Instructions to candidates:
- Write your name, admission number and name of your school in the spaces provided.
- This paper consist of TWO sections, A and B.
- Answer ALL the questions in section A.
- Answer question 16 and any other THREE questions from section B.
- All answers should be written in the spaces provided on the question paper.
- This paper consists of 12 printed pages.
- Candidates should check the question paper to ascertain that all the pages are printed as indicated and no questions are missing.
- Candidates should answer the questions in English.
|
Section |
Question |
Maximum Score |
Candidate’s Score |
|
A |
1 – 15 |
40 |
|
|
B |
16 |
15 |
|
|
17 |
15 |
||
|
18 |
15 |
||
|
19 |
15 |
||
|
20 |
15 |
||
|
Total Score |
|||

QUESTIONS
SECTION A (40 marks)
- Speech recognition devices are used to capture natural sound and convert the input into digital form. State two problems related to speech recognition devices. (2 marks)
- One classification of software is system software
-
- What is meant by system software (1 mark)
- Give one example of system software. (1 mark)
-
- Name one other software classification (1 mark)
- Give one example of this type of software (1 mark)
-
- Last year 2020 when corona virus was declared a pandemic internationally most companies allowed employees to telework or work at home and communicate with the office using the Internet. List the hardware, software and services required to access and use the Internet. (3 marks)
- Suggest any three reasons why reservation systems are not yet fully implemented by bus operating companies in Kenya (3 marks)
- Name the three constituent parts of a computer file. (3 marks)
- State two reasons for system reboot. (2 marks)
- Differentiate between Batch processing and real time processing modes. (2 marks)
- Outline three ways computers can be used to enhance marketing. (3 marks)
- Most computerized security systems make use of biometric analysis. Name three physical features of human beings that can be considered in this analysis. (3 marks)
- Differentiate between high definition multimedia interface and Firewire interface. (2 marks)
- Give two reasons why powder and liquid extinguishers are not recommended unlike gaseous extinguishers. (2 marks)
- Differentiate between Bcc and cc in an email. (2 marks)
- Since the invention of the first generation of digital computers, much advancement has been realized in the sector of information and technology. Explain two characteristics which have been improved from the first generation to the modern computers. (2 marks)
- Give three reasons why a mobile phone is regarded to as a computer. (3 marks)
- The following is an excel worksheet showing the performance of students in Tana class.
Using the above worksheet write the formula to calculate the values in cells labeled. (4 marks)A
B
Adm
C
Student name
D Cat1/50
E Cat2/50
F
Total /40
G
Exam / 60
H
Total
1 4321 DollineMbesa 30 28 (a) 45 (b) 2 4333 SelinaMbugua 20 29 55 3 4330 Winnie Wanjema 25 26 50 4 4322 MagaretWambari 27 24 43 5 4324 FaniNjuguna 28 24 42 6 Maximum (c) 7 Minimum 8 Average (d) 9
SECTION B
Answer question 16 (compulsory) and any other three questions from this section
-
- State and describe two types of error that can occur in programming (2 marks)
- Differentiate between compiler and interpreter as used in programming. (2 marks)
- Name the two major developments during the second generation programming languages (2 marks)
- Study the pseudocode below and answer the questions that follow.
Start
N=0
X=0
While n < 3
Repeat
X = X + 1
Until x < 2
N = N +1
End while
Print N, X
Stop- What will be the output from the program (2 marks)
- Draw a flowchart that was used to come up with the following pseud code (7 marks)
-
- List three advantages of wireless technology (3 marks)
- The computer is to be networked, name one extra device that should be fitted on every computer to enable this to happen (1mark)
- Data transmission via the internet is done using a mode known as packet switching. Describe this data transmission mode. (2 marks)
- The diagram below shows four common network topologies A, B, C and D.
