QUESTIONS
SECTION A 40MKS
Answer All the Questions in this section in the spaces provided
-
- Distinguish between optical and magnetic scanners (2marks)
- Differentiate between hardware and software portability (2marks)
-
- Name two special purpose memories found either inside or outside the microprocessor (2marks)
- Distinguish between an accumulator and an address register (2marks)
- Differentiate between formatting and editing as used in word processor (2marks)
-
- Distinguish between pasteboard and printable page in DTP (2marks)
- Differentiate between a margin guide and column guide as used in DTP (2marks)
-
- Define the term normalization as used in a database design (1mark)
- Explain two objective of normalization (2marks)
- Describe two methods used to secure data in a database (2marks)
- Explain the meaning of the following terms as used with DTP (4marks)
- Crop
- Embedded object
- Master page
- Tool box
- Make a clear difference between a website and web portal (2marks)
-
- What is a protocol (1mark)
- Write the following in full (2marks)
- TCP/IP
- HTML
- HTTP
- FTP
- Explain the following as used in data security (3marks)
- Fraud
- Eavesdropping
- Information security
- Explain the importance of control structure in program development (1mark)
- State four stages in data processing (2marks)
- Describe three electrical safety precaution rules that should be observed in a computer room (3marks)
-
- What is a speech input (1mark)
- State two disadvantages of using this method of data input (1mark)
- Name two solid state storage devices (1mark)
SECTION B (60MARKS)
Answer question 16 (compulsory) and any other THREE question from this section
-
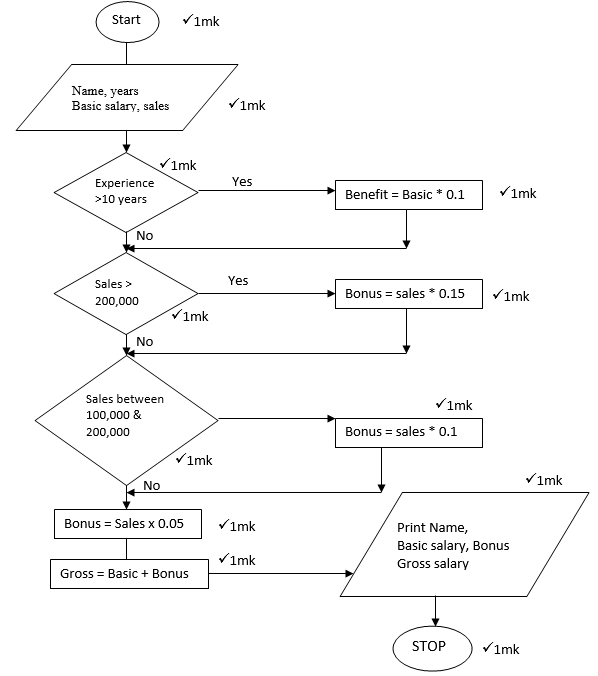
- Explain three errors detecting methods in program development (3marks)
- The gross salary of employees of Mutson chemists is based on the basic and additional benefits. Employees with more than 10 year’s experience get an additional pay of 10% of their basic salary. Bonuses are given as per employees’ sales of the month as:
>200,000 15%
100,000 – 200,000 10%
Below 100,000 5%
Draw a flowchart for the program that will calculate gross salary and output each employee’s basic salary, gross salary and all benefits. (12marks)
-
- Write the following acronyms in full
- EBCOIC (1mark)
- COBOL (1mark)
- ASCII (1mark)
- Explain why computes use binary numbers in data representation (2marks)
- Convert the following values to the stated number system
- 20.216 to decimal (2marks)
- 7.12510 to binary (2marks)
- Perform the following binary arithmetic
- 111001112 + 001011102 (1mark)
- 101012-1102 (1mark)
- Use Two’s compliment to subtract 1012 from 10002 (2marks)
- Convert 57.410 to its octal equivalent (2marks)
- Write the following acronyms in full
-
- Describe each of the following data processing methods and give an example of where used.
- Online processing
- Batch processing
- Real time
- Make a clear difference between (6marks)
- Logical file and physical file
- Master file and back up file
- Random and indexed sequential file organization methods
- An organization is facing threats to data integrity. Explain three ways on of how the threats can be minimized (3marks)
- Describe each of the following data processing methods and give an example of where used.
