Instruction to Candidates.
- This paper consists of TWO sections; A and B.
- Answer ALL the questions in Section A.
- Answer question 16 and any other THREE questions from Section B
Section A (40 Marks)
Answer ALL Questions from this section
- State three reasons why it is difficult to control, detect and prevent computer crimes (3marks)
- Mr. Kala wants to buy a printer to use in his automobile workshop for printing sales orders in duplicates. He has approached you for advice. What printer should he buy? (1 Mark)
Give a reason for your answer. (1mark) - Last year 2020 when corona virus was declared a pandemic internationally most companies allowed employees to telework or work at home and communicate with the office using the Internet. List the hardware, software and services required to access and use the Internet. (3 Marks)
- Using a well labelled diagram, describe the fetch and execute cycle. (3 Marks)
- Ventilation is an important practice in the computer lab because it enhances proper circulation of air. Outline three ways in which air is regulated in the computer room. (3 marks )
- Differentiate between COM ports and LPT ports. (2 marks )
- State any two advantages of the artificial intelligence. (2 Marks)
- The word COM appears several times in an essay. Jane would like to change the word to COMPUTER. Advise her on how she can accomplish this task using a word processor. (2 Marks)
-
- Anita was working on her computer studies project. She was worried of the media to use for storing her data. She settled on a media that used serial file organization. How are files organized on a storage medium using this method? (1 mark)
- List two advantages offered by this type of file organization. (2marks)
-
- Rose wants to send an email to Jack. Explain two items that must be present for the mail to be sent. (2 Marks)
-
- Define the term network protocol (1 Mark)
- Name any two examples of network protocols (1 Mark)
-
- What is the importance of layering in DTP? (1 Mark)
- Distinguish between column guides and margin guides as used in DTP. (2 Marks)
- Study the work sheet below and answer the questions that follow:
A B C D E F 1 2 MOKASA MIXED HIGH SCHOOL 3 ADM.NO NAME MATHS ENGLISH AVERAGE RANK 4 1001 Akinyi 78 85 5 1002 Kamau 89 77 6 1003 Leila 45 46 7 1004 Taita 67 69 8 1005 Mosomtany 98 67 9 Highest Score 10 Lowest Score 11 Average Score - Write a formula that would be entered in cell E4 to compute the average score for Akinyi. (1 Mark)
- Write down a formula that used to return the rank of Leila based on average score. (1 Mark)
- Write down a formula that would return the number of students whose score in English is below 70. (1 Mark)
- The manager of a company wants to improve the security of the computer network. She has decided to use authentication techniques so that employees can identify themselves to the system. Name two authentication techniques and describe how each technique would help keep the data more secure. (3 Marks)
- Mary who works as a systems analyst for JeroKin investments has produced documentation for a newly developed system. State three reasons why both user and technical documentation are needed. (3 Marks)
- Environmentalists plan to test a fast flowing river for pollution. State two advantages of using a computer to do this rather than doing it manually. (2 Marks)
SECTION B (60 MKS)
Answer question 16 (Compulsory)and any other THREE questions from this
Section.
- To maintain a strategic fit Safaricom is introducing a tariff called the mega tariff that will lower costs to Safricom to Safaricom calls and calls to other networks. Calls to Safaricom networks will be charged according to the time of the day as listed below:
- Between 8am to 12 noon – 6 Ksh
- Between 12 noon to 2pm-0.8 Kshs
- Between 6 to 1 am -4Kshs
- between 1 am t 8am- 1Kshs
Internal calls to other networks are charged at a fixed rate of 7 Kshs between 8am to 8pm and to while international calls are charged at a rate of 25 Kshs between 8am to 8pm and Kshs 35 for the rest of the day. All calls are charged per minute usage.
