- This paper consists of TWO Sections A and B
- Answer all questions in Section A
- Answer question 16 (compulsory) and any other THREE question in section B
SECTION A:ANSWER ALL QUESTIONS
- Define the following terms (2mks)
- Multiplexing
- Baseband signal
-
- Give two reasons why two’s complement is preferred to one’s complement in computing. (2mks)
- Write these abbreviations in full: (2mks)
- FOTRAN…………………………………………………………………………………
- BCD……………………………………………………………………………………….
- ASCII…………………………………………………………………………………......
- EBCDIC………………………………………………………………………………….
- Computers have evolved through a number of generations. List any three characteristics of the first generation of computers. (3mks)
-
- Define an electronicspreadsheet and give two examples of the software. (2mks)
- Differentiate between formula and function as used with spreadsheets. (2mks)
- Explain the difference between digital signal and analog signal in data communication. (2mks)
- List down two types of computer viruses (2mks)
- Explain graphic based DTP software. (1mk)
- Give two possible ways of fitting a document in one page. (2mks)
-
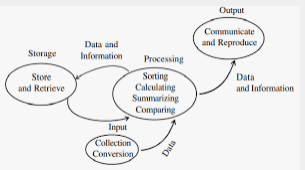
- Draw a well labelled diagram of the data processing cycle. (3mks)
- Give two disadvantages of electronicdata processingmethod. (2mks)
- Why must food and beverages be kept out of the computer lab? (2mks)
-
- What are toggle keys in relation to keyboards? (1mk)
- What type of keyboard would you prefer for the following and why? (4mks)
- Visually impaired users
- Busy restaurant
- Why are repeaters necessary when setting up a large network? (1mk)
- During class discussion, a Form One student was asked to present his findings on what Operating Systems perform in a computer. Explain two key points he will address. (2mks)
- As a computer expert, you were approached by certain organization to help them secure some computers they require. You were keen at certain considerations based on the knowledge you have in computing. What would the following considerations imply? (3mks)
- Software Authenticity
- Multi-media capability
- Software portability
- Outline four benefits of using word processors over manual typewriters. (2mks)
SECTION B:ANSWER Q16 AND ANY OTHER THREE QUESTIONS
-
- State two distinct differences between compilers and interpreters. (2mks)
-
- Outline three demerits of using low level programming languages. (3mks)
- Differentiate between monolithic and modular programs. (1mk)
- Study the following statements and answer the questions that follow.
Start
Initialize x to 3 and y to 4
Count = 1
While Count <=10
Increment x by 1
Update y by multiplying y by 2 and subtracting ½
Add x to y to attain z
Increase the value of Count by 2
Endwhile
Print the values for x, y and z
Stop- What does the above statements represents? (1mk)
- What is the value for y and z? (2mks)
- Implement the above statements using a program flowchart. (6mks)
- Otieno was tasked with entering marks for a certain exam that was done by an entire class.
- State two types of errors he is likely to encounter during this exercise. (2mks)
- How can the above identified errors be avoided? (1mk)
- Other than the errors identified above, list two other errors that can be encountered during data processing. (1mk)
- A certain research institution had his staff collect data from the field. The collected data are then surrendered to the central location where they are processed as a unit over a period of term. What processing mode is being used? (1mk) State one merit of this mode. (1mk)
- Describe data integrity. (1mk)
- There are so many ways that can be used to reduce threats to data integrity. Mention any two. (2mks)
- Give the best file organization employed by Magnetic tapes and SD Cards. (1mk)
-
- The school’s LAN is done using UTP cable. List two advantages of using this type of cable. (2mks)
- List two advantages of using fibre optic cable in networking. (2mks)
- Data flows in the school’s LAN in a duplex manner. List two other modes of data transmission in a network. (1mk)
-
- Outline three ways - 4 can be represented in a computer. (3mks)
- Use one’s compliment to represent -610 in 8-bits formation. (2mks)
- Briefly explain how data are represented on a floppy disk (2mks)
- Differentiate between wavelength and frequency of a signal. (2mks)
- Describe each of the following computer terminologies as used in data representation.(4mks)
- Word
- Bit
- Byte
- Nibble
- Convert 9.62510 to binary. (2mks)
- Study the passage below:
Outline four formatting styles that have been applied to the passage. (2mks)
-
- State one function of each of these objects in a database. (4mks)
- Table
- Query
- Forms
- Reports
- State two features of a primary key field. (2mks)
- Briefly describe the following field properties (3mks)
- Format
- Input mask
- Required
- List any two sources of graphics in a word processor (2mks)
- List two health problems associated with improper sitting posture while using a computer. (2mks)
