Instructions to Candidates
- Write your name and index number in the spaces provided above.
- This Paper consists of two sections A and B.
- Answer ALL the questions in section A.
- Answer question 16 (compulsory) and any other THREE questions from section B.
- All answers should be written in the spaces provided.
- This paper consists of 9 printed pages. Candidates should check to ensure that all pages are printed as indicated and no questions are missing
FOR EXAMINER’S USE ONLY
|
Section |
Questions |
Candidate’s score |
|
A |
1- 15 |
|
|
B |
16 |
|
|
17 |
|
|
|
18 |
|
|
|
19 |
|
|
|
20 |
|
|
|
TOTAL SCORE |
|

Questions
SECTION A (40 marks)
Answer all questions in this section in the spaces provided
- Name two functions of each of the following memories in a computer system (2 marks)
- RAM
- Hard disk
- List two application areas of artificial intelligence ( 2 marks)
- Explain briefly the following terms as used in desktop publishing (3 marks)
- Embedded object
- Auto flow
- Zoom
- Give four ways of identifying an illegal copy of an operating system ( 4 marks)
- State three ways in which horticultural farmers can benefit from the use of information and communication technology (3 marks)
- Define the following terms (2 marks)
- Password
- Authentication
- Outline three roles of an internet service provider(ISP) ( 3 marks)
- State two roles of
- Webmaster (2 marks)
- Network administrator (2 marks)
- List three advantages of using computer aided design (3 marks)
- List two files used in mail merging (2 marks)
- State any three disadvantages of using the magnetic tape ( 3 marks)
- With reference to cables list two reasons why a keyboard may not function correctly (2 marks)
- Kenya has been facing a lot of problems from insurgents of Alshabab terror group in Somalia. Give three ways in which robots can be used by Amison during war in Somalia. ( 3 marks)
- The formula = $Z49 + G$19 was typed in cell K31 and was copied to cell P17 of a spreadsheet. Write the formula in the destination cell (1 mark)
- Simulation is one of the application areas of computers.
- Define the term simulation (1 mark)
- Name two application areas of simulation (2 marks)
SECTION B (60 MARKS)
Answer question 16 and any other THREE questions in this section
- Study this flowchart and use it to answer questions that follows
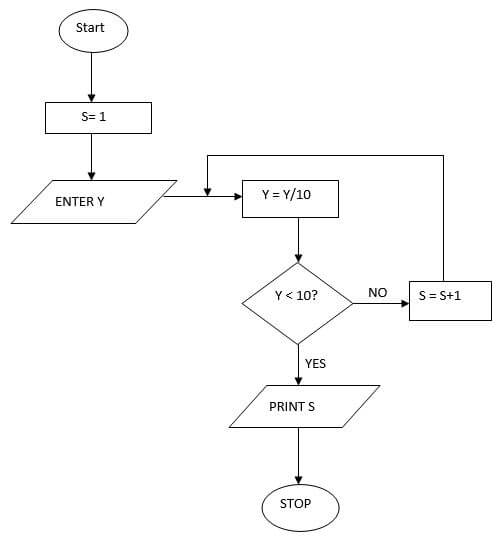
- Give the expected output from the flowchart when the value of Y is (6 marks)
- 48
- 9170
- 800
- Write the pseudocode that can be used to create a program represented by the above flowchart (6 marks)
- State three advantages of low-level languages (3 marks)
- Give the expected output from the flowchart when the value of Y is (6 marks)
-
- Use twos complement to perform the following arithmetic operations
- 1510 - 1210 (4 marks)
- 101112-10112 (3 marks)
- 10112 is a ones complement binary representation of a negative number using four bits work out the likely positive equivalent in base 10. (4 marks)
- Convert the decimal fraction 10.37510 into its binary equivalent (4 marks)
- Assuming the existence of base five, list the numbers used in the number system (1 mark)
- Use twos complement to perform the following arithmetic operations
-
- A company in Kericho town wishes to link its offices that are spread across the county through wireless or fibre optic network media.