Mr. Wasswa Bbaale a business man who makes both internal and internal calls would like to make maximum use of this of this tariff.- Write a pseudo code that would show him know the charges of calls with an appropriate label when he the inputs type of call and the time where appropriate. Use a 24 hour clock. (8mks)
- Design a flowchart for the pseudo code in 16(a) above (7mks)
-
- Explain how an operating system controls I/O devices. (2marks)
- Maintaining security is one of the functions the operating system. Explain how the operating system maintains security (2marks)
- Distinguish between Indexed sequential and direct file organizations (2marks)
-
- Using appropriate examples, differentiate between distributed and centralized processing modes (3marks)
- State one advantage and one disadvantage of distributed processing modes in 17(d) (i) (2marks)
-
- With reference to an operating system, differentiate between formatting and partitioning. (2marks)
- List any TWO types of user interface. (2mark)
-
- Using eight bits and twos complement, subtract 7810 from 1710. Give your answer in decimal notation (3marks)
- Convert 11011011111.11112 to:
- Octal (2marks)
- Hexadecimal (2marks)
- Decimal (2marks)
- State any Two methods used to gain illegal access to a computer system (2marks)
-
- Distinguish between peer-to-peer and client –server LANs. (2marks)
- Atieno was very happy when she bought a Safaricom 2G modem for she was able to easily connect her computer to the Internet. After six months she noticed it was taking her too long to connect to the Internet. State two possible causes of the problem. (2marks)
-
-
- Explain any two causes of system change. (2marks)
- Explain any THREE causes of system maintenance. (2marks)
-
- Use of questionnaire is one of the most popular fact finding method. State any TWO advantages and TWO disadvantages of using this method to gather data. (2marks)
- Explain the importance of requirement specification phase of Systems development.(2marks)
- Explain TWO reasons why a new system is tested before implementation. (2marks)
-
- State two duties performed by a system administrator. (1mark)
- The principal of a school is attempting to convince his staff to us CAL and CAI software. State one benefit and one limitation of using such software. (2marks)
- State one advantage and one disadvantage of using expert systems in medicine (2marks)
-
-
- Explain three types of communication links that may be used to get an Internet connection (3marks)
-
- Differentiate between the Internet and World Wide Web. (2marks)
- Technology has been blamed for polluting the environment.
Explain how computer technology has contributed to this. (2marks)
- A Company that makes and sells vehicles receives orders from various clients. The company wants to enter their orders into a database. Study the table structure below and answer the questions that follow.
Field Name Data Type Field Size
Order Number Number Long Integer
Order Date Date/Time
Supply Date Date/Time
Product code Text 5
Customer ID Number Long Integer
Customer F Name Text 15
Customer L Name Text 20
Customer phone Number Long integer
Delivery address Text 30
Product Type Text 15
Product Name Text 10
Quantity Ordered Number Long integer
Product Prize Number Long Integer- Split the above structure into THREE tables and for each table identify an appropriate primary key. (5marks)
- Design well labeled tables structures and identify foreign keys (3marks)

MARKING SCHEME
Section A (40 Marks)
Answer ALL Questions from this section
- State three reasons why it is difficult to control, detect and prevent computer crimes (3marks)
- It require well trained expertise which may not be available
- Crimes constantly change
- Some leave no evidences
- Some crimes can not be linked to an individual or organization.
