QUESTIONS
SECTION A (40 marks)
Answer all the questions in this section in the spaces provided.
- State one function for each of the following elements of a computer system:
- hardware;(1 mark)
- software:(1 mark)
- liveware.(1 mark)
- Explain two health issues that could arise from the use of an unsuitable computer desk.(4 marks)
- List the two categories of system software.(1 mark)
- Explain two contents of a warranty that should be considered when purchasing computer hardware.(4 marks)
- Students of a school intend to elect their school captain by secret ballot. State three ways in which computers can be used to improve the election process.(3 marks)
- Figure 1 and figure 2 show icons representing commands used to manipulate graphics in a desktop publishing package.

Explain the use of each of the icons labelled figure 1 and figure 2.(2 marks) - Give two differences between a Graphical User Interface (GUI) and a Commandline Interface.(4 marks)
- Identify each of the following symbols as used in a system flowchart.
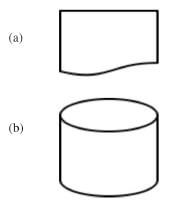 (1 mark each)
(1 mark each) - A student typed a letter in a wordprocessor and the last line of the letter flowed to the second page. State three ways in which the student could have adjusted the letter to fit on one page without changing the paper size.(3 marks)
- A computer user is unable to retrieve a file stored in a server in an organisation. State three reasons why the user would need to contact the network administrator.(3 marks)
- State three ways in which mobile phones have affected money transactions in the country.(3 marks)
- State two items that an electronic mail should have for it to be sent.(2 marks)
- List four devices that use scanning technology that would be used to capture data directly from the source.(2 marks)
- State two ways in which hardware failure is a threat to data security.(2 marks)
- Given the binary number 101011101111011, determine the number of:
- nibbles;(1 mark)
- bytes.(1 mark)
SECTION B (60 marks)
Answer question 16 and any other three questions from this section in the spaces provided.
-
- State two advantages of using low level programming languages.(2 marks)
- Other than flowcharts, state three tools that can be used to present an algorithm.(3 marks)
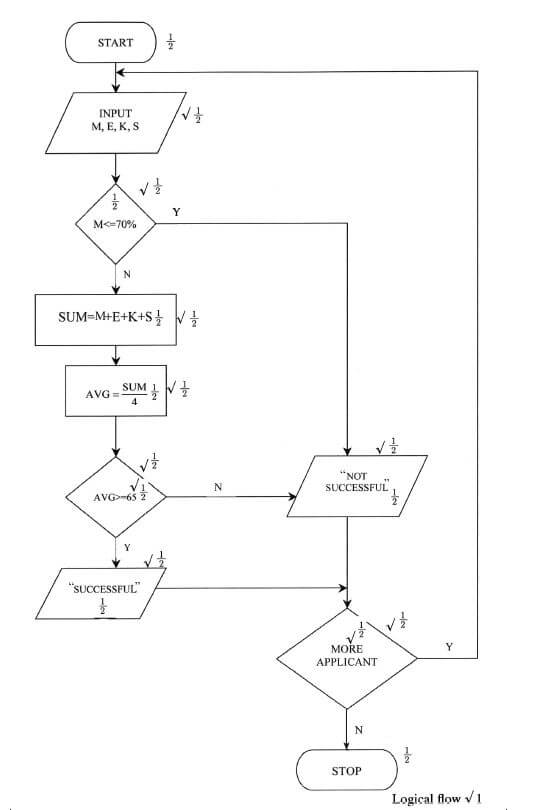
- A form one admission interview consists of four tests; Mathematics, English, Kiswahili and Science. In order to qualify for admission, an applicant must attain a minimum average of 65% in the four tests and not less than 70% in Mathematics. All applicants must sit for the interview. Draw a flowchart that would read the scores for each applicant and determine whether an applicant is successful or not. (10 marks)
-
- With the aid of a diagram, describe time sharing mode as used in computer data processing.(5 marks)
- A company's management has opted to use computers to process data. State four factors that the management needs to consider when selecting the company data processing mode.
