INSTRUCTIONS TO CANDIDATES
- Answer ALL the questions in section A
- Answer question 16 (compulsory) and ANY OTHER THREE questions from section B.
For Official Use Only
|
Question |
Maximum score |
Actual score |
|
|
1-16 |
|
|
|
|
17 |
|
|
|
|
18 |
|
|
|
|
19 |
|
|
|
|
20 |
|
|
|
|
TOTAL SCORE |
|
||

QUESTIONS
SECTION A: (40 MARKS)
Answer ALL questions in the spaces provided
-
- Explain the emerging trends in microcomputer technology in relation to Size (1 mark)
- Mention two Analogue devices (2 marks)
-
- Identify and briefly describe three advantages of using computers in banking (1½ marks)
- State two advantages of using a mouse instead of a keyboard. (1 mark)
- State two reasons why Magnetic tapes are not commonly used as computer data storage medium today (1 mark)
-
- Give two advantages of the higher number of pixels per square centimeter. (1 mark)
- Differentiate between Data interface cable and power cable. (1 mark)
- Explain two differences between serial and parallel communication ports of a computer . (2 marks)
-
- What is line spacing as used in word processing? (½ mark)
- Describe any two line spacing specification used in Microsoft Word. (1 mark)
- Name the two documents used in mail merge. (1 mark)
- With reference to the concept of graphics as used in Microsoft word. Explain the difference between object linking and embedding? (1 mark)
- Who am I? (3 marks)
- Am is skilled in software/program development as per requirement and technical operations of computer hardware. I also develop and update both system and application software together with the associated documentations.
- Am is skilled in designing computer hardware and also improves on existing ones.
- I maintain, update & modify information on the websites to meet new demands by the users. I also monitor the access & use of internet connection by enforcing security measures
- During the COVID 19 pandemic, the government advised the citizens to use electronic funds transfer and other popular mobile phone money transactions to make payments.
- State how the above method of conducting business would help to curb on the spread of the disease. (2 marks)
- What is the meaning of Electronic Funds Transfer? (1mk)
- Define the term dual booting as used in computing. (1 mark)
- Differentiate between cropping and grouping. (2 marks)
- Other than flow chart, state two tools that can be used to present an algorithm . (2 marks)
- Differentiate between a deadlock and interrupt as used in operating system. (2 marks)
-
- Securem is a company that deals with providing security services to its clients. Name any two ways the company can protect its computer network from hackers. (2 marks)
- State three characteristics of a suitable password. (3 marks)
- During system development the system analyst should consider the correct requirement specifications for the new system. State any four outcomes that may result from using incorrect requirement specifications. (3 marks)
-
- Define the term Computer Aided Design. (1 mark)
- List two advantages of using Computer Aided Design. (2 marks)
- Explain two arithmetic errors that may occur during computerised data processing. (2 marks)
SECTION B (60 marks)
Answer question 16 and ANY OTHER THREE questions from this section in the spaces provided.
-
- Give two examples of syntax errors in programming. (2 marks)
- ScrabbleTM is a word game where the players are awarded points by creating words from a combination of letters each of which carry a different point value. A player is awarded the points for creating words from the combination. Write a pseudocode using CASE to read a letter and output the value equivalent to that letter from the following table. (8 marks)
LETTER
VALUE
A,E,I,L,N,O,R,S,T,U
1
D,G
2
B,C,M,P
3
F,H,V,W,Y
4
K
5
J,X
8
Z,Q
10
- Classify the following programming languages according to their category: (3 marks)
Programming language
Category
HTML
JAVA
JAVASCRIPT
PASCAL
VISUAL BASIC
LISP
- With aid of a diagram, explain the “Repeat Until” construct as used in structured programming (2 marks)
-
- State the stage in system development life cycle where each of the following activities are carried out:
- Identifying shortcomings of a system. (1 mark)
- Preparing the system migration plan (1 mark)
- Identifying the technologies that may be used in the proposed system. (1 mark)
- State three roles of a programmer in system development life cycle. (3 marks)
- E-mail technology has become a very important part of today’s communication. Explain any three problems associated with using e-mail technology for communication. (6 marks)
- Sarafina wants to download her favourite movie from YouTube. State any three factors that may determine how long it will take her to complete the download. (3 marks)
- State the stage in system development life cycle where each of the following activities are carried out:
- The following Digital Club Member details were to be entered in a database: Name, Date of registration, Registration fee and Class.
