region 4
TOTAL
4
Rexona
3400
3700
4000
4100
5
Lifeboy
2500
2600
2100
2500
6
Omo
6000
6100
6300
1600
7
Ushindi
1200
1500
1400
6400
8
Carmel
7000
6900
7200
8000
9
Total
10
Maximum
11
Average
- Write functions that can be entered to get total, maximum and average of each region (3mks)
- Write down the function that returns the number of sales in the four regions whose values is greater than or equal to 2000 (2mks)
- The prices for region 4 were reduced with n% value which was placed in cell C13 Write a formulae to calculate the new price of product Rexona and applied to other products in the same region (3mks)
- Differentiate between stroke and fill as used in DTP (2mks)
-
- Define text wrap (1mk)
- List four ways you can wrap text on an object (4mks)
-
- State three ways in which a signed binary number can be represented (3mks)
- Convert the following numbers into binary form
- 24710 (2mks)
- 9AC16 (2mks)
- Using two complements compute 2710 - 1310 and leave your answer in binary form (use 8 bits) (3mks)
- Differentiate between logical file and physical file (2mks)
- Explain three parameters that can be used to measure data integrity (3mks)
-
-
- State the importance of information fact finding in system development (1mk)
- State any two advantages and two disadvantages of using interview method for information gathering (4mks)
- Explain three system development theories and methods (6mks)
- Your school wishes to replace the original system with an information system
- With a reason, advise the school on the best change over strategy to implement(2mks)
- Give two challenges the school may encounter while implementing the new system
-
MARKING SCHEME
- Define the term artificial intelligence. (1mk)
- Depicting human like behaviour.
- List three roles of a system analyst. (3mks)
- Reviewing the current manual system
- Working with programmers to construct and test the system.
- Co-ordinating training of users of the new system.
- Outline three ways which IEBC will use technology to ensure free and fair elections. (3mks)
- Bio metrics
- Use of password to access servers
- Controlled access privileges.
- Write the following acronyms in full. (2mks)
- WIFI - wireless fidelity
- HDMI - High Definition Multimedia Interface.
-
- List two reasons why USB interface has become popular than other types . (2mks)
- Flexibility
- Compatibility
- Can connect more than
- Give three disadvantages of using serial file organization. (3mks)
- Cumbersome to search for specific record
- Wastage of space
- Does not support modern high speed requirements.
- List two reasons why USB interface has become popular than other types . (2mks)
- Name three common types of malicious programs that are harmful to computers. (3mks)
- Virus
- Worm
- Back doors
- Trojan horse
- Define the term dead lock as used in operating systems. (1mk)
- A situation where a particular job holds a requested resource and refuses to release it yet it is requesting for another resource.
- Give any three categories of functions that are available in ms-excel. (3mks)
- Mathematical functions
- Logical
- Statistical
- Date & time
- Differentiate between count and count if functions as used in ms-excel. (2mks)
- Count - Counts cells with values
- Count if - conditionally counts cells with values.
- Explain why liquid based and powder based fire extinguisher are discouraged in a computer laboratory. (2mks)
- Liquid - cause corrosion
- short circuit
- Powder - clogging of computer movable parts
- Explain the following terms as used in computer crimes.
- Piracy - illegal copying
- Industrial espionage - spying on a competitor
- List three advantages of using fibre optic cables in networking. (3mks)
- Immunize to EMI and eaves dropping
- Fast
- Supports high bandwidth
- Suitable backbone because they do not suffer from low attenuation
- Suitable for use in highly flammable systems.
- Smaller and lighter than copper.
- Explain any two database models. (4mks)
- Relational - records are stored in tables
- Hierarchical - single path used to access records
- Network model - several links used to access one record.
-
- Give three ways in which ICT can be used to conserve forests. (3mks)
- Surveillance
- Research
- Creating awareness.
- Give three factors to consider when selecting ICT related careers. (3mks)
- Cost of training
- Location of the institution
- Physical look and management of the college
- Whether it offers ICT courses recognized
- Certification both locally or internationally.
- List four sub categories of system software. (4mks)
- Operating system
- Firmware
- Utility ware
- Networking software
- Give three ways in which ICT can be used to conserve forests. (3mks)
-
- List two examples of (2mks)
- Third generation languages
- FORTRAN
- COBOL
- Basic
- C
- Ada
- Object oriented programming languages. (2mks)
- C++
- Java
- Small talk
- Third generation languages
- Differentiate between source code and object code. (2mks)
- Source code - a program which has not been translated that is in program editor window.
- Object code is a program that has been translated.
- Draw a flow chart that will take two numeric values X and Y . compare the two numbers to give the following output:
- If X is more than Y, the program should compute the difference of the two numbers.
- If X is less than Y, the program should compute the sum of the two numbers.
- If X is equal to Y, the program should compute the product of the two numbers. (7mks)
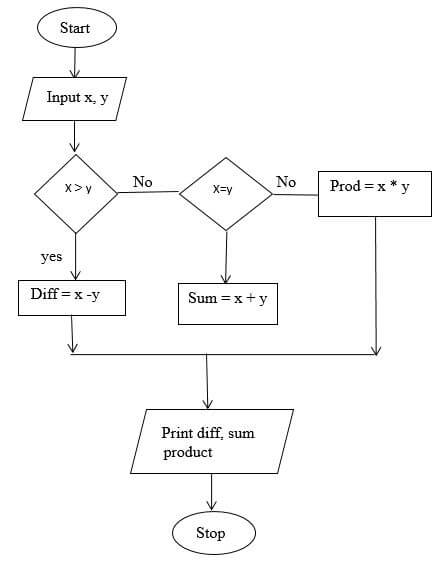
- List two repetitive control structures. (2mks)
- For….do loop
- While …do
- Repeat….until
- List two examples of (2mks)
-
- Differentiate between the following as used in data communication.