- State three advantages of using wireless over fibre optic network media (3 marks)
- Name two wireless communication devices (2 marks)
-
- Differentiate between Ethernet and token ring topology (2 marks)
- List two advantages and two disadvantages of hierarchical network topology (4 marks)
Advantages
a) …………………………………………………………………………………………………………………
b) …………………………………………………………………………………………………………………
Disadvantages
a) …………………………………………………………………………………………………………………
b) …………………………………………………………………………………………………………………
- State two importance of the Front-End Processors (FEP) in a network system (2 marks)
- Describe peer to peer networking (2 marks)
- A company in Kericho town wishes to link its offices that are spread across the county through wireless or fibre optic network media.
-
- Give two reasons for storing files in directories and sub directories (2 marks)
- Explain time sharing data processing mode giving two advantages and two disadvantages of its application (6 marks)
Advantages
i) ……………………………………………………………………………………………………………………
ii) ……………………………………………………………………………………………………………………
Disadvantages
i) ……………………………………………………………………………………………………………………
ii) …………………………………………………………………………………………………………………… - List four importance of training the staff or users after the implementation of a new system (4 marks)
- List three contents of a feasibility study report ( 3 marks)
- The information below is maintained by the patron of Kesup Girls wildlife club. Study it and answer the questions that follow.
Name
Form
Admission number
Membership number
Group
Grace
Memo
Faith
Tabitha
Marion
Chemutai
Albina
Jane
Janet
Rita
Elvis
4K
3G
2K
4G
3R
2G
2R
4R
3K
1R
1G
2720
2812
2929
2712
2820
2915
2926
2946
2805
3229
3213
S001
T001
T003
M001
A001
S002
N001
AB001
T002
N002
M002
Lion
Zebra
Zebra
Warthog
Warthog
Lion
Elephant
Elephant
Zebra
Elephant
Warthog
- Explain the terms fields, records and file (3 marks)
- State the most appropriate data type for the fields
- Admission number (1mark)
- Membership number (1 mark)
- Name the most appropriate primary key for the database (1 mark)
- If a database was to be created from the list; the following objects: forms, Tables, queries and reports are likely to be used
- State the purpose of each of the objects (4 marks)
- Name the objects that cannot be used to store date in the list (3 marks)
-
- Give the number of field values that are in the list (1 mark)
- Give the number of records that are in the list (1 mark)

MARKING SCHEME
- Importance of:-
-
- RAM - hold data that is urgently needed by the processor
- Short term storage/ temporary storage for holding data instruction during processing
- Hard disk - used to store large volumes of data that is not urgently required by the processor. Also for back up of os and data (Correct description @ 1mk x 2 = 2mks)
-
- Application areas of artificial intelligence
- Expert system
- Natural language processing
- Robotics
- Artificial neural networks (Each correct @ 1mk x 2 = 2mks)
-
- Embedded object
a separate image/ graphic/ clip that is placed into a file e.g. movie clip pasted into DTP document would be considered as an embedded object - Auto flow: Facility that allows text to flow automatically from one textbox to the next when the first text box is full
- Zoom - changing the magnification of publication page either to get a closer view (zoom in) or to see more of the page at a reduced size (zoom out). (Correct description @ 1mk)each x 3 = 3 marks
- Embedded object
- Ways of identifying an illegal copy of an operating system
- No license agreement as certificate of authenticity
- Prices that are extremely cheap
- No documentation manual
- When one connects to the internet for authentication, the report from the manufacturer indicates that the user may be a victim of software counterfeit.
- Frequent run time or occurrence of fatal error when using the machine. (Each correct @1mk x 4 = 4mks)
-
- Source of information for the best farming practices
- Searching tool for best market for their produce
- Marketing tool
- ICT can also be used by farmers to manage complex business systems
(any correct 3 @ 1mk x 3 = 3mks)
- Definition
- Password – Is a code that must be keyed in so as to access a file or a system
- Authentication – is the process of verifying a log on credentials of a user requesting access to a computer system or a resource. (Each correct definition @ 1mk x 2 = 2mks)
- Roles of an I.S.P
- Link user to the internet
- Host websites
- Provide customized email addresses
- Manage internet traffic
- Provide firewalls (any 3 correct @ 1mk x 3 = 3mks)
-
- Design, develop and test websites
- Maintain the websites
- Upload information into the website
- Monitor or control access to the website (any 2 @ 1mk each x 2= 2mks)
- Configure a computer network
- Maintain and enforce network security measures
- Check the user of computer network resources
- Troubleshoot a network (any 2 x@ 1mk each x 2=2mks)
- Design, develop and test websites
- Advantages of using computer aided design
- Easy simulation and testing of models
- Duplicates of design are easy to produce
- Easier to make changes or update the original design
- The length of time taken to draw design is reduced/ faster (Any 3 @ 1mk x 3 = 3mks).