-
- One of the functions of an operating system is job scheduling. Explain what is meant by job scheduling (2marks)
- Recently on 4th March 2013 Kenya went on election in which the results were to be transmitted electronically using mobile phones from all polling stations to the main server. But the system (server) failed to work.
- Give two security threats that the system was prone to (2marks)
- State control measures that the IEBC should take in future to ensure and safe tallying of votes (2marks)
- The principal of Chebloch primary school wants to acquire a new operating system for his computer. Advise him stating the advantages of graphical user interface over command line interface. (2marks)
- Explain the meaning of the following terms used in data processing (6marks)
- Truncated
- Transposition
- Transcription
- Explain why the processor of a micro computer is referred to as micro processor. (1mark)
-
- List and explain the functions of each computer bus (6marks)
- The formul = &B2 + C&4 is entered in cell C5 and then copied to D10. Write down the formula as it appears in the destination cell (2marks)
- Give two reasons why smaller computers like laptops tend to be more expensive than desktop computer (2marks)
- Define the term program documentation (1mark)
- Briefly explain the terms parallel running and direct changeover as used in system implementation (2marks)
- Differentiate between a primary key and a foreign key as used in designing a database (2marks)
MARKING SCHEME
-
- Optical scanner capture using light technology while magnetic capture data written using magnetic ink or coded into magnetic strip ( award 2 marks)
- Hardware portability refers to the ability of the computer to be carried from one place to another with ease. Software portability refers to the ability to install a program in two or more computers (award 2 marks)
-
- Cache
Buffer
Registers (award 2 marks) - Accumulator holds the results of the last processing step of the Alu temporarily while address temporarily holds next piece of date waiting to be processed (award 2 marks)
- Cache
- Formatting refers to applying various styles to enhance the documents appearance
Editing refers to making necessary changes to a document (award 2 marks) -
- Pasteboard is a large area where you place text and graphical objects before arranging them on a printable area. Printable area is the area surrounded by the margins.
- Margin guide determines printable area while column guide divide a page into columns
-
- Normalization is the process of trying to eliminate duplication values in a database.
-
- To relate different tables in database
- To ease the retrieval of data from a relation database
- Breaking up multi theme tables to smaller workable tables.
-
- Password protection
- Data encryption
- User - level security
- User and group permissions
-
- Crop- trim graphics
- Embedded objects – separate file not created in the program in use but in another and placed in the program in use.
- Master page - A page used to design general layout that needs to be applied in other pages.
- Tool box – a set of buttons that contain tools used to create and manipulate publication
- Website – A group of related web pages
Web portals - It offers specialized service such as searching, email, sports. -
- Protocol is a communication rules that govern sending and receiving of messages by computer network.
- TCPL/IP – Transmission Control Protocol/Internet Protocol
HTML – Hypertext Markup Language
HTTP – Hypertext Transmission Protocol
FTP – File Transfer Protocal
- Fraud – Stealing by false pretence
Eaves dropping – Tapping into Communication Channel
Information Security – Ensuring of safety of data and information against threats - Control structure determine how statements are to be executed
- Data collection
Data input
Processing
Output - Cables and sockets well insulated
Provide stable power supply
Cables laid out away from pathways -
- Is a type of input where data is entered in form of spoken words
-
- Homophones
- Limited to few vocabularies
- Response is slow
- Problem of accents and tones
-
- Flash disk
- Memory stick
-
- Dry running
Use of translators
Debugging utilities (award 3 marks well explained)
- Dry running
-
-
- EBCDIC
- Extended Binary Coded Decimal Interchange Code
- COBOL
- Common Business Oriented Language
- ASCII
- American Standard Coded for Information Interchange
- EBCDIC
- Why computers use binary numbers
- Electrical pulses are either high or low
- Storage system is either magnetic or not
- Computer understands only ones 1s and 0’s