- Explain the purpose of each of the following in system documentation:
- user manual;(2 marks)
- sample data;(2 marks)
- table descriptions.(2 marks)
-
- State the role of each of the following data communication devices:
- repeater:(1 mark)
- router.(1 mark)
- Figure 3 shows a network based on the bus topology.
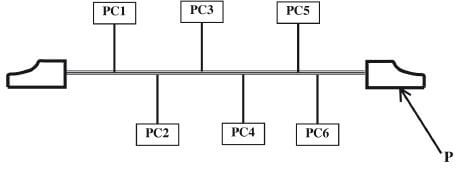
Figure 3- Identify the component labelled P.(1 mark)
- State the function of the component labelled P.(2 marks)
- Students of Neema Secondary School formed an environmental club with a goal of taking part in environmental conservation activities. Outline three ways in which they can use the internet to achieve this goal.(3 marks)
-
- A company has three branches A, B and C where A is the headquarter. The local area network (LAN) at A is directly connected to the LAN at B and directly to the LAN at C. Explain two benefits of having the LAN at B also directly connected to the LAN at C.(4 marks)
- State three ways in which a company can protect its computer network from hackers.(3 marks)
- State the role of each of the following data communication devices:
-
- The following is an extract from a document created using a wordprocessor.

Identify six formats that have been applied on the extract.(3 marks) - State three tools in a wordprocessor that would help a user to minimize spelling mistakes when creating a document.(3 marks)
- The following is an extract of a spreadsheet created to manage sales. Use it to answer the questions that follow.
A B C D 1 ITEM NAME UNIT PRICE UNITS SOLD 2 Bed 12,300 2 3 Wardrobe 16,000 4 4 Blanket 5,000 4 5 Mattress 7,000 5 6 Table 10,000 3 - Write a formula that will compute the number of items whose unit price is more than 10.000.(3 marks)
- If the formula = $B2 * C$2 was placed in cell D2, state the output if it was copied to D3.(2 marks)
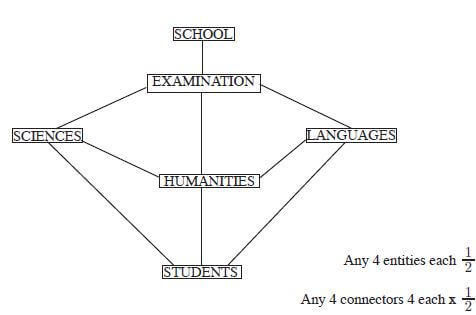
- A school administers examinations to all students in sciences, humanities and languages. Use the entities; EXAMINATIONS, STUDENTS, SCIENCES, HUMANITIES and LANGUAGES to illustrate a network database model.(4 marks)
- The following is an extract from a document created using a wordprocessor.
-
- Describe the octal number system.(2 marks)
- Convert each of the following to the number system indicated:
- 111.1012, to decimal;(3 marks)
- 14.687510, to binary.(4 marks)
- Convert the number - 1710 into 8-bit:
- signed magnitude representation;(2 marks)
- two's complement.(2 marks)
- Perform the arithmetic operation. 110.112, + 11.0112,(2 marks)
Marking Scheme
- Function of:-
- Hardware: To perform tasks of inputting, storage, outputting, processing during data processing and communication.
- Software: - Instructs the hardware/computer on what to do during data processing.
Provides interface between hardware and liveware. - Accept functions of software based category ie. system / application/working/uses. - Liveware: Meant to design or operate a computer.
- Problems arising from use of unsuitable computer desk.
- It could lead to back problems if the desk is of an unrealistic height.
- If it does not provide good positioning of the monitor, it could result in eye strain.
- Wrist problems will arise if the keyboard and mouse seating positions are bad.
- Injury as a result of falling computer components due to weak computer desks/ small size.(First 2 x 2)
- Categories of system software
- Firmware;
- Networking software;
- Operating system;
- Utilities.(First 2 x 21 )
- Two factors to consider when evaluating warranty
- Period/ duration/scope of cover: The warranty should specify the duration of time covered.
- Service agreement/level: The warranty should indicate the type of service to be provided.
- Cost implication/liability agreement: Cost sharing between the dealer and the buyer in the event of any loss or malfunction.