-
- Primary file/ main document
- Secondary file/ data source
- Merged file / letter (any 2 @ 1mk x 2 = 2mks)
- Disadvantage of using magnetic tape
- Wastage of space due to inter record gap (IRG)
- Tapes are susceptible (prone) to dust, stroke and magnetic fields which distort data on the tape
- Tapes have short life span (average of about 2 years)
- Data stored on a tape must be read/ accessed sequentially
- Data stored on magnetic tape ( and - disk) is not human readable e.g. if you wish to verify the accuracy of data stored on tape, a computer run would have to be made, in order to read the content on the tape and print it. (Any 3 @ 1mk x 3 = 3mks).
- Reasons why keyboard may not function correctly in reference to cabling
- Keyboard might not be connected through the right port
- Keyboard might not be connected at all to the port
- Pin(s) in the keyboard could be bent or broken
- There could be breakage of the cable (Any 3 @ 1mk x 3 = 3mks).
- Ways in which robots can be used in the army
- Detect bombs set up by the enemy and then detonate them
- Spy on the activities of the enemy
- Clear land mines any disarm bombs
- Confuse the enemy by deploying decoys
- Retrieve items from dangerous war zones (Any 3 @ 1mk x 3 = 3mks).
- H20 + P$18 (correct answer = 1mk)
-
- stimulation – is the modeling /imitating/mimicking/demonstrating real world situations.
(Correct definition – 1mk) - Application areas of simulation
- Aviation
- Lab forecasting
- Missile launch
- Entertainment games
- Space exploration
- Vehicle accidents
- Medical training (Any 2 correct @ 1mk x 2 = 2mks).
- stimulation – is the modeling /imitating/mimicking/demonstrating real world situations.
-
-
- = 1
- = 3
- = 1 (Each correct @ 2mks x 3 = 6mks)
- pseudocode
Start marks
S=1 start / stop – 1mk
Read Y initialization – 1mk
Repeat input/ output – 1mk
Y-Y/10 looping – 1mk
If Y <10 Then if statement -1mk
S=S+1 logical sequence – 1mk
End if
Until Y<10 total = 6mks
Print S
Stop - Advantages of low - level languages
- The CPU can easily understand low - level languages without or with little translation
- The program instructions can be executed by the processor much faster as complex instructions are already broken down into smaller simpler ones
- They have a closes control over the hardware, are highly efficient and allow direct control of each operation
- They require less memory space
- They are stable i.e. do not crash once written
- Not commonly used, hence can be used to code secret programs (Each 3 correct @ 1mk x 3 = 3mks).