- Prepare a suitable structure showing field names and their field types (4 marks)
Field
Data type
Name
Text
Date of registration
Date
Registration fee
Currency or Number
Class
Text
- Name one other field that the Club Patron may need to add to uniquely identify the records (1 mark)
- Write the statement that can be used to select members of the class form 3. (2 marks)
Name
Date of registration
Registration fee
Class
Criteria/ Expression
- The following is an extract from a spreadsheet created to manage sales. Use it to answer the questions that follow.
A
B
C
D
1
ITEM NAME
UNIT PRICE
UNITS SOLD
2
HDD 300 GB
7,500
2
3
Optical Drive
4,500
8
4
DELL Latitude core i5
44,500
3
5
DDR4 8GB RAM
10,000
4
6
Lenovo Yoga Smart Tab
28,953
1
- Write a formula that will compute the number of items whose unit price whose price more than 10,000 (3 marks)
- If the formula =$B2*C$2 was placed in D2, state the output if copied to D3. (2 marks)
- Write the cell referencing used in c(ii) above. (1 mark)
- Write the data type that is stored in cell C5 and A6 respectively (2 marks)
- Prepare a suitable structure showing field names and their field types (4 marks)
-
- Define the term attenuation as used in networking and data communication. (1 mark)
- The following are figures of networking cables. Identify each. (2 marks)
figure 1 figure 2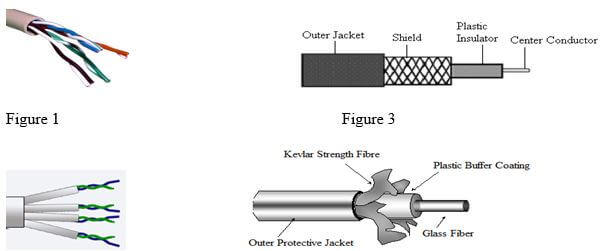
-
- Give two examples of network software (2 marks)
- In a network setup, list any two items that may be referred to as data terminal equipment. (2 marks)
- Explain the following terms as used in networking (4 marks)
- Remote Communication
- Distributed processing
- State four functions of a server in a network (4 marks)
-
- Determine the binary equivalent of the octal number 253243. (2 marks)
- Carry out the following binary arithmetic using ones complement. In each case leave your answer in base 10.
- 1010-108 (5 marks)
- 2BH-9H (6 marks)
- Arrange the following numbers in ascending order. (2 marks)
1016, 1010, 158, 10112

MARKING SCHEME
-
- Explain the emerging trends in microcomputer technology in relation to Size (1mk)
- PCs are becoming small and portable, e.g. personal Digital Assistant (PDA). (correct @1mk)
- Mention two Analogue devices (2mks)
- Computer used to control a flight Simulator for training pilots
- Bathroom scale
- Thermometer
- Speedometer
- Post- office scale
- A radio with a knob that slides in a slot to increase volume
- Explain the emerging trends in microcomputer technology in relation to Size (1mk)
-
- Identify and briefly describe three advantages of using computers in banking (1½mks)
- Speed and accuracy
- Easy to access information
- Easy to update records
- Requires less space for storage
- Improves data security and privacy (first 2@ 2mks)
- State two advantages of using a mouse instead of a keyboard. (1mk)
- The mouse is easy & convenient to use.
- Modern software includes an option to use it.
- It selects a position on screen much more quickly than a keyboard.
(first two correctr @ 1mk, ½ mk each)
- Identify and briefly describe three advantages of using computers in banking (1½mks)
- State two reasons why Magnetic tapes are not commonly used as computer data storage medium today (1mk)
- Are slow when retrieving data. This is because of the linear storage of data on the tape.
- Do not fully use their recording surface due to inter- record Gaps
(first 2 correct @ 1mk, ½ mk each)
-
- Give two advantages of the higher number of pixels per square centimeter (1mk)
- Higher screen resolution
- Displays of sharp & clear images
- The screen is able to display a higher number of different images
(first 2 correct @ 1mk, ½ mk each)
- Differentiate between Data interface cable and power cable (1mk)
- Data interface cable -These are special cables that connect all the peripheral devices to the motherboard and the CPU. They transmit data signals and information to and from the devices
- Power cable - Cable that supplies power to devices
(correct @ 1mk)
- Explain two differences between serial and parallel communication ports of a computer (2mks)
- Serial ports have 9 pins, while parallel ports have holes for 9 or 25 pins
- Parallel cables transmit several bits of data simultaneously, while serial cables transmit One bit at a time
- Serial cables are slower than parallel cable
- Serial cables allow for 2 ways communication (i.e. communication to and from the computer and the device connected to it) while parallel cables usually offer 1- way communication.
