QUESTIONS
SECTION A (40 marks)
Answer all questions in this section.
- State two reasons for the increased use of laptop computers in government offices.(2 marks)
- Computer network technicians prefer to use command-line based operating system when configuring networks. State three reasons for the preference.(3 marks)
- State three measures that should be put in place in a computer laboratory to safeguard users' health.(3 marks)
- State three ways in which barcode readers may be used in schools.(3 marks)
- State three advantage of flat panel monitors over cathode ray tube monitors as used in computers.(3 marks)
- State three possible reasons for the extinction of daisy wheel printers in the market. (3 marks)
- State three ways in which an operating system secures a computer system.(3 mark)
- A law firm prefers to use hard copy output over soft copy output when handling documents for legal matters. State two reasons for this preference. (2 marks)
- State the function of each of the following features in a word processor application:
- Thesaurus;(1 mark)
- Comments.(1 mark)
- With the aid of an example, explain the term multi-level list as used in word processing.(3 marks)
- Distinguish between real-time operating system and distributed operating system.(3 marks)
- Explain the function of project sheet feature in a spreadsheet program.(2 marks)
- State four computer-based careers introduced as a result of computerised data processing method at the airport.(2 marks)
- In a spreadsheet, the formula If(Al>10, A1*77, A150) is entered in a cell. Interpret the results.(3 marks)
- State a stage in systems development life cycle where each of the following activities are carried out:
- identifying the technologies that may be used in a proposed system;(1 mark)
- identifying shortcomings of a system; (1 mark)
- preparing the system migration plan.(1 mark)
SECTION B (60 marks)
Answer question 16 and any other three questions from this section in the spaces provided.
-
- With the aid of a flow chart, describe a loop control structure as used in programming.(4 marks)
- Study the following pseudocode and answer the questions that follow.
- Start
- Get value1 and value2
- If value1 > value2 Then
- Maximum = value1
- Else If value1 < value2 Then
- Maximum = value2
- Else Go to 9
- Display Maximum
- Stop
- State the purpose of the pseudocode.(1 mark)
- Draw a flowchart equivalent to the pseudocode.
- Distinguish between a source program and a compiler as used in computer programming.(4 marks)
-
-
- Explain the term search engine as used in the Internet.(2 marks)
- Peter intends to download a movie from the Internet. State the three factors that may determine the total time taken to complete the download. (3 marks)
- Wakulima online is an organisation that runs a web based system for assisting farmers to obtain market for their farm produce. State four technological reasons that may cause a farmer not to access the organisation's system.(4 marks)
- Explain a situation when each of the following Desktop Publishing program features may be used when creating a publication:
- cropping:(2 marks)
- transparency.(2 marks)
- List two areas where infrared waves are used in data communication.(2 marks)
-
-
- State four activities of the planning stage of systems development.(4 marks)
- Explain a circumstance when each of the following feasibility studies are carried out during systems development:
- Technical;(2 marks)
- Economic;(2 marks)
- Schedule.(2 marks)
- Table 1 and Table 2 are related tables in a database. Use them to answer the questions that follow
Table 1
Table 2Dept Code Dept Name 001 Computer 002 Aviation 003 Engineer
DeptID Student Registration Number Student's Name 002 St01 Alex Toro 003 St02 Naomi Komi 002 St03 Peter Kengo - Identify the appropriate primary key for each table.(1 mark)
- Explain two benefits of enforcing referential integrity in the database.(4 marks)
-
- Describe each of the following validation checks as used in data processing:
- Preserve check;(2 marks)
- Data type check;(2 marks)
- Check digit.(2 marks)
- Write each of the following abbreviations in full:
- BCD;(1 mark)
- EBCD;(1 mark)
- ASCII.(1 mark)
- Using 10-bits binary number system, perform the following decimal operation using two's complement (6 marks)
12910- 12810
- Describe each of the following validation checks as used in data processing:
-
- The figure shows a network design. Use it to answer the questions that follow.
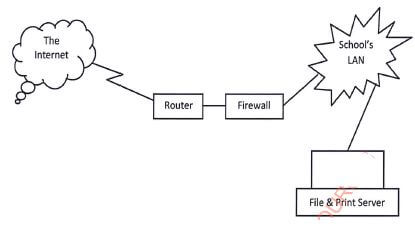
- Explain the function of each of the following in the network.
- Router;(2 marks)
- Firewall;(2 marks)
- File server.(2 marks)
- State two categories of software that must be installed in a computer so that users can use it to access the internet.(2 marks)
- Explain the function of each of the following in the network.