- Call out response.(First 2 x 2)
- Three ways of using computers in electing school captain
- Registering voters/(faster);
- Voter identification (accurate);
- Actual voting;
- Tallying process (speedy).(Any 3 x 1)
- Figure 1: Bring to front or bring to back
Used when the target graphic is hidden by other objects. When clicked, the target graphic is brought to the front.
Figure 2: Text wrap
It is used when a graphic is placed within the text area and the user needs to define how the text flows around the graphic. - Distinction of GUI and command line operating systems
(Any 2 x 2 )GUI Command line Makes use of emerging software/and hardware technologies
Their interfaces have:
- ribbons
- control buttons
- scroll bars
- menus
- can process complex graphics
The user interacts by:
- clicking
- scrolling
- mouse over
More user friendly.Hardly makes use of emerging hardware/software technologies.
Their interfaces have:
- typed commands
- prompt
- editor window
- cannot process complex graphics
Users interact by typing in commands
Less user friendly. - A system flowchart symbols
- Report or documentation

- Disk/ master file/ database
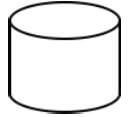
- Report or documentation
- Ways of adjusting a document to fit a page
- change page orientation.
- change the font;
- decrease font size;
- reduce margin size;
- reduce character spacing;
- reduce line height.
- change font style eg. bold/italic(Any 3 x 1)
- Role of network administrator
- to confirm that the network services are running;
- to confirm that the user is granted appropriate priviledge to access the network services/password/authentication;
- to confirm that the network infrastructure is in good condition;
- to confirm that the files sought are in existence.(First 3 x 1)
- Impact of mobile phones
- Users no longer queue in the bank in order to deposit or withdraw money;
- Easy acquisition of financial statements;
- Easy payment of bills;
- Online banking is possible;
- Money transfer is fast.
- Safer transfer of money.
- Provides wide coverage.
- Can offer services anywhere any time.
- Cheaper money transfer services.
- Increase in fraud.(First 3 x 1)
- Items that an email must have:
- the email address of the recipient;
- the content or message being communicated.
- Direct input methods
- OBR
- MICR
- OCR;
- OMR;
- Image scanner;
- Magnetic strip technology;
- Image recognition/ face recognition/finger print. (First 4 × 1/2 )
- Insecurity arising from hardware failure
- Data loss due to total system failure e.g. HD crash;
- The experts called upon to repair can access critical/ valuable information;
- Data recovery software may be used to make unauthorised backups. (First 2 x 1)
-
- Nibbles - 4
- Bytes - 2
-
- Advantages of using low-level language
- program execution is immediate;
- they require no compilation, no interpretation/translation hence they are faster;
- hardware optimization is extensive;
- program developed takes less memory space;
- suitable for micro devices;
- easy to design electronic device.(First 2 x 1)
- Three tools that can be used to develop an algorithm
- Decision table
- pseudocode;
- natural language;
- top down charts;
- flowcharts.
- DFD/context diagram
- ERD
- decision tree(First 3 x 1)
-
- Advantages of using low-level language
-
- Time-sharing mode
- This is a processing mode in which a central processor serves two or more users with different requirements. The processor time is divided equally among the tasks in the queue. A user whose task requirements are more than is apportioned is send back to the queue. For example, four jobs requiring times t1, t2, t3 and t4 to complete is apportioned equal time in each round until when they are done.

- This is a processing mode in which a central processor serves two or more users with different requirements. The processor time is divided equally among the tasks in the queue. A user whose task requirements are more than is apportioned is send back to the queue. For example, four jobs requiring times t1, t2, t3 and t4 to complete is apportioned equal time in each round until when they are done.
- Factors to consider when selecting data processing mode
- The optimisation of processing time;
- The time factor required for decision arising from the processed data;
- The ease of development, use and maintenance;
- The control over the resources e.g. files, I/O devices e.t.c;
- The need for the shared resources among several users who may afford purchasing their own facilities as in time sharing configuration;
- The volume of work involved;
- The cost of acquiring the relevant hardware, software, media e.t.c and the cost of maintenance;
- The nature of the task to be processed.(First 4 x 1)
-
- Purpose of user manual
- It is a documentation whose purpose is to help a user to use the system with little guidance.