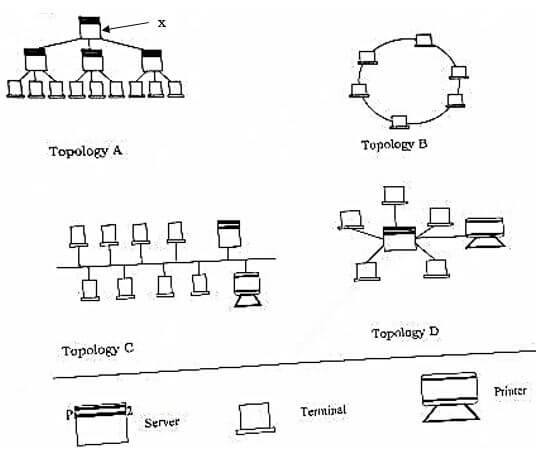
- Name the network topologies A, B, C and D (4 marks)
A
B
C
D - Explain what happens if server X in topology A fails (1 mark)
- List two advantages with network topology B (2 marks)
- List two disadvantages associated with network topology D (2 marks)
- Name the network topologies A, B, C and D (4 marks)
-
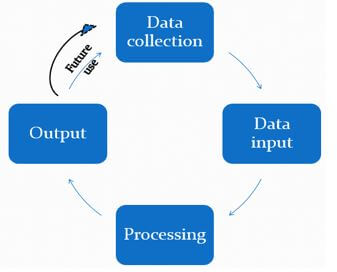
- In order to generate information from data items, a set of processing activities have to be performed on the data items in a specific sequence depending on the desired result. Draw a well labeled diagram to illustrate data processing cycle. (2 marks)
- A data entry clerk experiences some common errors when typing. Most of the time, she finds that:
- After every calculation, the result is less than the expected number of digits required e.g. 345.7896543 the result is given as 345.789.
- Different characters are typed wrongly, for example instead of typing 12873457 she types 128734S7.
Identify the two types of errors commonly experienced by the clerk during data processing in (i) and (ii) above respectively. (2 marks)
- Briefly describe any three electronic data processing modes: (6 marks)
- State three ways a user can ensure data accuracy is maintained during data processing (3 marks)
- State two advantages of a computerized filing system as used in data processing. (2 marks)
-
- Define a database model (1 mark)
- List two advantages of using database systems (2 marks)
- In a database system, data integrity ensures the correctness and completeness of the data in the database. Differentiate the following types of integrity constraints:
- Validity integrity (1 mark)
- Entity integrity (1 mark)
- Referential integrity (1 mark)
- Briefly describe the three database models (3 marks)
- Using diagrams describe the following three types of relationships. (3 marks)
- One – to – one
- One – to – many
- Many – to – many
- Explain any three features of database. (3 marks)
-
- State three standard coding scheme used computing and electronic systems. (3 marks)
- Convert each of the following numbers
- 101.0012 to decimal. (3 marks)
- 5E6H to octal. (3 marks)
- Add 110.012 to 11001.01012 (2 marks)
- Using two’s compliment perform the following arithmetic leaving your answer in binary form. (4 marks)
1310 - 1010

MARKING SCHEME
- Speech recognition devices are used to capture natural sound and convert the input into digital form. State two problems related to speech recognition devices. (2 marks)
- Recognition rate is slow – the number of words in English and the number of words which can be said at a given point (known as branching factor) mean that response rates are still relatively slow.
- Limited vocabularies – most systems are still limited to words in isolation; connected speech is much harder to get right than segmented speech. A computer may not respond to a voice command that has speech related problems like accents, Inflations and varying tones.
- Speaker variability–The speed, pitch, range, rhythm. Intonation, loudness and pronunciation of an individual can vary (especially if they a have a cold).
- Homophones – Some words e.g. see and sea, sound the same.
- Problems of speech context – A computer cannot understand different contexts and meanings of speech because it is ‘literal minded’.
- Background noise –Can upset voice input without a shielded mouthpiece on the microphone.
- One classification of software is system software
-
- What is meant by system software (1 mark)
- System software refers to the programs that control the performance of the computer.