- State four ways in which computers may be used to manage data in a research environment.(4 marks)
- Some computer companies have opted to use the Internet to provide shared processing resources and online application services to users. State three advantages that this approach will have on their customers.(3 marks)
- The figure shows a network design. Use it to answer the questions that follow.
MARKING SCHEME
- Reasons for the preference for laptops.
- They are small and fit in a small storage space.
- They are light weight hence can be carried to areas where their services are required.
- The monitor, system unit, keyboard units are attached together hence making its use to be convenient.
- Rechargeable /backup battery.
- Reasons for the use of command-line interface OS
- They do not take up a lot of memory hence boot faster than the GUI OS.
- They have direct access or most hardware devices.
- They are cheaper to acquire as some can be downloaded free of charge.
- They can run on lower-bit hardware systems such as 32-bit computers.
- Measures to be put in place in the laboratory to safeguard user health.
- All power cables must be insulated and hidden from users.
- The furniture used must be of standard computer fumiture.
- The room should be lit with adequate lighting.
- The room must be ventilated.
- Computer monitor should be fitted with antiglare to filter excess light rays emanating from the monitor.
- Avoid slippery floors/cemented floors.
- Controlling dust.
- Ways in which barcode readers can be used in a school.
- To take inventory of items in the school.
- To keep track of employee login log out.
- Used to transact business in the library.
- Used to keep track of movement of goods.
- Advantages of flat panel monitors.
- They are compact and light weight;
- They consume less power;
- They do not suffer from geometrical distortions;
- They do not cause eye fatigue.
- They support many advanced technologies;
- They can be made in almost any size and shape;
- They support higher resolution. Low heat radiation.
- Reasons why daisy wheel printer are in extinct.
- They supported one font size and font face;
- They were monochrome printers;
- They produced noise while printing;
- They were very slow;
- Did not print graphics.
- Had poor print quality.
- Ways in which an OS secures computer system:
- Access controls: Authentication of users in order to access files;
- Performing regular patches of updates;
- Creating secure accounts with required privileges;
- Scrutinizing all incoming and outgoing packets of data through a firewall;
- Encryption of data, during the transmission stage;
- Password / biometric analysis; Log files to detect any breach.
- Advantages of hardcopy output.
- They are acceptable as exhibit in cases of litigation.
- Can be used without a computer.
- They are difficult to change without leaving any trace.
- They can be used without power.
- They can be used without the experience of computer usage.
-
- Thesaurus:
- It is a feature in a word processor that suggest words with similar or opposite meaning to the selected word @ 1.
- Comments:
- It is a feature in WP that allows a user to attach a remark about the selection @1.
- Thesaurus:
- Multilevel list:
- It is a format style that shows the listed items of different levels rather than one at one level. Each level has different indentation and numbering style @2.
Example (Accept any)- Chapter One
1.1 Introduction
1.1.1 Definition of terms @1.
- Chapter One
- It is a format style that shows the listed items of different levels rather than one at one level. Each level has different indentation and numbering style @2.
- Distinction between real-time and distributed OS.
- Real-time OS reads information from input devices and must respond within a short duration of time to ensure correct performance.
- Distributed OS distributes computation among several physical processors which do not share memory or clock.
- Function of protect sheet:
- It is a feature used to prevent unwanted changes to be made on the data contained in a sheet by limit the ability to make changes.
- Computer based careers created by introducing computerized data processing.
- System analysts
- Hardware technicians
- Data entry clerks
- Programmers
- Networks technicians
- Database administrators
- Web designers
- Network administrator
- =If (A1 > 10, A1 * 77, A1 * 50)
- Compares the value in cell Al If it is greater than 10, if comparison is True, the results of operations Al* 77 is displayed, if it is False the results of the operations Al 50 is displayed.
-
- Identifying technologies that could be used in the system.
- System analysis/ information gathering problem recognition(@ 1)
- Identifying the shortcoming of the old system
- Problem definition (@1)
- Prepares the software migration plan
- Implementation stage (@1)
- Identifying technologies that could be used in the system.
-
- Looping is the control structure that allows a block of code/statements to be repeated until a certain condition is fulfilled. @ 2 marks
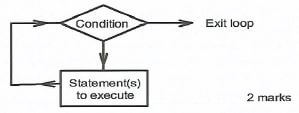
Accept any type of looping control structure -
- The pseudocode compares two values and output one of the two which is greater.