- Base band and broadband
- Baseband - signal generate and fed into the transmission medium directly without modulation.
- Broadband - signal is sent over the transmission medium using a particular frequency.
- Multiplexing and demultiplexing
- Multiplexing - processing of sending multiple data signals through the same medium.
- Demultiplexing - is the process of splitting multiplexed signal back into multiple channels.
- Base band and broadband
- ABC company intends to start their operations across all the East African countries.
- Recommend to them the most ideal computer network that they should use. (1mk)
- Wide area network
- List three challenges the company is likely to encounter while using the network. (3mks)
- Compute crimes - hacking, sabotaging etc.
- Over reliance of nilco
- Expenses due to the new running and installation costs.
- Some employees will require to be trained.
- With an example, state three networking elements that the company will need for them to implement the network. (6mks)
- Data communication media e.g bound, unbound media
- Communication devices e.g data ternal equipment I.e computer, mobile phones etc.
- Data circuit terminating equipment I.e modems, switches and routers.
- Network software e.g network operating system protocols
- Recommend to them the most ideal computer network that they should use. (1mk)
- Give one advantage of using unbound media for networking. (1mk)
- Flexibility
- Covers a wide physical location
- Cheap
- Differentiate between the following as used in data communication.
- Study the worksheet below and answer the questions that follow.
1
A
B
C
D
E
F
2
SKY WAYS AGENCIES
3
Product
Region 1
Region 2
Regions 3
Region 4
TOTAL
4
Rexona
3400
3700
4000
4100
5
Lifeboy
2500
2600
2100
2500
6
Omo
6000
6100
6300
1600
7
Ushindi
1200
1500
1400
6400
8
Carmel
7000
6900
7200
8000
9
Total
10
Maximum
11
Average
- Write functions that can be entered to get total, maximum and average of each region. (3mks)
- Total = Sum(B4:B8)
- Maximum = Max(B4:B8)
- Average = Average(B4:B8)
- Write down the function that returns the number of sales in the four regions whose value is greater than or equal to 2000. (2mks)
- = Sum IF(B4: E4, ">2000")
- The prices for region 4 were reduced with n% value which was placed in cell C1. Write a formulae to calculate the new price of product Rexona and applied to other product in the same region. (3mks)
- =E4 - (E4 * & C & 13)
- Differentiate between stroke and fill as used in DTP. (2mks)
- Stroke - outline
- Fill - shading
- Define the term text wrap . (1mk)
- Refers to moving text around the object.
- Give four ways you can wrap text on an object. (4mks)
- Infront
- Back /behind
- Tight
- Square
- Through
- Write functions that can be entered to get total, maximum and average of each region. (3mks)
- State three ways in which a signed binary number.
- Can be represented (3mks)
- Prefixing a sign bit
- Using ones complement
- Using twos complement.
- Convert the following numbers into binary form
- 24710 (2mks)

24710 = 10111111112 - 9AC16 (2mks)
9 A C
1001 1010 1100
9 A C16 = 1001101011002
- 24710 (2mks)
- Using twos complements compute 2710 - 1310 and leave your answer in binary form
(use 8 bits) (3mks)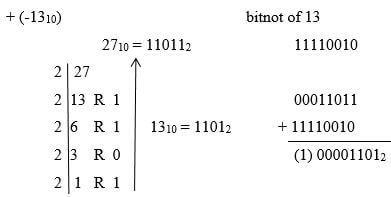
- Differentiate between logical and physical files. (2mks)
- Logical the file is viewed in terms of data items it contain and details of processing operations that can be performed on the data items while physical file is one that is viewed in terms of actual data stored on storage media.
- Explain three parameters that can be used to measure data integrity. (3mks)
- Accuracy - how close an approximation is to the actual value.
- Timeliness - relative accuracy of data in respect to the current state for which it is needed.
- Relevance - the data entered must be relevant to the processing needs and expectations.
- Can be represented (3mks)
-
-
- State the importance of information (fact finding) in system development. (1mk)
- So as to understand the problem and finding out any constraints that may limit the solution.
- State any two advantages and two disadvantages of using interview method when used for information gathering. (4mks)
Advantages- You can seek for clarification in case the response is not clear.
- You can read non-verbal question.
- You can cover much more than what you had initially planned.
- The interviewee can offer solutions to the current problem.
Disadvantages - It is expensive
- Time consuming
- Some respondents may not be free to open up.
- State the importance of information (fact finding) in system development. (1mk)
- Explain three system development theories and methods. (6mks)
- Traditional approach.
- This approach relies on the skills and experience of individual staff members. There is no formal documented methodology to be followed.
- Rapid application development.(RAD)
- This in a highly interactive approach that uses prototyping and active user involvement.
- Structured system development
- This follows sequential stages I.e waterfall, IV-model, spiral and interative model
- Traditional approach.
- Your school wishes to replace the original system with an information system.
- With a reason , advice the school on the best change over strategy to implement. (2mks)
- Parallel - safe and secure
- Phased - safe and secure
- Direct changeover - saves time and resources.
- Give two challenges the school may encounter while implementing the new system.(2mks)
- Loss of data
- High cost of operations and implementation.
- With a reason , advice the school on the best change over strategy to implement. (2mks)
-
Download Computer Studies Paper 1 Questions and Answers - Mincks Group of Schools Mock Examinations 2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students
