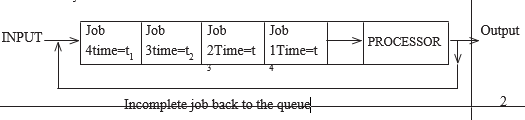INSTRUCTIONS TO CANDIDATES
- Write your name , school and index number in the spaces provided above
- This paper consists of TWO sections A and B
- Answer ALL questions in section A
- Answer question 16 and any other THREE questions from section B
- ALL answers should be written on spaces provided on the question paper
- This paper consists of 15 printed pages
- Candidates should check the question paper to ascertain that All pages are printed as indicated and that no questions are missing
FOR EXAMINERS USE ONLY
|
SECTION |
QUESTION |
|
|
A |
1-15 |
|
|
B |
16 |
|
|
17 |
||
|
18 |
||
|
19 |
||
|
20 |
||
|
TOTAL MARKS |

QUESTION
- State one function for each of the following elements of a computer system:
- Hardware (1 mark)
- Software (1 mark)
- Liveware (1 mark)
- Explain two health issues that could arise from the use of an unsuitable computer desk (4 marks)
- List two categories of system software (1mark)
- Explain two contents of a warranty that should be considered when purchasing computer hardware (4 marks)
- Students of a school intend to elect their school captain by secret ballot. State three ways in which computers can be used to improve the election process (3 marks)
- Figure 1 and figure 2 show icons representing commands used to manipulate graphics in a desktop publishing package.
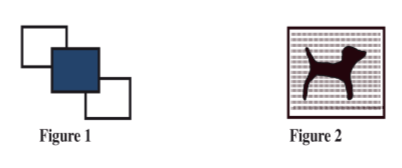
Explain the use of each of the icons labeled figure 1 and figure 2 - Give two differences between a Graphical User Interface (GUI) and a command line Interface. (4 marks)
- Identify each of the following symbols as used in a system flowchart.
 (1 mark)
(1 mark)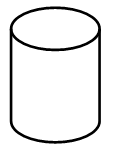 (1 mark)
(1 mark)
- A student typed a letter in a word processor and the last line of the letter flowed to the second page. State three ways in which the student could have adjusted the letter to fit on one page without changing the paper size. (3 marks)
- A computer user is unable to retrieve a file stored in a server in an organization. State three reasons why the user would need to contact the network administrator (3 marks)
- State three ways in which mobile phones have affected money transactions in the country (3 marks)
- State two items that an electronic mail should have for it to be sent. (2 marks)
- List four devices that use scanning technology that would be used to capture data directly from source. (2 marks)
- State two ways in which hardware failure is a threat to data security. (2 marks)
- Given the binary number 101011101111011, determine the number of:
- Nibbles (1 mark)
- Bytes (1 mark)
Section B (60 marks)
Answer question 16 and any other three questions from this section in the spaces provided
-
- state the advantages of using low level programming languages (2 marks)
- other than flowcharts, state three tools that can be used to present an algorithm (3 marks)
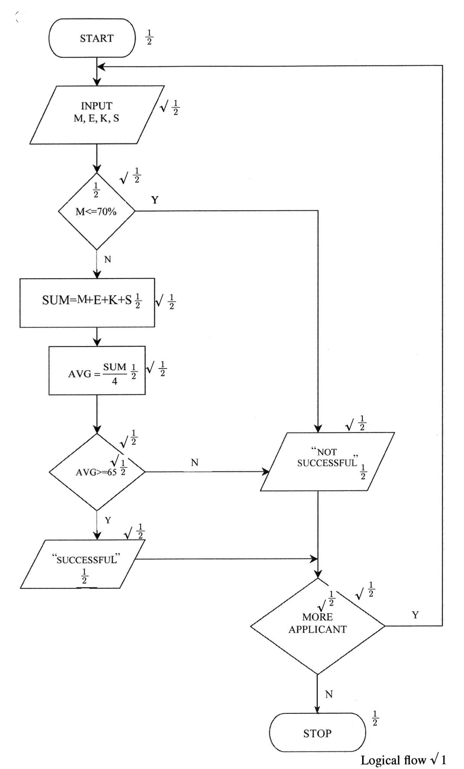
- A form one admission interview consists of four tests:
Mathematics, English, Kiswahili, and Science. In order to qualify for admission, an applicant must attain a minimum average of 65% in four tests and not less than 70% in Mathematics. All applicants must for the interview. Draw a flowchart that would read the scores for each applicant and determine whether an applicant is successful or not. (10 marks)
-
- with the aid of a diagram, describe time sharing mode as used in a computer data processing (5 marks)
- A company’s management has opted to use computers to process data. State four factors that the management needs to consider when selecting the company data processing mode. (4 marks)
- Explain the purpose of each of the following in system documentation:
- User manual (1 mark)
- Sample data (1 mark)
- Table descriptions (1 mark)
-
- State the role of each of the following data communication devices
- Repeater (1 mark)
- Router (1 mark)
- Figure 3 shows a network based on the bus topology.