- Mr. Kala wants to buy a printer to use in his automobile workshop for printing sales orders in duplicates. He has approached you for advice. What printer should he buy? (1 Mark)
Dot matrix printer
Give a reason for your answer. (1mark)
Can produce multiple copies with a carbon paper - Last year 2020 when corona virus was declared a pandemic internationally most companies allowed employees to telework or work at home and communicate with the office using the Internet. List the hardware, software and services required to access and use the Internet. (3 Marks)
- Data terminal
- Transmission media
- Internet service providers
- Internet s/w
- Using a well labelled diagram, describe the fetch and execute cycle. (3 Marks)
- Fetch – gets the next program command from the computer’s memory
- Decode – deciphers what the program is telling the computer to do
- Execute – carries out the requested action
- Ventilation is an important practice in the computer lab because it enhances proper circulation of air. Outline three ways in which air is regulated in the computer room. (3 marks )
- Avoiding overcrowding of either machines or users in the room
- Ensuring that the room has enough ventilation points like windows
- Installing air conditioners
- Differentiate between COM ports and LPT ports. (2 marks )
- COM ports are used for serial cables
- LPT ports are used for parallel cables connection
- State any two advantages of the artificial intelligence. (2 Marks)
- Reduction in Human Error
- Helping in Repetitive Jobs
- AI machines have no emotions
- Round-the-clock availability
- The word COM appears several times in an essay. Jane would like to change the word to COMPUTER. Advise her on how she can accomplish this task using a word processor. (2 Marks)
- The word can be edited with Find and Replace
-
- Anita was working on her computer studies project. She was worried of the media to use for storing her data. She settled on a media that used serial file organization. How are files organized on a storage medium using this method? (1 mark)
- Serial file are stored and accessed one after another on a storage medium
- List two advantages offered by this type of file organization. (2marks)
Advantages – simple, chea
- Anita was working on her computer studies project. She was worried of the media to use for storing her data. She settled on a media that used serial file organization. How are files organized on a storage medium using this method? (1 mark)
-
- Rose wants to send an email to Jack. Explain two items that must be present for the mail to be sent. (2 Marks)
- senders address
- Receivers address
- Content
-
- Define the term network protocol (1 Mark)
- Set of rules and procedures that govern how computers and related devices communicate and transfer data signals
- Name any two examples of network protocols (1 Mark)
- TCP/IP
- FTP
- Define the term network protocol (1 Mark)
- Rose wants to send an email to Jack. Explain two items that must be present for the mail to be sent. (2 Marks)
-
- What is the importance of layering in DTP? (1 Mark)
- creating a sense of page harmony
- increases productivity
- For the purpose of editing, working with layers allows for applying changes to just one specific layer.
- Distinguish between column guides and margin guides as used in DTP. (2 Marks)
- Margins a non-printing line that marks the boundary of the top, bottom, right and left margins while column guide is non-printing line that marks the boundary of a column on a page
- What is the importance of layering in DTP? (1 Mark)
- Study the work sheet below and answer the questions that follow:
- Write a formula that would be entered in cell E4 to compute the average score for Akinyi. (1 Mark)
= (c4+d4)/2 or =average(c4:d4) - Write down a formula that used to return the rank of Leila based on average score. (1 Mark)
=RANK(F6,$F$4:$F$8,0) - Write down a formula that would return the number of students whose score in English is below 70. (1 Mark)
=COUNTIF(E4:E8,"<70")
- Write a formula that would be entered in cell E4 to compute the average score for Akinyi. (1 Mark)
- The manager of a company wants to improve the security of the computer network. She has decided to use authentication techniques so that employees can identify themselves to the system. Name two authentication techniques and describe how each technique would help keep the data more secure. (3 Marks)
- Use of biometric methods ie finger prints
- smart cards or hand-held tokens
- password or a simple personal identification number (PIN)
- Mary who works as a systems analyst for JeroKin investments has produced documentation for a newly developed system. State three reasons why both user and technical documentation are needed. (3 Marks)
- Technical - presents how to use and maintain the product.
- User – explains exactly how to use the software
- Environmentalists plan to test a fast flowing river for pollution. State two advantages of using a computer to do this rather than doing it manually. (2 Marks)
- Facilitates a detailed analysis of test results with minimal effort.
- Immediate Grading results are obtained.
SECTION B (60 MARKS)
Answer question 16 (Compulsory) and any other THREE questions from this section.
- To maintain a strategic fit safaricom is introducing a tariff called the mega tariff that will lower costs to safaricom to safaricom calls and calls to other networks. Calls to safaricom networks will be charged according to the time of the day as listed below:
-Between 8am to 12 noon-6 Kshs
-Between 12 noon to 2 pm-0.8 Kshs
-Between 2 pm to 6 pm-2 Kshs
-Between 6 to 1 am-4 Kshs
-Between 1 am to 8 am-1 Kshs
Internal calls to other networks are charged at a fixed rate of 7 Kshs between 8am to 8 pm and to while international calls are charged at a rate of 25 Kshs between 8 am to 8 pm and Kshs 35 for the rest of the day. All calls are charged per minute usage.