(first 2 @ 2mks)
- Give two advantages of the higher number of pixels per square centimeter (1mk)
-
- What is line spacing as used in word processing? (½mk)
- The vertical distance between two text lines in a document (correct @ ½ mk)
- Describe any two line spacing specification used in Microsoft Word. (1mk)
- Single space – accommodates the largest font in a line
- 1.5 line space- 1 ½ time that of single line spacing
- Double – twice that of single line spacing
- Exactly – a fixed line spacing that word does not adjust
- At least – the minimum line spacing that is needed to fit the largest font or graphic on the line.
- Multiple- a line spacing that is increased or decreased by a percentage that you specify (first 2 @ 2mks, each ½ mk)
- Name the two documents used in mail merge (1mk)
- main document
- Data source
(correct @ 1mk)
- With reference to the concept of graphics as used in Microsoft word. Explain the difference between object linking and embedding? (1mk)
- In linking, the object imported can only be edited in the original application from which it was created.
- In embedding, the object imported becomes part of the current application and can be edited there.
(correct @ 1mk)
- What is line spacing as used in word processing? (½mk)
- Who am I? (3mks)
- Am is skilled in software/program development as per requirement and technical operations of computer hardware. I also develop and update both system and application software together with the associated documentations.
- A Software developer/Engineer (correct @ 1mk)
- Am is skilled in designing computer hardware and also improves on existing ones.
- A Computer engineer (correct @ 1mk)
- I maintain, update & modify information on the websites to meet new demands by the users. I also monitor the access & use of internet connection by enforcing security measures
- A Web or Network Administrator (correct @ 1mk)
- Am is skilled in software/program development as per requirement and technical operations of computer hardware. I also develop and update both system and application software together with the associated documentations.
- During the COVID 19 pandemic, the government advised the citizens to use electronic funds transfer and other popular mobile phone money transactions to make payments.
- State how the above method of conducting business would help to curb on the spread of the disease (2mks)
- Instant – One receive s the money –During the lockdowns people were able to send financial support easily
- Used as a measure to quarantine or curb spread of COVID 19 which spreads easily through hands and infected items or surfaces
- Digital payments allow people to access goods and services while in quarantine or social distancing.
- digital payments were such an alternative to boosting or sustaining e-commerce in the country.
- Local Governments and well-wishers were able to fundraise and distributed vouchers
- Businesses experience some level of growth with e-commerce and online payments .
- What is the meaning of electronic funds transfer? (1mk)
- EFT (electronic fund transfer) - us used to move money from one account to another. Or from case of mobile phone transactions .The transactions are completed electronically, and the two accounts can be at the same financial institution or different financial institutions. Term “EFT” is an umbrella term that covers a broad range of electronic payments
- State how the above method of conducting business would help to curb on the spread of the disease (2mks)
- Define the term dual booting as used in computing. (1mk)
- A dual boot is when you INSTALL two operating systems on one computer and being able to choose which one to boot (correct @1mk)
- Differentiate between cropping and grouping. (2mks)
- Cropping is removing unwanted parts of a graphics
- Grouping is combining more than one object to be manipulated as one
(correct @ 2mks)
- Other than pseudocode, state two tools that can be used to present an algorithm (2mks)
- flow chart
- Decision Tables
- Decision Trees (any two @2mks)
- Differentiate between a deadlock and interrupt as used in operating system. (2mks)
- Deadlock refers to a situation whereby a particular job holds a resource and refuses to release it yet it is requesting for a resource held by another job
- Interrupt is a break from the normal sequecial processing of instructions in a program
(Correct @2mks )
-
- Securem is a company that deals with providing security services to its clients. Name any two ways the company can protect its computer network from hackers. (2mks)
- Log files
- Data encryption
- Use of passwords
- Firewalls (first 2 @2mks)
- State three characteristics of a suitable password. (3mks)
- Easy to remember
- Hard to guess
- Should be a combination of letters and numbers
- Should be a minimum of 8 characters (first 3@3mks)
- Securem is a company that deals with providing security services to its clients. Name any two ways the company can protect its computer network from hackers. (2mks)