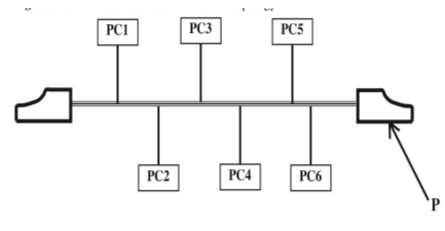
- Identify the component P (1 mark)
- State the function of the component labeled P (2 marks)
- Students of Neema secondary school formed an environmental club with a goal of taking part in environmental conversation activities. Outline three ways in which they can use the internet to achieve this goal. (3 marks)
-
- A company has three branches A, B and C where A is the headquarter. The local area network (LAN) at A is directly connected to the LAN at B also directly connected to the LAN at C. Explain two benefits of having the LAN at B also directly connected to the LAN at C. (4 mks)
- State three ways in which a company can protect its computer network from hackers (3 mks)
- State the role of each of the following data communication devices
-
- The following is an extract from a document created using a word processor.

Other challenges include:- Identify crisis: Who am i?
- Lack of self confidence and low esteem: I am worthless?
- Sense of hopelessness: where am I going?
- Confusion and ambiguity concerning moral issues: what is right and wrong?
- Negative impact of electronic media: Entertainment?
- Competitiveness in education the even playing field: Excellence by whom?
Not Me
Identify six formats that have been applied on the extract. (3 marks)
- State three tools in a word processor that would help a user to minimize spelling mistakes when creating a document (3 marks)
- The following is an extract of a spreadsheet created to manage sales. Use it to answer the questions that follow.
A
B
C
D
1
ITEM NAME
UNIT PRICE
UNITS SOLD
2
Bed
12,300
2
3
Wardrobe
16,000
4
4
Blanket
5,000
4
5
Mattress
7,000
5
6
Table
10,000
3
- Write a formula that will compute the number of items whose unit price is more than 10, 000. (3 marks)
- if the formula =$B2 * C$2 was placed in D2, state the output if it was copied to D3.
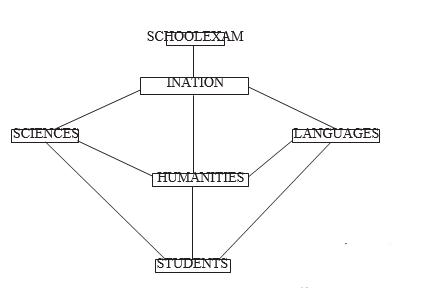
- A school administers examinations to all students in science, humanities and languages. Use the entities: EXAMINATIONS, STUDENTS, SCIENCES, HUMANITIES and LANGUAGES to illustrate a network database model.(4 marks)
- The following is an extract from a document created using a word processor.
-
- Describe the octal number system. (2 marks)
- Convert each of the following to the number system indicated:
- 111.1012 to decimal (3 marks)
- 14.687510 to binary (4 marks)
- Convert the number -1710 into 8-bit:
- Signed magnitude representation. (2 marks)
- Two’s compliment (2 marks)
- Perform the arithmetic operation. (2 marks)
110.112 + 11.0112

MARKING SCHEME
|
SECTIONA(40 marks) |
|||
|
QNS |
RESPONSES |
MARKS |
|
|
1. |
Function of:- |
||
|
(a)Hardware: To perform tasks of inputting, storage, outputting, processing |
|||
|
during data processing and communication. |
1 |
||
|
(b)Software:-Instructs the hardware/computer on what to do during data |
1 |
||
|
Processing. |
|||
|
-Provides interface between hardware and liveware. |
|||
|
-Accept functions of software based category i.e. system/ |
|||
|
application/ working/uses. |
1 |
||
|
(c)Liveware: Meant to design or operate a computer. |
|||
|
2. |
Problems arising from use of unsuitable computer desk.