- The logic that computer uses is based on the states ON and OFF
(Answer 1 mark each total 2 x 1= 2 marks)
-
- 20.216 to decimal
= [ax 161] + [0 x 160] + [2 x (1/16) ]161
160
•
16-1
2
0
•
2
= 32. [0.125] (1mk)
= 32.12510 -
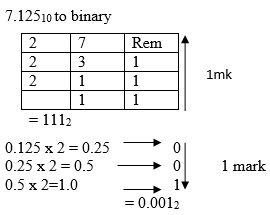
Combine the two
. := 111.0012
- 20.216 to decimal
-
- 111001112 + 001011102
11100111
00101110
(1)00010101 = 1000101012 (1 mark) - 101012 -110
10101
110
11112 (1mark)
- 111001112 + 001011102
- Use Two’s complement to subtract 101 from 1000:
Step 1: Change the values to 8 binary digits
000010002-000001012 (1 mark)
Step 2: Add the binary equivalent of the first value to the Two’s complement of the second value
That is: 00001000
11111011 +
(1)00000011
= 1000000112 (1mk) - Convert 57.410 to its octal equivalent
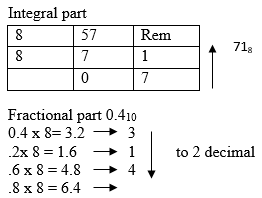
.3146
Therefore combine intergal and fractional part
71.318
-
-
-
- Online processing – data is processed immediately as internet banking, online payment system using credit card (2mks)
- Batch processing – data is accumulated as a group as grading system in a school (2mks)
- Real time – computer processes the incoming data as soon as it occurs, update the transaction file and give an immediate response as making reservation for airlines seats. (2mks)
-
- Logical file and physical file
- Viewed in terms of what item it contains & details of what processing operations may be performed on the data items.
- Physical files are one that is viewed in terms of how data is stored on a storage media (2mks)
-
- Master file and back - up file
- Master file is the main file that contains relatively permanent records. Back up files used to hold copies of data or information from fixed storage (hard disk) (2mks)
-
- Random and indexed sequential file organization methods
- Random – Also direct file organization records are stored randomly but accessed directly on a storage medium. Indexed sequential records are stored and accessed individual records on storage media. (well explained) (2mks)
- Logical file and physical file
-
- Back up data
- Control access of data by enforcing security measures
- Design user interface that minimize unauthorized access.
- Use error detection and correction softwares
- Use device that directly capture data from source document i.e. digital camera, optical CR
(Any three each 1mk).
-
-
-
- The scheduler decides which of the jobs is to be allocated to the CPU for processing
- Allocating CPU time to jobs
- Sequencing of jobs in a queues (well explained) (2mks)
-
-
- Tapping
- Hacking
- Sabotage
- Alteration of data
- Damage of software (and any other each 1mk)
-
- Careful recruitment of staff
- Set up a clear and firm management policy on crimes and fraud
- Access restriction to computer rooms or terminal
- Use transaction files and file logs to monitor access of the system
- Use backups (any 2 each 1mk)
-
-
- Its user friendly
- Faster to work with as its work relies on the user clicking icons by the use of pointing device
- Easy to use ( each 1mk)
- Trun cated – Results from having real number that have along fractional part being cut e.g. 73.73487 can be 73.734
Transposition – Result from incorrect reading of source document e.g. 69371 can be 63971
Transcription – Occurs during data entry e.g. misreading and transportation. (each 2 mks) - Its small/ tiny clip put into a silicon clip (1mk)
-
-
- List and explain two functions of computer bus
- Data bus – Carries data to and from the CPU i.e. pathway of actual data
- Address bus – Used to locate the storage position in memory where the next instruction or data to be processed is held
- Control bus – it is the pathway for all timing and controlling functions sent by the control unit to other parts of the system
- =&B7 + D&4
- The technology of producing smaller devices is expensive
Convenient because they are portable
Have advanced power management capabilities (consume less power) - Document used to explain and describe how a particular program function in a system
-
- Parallel running is where both the old and the new systems are run in parallel to each other at the same time
- Direct changeover is a complete replacement of the old system with the new system in one bold move. (Old system is stopped and abandoned and the new system starts operating immediately).
- Primary key – Unique field that identifies a record in a database
Foreign key – a primary key in another table once the tables are linked.
- List and explain two functions of computer bus
Download Computer Studies Paper 1 Questions and Answers - Form 3 End Term 3 2022 Exams.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