- State two ways of mitigating intellectual property theft (piracy) (2mks)
- State one function of each of these objects in a database. (4mks)
-
- Human activity systems are said to be soft systems. Give threereasons why they are said to be so. (3mks)
- What are hard information systems? (2mks)
- Discuss any five characteristics of a system. (10mks)
MARKING SCHEME
SECTION A
-
- Multiple xing data signal over the same
- It is the process of sending multiple medium (Give mark if diagram exist)
- Baseband signal
- It is a digital signal that is generated and applied to the transmission medium directly without modulation. (2mks)
- Multiple xing data signal over the same
-
- Explain why two’s complement is preferred to one’s complement in computing.(1mk)
- No two ways of representing zero
- No need of extra circuitries when doing operations involving extra sign bit
-
- FOTRAN - FORMULA TRANSLATOR
- BCD - BINARY CODED DECIMAL
- ASCII - AMERICAN STANDARD CODE FRO INFROMATION INTERCHANGE
- EBCDIC - EXTENDED BINARY CODED DECIMAL INTERCHANGE CODE
- Explain why two’s complement is preferred to one’s complement in computing.(1mk)
- Computers have evolved through a number of generations. List any three characteristics of the first generation of computers. (3 marks)
- Very large in size
- Consumed a lot of heat
- Used vacuum tubes technology
-
- Define an electronic spreadsheet . (1mk)
- an application software that is used to manipulate numeric data mathematically
- Differentiate between formula and function as used with spreadsheets.(2mks)
- formula-user based expression
- function-inbuilt formula
- Define an electronic spreadsheet . (1mk)
- Explain the difference between digital signal and analog signal in data communication. (2mks)
- Analog signal is made up of continuous varying waveform while digital signal is made up of non continuous discrete waveform.
- List down two types of computer viruses (2mks)
- Boot sector viruses
- File virus
- Hoax virus
- Trojan virus
- Worms
- Backdoors
- Explain Graphic based DTP software. (1 mark)
- Used to design pictures, objects,drawings, or images accurately
- Give two possible ways of fitting the document in one page:
- Reduce the line spacing
- Adjust the left and right margins
- Reduce the font size (2mks)
-
- Draw a well labelled diagram of the data processing cycle. (3 marks)
- disadvantages of electronic data processing
- data security is compromised
- lack of legal frameworks supporting electronic data processing
- lack of ICT skills
- Draw a well labelled diagram of the data processing cycle. (3 marks)
- Why must food and beverages be kept out of the computer lab? (2mks)
- Food droplets may attract rodents which may computer components more so cables,may also fall on movable parts clogging them while beverage may spill on metallic part therefore causing rust
-
- What are toggle keys in relation to keyboards? (1mk)
- These are keyboard keys that can perform two different functions or any key that is used to turn a function on or off, or to switch between two functions. Examples are the caps lock key, number lock key and scroll lock key.
- What type of keyboard would you prefer for the following and why? [4 marks]
- Visually impaired users: Braille keyboards because they have touch overlays that are raised keys that can be felt by the fingers
- Busy restaurant: Concept keyboards are used when fast input is needed and are ideally suited to selecting from a limited range of choices.
- What are toggle keys in relation to keyboards? (1mk)
- Why are repeaters necessary when setting up a large network? (1mk)
- They receive weak signal from one segment, clean, boast and then retransmit to the next segment
- During class discussion, a Form One student was asked to present his findings on what Operating Systems perform in a computer. Explain two key points he will address. (2mks)
- Job scheduling – allocating processor time to various tasks following certain criteria
- Interrupt handling – dealing with breaks from the normal sequencing of operations when processing a task
- Error handling – recognizing any error that may occur and suggesting possible remedies
- Memory management – organizing how memory locations shall be utilized by data and programs
- As a computer expert, you were approached by certain organization to help them secure some computers they require. You were keen at certain considerations based on the knowledge you have in computing. What would the following considerations imply?(3mks)
- Software Authenticity: It is the genuineness, validity and legitimacy of the software i.e. obtained from authorized source
- Multi-media capability; Ability of the computer to work with text, audio and visual
- Software portability; The ease of software to be installed or copied in multiple computers
- Outline four benefits of using word processors over manual typewriters.(2mks)
- Efficiency.
