Instructions
- This paper consists of TWO sections.
- Answer ALL questions in section A.
- Answer Question 16 and any other THREE Questions from Section B

QUESTIONS
SECTION A: 40 MARKS
Answer all the questions in this Section.
- State two reasons for the increased use of Laptop computers in modern workplaces (2marks)
- What precautions would you take in the computer laboratory incase users are complaining of overheating and suffocation. (2marks)
- Convert the decimal number 15.37310 to its binary number system equivalent. (3marks)
- With an aid of a diagram describe the difference between Repeat Until and While… Do (3marks)
- State three circumstances which may force an individual to acquire an impact printer instead of non-impact printer. (3marks)
- Sam prepared a five-page brochure of Maseno School using Ms-publisher. He wanted to insert a school badge in each page of the publication. State two methods he need to apply to execute this task. (2marks)
- State the difference between ones complement and twos complement (2marks)
- Explain the impact of Information Technology on organization in each of the following areas. (2 marks)
- Competition.
- Pace of growth.
- State four benefits of cloud storage in computing. (4marks)
- Describe the functions of the following disk management operations.
- Defragmentation (1mark)
- Partitioning (1mark)
- Describe four ways through which an organization can minimize threats to it data integrity. (4marks)
- Study the following three sections of code and name accordingly (3marks)
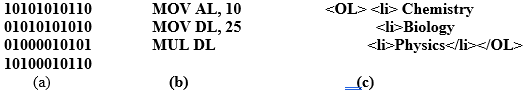
- Identify how the operating system will label the following drives in case a computer has one floppy drive, one hard disk partition into two and a DVD. (3marks)
- Five students Jane, Beryl, Baroness, Linda, and Jael scored the following marks in mathematics: 45, 76, 34, 65 and 45. The marks were recorded in cell C3 to C7. Write down the most appropriate function that can be used to give those positions so that they can be awarded in descending order. (3marks)
- Match the following statements with repeater, router or a bridge. (2 marks)
STATEMENT
DEVICE
Operates at data link layer
Determine the best path for data to follow
Regenerates signals
Forwards everything which it doesn’t recognize
SECTION B: 60 MARKS
ANSWER QUESTION NUMBER 16 ANY OTHER THREE QUESTIONS FROM THIS SECTION
-
-
- Define the following terms as used in programming. (3marks)
- Machine dependent
- Bug
- Syntax
- Give two reasons to justify why most programmers prefer using compilers instead of interpreters. (2marks)
- Describe two limitations of machine language. (2marks)
- Study the pseudo code below and design its equivalent flowchart (8marks)
Start
Count=1
For count =1 to 5 Do
Get Value 1 and Value 2
If Value 1 > Value2 Then
Maximum =Value1
Else
Maximum =Value2
Endif
Display Maximum
Count=Count+1
Stop
-
-
- The five-bit number 00101 is used to represent decimal number 5, show three methods of coding for negative 5. (3marks)
- Convert the binary number 1010111101011011100012 into its
- Octal equivalent (2marks)
- Hexadecimal (2marks)
- Convert 10101.0101012 to decimal (3marks)
- Use 8-bit twos to subtract 3510 from 1710 (3marks)
- Perform the following calculation (2marks)
1100012+11112-111112
-
- Define the term desktop publishing. (2marks)
- List three nonprinting guides used in Desktop publishing (3marks)
- Explain the following features as used in DTP when manipulating graphical objects.
- Fill (1mark)
- Stroke (1mark)
- Describe any three types of action queries. (3marks)
- Describe the function of the following features of a query grid.
- Criteria (1mark)
- Show (1mark)
- Mention three functions of database management software. (3marks)
-
- State three causes of system entropy. (3marks)
- Describe three main ways of maintaining a computer-based system. (3marks)
- State three advantages of using pilot changeover strategy in system development (3marks)
- State a stage in system development life cycle where each of the following activities are carried out.
- Identifying shortcomings of the system (1mark)
- Prepare training manuals (1mark)
- Calculating the cost benefit analysis (1mark)
- State three outcomes that may result from using incorrect requirement specifications during system development. (3marks)
-
- Define the following terms.
- Downloading (1mark)
- Uploading (1mark)
- Blog (1mark)
- Briefly describe how internet platform have revolutionized business operations in the 21st century. (3marks)
- Mention three emerging issues that make many people have a negative perception about internet. (3marks)
- Explain the following terms as used in data processing.
- Multiprocessing (1mark)
- Batch processing (1mark)
- Explain the following types of errors.
