QUESTIONS
-
- A computer laboratory should be constantly kept dust and smoke free.
Specify two effects that dust would have on the operation of computers. (2 marks) - Why should you first switch on the UPS before switching on the system unit and the monitor? (2 mark)
- A computer laboratory should be constantly kept dust and smoke free.
- Explain the meaning of backup. (2 marks)
- State the following types of transcription errors. (2 marks)
- 3455 instead of 3456
- Smith instead of simth
-
- State three ways used to represent a negative number. (3 marks)
- Perform the following binary arithmetic giving the answer in decimal notation.
1110.0111 + 1101001.011 (2 marks)
- Distinguish between data privacy and data integrity as used in computing. (2 marks)
- Differentiate between a primary key and a foreign key while designing a database. (2 marks)
- Distinguish between ‘count’ and ‘count if’ functions as used in spreadsheets. (2 marks)
- Explain the impact of Information Technology on organization in each of the following areas. (2 marks)
- Competition.
- Pace of growth.
- List two roles performed by system analyst. (2 marks)
- Explain the following internet related terms. (4 marks)
Sign IN
Search engine
Surf
Sign up - In Kenya Tea Packers Company, several people are employed as record clerks, typists and messenger. The company intends to introduce a computerized system in all the departments. Suggest three reasons that would make workers unhappy with the new system. (3 marks)
- State two magnetic Storage devices. (2 marks)
- State three functions of Central Processing Unit. (3 marks)
- Explain two ways of protecting data and information in a database against unauthorized access (2marks)
-
- Name two ways in which data can be input into a computer, and state the device that can be used in each case. (2mks)
- Explain why a buffer is used in the output of data to a line printer (1mk)
SECTION B
(Answer question 16 and any other three questions from this section)
-
- List two programming language translators. (2mks)
- State three advantages of using low level programming languages. (3mks)
- Give two methods you would use in error detection during program testing. (2mks)
-
- Study the flowchart below and write a pseudo-code for the flowchart. (7mks)

- Name the control structures used in the flow chart above. (1mks)
- Study the flowchart below and write a pseudo-code for the flowchart. (7mks)
-
- Explain any THREE functions of system software in a computer (3mks)
- As a computer student you have been asked to assist in buying an input device. State any four factors to consider when buying input devices. (4mks)
- Explain three problems associated with using e-mail technology for communication. (6mks)
- State three advantages of integrated software as opposed to single purpose. (3mks)
-
- List and describe four strategies for converting from an old system to a new system. (4mks)
-
- Distinguish between private data and confidential data. (2mks)
- What can be done to stop illegal access to a computer laboratory by unauthorized people? (3mks)
- List four areas that would be considered in the requirement specification. (4mks)
- Name any two areas covered in feasibility report during system analysis and design. (2mks)
-
- What is the hexadecimal equivalent of 7678 (3mks)
- Use one’s compliment to solve the following sum: -510 (2mks)
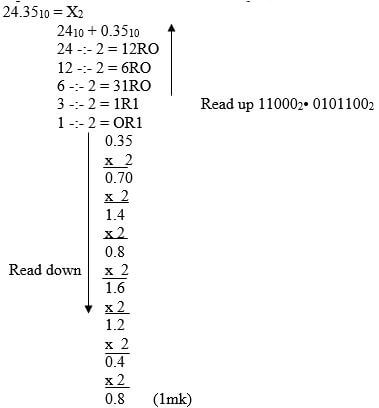
- Compute the values of X in the following expressions
- 24.3510 = X2
- 6A13H = X10 (2mks)
- Using two’s complement compute (5mks)
3610 – 2510
-
- On her first day at work as a school librarian, Sera notices that book records are kept manually using a card system. She suggests to the Principal that they use a database. State three reasons why using a database would be helpful to the librarians (3mks)
- Give four examples of DBMS programs which could be used. (2mks) Lotus
- The manager of Pacific Company Ltd uses a database to keep records of his employees as shown in the table below. Use this information to answer the questions that follow.