- Documents can easily be sent electronically.
- It is easier to make changes to your documents.
- Spell checking/Gramma checking.
- Insert images and art in documents
- Documents can be saved for future reference electronically
SECTION B
-
- State two distinct differences between compilers and interpreters. [2 marks]
- Compilers translate the entire source code at once before execution while interpreters translate source code one statement at a time
- Compiled codes can be saved and run when required while interpreters translate the code each time the program is to run
- Compiled codes require more memory while interpreted codes require less memory
-
- Outline three demerits of using low level programming languages (3mks)
- They are machine dependent and therefore not portable
- Require well trained personnel to develop and maintain them
- Are difficult and cumbersome to learn and use
- Debugging is difficult
- Differentiate between monolithic and modular programs [2 marks]
- A monolithic program that is self-contained and independent from other computing applications while modular program is a program that is divided into a set of loosely coupled functional units (named modules) that can be integrated into a larger program
- Outline three demerits of using low level programming languages (3mks)
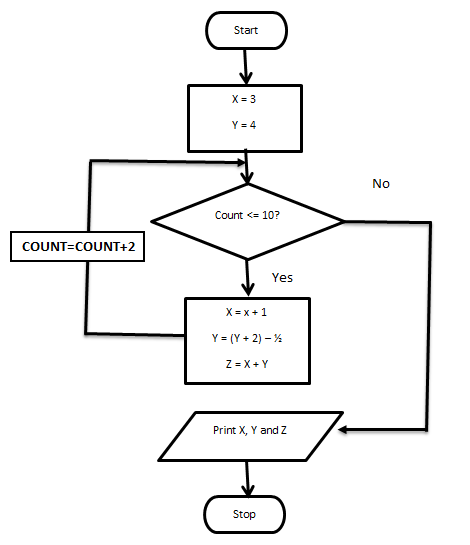
- Study the following statements and answer the questions that follow [7 marks]
Start
Initialize x to 3 and y to 4
Count = 1
While Count <=10
Increment x by 1
Multiply y by 2 and subtract ½
Add x to y to attain z
Increase the value of Count by 2
Endwhile
Print the values for x, y and z
Stop- What does the above statements represents? [1 mark]
- Pseudocode
- What is the value for y and z [1 mark]
- y = 112.5 and z = 120.5
- Implement the above statements using a program flowchart [6 marks]
- What does the above statements represents? [1 mark]
- State two distinct differences between compilers and interpreters. [2 marks]
- Otieno was tasked with entering marks for a certain exam that was done by an entire class.
- State two types of errors he is likely to encounter during this exercise
- Transposition
- Misreading
- How can the above identified errors be avoided?
- Using devices that capture directly from the source
- Designing user interfaces that minimizes chances of wrong entries
- Other than the errors identified above, list two other errors that can be encountered during data processing
- Truncation
- Rounding
- Overflow
- A certain research institution had his staff collect data from the field. The collected data are then surrendered to the central location where they are processed as a unit over a period of term. What processing mode is being used?
- Batch processing
State one merit of this mode. [1 mark] - Cheaper to produce a whole batch of a product than a single item at a time.
- Machinery can be utilized more efficiently, therefore saving money for the business.
- Reduces the risk of concentrating on one product and allows for flexibility.
- It is not labour intensive
- Batch processing
- Describe data integrity.
- It is the completeness and validity of data entered in a computer for processing
- There are so many ways that can be used to reduce threat to data integrity. Mention any two
- Using direct capture devices
- Backing data on separate location/external storage devices
- Controlling access to data by putting security measures
- Using error detection and correction software when transmitting data
- Designing user interfaces that minimize chances of entry of invalid data
- Give the best file organization employed by Magnetic tapes and SD Cards.
- SD Card – Random/Direct
- Magnetic tapes - Serial
-
- The school’s LAN is done using UTP cable. List two advantages of using this type of cable.