- Overflow error (1mark)
- Truncation error (1mark)
- Mention two application areas of real processing (2mark)
- Define the following terms.

MARKING SCHEME
- State two reasons for the increased use of Laptop computers in modern workplaces
- Laptops are portable and can be carried from one to another with ease.
- Laptops have rechargeable batteries therefore can be used even in places without electricity once charged.
(Award 1mark each max 2)
- What precautions would you take in the computer laboratory incase users are complaining of overheating and suffocation?
- Fit standard windows and doors.
- Have vents.
- Install air conditioning systems.
- Avoid overcrowding in the laboratory.
(Award 1mark each max 2)
- Convert the decimal number 15.37310 to its binary number system equivalent (3marks)

Award 1 mark for converting 152 to binary.
Award 1 mark for converting 0.37310 to binary.
Award 1 mark for the combined answer - With an aid of a diagram describe the difference between Repeat Until and While… Do
- Repeat until allows the statements within it to be executed at least once since the condition is tested at the end of the loop.
- While loop is used if a condition has to be met before the statements within the loop are executed
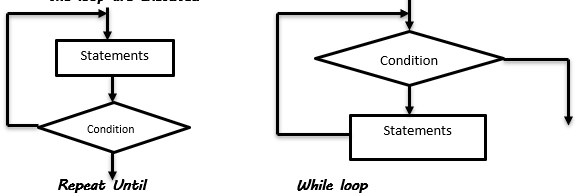
Award 2 marks for the difference and ½ each for the illustration max 1
- State three circumstances which may force an individual to acquire an impact printer instead of non-impact printer.
- When an individual has less money therefore cannot afford non-impact printers
- When the output required is of low quality
- When there is need for multiple copies in one instance of print
(Award 1 mark each max 2)
- Sam prepared a five-page brochure of Maseno School using Ms-publisher. He wanted to insert a school badge in each page of the publication. State two methods he need to apply to execute this task.
- Insert the badge at the footer or header.
- Use the master page.
(Award 1mark each max 2)
- State the difference between ones complement and twos complement.
- Ones complement has two ways of representing zero while Two’s complement has only one way of representing zero.
- In ones complement the overflow is added and in twos complement the overflow is ignored
- In ones complement the binary bits are bitwise or negated while in twos complement the binary bits are bitwise then one is added
(Award 1mark each max 2)
- The impact of information Technology on organization in each of the following areas
- Competition
- Ability to advertise on the internet
- Improve quality of goods
- Reduced operational cost
- Pace Growth
- Reduced cost
- Reduced need for man power
- Reduced space requirement
- Greater output
(Award 1mark each max 2)
- Competition
- State four benefits of cloud storage in computing
- Flexible
- Mass storage
- Cost efficient.
- Ensure data security.
- Scalable
(Award 1mark each max 4)
- Describe the functions of the following disk management operations.
- Defragmentation
- To enable files and folders to be accessed within the shortest possible.
- Partitioning
- For backup purposes
- To all the computer to run more than one operating system
(Award 1mark each max 2)
- Defragmentation
- Describe four ways through which an organization can minimize threats to it data integrity.
- Use devices that capture data directly from source.
- Using error detection and correction software when transmitting data
- Design user interfaces that restrict invalid data entry
- Backup data regularly
- Control access to data by enforcing security measures.
(Award 1mark each max 4)
- Study the following three sections of code and name accordingly.
10101010110 MOV AL, 10 <OL> <li> Chemistry
01010101010 MOV DL, 25 <li>Biology
01000010101 MUL DL <li>Physics </li></OL>
10100010110
(a) (b) (c)- (a) Machine Language
- (b) Assembly language
- (c) Web scripting language /HTML
(Award 1mark each max 3)
- Identify how the operating system will label the following drives in case a computer has one floppy drive, one hard disk partition into two and a DVD.
- Floppy drive A
- Hard disk C and D
- DVD E
(Award 1mark each max 3)
- Five students Jane, Beryl, Baroness, Linda, and Jael scored the following marks in mathematics: 45, 76, 34, 65 and 45. The marks were recorded in cell C3 to C7. Write down the most appropriate function that can be used to give them positions so that they can be awarded in descending order.
- =RANK (C3, $C$3:$C$7, 0)
- Correct Function 1mark
- Correct range with absolute reference 1mark
- Correct bracket to bracket 1mark
- Match the following statements with repeater, rooter or a bridge
STATEMENT
DEVICE
(a). Operates at data link layer
Bridge
(b). Determine the best path for data to follow
Router
(c). Regenerates signals
Repeater
(d). Forwards every thing which it doesn't recognize
Bridge
each max 2) -
-
- Define the following terms as used in programming.