-
-
-
-
- 1510
= 11112
1210=10112 √1 mk
Ones complement of = 11002 = 00112 √(1mk)
Therefore:
11112
+ 10112 √
Overflow bit (1) 10112
1011 +
+ 1 (overflow bit)
= 11002√ 1mk
- 1510
- 101112 - 10112
Ones complement of 010112 = 101002√ 1mk
Therefore
101112
10100
(1)01011 √1mk
Add the overflow bit
010112 + 12 =011002 √1mk
-
- Binary positive is 00102 √2mks
Convert to base 10 √1mk
= + 210 √1mk - Whole numbers
10/2 = 5 R 0
5/2 = 2 R 1 ↑ read upward. √1 mk
2/2 =1 R 0 ↑
½ = 0 R 1 ↑
Fractional part
0.375x 2 = 0.75
.75 x 2 = 1.50 ↓ read the whole number downwards √1mk
.5 x 2 = 1.00 ↓
= 0.0112 ↓
Combine the two
= 10102 + 0.0112 √1mk
= 1010.0112 √1mk - Base five numbers
0, 1, 2, 3, 4 √1mk
-
-
-
- Advantages of wireless over Fibre optic
- No cumbersome cabling needed between sites
- Do not require access rights on the land between the buildings
- Wireless support un-directed signals therefore allowing more recipients
- Allows remote access to the network to the network signals
- Less risks of vandalism (any correct 3 @ 1mk x 3 = 3mks)
-
- access points
- Wireless antence
- Personal computer memory card international association card (Any 2 correct @ 1mk x 2= 2mks)
- Advantages of wireless over Fibre optic
-
- In Ethernet topology , all computer listen to the network media and a particular computer can only send data when none of the others is sending while in token ring (topology the data to be transmitted is placed in a special packet which then goes around the network. Only the computer whose address is on the data held in the token will pick the token to read it. (Correct difference = 2mks)
- Hierarchical topology
- Advantages
- Provide centralized control
- Easy to add and remove notes
- Easy to isolate faults
- If a non- critical node falls, the network is not affected since partial communication is still possible
- It is possible to give control in the network to the DTE’s other than server
- Enhances data security and privacy (Any 2 correct @ 1mk x 2 = 2mks).
- Disadvantages
- If the parent node fails, the network fails because it controls all other computers in the network
- If the linear backbone fails, the network fails
- Installation is expensive
- Data moves slowly along the branches
- It is difficult or complex to implement in a wide area network (Any 2 correct @ 1mk x 2 = 2mks).
- Advantages
- Importance of the front end processor
- They link terminals to the central/ host computers
- They are used to control the communication information between the various work stations and the host computer
- They handle input and output activities from various terminals
- They relieve the main processor from excess storage and processing by handling some of the limited processing activities (Any 2 correct @ 1mk x 2 = 2mks).
- This is a network situation where all the connected computers are equal and each work station in the network acts both as the client to resources hosted by other computers and a server to the resources it hosts.
-
-
-
- Classification of related files will be easier
- Retrieving central files will be easier (Any 2 correct @ 1mk x 2 = 2mks).
- Time sharing mode is where the central processor serves two or more users with different processing requirement (correct definition = 2mks)
- Advantages
- Better services to user since the output is fast
- User interaction is possible through terminals (Any 2 correct @ 1mk x 2 = 2mks).
- Disadvantages
- The user has no control over the central computer
- The response time is slow where there are many tasks (Any 2 correct @ 1mk x 2 = 2mks).
- Advantages
- Importance of training staff or users
- To remove the fear of change from them
- To convince the staff of the user department on the effectiveness and efficiency of the new system
- To enable the staff run the system or to show users how the system can help them perform their job better
- To enable the staff to cope with the processing tasks of the new system
- Contents of feasibility study report
- Recommendations on whether to continue or abandon the project
- Methods used to collect data
- Benefits and limitations expected (whether cost effective)
- Technology required to develop and maintain the project
- Installation and running cost
- Time limit (Any 3 correct @ 1mk x 3 = 3mks).
-
-
- Field values are the values assigned to the attributes i.e. actual names classes,
- The field value for each student constitutes a record
- The collection of all student records is the file. (correct description each @ 1mk x 3 = 3mks)
- Admission number - Text
- Membership number - Text (Each correct @ 1mk x 2 = 2mks)
- Membership number (correct statement = 1mk)
-
-
- Table – for storing data
- Form – data entry, editing and viewing the records
- Query – extracting data based on some criteria, performing calculations
- Reports – creating summaries for data, performing calculations (Each correct purpose @ 1mk x 4 = 4mks)
-
- Forms
- Queries
- Reports (Any 3 correct @ 1mk x 3 = 3mks).
-
-
- 55 (correct = 1mk)
- 11 (correct = 1mk)
- Field values are the values assigned to the attributes i.e. actual names classes,
Download Computer Studies P1 Questions and Answers - Mangu High School Trial Mock Exams 2021/2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