- Cheaper because of mass production
- Installation equipment used are usually cheap
- Easier to set up a network as they readily available
- List two advantages of using fibre optic cable in networking [2 marks]
- Fast and support high bandwidths
- Smaller and lighter
- Suffer low attenuation hence suitable for use as backbone
- Immune to electromagnetic interference and eavesdropping
- Can be used in highly flammable systems
- Data flows in the school’s LAN in a duplex manner. List two other modes of data transmission in a network
- Simplex
- Half duplex
- The school’s LAN is done using UTP cable. List two advantages of using this type of cable.
- State two types of errors he is likely to encounter during this exercise
-
- Outline three ways - 4 can be represented in a computer [3 marks]
- Prefixing an extra bit – (0)100
- Ones complement – 011
- Twos complement - 100
- Use one’s compliment to represent −610 in 8-bits formation. [2 marks]
610 = 1102
8-bit notation = 00000110
Ones complement = 11111001 - Briefly explain how data are represented on a floppy disk [2 marks]
- By rearranging the magnetic dipoles within the domains. Dipoles facing one direction would be interpreted as 1s and those in opposite directions as 0s
- Differentiate between wavelength and frequency of a signal [2 marks]
- Wavelength is the distance between two successive peaks of a signal while frequency is the number of complete oscillations/cycles made within one second by a signal
- Describe each of the following computer terminologies as used in data representation [4 marks]
- Word
- A combination of two or more bytes
- Bit
- Binary digits that is either 1 or 0
- Byte
- Combination of 8 consecutive bits that forms a character
- Nibble
- It is a half a byte or 4 consecutive bits
- Word
- Convert 9.62510 to binary [2 marks]
Integral part Fractional part
2 9 0.625 x 2 = 1.25
2 4 rem 1 0.250 x 2 = 0.50
2 2 rem 0 0.500 x 2 = 1.00
2 1 rem 0
2 0 rem 1
= 1001 = 0.101
The answer is 1001.1012 - Study the passage below
Outline four formatting styles that have been applied to the passage- Indentation
- Bold facing
- Double strikethrough
- Underline
- Outline three ways - 4 can be represented in a computer [3 marks]
-
- State one function of each of these objects in a database. (4mks)
- Table…Stores related data item
- Query…used to extract data from a table
- Forms…used to add,update records
- Reports…used to output summarised information from a table or query
- State two features of a primary key field. (2mks)
- Unique identifier
- Prevents users from making duplication
- Briefly describe the following field properties (3mks)
- Format…affects how data values are when printed
- Input mask……determines how data are displayed during data entry and editing
- Required…data has to be entered in the field, not to be left empty
- List any two sources of graphics in a word processor (2mks)
- pictures,shapes,smartart,screenshot…………
- List two health problems associated with improper sitting posture while using a computer. (2mks)
- headache
- Fatigue
- Back pain
- State two ways of mitigating intellectual property theft (piracy) (2mks)
- making sw cheap and affordable
- putting stiff penalties for those found in possession of pirated sw
- sensitizing public
- use of passwords
- State one function of each of these objects in a database. (4mks)
-
- Human activity systems are said to be soft systems. Give three reasons why they are said to be so (3mks)
- Their boundaries are fluid or keep on changing.
- Their goals and objectives usually conflict and can hardly be captured clearly at any one time
- It’s difficult to define exact measures of performance for them
- What are hard information systems (2mks)
- One in whose goals and objective are clearly defined and the outcomes from the systems processes are predictable and can be modeled.
- Discuss any five characteristics of a system (10mks)
- Holistic thinking: Components may be simple but the combination gives a complex whole whose overall goals are more sophisticated.
- Subsystems: systems are made up of different components
- Boundary and environment: each system has space within which the components operate.
- Purpose: each system performs a specific task.
- Process: Process data from one state to another
- System entropy: systems decay naturally over time
- Inputs and outputs: systems communicate with their environments y receiving inputs and giving outputs.
- Open and closed systems: open systems adapt to changes in the environment.
- Control: control is achieved through feedback and adjusts control signals ensuring that outputs meet set expectations.
- Human activity systems are said to be soft systems. Give three reasons why they are said to be so (3mks)
Download Computer Studies Paper 1 Questions and Answers - Momaliche Pre Mock Exams 2023.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students