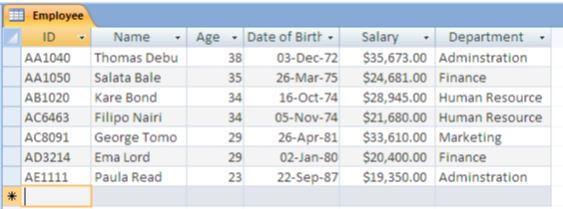
- Name and explain the appropriate data type for
ID: (1mk)
Age: (1mk)
Salary (1mk) - Write a query expression to display details of employees working in the Administration department (3mks)
- Name and explain the appropriate data type for
- The function =AVERAGE (B2:B8) in cell B9 has been copied and pasted to cells C9 to K9 in spreadsheet.
- What would be the formula at cell D9 (2mks)
- Explain the type of cell referencing used in the above formula (2mks)
MARKING SCHEME
-
- A computer laboratory should be constantly kept dust and smoke free.
Specify two effects that dust would have on the operation of computers. (2 marks)
- Dust may cause malfunction of read/write heads of the drive
- Dust May cause failure of a fan that cools the processor
- Why should you first switch on the UPS before switching on the system unit and the monitor? (2 mark)
Because the computer get power from the UPS
- A computer laboratory should be constantly kept dust and smoke free.
- Explain the meaning of backup. (2 marks)
- Making of copies of data, programs incase the originals are corrupted or lost
- It is used to protect data from accidental erasure or hardware problems
- State the following types of transcription errors. (2 marks)
- 3455 instead of 3456
- Misreading errors
- Smith instead of simth
- Transposition
- 3455 instead of 3456
-
- State three ways used to represent a negative number. (3 marks)
- Ones complement
- Twos complement
- Perform the following binary arithmetic giving the answer in decimal notation.
1110.0111 + 1101001.011 (2 marks)
1110.0111
1101001.0110 +
110111.1101
119.8125 or 11913/16
- State three ways used to represent a negative number. (3 marks)
- Distinguish between data privacy and data integrity as used in computing. (2 marks)
- Data privacy -keep data secretly so that unauthorized people don't access it
- Data integrity- correctness, completeness and accuracy of data
- Differentiate between a primary key and a foreign key while designing a database. (2 marks)
- Primary key-unique field that identifies a record in a database
- Foreign key-a primary key in another table once the tables are linked
- Distinguish between ‘count’ and ‘count if’ functions as used in spreadsheets. (2 marks)
- Count- counts cells that contain values in a range of cells
- Count if- counts cells that meet a given criteria in a range of cells.
- Explain the impact of Information Technology on organization in each of the following areas. (2 marks)
- Competition.
- Ability to advertise on the internet
- Improve quality of goods
- Reduced operational cost
- Pace of growth.
- Reduced cost
- Reduced need for man power
- Reduced space requirement
- Greater output
- Competition.
- List two roles performed by system analyst. (2 marks)
- Analyses and assesses suitability of a system for computerization
- Programmers builds on the analyst results to create a new computer based system
- Trains staff on the new system
- He collects facts from the users
- Works hand in hand with programmers to create a new computer based program
- Explain the following internet related terms. (4 marks)
- Sign IN - Enter user name and password to authenticate the access to e-mail account
- Search engine -Site used for searching material from the internet
- Surf - Browsing or accessing internet resources.
- Sign up - Registering to have an account for e-mail or other communication media
- In Kenya Tea Packers Company, several people are employed as record clerks, typists and messenger. The company intends to introduce a computerized system in all the departments. Suggest three reasons that would make workers unhappy with the new system. (3 marks)
- Job replacement
- Retraining on use of computers
- Side effect of using computer
- Loss of status Quo
- State two magnetic Storage devices. (2 marks)
- Hard disk
- Floppy disk
- Jaz disk
- Zip disk
- Magnetic tape
- State three functions of Central Processing Unit. (3 marks)
- Control the use of the main memory in storing data & information
- Processing and manipulation of data into useful information
- Manages execution of instructions
- Give commands to all parts of the computer
- Control the sequence of operations within the computer
- Explain two ways of protecting data and information in a database against unauthorized access (2marks)
- Password protection – A password to open or exit the database file i.e. let’s any user who wishes to do any action.