-
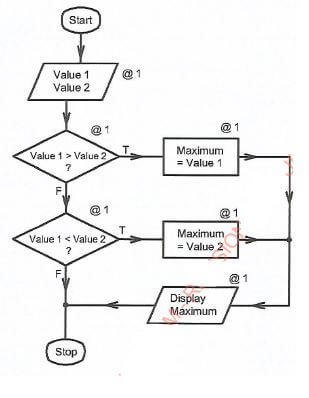
chart logic @ 1
- Distinction between a source program and compiler
- Source program is the original computer based instructions written by a programmer in a programming language
while
A compiler is a program that processes statements/instructions and translates them into machine language.
- Source program is the original computer based instructions written by a programmer in a programming language
- Looping is the control structure that allows a block of code/statements to be repeated until a certain condition is fulfilled. @ 2 marks
-
-
- Search-engine
- It is a web-based application used to locate for an item or information from world wide web.
- Factors that affects duration of download
- The size of the video
- The band width of the media used
- Availability of network
- Other activities that may be running in the computer.
- Other restrictions enforced in the computer
- The restrictions by the ISP
- Speed of computer
- Search-engine
- Causes of Wakulima system's failure
- Lack of power supply to the system servers.
- Network infrastructure breakdown/poor network coverage/lack of connection.
- Program failure in the system/malware (virus).
- Hardware failure in the system.
- Human action which could be accidental or intentional.
- Lack of access rights.
- System overload
-
- Cropping
- Used when handling a graphic and there is a need to remove some of the portions in the graphic.
- Transparency
- Used when there is a need to make the background of a graphic to be visible.
- Cropping
- Areas where infra-red radio waves are used.
- TV remote control communication;
- DVD remote control communication
- Communication between peripheral devices and the computer
- Data link over short distance using mobile phones
- Radio remote control
- Remote locking / opening doors/devices
-
-
- Activities at the planning stages
- Identify opportunity for the new project.
- Analyse feasibility to establish the viability of the project.
- Develop a work plan.
- Identify appropriate staff to work in the project.
- Control and direct the project.
-
- Technical Feasibility
- Meant to determine whether the proposed solution is technically practical/establish whether the technology is available /expertise is available.
- Economie Feasibility
- Meant to establish whether the proposed system will be cost effective. (@2)
- Schedule Feasibility
- Meant to establish whether the system can be implemented within an acceptable time frame. (@2)
- Technical Feasibility
-
- Primary keys in the table
- Table 1 : Dept code
- Table 2 : Student's Registration No.
- Benefits of referential integrity in the table
- No record can be added to the table 2 if its corresponding record in Table 1 does not exist.
- No record in Table 1 can be deleted without first deleting associated records in Table 2.
- Reduces data redundancies.
- Prevent deletion of related tables.
- Primary keys in the table
- Activities at the planning stages
-
-
- Preserve check
- It is a measure placed used to ensure that data item is in its original status.
- Data type check
- It is a measure that ensures that correct data type is entered for each field.
- Check digit
- This is a number calculated by the computer to make sure that the other numbers in a sequence have been entered properly.
- Preserve check
-
- BCD
- Binary Coded Decimal
- EBCDIC
- Extended Binary Coded Decimal Interchange Code.
- ASCII
- American Standard Code for Information Interchange
- BCD
- 12910 - 12810
+129 = 00 1000 0001
128 = 00 1000 0000
-128 = 11 0111 1111
+1
11 1000 0000 (Twos complement)
+129 + (-128)
= 00 1000 0001
+ 11 1000 0000
1 00 0000 0001
= 00 0000 0001 (Overflow bit ignored)
-
-
-
-
- Router
- It is the device meant to forward data packets between computer network in the school and the internet.
- Firewall
- It is a device that prevents unauthorized access to or from a private network (school's LAN)
- File server
- It is a computer attached to a network whose purpose is to provide location for shared disk access (shared storage of computer files).
- Software to be installed in a computer
- Network operating system
- Browser/Mozilla firefox
- Necessary system drivers to supports installed hardware
- Protocols(SMTP,HTTP)
- Router
-
- Use of computers in research for data management
- Used for data manipulation;
- Computers aid in data capturing:
- Computers can be used to store researched and analysed data;
- Information in computers can be a secondary source of data;
- Computers can be used to generate reports,
- Computers can be used to communicate researched work.
- Advantages of online application services and shared processing resources.
- Users will not be required to have powerful processing devices;
- Users can access the services from anywhere in the world;
- Users can access services at any time (24/7);
- Users can offload their data to the cloud infrastructure;
- Users can collaborate with remote users to process the data;
- The approach will cut out high cost of hardware;
- Sharing of resources,
- Faster access to service;
- Cost effective;
- Orders are made without going to the shop.
-
Download KCSE 2018 Computer Studies Paper 1 with Marking Scheme.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