(First 2 x 2) |
4 |
|
|
3. |
Categories of system software
|
(First 2 x ½) |
1 |
|
4. |
Two factors to consider when evaluating warranty
|
4 |
|
|
5. |
Three ways of using computers in electing school captain
|
3 |
||||
|
6. |
Figure1:Bring to front or bring to back
Figure2:Textwrap
|
1 1 |
||||
|
7. |
Distinction of GUI and command line operating systems
|
4 |
|
8. |
A system flow chart symbols
|
1 1 |
|
9. |
Ways of adjusting a document to fit a page
|
3 |
|
10. |
Role of network administrator
|
3 |
|
11. |
Impact of mobile phones
|
3 |
|
12. |
Items that an email must have:
|
2 |
|
13. |
Direct input methods
|
2 |
|
14. |
Insecurity arising from hardware failure
|
2 |
|
15. |
|
1 1 |
|
SECTIONB(60marks) |
||
|
16. |
(a) Advantages of using low-level language
(b) Three tools that can be used to develop an algorithm
|
2 3 |
|
(c)
|
||
| 17 |
(a) Time-sharing mode
|
3 2 |
|
(b) Factors to consider when selecting data processing mode
|
||
|
(c)
|
| 18 |
(a)
|
1 |
|
(b)(i)The component P is the terminator. |
1 |
|
|
(ii)Terminatorinabackboneisusedtopreventdatasignalfrombouncingback/absorbsignals. |
2 |
|
|
(c)Use of internet in environmental conservation club
|
3 |
|
|
(d)(i)Benefits of linking branch B and C
|
4 |
|
|
(ii)Ways to protect company network from hackers
|
3 |
|
|
19. |
(a)Formats applied
|
3 |
|
(b)Tools for proofreading
|
3 |
|
|
(c)
|
3 2 |
|
|
(d) Any4 connectors 4 each x ½ |
4 |
|
|
20. |
(a)Characteristics of octal number system.
|
2 |
|
(b)(i)111.1012to decimal |
210 111=1#22+1#21+1#20 =4 + 2 + 1 = 710 1012= 1#2+0#2+ 1#2 -1 -2 -3 =1#1+0#1+1#12 4 8 =0.5 + 0 + 0.125 = 0.62510 `111.101=7.625 2 |
|||
|
111=710√1 |
||||
|
0.101= 1+0+1=5√1 OR |
||||
|
2 4 8 8 |
||||
|
=0.625 |
||||
|
3 |
||||
|
111.1012= 7.62510or7.625 √ 1 |
||||
|
(ii)14.687510to binary |
||||
|
1410= 11102√ 1 |
||||
|
0.6875#2=1.375 |
||||
|
0.375#2=0.75 |
||||
|
0.75#2=1.5 |
||||
|
0.5#2=1.0 √ 1 |
||||
|
Decimal portion=0.1011√1 |
||||
|
Numberis1110.10112√1 |
4 |
|||
|
(c)(i) 1710= 10001 or 100012√1 10010001√ 1 binary equivalent of 17Signbit for negative. |
2 |
|||
|
(ii) 1710= 10001 In 8 bit 00010001 Reverse bits 1 1 1 0 1 1 1 0√1 + 1 1 1 1 0 1 1 1 1 Number is 11 1 0 11 1 12√ |
2 |
|||
|
(d) |
110.112+11.0112 |
|||
|
1 1 0.1 1 0 |
||||
|
+0 1 1.0 1 1√ 1 |
||||
|
1 0 1 0 . 0 0 1√ 1 |
2 |
|||
Download Computer Studies P1 Questions and Answers - Butula Sub-County Post Mock Exams 2021/2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students