- During system development the system analyst should consider the correct requirement specifications for the new system. State any four outcomes that may result from using incorrect requirement specifications. (3mks)
- More costs than was projected
- The system will be delivered later than schedule
- The system will not meet user’s expectations
- The cost of maintaining and enhancing the system may be excessively high
- The system may be unreliable and prone to errors and downtime
(first 4 @ 4mks)
-
- Define the term Computer Aided Design. (1mk)
- A system of programs and workstations used in designing engineering, architectural and scientific models ranging from simple tools to building. (correct @ 1mk)
- List two advantages of using Computer Aided Design. (2mks)
- The length of time taken to draw is reduced
- Easier to make changes or update the original design
- Duplicates of the design are easy to produce, distribute to various interested parties
- It is easier to view the end product before it is designed (first 2 @2mks)
- Define the term Computer Aided Design. (1mk)
- Explain two arithmetic errors that may occur during computerised data processing. (2mks)
- Truncation error
- Rounding off error
- Overflow error (state @½ mk , explain @½ mk, total 1mk each)
-
- Give two examples of syntax errors in programming. (2mks)
- Punctuation mistakes
- Improper naming of variables
- Wrong spellings of user defined and reserved words. (first 2@2mks)
- Scrabble is a word game where the players are awarded points by creating words from a combination of letters each of which carry a different point value. A player is awarded the points for creating words from the combination. Write a pseudocode to read a letter and output the value equivalent to that letter from the following table. (8mks)
START……………………………………………………………………………..½ MKLETTER
VALUE
A,E,I,L,N,O,R,S,T,U
1
D,G
2
B,C,M,P
3
F,H,V,W,Y
4
K
5
J,X
8
Z,Q
10
READ letter………………………………………………………………..1 MK
CASE letter of ……………………………………………………………1 MK
‘A’,’E’,’I’,’L’,’N’,’O’,’R’,’S’,’T’,’U’:marks=1;............................... ½ MK
‘D’,’G’:marks=2;……………...…………………………………..½ MK
‘B’,’C’,’M’,’P’:marks=3;…………………………………………..½ MK
‘F’,’H’,’V’,’W’,’Y’:marks=4;.......................................................½ MK
‘K’:marks=5; ……………………………………………………….½ MK
‘J’,’X’:marks=8; …………………………………………………….½ MK
‘Z’,’Q’:marks=10; …………………………………………………. ½ MK
ELSE
PRINT ”INVALID CHARACTER” ………………………………… ½ MK
END CASE
PRINT marks ………………………………………………………………..1MK
STOP………………………………………………………………………………….. ½ MK
START/STOP >1MK
INPUT > 1MK
CORRECT USE OF SELECTION(CASE) > 1MK
EACH CONDITION > ½ MK
OUTPUT > 1MK - Classify the following programming languages according to their category: (3mks)
Programming language
Category
HTML
Web scripting (½mk )
JAVA
OOP (½mk )
JAVASCRIPT
Web scripting (½mk )
PASCAL
3GL (½mk )
VISUAL BASIC
4GL (½mk )
LISP
5GL (½mk )
- With aid of a diagram, explain the “Repeat Until” construct as used in structured programming (2mks)
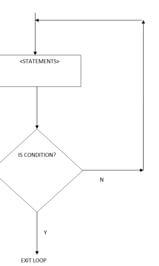
- the program first executes then tests the condition and continues looping until the condition turn to true
- The program tests and then executes until the condition becomes true
(diagram @1mk, correct explanation @ 1mk)
- Give two examples of syntax errors in programming. (2mks)
-
- State the stage in system development life cycle where each of the following activities are carried out:
- Identifying shortcomings of a system. (1mk)
- Problem definition (correct @1mk)
- Preparing the system migration plan (1mk)
- Implementation stage (1mk)
- Identifying the technologies that may be used in the proposed system. (1mk)
- system analysis(correct @1mk)
- Identifying shortcomings of a system. (1mk)
- State three roles of a programmer in system development life cycle. (3mks)
- Coding/writing code for the new program
- Turning system specification into an information system
- Modify existing programs to meet changes in information processing needs
- Installing a system
- Testing the new system
- Developing technical guide/documenting (first three @ 3mks)
- E-mail technology has become a very important part of today’s communication. Explain any three problems associated with using e-mail technology for communication. (6mks)
- Threat to privacy
- Messages can be sent to many people without their consent
- Email attachments can be sources of viruses
- Not available to all/technology illiteracy
- Emails can be unsolicited/spam mail
- Encourage illicit communication such as immoral behaviour (first 3 @2mks each)
- Sarafina wants to download her favourite movie from YouTube. State any three factors that may determine how long it will take her to complete the download. (3mks)
- Other activities that may be running in the computer
- Bandwidth of the media used
- Size of the video
- Other restrictions enforced in the computer
(first 3 @ 3mks)
- State the stage in system development life cycle where each of the following activities are carried out:
- The following Digital Club Member details were to be entered in a database: Name, Date of registration, Registration fee and Class.