Mr. Wasswa Bbaale a business man who makes both internal and external calls would like to make maximum use of this tariff.- Write a pseudo code that would show him know the charges of calls with an appropriate label when he inputs type of call and the time where appropriate. Use a 24 hour clock.
START
READ calltype
CASE calltype OF
“Safaricom”:
READ time
CASE time OF
8 to12: charge=6
12 to14: charge=0.8
14 to 18: charge=2
18 to 1: charge=4
1 to 8: charge=1
ENDCASE
“Other Networks”:
Charge=7
“International”:
READ time
CASE time OF
8 to 20: charge=25
ELSE
Charge=35
ENDCASE
ENDCASE
PRINT “call on mega ongea now at,”charge,”shillings per minute on safaricom to”, calltype,”calls”
STOP
Note: Award marks as follows
Input- ½ calltype, ½ time=1 mark
Output- ½ for output, ½ for appropriate label=1 mark
Logic – selection construct= 1/2
Decision (proper branching)-1 mark for 3 correct selections – ½ for two selections =1 mark
Process- International calls-1
- Calls to other networks – ½
- Safaricom calls- 2½
Use of 24 hour clock- ½ Mark
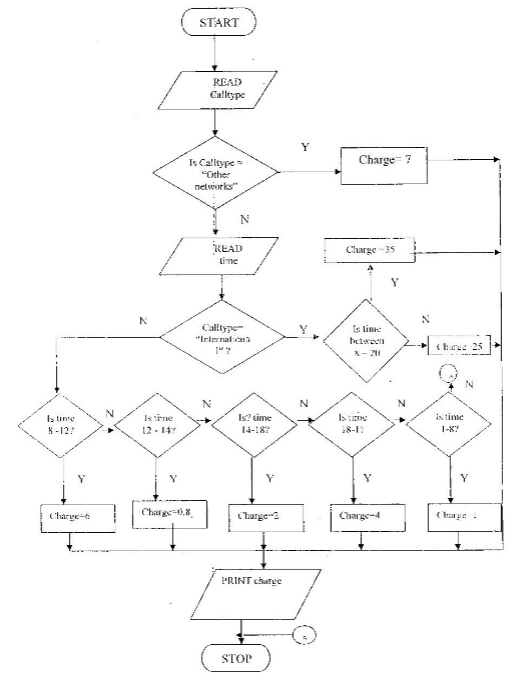
- Design a flowchart for the pseudocope in 16 (a) above (7 marks)
Note: award marks as follows
Correct symbols – ½
Start /stop symbols - ½
Input – ½
Output – ½
Correct logic – ½
Correct use of symbols – ½
Decisions- Based on calltype – ½
- Based on safaricom to safaricom calls-2
- Based on international calls- 1
- Based on calls to other networks- ½
- Write a pseudo code that would show him know the charges of calls with an appropriate label when he inputs type of call and the time where appropriate. Use a 24 hour clock.
-
- Explain how an operating system controls I/O devices. (2 marks)
- The operating system manages the use of input and output devices. This is done by the use buffers .The operating instructs input and output buffers to take inputs from an input device or to take outputs from the processor while the process using the input or output is suspended .when the process which needs the input is made active once again, the operating system will command the buffer to send data.
- Maintaining security is one of the functions of the operating system. Explain how the operating system maintains security.
- Maintaining security-in networks and larger computers each user is given a username or ID and passwords to gain access to the computer system. the operating system keeps a register of all the names so that the only persons with valid usernames or IDs passwords can access the system. The operating system keeps a log which records users logged in, the length of time each user stayed in the system and what they did.
- Distinguish between the following pairs of terms
- Indexed sequential and direct file organizations
- In direct access the computer can go directly to the record you want without reading the preceding records. For example, to access a record, the computer goes directly to it without having to go through what is in in front of it. In indexed sequential file organization the records are stored in a particular order using a key file. However the file in which the records are stored contains an index that lists each record by its key field and identifies its physical location on the disk. The records in an indexed sequential file can either be accessed directly or sequentially (one after the other).