- Give one example of system software. (1 mark)
- Utility programs, O/S, compilers and interpreters
- What is meant by system software (1 mark)
-
- Name one other software classification (1 mark)
- Application software
- Give one example of this type of software (1 mark)
- Word processors, spreadsheet, DBMS, DTP
- Name one other software classification (1 mark)
-
- Last year 2020 when corona virus was declared a pandemic internationally most companies allowed employees to telework or work at home and communicate with the office using the Internet. List the hardware, software and services required to access and use the Internet. (3 marks)
- Data terminal
- Transmission media
- Internet service providers
- Internet s/w
- Suggest any three reasons why reservation systems are not yet fully implemented by bus operating companies in Kenya (3 marks)
- Computer illiteracy among customers
- Lack of trust in online transactions
- Lack of fast communication network
- Low penetration of communication infrastructure
- High initial cost of hardware and software required for systems
- Lack of skilled programmes to develop the systems locally
- Name the three constituent parts of a computer file. (3 marks)
- Character
- Record
- File
- State two reasons for system reboot. (2 marks)
- Recover from a problem such as system hung, grub
- So that the computer can handle maintenance services such as backing up and restoring data
- Due to power outage
- Add or remove hardware
- Customize CMOS settings or Change Kernel parameters
- Repair system configuration files
- Allow auto update files to run
- Differentiate between Batch processing and real time processing modes. (2 marks)
- Batch processing is where data is first collected and data collected is processed/at once
- Real-time —data is processed so quickly such that the results (output) produced are able to influence, control, or affect the outcome of the activity currently taking place
- Outline three ways computers can be used to enhance marketing. (3 marks)
- E-commerce
- Electronic presentation
- Advertising
- Most computerized security systems make use of biometric analysis. Name three physical features of human beings that can be considered in this analysis. (3 marks)
- Eyes pattern
- Finger prints
- Voice
- Computer technology advances so rapidly that the life of computer is just a few years.
- The increasing turnover rate of computer equipment results in a rapidly growing waste stream that is hazardous to our environment
- Differentiate between high definition multimedia interface and Firewire interface. (2 marks)
- High definition interface is an interface used for transmitting digital audio and video data from computer to a projector, TV or audio device. Firewire It is similar to USB but has a higher transmission rate hence it is suitable for streaming video from digital cameras to a computer
- Give two reasons why powder and liquid extinguishers are not recommended unlike gaseous extinguishers. (2 marks)
- Liquid –based extinguisher may cause rusting and corrosion of computer components
- Powder particles may increase friction, clogging and wearing of movable computer parts
- Differentiate between Bcc and cc in an email. (2 marks)
- In cc, all the recipients of the mail are able to see other recipients of the same mail. Bcc: In Bcc, all recipients of the mail are not able to see other recipients.
- Since the invention of the first generation of digital computers, much advancement has been realized in the sector of information and technology. Explain two characteristics which have been improved from the first generation to the modern computers. (2 marks)
- Size: Computers are becoming smaller and smaller since they involve Very Large Scale Integration of electronic components leading to the introduction of very small computers like palmtops, notebooks and laptops.
- Speed: Computers are becoming faster in processing of data due to invention of very high speed processors.
- Storage Capacity: This has been increased. Initial devices could only store several kilobytes and they took long to store and retrieve data.
- Energy consumption and heat emission: The modern computers consume little energy and emit little heat.
- Give three reasons why a mobile phone is regarded to as a computer. (3 marks)
- It is electronic
- It has a display unit
- It has a keypad
- It has memory for storage
- It is programmable
- Using the above worksheet write the following formula to calculate the values in cells labeled
- = (D1+E1/100)*40) (1 mark)
- = sum(F1:G1) (1 mark)
- = MAX(H1:H6) (1 mark)
- = AVG (H1:H6) (1 mark)
-
- State and describe two types of error can occur in programming (2 marks)
- Syntax errors- are mistakes in the programming language’s keywords or control structures. They show up when the program is being entered.
- Runtime errors- show up when the program is run. The program begins to run but the computer cannot carry out one of the instructions and crashes.
- Logical errors-occur when the program runs but produces wrong results. They show up when the program is being tested.