- Machine dependent
- Software application that is designed to operate on a specific computers or hardware devices. Programs with this attribute are optimized for the target hardware.
- Bug
- Bug is an error, flaw or fault in a computer program or system that causes it to produce an incorrect or unexpected result.
- Syntax
- Syntax refers to the rules that define the structure of a language. Syntax in computer programming means the rules that control the structure of the symbols, punctuation, and words of a programming language.
(Award 1mark each max 3)- Give two reasons to justify why most programmers prefer using compilers instead of interpreters.
- Compiled programs run quickly since they have already been translated.
- A compiled program can be supplied as an executable file. An executable file is a file that is ready to run.
- Compilers optimize code. Optimized code can run quicker and take up less memory space.
(Award 1mark each max 2)
- Describe two limitations of machine language.
- Machine dependent
- Difficult to learn and use.
- Difficult to debug.
- Programs written using machine language are difficult to maintain.
(Award 1mark each max 2)
- Study the pseudo code below and design its equivalent flowchart.
Start
Count=1
For count =1 to 5 Do
Get Value 1 and Value 2
If Value 1 > Value2 Then
Maximum =Value1
Else
Maximum =Value2
Endif
Display Maximum
Count=Count+1
Stop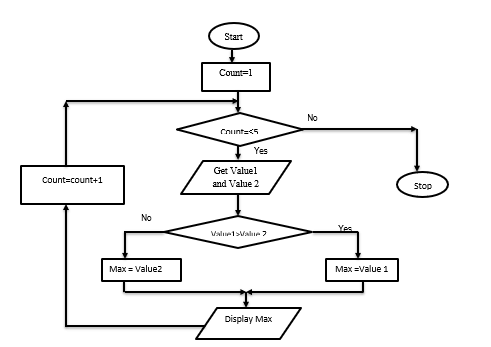
- Give two reasons to justify why most programmers prefer using compilers instead of interpreters.
- Syntax refers to the rules that define the structure of a language. Syntax in computer programming means the rules that control the structure of the symbols, punctuation, and words of a programming language.
-
-
- The five-bit number 00101 is used to represent decimal number 5, show three methods of coding for negative 5.
Ones complement
Twos complement
Prefixing a sign bit
00101
11010
00101
11010
+ 1
11010
00101
10101
(Award 1mark each max 3) - Convert the binary number 1010111101011011100012 into its
- Octal equivalent
101 011 110 101 101 110 001
5 3 6 5 5 6 1
53655618
Grouping the bits in three bits and getting equivalent per group =1mark
Final answer =1 mark - Hexadecimal
1 0101 1110 1011 0111 0001
1 5 E B 7 1
15EB7116
Grouping the bits in four bits and getting equivalent per group =1mark
Final answer =1 mark
- Octal equivalent
- Convert 10101.0101012 to decimal.
(24x1) + (23x0) + (22x1) + (21x0) + (20x1)
16 + 0 + 4 + 0 + 1 = 21
¼ =0.25
1/16 =0.0625
1/64 =0.015625
0.328125
21.328125
Conversion of the whole number part = 1mark
Conversion of the fraction part = 1mark
Combined answer 1 mark - Use 8-bit twos to subtract 3510 from 1710
35 = 100011
17=10001
00100011
11011100……………1c
11011101 …………2c
+10001
11101110
Getting the binary equivalent of 35 and 17 @1mark
Ones complement ½ mark.
Twos complement ½ mark.
Answer 1mark - Perform the following calculation.
1100012+11112-111112
110001
1111
1000000
- 11111
=100001
Addition answer = 1mark
Subtraction answers 1 mark
- The five-bit number 00101 is used to represent decimal number 5, show three methods of coding for negative 5.
-
- Define the term desktop publishing.
- Is the process of producing publication by designing, inserting, editing, formatting, and printing of text and graphical objects using desktop publishing software
(Award 2marks max 2)
- Is the process of producing publication by designing, inserting, editing, formatting, and printing of text and graphical objects using desktop publishing software
- List three nonprinting guides used in Desktop publishing.
- Margin guide
- Ruler guide
- Column guide
(Award 1mark each max 3)
- Explain the following features as used in DTP when manipulating graphical objects.
- Fill
- Fill refer to applying pattern such as shading.

- Fill refer to applying pattern such as shading.
- Stroke
- Stroke refer to applying line style.