- Prepare a suitable structure showing field names and their field types (4mks)
Field
Data type
Name
Text (✓1mk)
Date of registration
Date(✓1mk)
Registration fee
Currency or Number(✓1mk)
Class
Text(✓1mk)
- Name one other field that the Club Patron may need to add to uniquely identify the records (1mk)
Member Number (✓1mk) - Write the statement that can be used to select members of the class form 3 (2mks)
Name
Date of registration
Registration fee
Class
Criteria/ Expression
Form 3 (✓1mk)
- The following is an extract from a spreadsheet created to manage sales. Use it to answer the questions that follow.
A
B
C
D
1
ITEM NAME
UNIT PRICE
UNITS SOLD
2
HDD 300 GB
7,500
2
3
Optical Drive
4,500
8
4
DELL Latitude core i5
44,500
3
5
DDR4 8GB RAM
10,000
4
6
Lenovo Yoga Smart Tab
28,953
1
- Write a formula that will compute the number of items whose unit price whose price more than 10,000 (3mks)
=COUNTIF(B2:B6,”>10,000”) OR @COUNTIF(B2:B6,”>10,000”) OR +COUNTIF(B2:B6,”>10,000”)- (B2:B6) Argument range @1 mark
- (>10,000) Criteria @ 1 mark
- All Formula correct @ 1 mark
- If the formula =$B2*C$2 was placed in D2, state the output if copied to D3 (2mks)
- Formula is =$B3*C$2 @ 1 mark
- =4,500*2
- = 9,000 @ 1 mark
- Write the cell referencing used in c(ii) above (1mk)
- Mixed cell referencing
- Write the data type that is stored in cell C5 and A6 respectively (2mks)
- C5-Value
- A6- label
- Write a formula that will compute the number of items whose unit price whose price more than 10,000 (3mks)
- Prepare a suitable structure showing field names and their field types (4mks)
-
- Define the term attenuation as used in networking and data communication (1mk)
- It refers to the weakening of signal strength as it progressively moves from one point to another on the transmission media.
- The following are figures of networking cables. Identify each. (2 marks)
- Figure 1: Unshielded Twisted Pair (UTP)
- Figure 2: Shielded Twisted Pair (STP)
- Figure 3: Coaxial
- Figure 4: Fibre optic
(Each @ ½ mark)
-
- Give TWO examples of network software (2mks)
- Network operating system
- Network protocols
- In a network setup, list any TWO items that may be referred to as data terminal equipment. (2mks)
- Computer
- Printer
- Visual Display Unit
- Give TWO examples of network software (2mks)
- Explain the following terms as used in networking (4mks)
- Remote Communication
- It involves transmission of data signals between two communication devices located at different geographical location, through which people can be able to share ideas over network
- Distributed processing
- This involves the subdivision of a process into several subprocess then each subprocess can be processed at a different site co-currently hence speeding up the entire process
- Remote Communication
- State FOUR functions of a server in a network (4 marks)
- It allows sharing a network printer
- It allows communication between the various workstations in a network
- It provides control access to available storage devices in network
- It allows sharing of communication. Files in the network
- It provides the transfer of files from one workstation to another workstation in the network.
- Define the term attenuation as used in networking and data communication (1mk)
-
- Determine the binary equivalent of the octal number 253243. (2 marks)
- 0100101011010100011
- Carry out the following binary arithmetic using ones complement. In each case leave your answer in base 10.
- 1010-108 (5 marks)
Binary equivalents table
1010-1010Binary Bits
Decimal equivalent
000
0
001
1
010
2
011
3
100
4
101
5
110
6
111
7
1000
8
1001
9
1010
A
1011
B
108 - 001000
Make the digits of the values the same
001010
-001000
Complement the negative value
110111
Add the complemented value to the positive value
001010
+ 110111
(1)000001
Add the overflow digit to the LSD
000001
+ 1
Ans 0000102
Convert it to decimal
210 - 2BH-9H (6 marks)
- 2BH - 00101011
9H -1001
00101011
- 1001
Make the digits of the values the same
00101011
- 00001001
Complement the negative value
11110110
Add the complemented value to the positive value
00101011
+ 11110110
(1)0010000
Add the overflow to the LSD
001000102
Convert the answer to decimal
3410
- 2BH - 00101011
- 1010-108 (5 marks)
- Arrange the following numbers in ascending order. (2 marks)
1016, 1010, 158, 10112
1010, 10112, 158, 1016,
- Determine the binary equivalent of the octal number 253243. (2 marks)
Download Computer Studies Paper 1 Questions and Answers - Bunamfan Post Mock 2021 Exams.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