- Differentiate between compiler and interpreter as used in programming.(2 marks)
Compiler
Interpreter
Translates the entire source code all at once before execution
Translate the source code line by line
Execution is faster
Execution is slower
They require large space
Requires less space
- Name the two major developments during the second generation programming languages (2 marks)
- Introduction of structured programming style
- The use of control structures
- State and describe two types of error can occur in programming (2 marks)
-
- Study the pseudocode below and answer the questions that follow.
Start
N=0, X=0
While n < 3 Repeat
X = X + 1 Until x < 2
N = N +1
End while
Print N, X
Stop- What will be the output from the program (2 marks)
- X - 4
- N - 3
- Draw a flowchart that was used to come up with the following pseud code (7 marks)
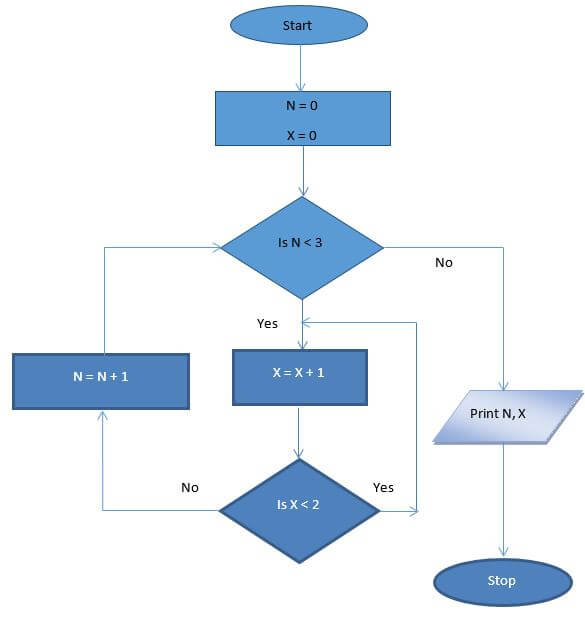
- What will be the output from the program (2 marks)
- Study the pseudocode below and answer the questions that follow.
-
- List three advantages of wireless technology (3 marks)
- Flexible as compared to bounded media i.e devices can be moved around without losing access to the network
- Can span large geographical areas easily
- Can take place via satellite even very remote areas that do not have high cost physical infrastructure like telephone lines
- The computer is to be networked, name one extra device that should be fitted on every computer to enable this to happen (1mark)
- NIC (network interface Card)
- Data transmission via the internet is done using a mode known as packet switching. Describe this data transmission mode. (2 marks)
- Refer to the process over the network of breaking down into discrete systematic steps the data transmission process and at each step a certain action takes place.
- The diagram below shows four common network topologies A, B, C and D
- Name the network topologies A, B, C and D (4 marks)
- A – Hierarchical /tree
- B – Token-ring
- C-Bus/line/multi-drop
- D-Star
- Explain what happens if server X topology A fails. (1 mark)
- Terminal 4, 5, 6 cease to function or cut off from the network.
- List two problems associated with network topology B. (2 marks)
- Difficult to trouble shoot
- Duplication of resources
- Packets collision causing data distortion
- When a terminal fails the network fails
- To add a terminal one has to disable the network
- List two disadvantages associated with network topology D (2 marks)
- Uses many cables
- If the server fails the entire system fails
- All communication must pass through server
- Difficult to implement in a wide area of long distance.
- Name the network topologies A, B, C and D (4 marks)
- List three advantages of wireless technology (3 marks)
-
- In order to generate information from data items, a set of processing activities have to be performed on the data items in a specific sequence depending on the desired result. Draw a well labeled diagram to illustrate data processing cycle. (2 marks)
- A data entry clerk experiences some common errors when typing. Most of the time, she finds that:
- After every calculation, the result is less than the expected number of digits required e.g. 345.7896543 the result is given as 345.789.
- Different characters are typed wrongly, for example instead of typing 12873457 she types 128734S7.
Identify the two types of errors commonly experienced by the clerk during data processing in (i) and (ii) above respectively. (2 marks)- Truncation error
- Misreading error
- Briefly describe any three electronic data processing modes: (6 marks)
- Multiprogramming – More than one program are executed apparently at the same time by a single processor
- Real-time – involves processing of incoming data as soon as it occurs, up – data the transaction file and gives an immediate response that would affect the current as they happen.