(Award 1mark each max 2)
NOTE accept illustrations.
- Stroke refer to applying line style.
- Fill
- Describe any three types of action queries.
- Delete query – deletes specified records from one or more tables.
- Make table query – creates a new table from dynaset.
- Append query – adds data in a table.
- Update query – change the data in a data to reflect the current position.
(Award 1mark each max 3)
- Describe the function of the following features of a query grid.
- Criteria
- This is where you enter a condition or expression that will be used by the query to filter records.
- Show
- Is used to specify whether to display a field in the dynaset.
(Award 1mark each max 2)
- Is used to specify whether to display a field in the dynaset.
- Criteria
- Mention three functions of database management software.
- Keep statistics of data items a database.
- Ensure security and integrity of data by safeguarding it against unauthorized access.
- Interface between database files and other application programs
- Allows users to update or modify existing records.
- Allows authorized users to add or delete records.
(Award 1mark each max 3)
- Define the term desktop publishing.
-
- State three causes of system entropy
- Advancement in technology
- New management policies
- Change in user needs
- Directives
(Award 1mark each max 3)
- Describe three main ways of maintaining a computer-based system.
- Perfective maintenance is software maintenance performed to improve the performance, maintainability, or other attributes of a computer program.
- Adaptive maintenance is modification of a software product performed after delivery to keep a software product usable in a changed or changing environment.
- Corrective maintenance is a concerned with put in place mechanisms that fix errors as they occur so as to keep the system running.
- Preventive maintenance involves carrying out activities that prevent occurrence of bugs.
(Award 1mark each max 3)
- State three advantages of using pilot changeover strategy in system development.
- Cheaper than parallel changeover
- The implementation is on a smaller scale and therefore it is easier to manage that direct changeover.
- Staff be trained gradually.
- If the new system does not work correctly, it only affects a smaller percentage of the organization.
(Award 1mark each max 3)
- State a stage in system development life cycle where each of the following activities are carried out.
- Identifying shortcomings of the system
- Problem definition
- Prepare training manuals.
- System implementation
- Calculating the cost benefit analysis
- Feasibility study
(Award 1mark each max 3)
- Feasibility study
- Identifying shortcomings of the system
- State three outcomes that may result from using incorrect requirement specifications during system development.
- The system may be costing more than what was projected.
- The system will be delivered later than schedule.
- The system will not meet the user’s expectation.
- The cost of maintaining and enhancing the system may be excessively high.
- The system may be unreliable and prone to errors and downtime.
- The system will not meet legal requirements.
(Award 1mark each max 3)
- State three causes of system entropy
-
- Define the following terms.
- Downloading
- Receiving data or a file from the Internet on your computer
- Uploading
- Sending data or a file from your computer to somewhere on the Internet.
- Blog
- A website that contains personal information which can easily be update.
(Award 1mark each max 3)
- A website that contains personal information which can easily be update.
- Downloading
- Briefly describe how internet platform have revolutionized business operations in the 21st century.
- Promoted E-commerce where business activities can be carried out all over the world provided there is internet connectivity.
- Internet have changed the mode of payment to electronic payment where money is transferred electronically.
- Monitoring and surveillance using CCTV camera. Managers can monitor business operation without necessarily going to the business premises.
- Internet open different avenues for communication between parties involved in business operations.
(Award 1mark each max 3)
- Mention three emerging issues that make many people have a negative perception about internet.
- Spread of malicious software.
- Security and Privacy
- Pornography and dirty sites
(Award 1mark each max 3)
- Explain the following terms as used in data processing.
- Multiprocessing
- Refer to processing of more than one tasks apparently at the same time.
- Batch processing
- Data is accumulated over a period of time then later processed at once.
(Award 1mark each max 2)
- Data is accumulated over a period of time then later processed at once.
- Multiprocessing
- Explain the following types of errors.
- Overflow error
- This type of error occurs if the result from a calculation is too large to be stored in the allocated memory space.
- Truncation error
- Result from having real numbers that have a long fractional fraction part which cannot fit in the allocated memory space therefore excess bits will be cut off.
(Award 1mark each max 3)
- Result from having real numbers that have a long fractional fraction part which cannot fit in the allocated memory space therefore excess bits will be cut off.
- Overflow error
- Mention two application areas of real processing.
- Airline reservation
- Defense application system like Radar
- Bus booking and reservation system
(Award 1mark each max 2)
- Define the following terms.
Download Computer Studies Paper 1 Questions and Answers - Wahundura Boys Mock Examination 2023.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students