- Data encryption – If the database is to be sent electronically encryption secures the data from un authorized access
- User and group permission to users on data base object such as queries form and reports
- User level security – this feature is used to assign permission to users in order to limit user access to certain database object
-
- Name two ways in which data can be input into a computer, and state the device that can be used in each case. (2mks)
- Console input (keyboard)
- Voice input –(microphone)
- Explain why a buffer is used in the output of data to a line printer (1mk)
To store information temporarily to cope with the difference in speeds of the various peripherals (input / output) devices.
- Name two ways in which data can be input into a computer, and state the device that can be used in each case. (2mks)
SECTION B
(Answer question 16 and any other three questions from this section)
-
- List two programming language translators. (2mks)
- Assemblers
- Compilers
- Interpreters
- State three advantages of using low level programming languages. (3mks)
- Program execution is immediate
- They require no compilation, no interpretation/ translation hence they are faster.
- Hardware optimization is extensive
- Program developed takes less memory space
- Suitable for micro devices
- Easy to design electronic device
- Give two methods you would use in error detection during program testing. (2mks)
Use of disk checking
Using debugging utilities
Using test data -
- Study the flowchart below and write a pseudo-code for the flowchart. (7mks)

PSEUDO CODE
START
Input A,B,C
Calculate Sum = A+B+C
IF SUM > 200 THEN
SUM = SUM – 30
ELSE
SUM= SUM + 20
ENDIF
PRINT SUM
STOP
- Name the control structures used in the flow chart above. (1mks)
- Study the flowchart below and write a pseudo-code for the flowchart. (7mks)
- List two programming language translators. (2mks)
-
- Explain any THREE functions of system software in a computer (3mks)
- Supports the development of other application software.
- Supports the execution of other application software.
- Monitors the effective use of various hardware resources e.g. CPU, memory, peripherals etc.
- Communicates and controls the operation of peripheral devices such as a printer.
- Performs a variety of system utility functions
- As a computer student you have been asked to assist in buying an input device. State any four factors to consider when buying input devices. (4mks)
- Type of data to be input -
- user friendliness
- Speed of the input device
- Volume of data
- Accuracy of the input device
- Cost of the device
- Availability of the device
- Explain three problems associated with using e-mail technology for communication. (6mks)
- Threat to privacy
- Organization ‘System admn’ can snoop into people mail.
- Email can be unsolicited/spam mail.
- Messages can be sent to masses of people without their consents
- Vulnerability of machine failures
- Emails can be overwhelming when many messages are received leading email overloading and going through each of them can be taxing.
- Email can be faked.
- Email attached can be a source of viruses.
- Email technology not available to all/technology illiteracy.
- Encourage illicit communication such as immoral behavior
- State three advantages of integrated software as opposed to single purpose. (3mks)
- Takes shorter time to install
- Error free since they are thoroughly tested.
- They are readily available for almost all the tasks
- The integrated software is compatible and has common features so easy to learn
- Explain any THREE functions of system software in a computer (3mks)
-
- List and describe four strategies for converting from an old system to a new system. (4mks)
- Direct approach- user simply stops using old system and starts using the new one
- Parallel approach- old and new system is operated side by side until the new system has shown it is reliable.
- Phased approach -parts of a new system are phased in separately either at different times or all at one in groups
- Pilot approach- entire system is tried out but only by some users
-
- Distinguish between private data and confidential data. (2mks)
- Private data – belongs to an individual and must be accessed through direct permission from the owner
- Confidential data – held by government or organization about people but can be seen by authorized people only.