- State any TWO factors to consider when selecting a data processing mode
- Link between applications
- Area of application
- Volume of data to be processed
- Urgency of output
- Indexed sequential and direct file organizations
-
- Using appropriate examples, differentiate between distributed and centralized processing modes. (3 marks)
- Distributed processing modes is a mode of processing where two or more geographically dispersed networked computers belonging to the same organization share all or some processing tasks whereas centralized processing is a mode of processing where a host computer (central computer) does all the processing tasks of the terminals (users) connected to it.
- State one advantage and one disadvantage of the processing modes in 17 (d) (i) above (2 marks)
Centralized processing- Advantages
- The processor idle time is eliminated
- User interaction is possible through the terminals
- Queries are possible since files are held online
- Disadvantages
- Not reliable with regard to data security
- Response time is slow where there are many tasks
- Users have no control over the central processor
- When the processor is down all the operations are paralyzed
- Advantages
- Using appropriate examples, differentiate between distributed and centralized processing modes. (3 marks)
-
- With reference to an operating system ,differentiate between formatting and partitioning (2 marks)
- Formatting is preparing a disk so that the operating system can write information on it by defining the tracks and sectors. Partitioning a disk refers to the process of dividing a large physical disk into two or more logical drives (partitions).
- List any TWO types of user interface. (1 mark)
- Command line
- Menu driven
- Graphical user interface
- With reference to an operating system ,differentiate between formatting and partitioning (2 marks)
- Explain how an operating system controls I/O devices. (2 marks)
-
- Using eight bits and two complement, subtract 7810 from 1710 . Give your answer in decimal notations. (3 marks)
Convert the numbers to binary and make the bits equal-1 mark
7810 - 10011102
1710 - 00100012
Complement the negative number and add 1 to the ones complement
Complement of 01001110 = 10110001 - ½ mark
Add 1 + 1
101100102 - ½ mark
Add the two numbers 000100012
+ 101100102
110000112 - ½ mark
Conversion to decimals (- 128 + 64 + 2 + 1) = - 6110 ½ mark - Convert 11011011111.11112 to:
- Octal (2 marks)
Group the bits in to threes
011 011 011 111 .111 100 - 1 mark
3 3 3 7. 7 4 - ½ mark
= 3337.748 - ½ mark - Hexadecimal (2 marks)
Group the bits in to fours
0110 1101 1111. 1111 - 1 mark
6 D F F - ½ mark
= 6 DF 16 - ½ mark - Decimal (2 marks)
110110111111.1111
210 + 29 + 27 + 26 + 24 + 23 + 22 + 21 + 20 + 0.5 + 0.25 + 0.125 + 0.0625 - 1 mark
1024 + 512 + 128 + 64 +16 + 8 + 4 + 2 + 1 + 0.9375
= 1759.937510 - 1 mark
- Octal (2 marks)
- State any two methods used to gain access to a computer system. (2 marks)
- by using weak access points
- through hacking
-
- Distinguish between peer to peer client server LANS (2 marks)
- Client server LAN is a LAN that consists of requesting computers called clients and a computer that provides services to the clients called the server.
Peer to peer LAN is a LAN where all the computers on the network communicate with one another directly without relying on the server.
- Client server LAN is a LAN that consists of requesting computers called clients and a computer that provides services to the clients called the server.
- Atieno was very happy when she bought a safaricom 2G modem for she was able to easily connect her computer to the internet. After six months she noticed it was taking her too long to connect to the internet .State two possible causes of the problem. (2 marks)
- Many people may be using the same band
- The bandwidth she is using is narrow.