- Online processing- data is processed immediately it is received
- State three ways a user can ensure data accuracy is maintained during data processing (3 marks)
- Using modern data capture devices (direct data capture) such as barcode readers, optical character readers, digital cameras etc., which capture/enter data with minimum user involvement.
- Design user interfaces that minimizes chances of invalid data entry.
- Double entry checks
- Use of error detection and correction software when transmitting and processing data.
- Use of automated data verification and validation routines in the data processing system.
- State two advantages of a computerized filing system as used in data processing. (2 marks)
- Information takes up much less space than the manual filing
- It is much easier to update or modify information
- It offers faster access and retrieval of data
- It enhances data integrity and reduces duplication
- It enhances security of data if proper care is taken to secure it.
- In order to generate information from data items, a set of processing activities have to be performed on the data items in a specific sequence depending on the desired result. Draw a well labeled diagram to illustrate data processing cycle. (2 marks)
-
- Define a database model (1 mark)
- The arrangement of data in a file which determine the access method.
- List two advantages of using database systems (2 marks)
- Control of data redundancy
- Maintain data consistency
- Sharing of data
- Improved date integrity
- Economy of scale
- Improved security
- In a database system, data integrity ensures the correctness and completeness of the data in the database. Differentiate the following types of integrity constraints:
- Validity integrity (1 mark)
- Ensure that the data fields contain the correct data type
- Entity integrity (1 mark)
- Primary key cannot have empty values.
- Referential integrity (1 mark)
- A foreign key can only have the values of the relevant primary key.
- Validity integrity (1 mark)
- Briefly describe the three database models (3 marks)
- Hierarchical model – Records in the database can be related in one parent only but can have more child records.
- Network – any record can be related with any other record.
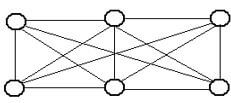
- Relational model – all data is logically structured within tables.
- Hierarchical model – Records in the database can be related in one parent only but can have more child records.
- Using diagrams describe the following three types of relationships. (3 marks)
- One to one – for any member of A there is only one member of B and for any member in B there is one member of A.

- One to many – for a single member of A, there may be multiple associations with it B but for any B member there is only one member of A associated with it.
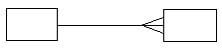
- Many to many – for member in A there may be more members of B and for any member in B there may be many members of A

- One to one – for any member of A there is only one member of B and for any member in B there is one member of A.
- Explain any three features of database. (3 marks)
- Tables – holds related records, organised in rows and columns
- Forms – data capture tool
- Queries – statement used to extract, change analyses or request for a specific data from one or more tables
- Reports – provides the user with a means to specify the output layout and what is to be output/printed
- Define a database model (1 mark)
-
- State three standard coding scheme used computing and electronic systems. (3 marks)
ASCII
BCD
EBCDIC - Convert each of the following numbers
- 101.0012
Whole part =>( 1 x 20) + ( 0 x 21) + ( 1 x 23) = 1 + 0 + 8 = 9
Fraction part => ( 0 x 21) + ( 0 x 2-2) + ( 1 x 23) = 2-3 = 0.125
∴ 101.0012 = 9.12510
- 101.0012
-
- 5E6H to octal. (3 marks)
5E6H 010111100110
010 111 100 110
2 7 4 6
27468 - 110011.0101
+ 110.0100
111001.10012
- 5E6H to octal. (3 marks)
- 1310 to binary
13 – 16 13 – 8 5 – 4 1 – 2 1-1
6 1 1 0 1
1310 = 011012 → 8-bit → 000011012
1010 to binary
10 – 16 10 – 8 2 – 4 2 – 2 0 – 1
0 1 0 1 0
=010102 8-bit 000010102
Ones complement of 000010102 → 111101012
Two’s complement 111101012
+1
111101102
1310 + (-1010) = 000011012
+ 1111011012
(1) 000001012
= 000001012
- State three standard coding scheme used computing and electronic systems. (3 marks)
Download Computer Studies Paper 1 Questions and Answers - Cekenas Pre Mocks 2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