- What can be done to stop illegal access to a computer laboratory by unauthorized people? (3mks)
- Fit strong metallic grills and locks to doors
- Don’t welcome strangers into the lab
- Install alarms
- Employ guards
- Burglar proof
- List four areas that would be considered in the requirement specification. (4mks)
- Output specification
- Input specification
- File /data/tables
- Hard ware/soft ware
- Name any two areas covered in feasibility report during system analysis and design. (2mks)
- Schedule
- Users
- Environment
- Technology
- Distinguish between private data and confidential data. (2mks)
- List and describe four strategies for converting from an old system to a new system. (4mks)
-
- What is the hexadecimal equivalent of 7678 (3mks)
Step1convert 7678 to decimal
7x 82 + 6x81 +7x80
448+48+7=50310
Step2
Convert 50310 to hexadecimal
7678=IF 71616
503
Rem
16
31
7
16
1
15
1
1
Correct method/ step and answer give a mark
- Use one’s compliment to solve the following sum: -510 (2mks)
2
5
Rem
2
2
1
2
1
0
1
1
- Compute the values of X in the following expressions
- 24.3510 = X2
- 6A13H = X10 (2mks)
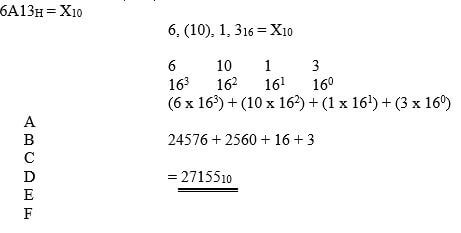
- 24.3510 = X2
- Using two’s complement compute (5mks)
3610 – 2510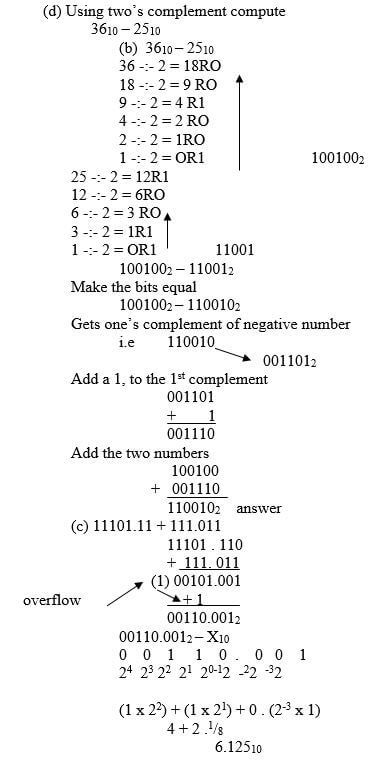
- What is the hexadecimal equivalent of 7678 (3mks)
-
- On her first day at work as a school librarian, Sera notices that book records are kept manually using a card system. She suggests to the Principal that they use a database. State three reasons why using a database would be helpful to the librarians (3mks)
Unnecessary duplication
Time wastage
Poor update of records - Give four examples of DBMS programs which could be used. (2mks)
approach, Ms access, ms SQL server, Oracle, DbaseIV - The manager of Pacific Company Ltd uses a database to keep records of his employees as shown in the table below. Use this information to answer the questions that follow.

- Name and explain the appropriate data type for
ID: text
Age: number
Salary currency - Write a query expression to display details of employees working in the Administration department (3mks)
Select * from table where department=”administration”
- Name and explain the appropriate data type for
- The function =AVERAGE (B2:B8) in cell B9 has been copied and pasted to cells C9 to K9 in spreadsheet.
- What would be the formula at cell D9 (2mks)
- Explain the type of cell referencing used in the above formula (2mks)
Relative cell referencing
- On her first day at work as a school librarian, Sera notices that book records are kept manually using a card system. She suggests to the Principal that they use a database. State three reasons why using a database would be helpful to the librarians (3mks)
Download Computer Studies Questions and Answers - KCSE 2022 Pavement Form 4 Trial 1 Pre-Mock Examination.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