- Distinguish between peer to peer client server LANS (2 marks)
- Using eight bits and two complement, subtract 7810 from 1710 . Give your answer in decimal notations. (3 marks)
-
-
- Explain any TWO causes of system change. (2 marks)
- Errors in the system
- Change in user requirements
- Expansion /growth of the organization
- Technological changes
- Frequent failure of the system
- Explain any THREE causes of system maintenance (2 marks)
- High failure rate of the existing system
- Slowness of the system
- Complaints from users
- Lack of security
- High cost of maintenance
- Explain any TWO causes of system change. (2 marks)
-
- Use of questionnaire is one of the most popular fact finding methods .State any TWO advantages and TWO disadvantages of using this method to gather data. (2 marks)
- Advantages
- Most questionnaires can be answered quickly
- Responses can be tabulated and analyzed quickly
- It is an inexpensive method of fact finding
- Disadvantages
- The number of respondents is usually low
- There is no guarantee that an individual will answer all the questions
- Questionnaires are inflexible.
- Advantages
- Explain the importance of requirement specification phase of system development
- It enables the systems analyst determine the equipments needed for the new system.
- Use of questionnaire is one of the most popular fact finding methods .State any TWO advantages and TWO disadvantages of using this method to gather data. (2 marks)
- Explain TWO reasons why a new system is tested before implementation.
- To detect and remove bugs (errors)
- To ensure the program works properly
- To ensure the program solves the intended problem
-
- State TWO duties performed by a systems administrator
- Installing and configuring servers
- Installing and configuring application software
- Creating and maintaining user accounts.
- Backing up and restoring files
- Monitoring and improving system performance
- Configuring a secure system and maintaining system security.
- The principal of a school is attempting to convince his staff to use CAL and CAI software .State one benefit and one limitation of using such software. (2 Marks)
- Benefits
- They use multi media that make learning more interesting and interactive
- Students can learn on their own and at their own pace even in the absence of a teacher.
- Abstract concepts can often be explained more clearly with the use of a multimedia
- Limitations
- It reduces face to face interaction with others
- Lessons are set in a predefined order and students can only -- follow in that order thus hindering creativity.
- Benefits
- State TWO duties performed by a systems administrator
- State ONE advantage and ONE disadvantage of using expert systems in medicine (2 marks)
- Advantages
- Experts can use the system to arrive at a faster, more accurate conclusion
- It can support a doctor who is doubtful of his decision because of lack of experience.
- Disadvantage
- The system cannot learn from its mistakes
- Lack instinct and common sense which are essential for decision making
- Advantages
-
-
- Explain THREE types of communication links that may be used to get an internet connection.
- Dedicated links-this provides permanent connection to the Internet
- Remote network access-this provides access to the internet via satellite dish
- SLIP/PPP (serial line internet protocol /point-to-point protocol)-to get access to the internet, one must dial up an internet service provider which gives you access to the internet.
-
- Differentiate between the internet and World Wide Web (2 marks)
- The internet is a network of networks that connect computers across the world while the World Wide Web is a part of the internet that which stores information in multimedia form.
- Technology has been blamed for polluting the environment .Explain how the computer technology has contributed to this. (2 marks)
- The use of solvents in the manufacturing of computers can harm the environment.
- Disposal of old and used computer parts are harmful to the environment because they do not decompose.
- Differentiate between the internet and World Wide Web (2 marks)
- A company that makes and sells vehicles receives orders from various clients .the Company wants to enter their orders in to a database. Study the table structure below and answer the questions that follow.
Field name data type field size
Order number number long integer
Order date date/time
Supply date date/time
Product code text 5
Consumer ID number long integer
Customer FName text 15
Customer Lname text 20
Customer phone number long integer
Delivery address text 30
Product type text 15
Product name text 10
Quantity ordered number long integer
Product prize number long integer- Split the above table structure in to THREE tables and for each table identify an appropriate primary key. (5 marks)
Order table
Order number number long integer
Order date date/time
Ordered quantity number long integer
Supply date date/time
Primary key: order number
Customer table
Customer ID number long integer
Customer FName text 5
Customer LName text 20
Customer phone number long integer
Delivery address text 30
Primary key: customer ID
Product table
Product code text 5
Product type text 15
Product name text 10
Product prize number long integer
Primary key: product code.
- Split the above table structure in to THREE tables and for each table identify an appropriate primary key. (5 marks)
- Explain THREE types of communication links that may be used to get an internet connection.
Download Computer Studies Paper 1 Questions and Answers - Joint Pre-Mock Exams 2021/2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students