- Purpose of sample data
- Before the system is implemented, it has to be confirmed that it is functional. Sample data is meant to be used to test whether the system is giving desired output.
- Purpose of table descriptions
- They are details of table structures that the system will require for the purpose of designing the actual tables.
- Purpose of user manual
- Time-sharing mode
-
-
- Repeater
- A device used to re-construct data signal during data transmission to its original strength/amplify/boost/regenerate.
- Router
- It is a device used to facilitate movement of data or packets between two or more LANS of different configuration (expansion of networks).
- Delivers a packet/data directly to destination computers.
- Interconnects different networks/provides network services.
- Repeater
-
- The component P is the terminator.
- Terminator in a backbone is used to prevent data signal from bouncing back/absorb signals.
- Use of internet in environmental conservation club
- Source of knowledge on environmental matters;
- Collaboration with peers from other schools or organisations;
- Dissemination of information on what the club is doing;
- Seeking for funding from sponsors.(First 3 x 1)
-
- Benefits of linking branch B and C
- Speed of communication between B and C is increased since the traffic between the two branches can be re-routed through the link BC;
- If either AC or AB is down, the three branches can still communicate;
- If the HQ systems fail, the two branches B and C can communicate using this link.(First 2 x 2)
- Ways to protect company network from hackers
- Changing password frequently
- Use of encryption;
- Use of data proxies;
- Use of firewalls to filter unwanted packets;
- User restriction e.g. passwords/ biometrics.
- Use of complex password.(Any 3 x 1)
- Benefits of linking branch B and C
-
-
- Formats applied
- Bold, strikethrough, underline, italics, centre alignment, dropcap, bulleted list, line height / spacing, 2 column paragraph, column break, casing, font type, left alignment, column separator.(First 6 × 1/2 )
- Tools for proofreading
- Spell checker and grammar/ dictionary;
- Autocomplete;
- Autocorrect;
- Thesaurus.(Any 3 x 1)
-
- = @ or + Countif (B2: B6, “>10,000”)
(B2:B6) Argument range √ 1
(>10,000) Criteria √ 1
All Formula correct √ 1 - At D3
Formula is
$ B3 * C$2 √ 1
= 16000 x 2
= 32, 000 √ 1
- = @ or + Countif (B2: B6, “>10,000”)
-
- Formats applied
-
- Characteristics of octal number system.
- each symbol is represented by 3 bits.
- The number is made of 8 symbols 0, 1, 2, ...............7;
- Maximum value of a single digit is 7 (one less than the value of the base);
- This number system uses base 8.(Any 2 x 1)
-
- 111.1012 to decimal
111 = 710 √ 1
0.101 = 1 + 0 + 1 =5 √ 1 OR
2 4 8 8
= 0.625
111.1012 = 7.62510 or 7.625 √ 1
210
111 = 1 x 22 +1 x 21 + 1 x 20
= 4 + 2 + 1 = 710
1012 = 1 x 2-1 + 0 x 2-2 + 1 x 2-3
= 1 x 1 + 0 x 1 + 1 x 1
2 4 8
= 0.5 + 0 + 0.125 = 0.62510
therefore: 111.1012 = 7.625 - 14.687510 to binary
1410 = 11102 √ 1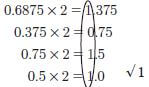
decimal portion = 0.1011 √ 1
Number is 1110. 10112 √ 1
- 111.1012 to decimal
-
- 1710 = 10001 or 100012 √1
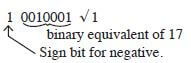
- 1710 = 10001
In 8 bit 00010001
Reverse bits 1 1 1 0 1 1 1 0 √1
+ 1
1 1 1 0 1 1 1 1
Number is 1 1 1 0 1 1 1 12 √
- 1710 = 10001 or 100012 √1
- 110.112 + 11.0112
1 1 0.1 1 0
+ 0 1 1.0 1 1 √ 1
1 0 1 0 . 0 0 1 √ 1
- Characteristics of octal number system.
Download KCSE 2014 Computer Studies Paper 1 Questions with Marking Scheme.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

