INSTRUCTIONS TO CANDIDATES
- Answer all questions in section A
- In section B, answer question 16(compulsory) and any other three questions
- Candidates should check the question papers to ascertain that all the pages are printed as indicated and that no questions are missing
- Candidates should answer the questions in English
FOR EXAMINER’S USE ONLY
|
SECTION |
QUESTION |
CANDIDATE’S SCORE |
|
A |
1-15 |
|
|
B |
16 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
TOTAL SCORE |
|
|

QUESTIONS
SECTION A (40 Marks)
Answer all questions in this section
- Identify the computer generation that is associated with each of the following characteristics
- Use of computers that imitate human intelligence (1 mark)
- Used of punched cards for data input (1 mark)
- Use of Large Scale integrated circuits (1 mark)
- Use of cloud storage (1 mark)
- Distinguish between line spacing and character spacing as used in word processors (2 marks)
- Although super computers have greater processing capabilities than main frame computers, large communications companies prefer main frame computers for management of their data and operations State two reasons for this preference (2 marks)
- After purchasing a laptop, Mary realized that it could not connect to the internet through a wireless access point State three possible causes for the failure in connection (3 marks)
- Aisha found one of her favourite movies on a youtube channel State three advantages of downloading the movie to the computer hard disk and watching it from there instead of streaming it live from the youtube channel (3 marks)
- State two circumstances that necessitate encryption of data in computer systems (2 marks)
- A student saved a document in a memory card Later on the memory card crashed and therefore the work got lost State three precautions that the student should have taken to ensure that the work was not lost (3 marks)
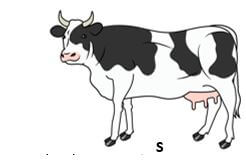
- Purity inserted a picture labelled S in a publication she designed as shown in the figure below
She applied different transformations to achieve the results labelled W, X and Y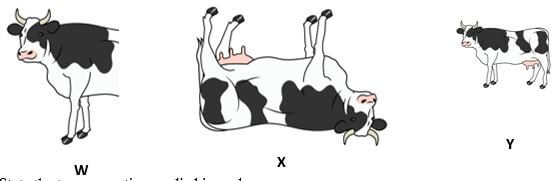
State the transformation applied in each case
W (1 mark)
X (1 mark)
Y (1 mark) - Kennedy inserted a flash disk in a computer to print out a document stored in it but the error message “USB not recognized” appeared on the screen of the computer State two possible causes of the error message (2 marks)
-
- Ben noticed that a USB mouse in one of the desktop computers in the computer lab could not move the pointer on the screen State two ways he could solve that problem (2 marks)
- Suzzie, a secretary at Achievers secondary school carries out her daily duties using computers and suffers repetitive strain injury State two ways she would use to reduce repetitive strain injury(2 marks)
- Sarah, a system analyst in Excel Company has decided to use document review in order to collect data necessary for developing a new information system for the company State three reasons that could have influenced her decision to use this method (3 marks)
- Explain two ways in which growth of the internet has contributed to an increase in computer crimes (2 marks)
- When constructing a school’s database, Mark set the data type “number” for the field “marks” Name three field properties that he can set for this data type in order to limit values entered in the field (3 marks)
- State two ways in which errors that occur during data processing are threat to data integrity (2 marks)
- Wireless Fidelity (WiFi) has become one of the most popular modes of internet connection in recent days State two reasons for this trend (2 marks)
SECTION B (60 Marks)
Answer question 16 (Compulsory) and any other three questions
-
- State three characteristics of third generation languages that distinguish them from all other high level programming languages (3 marks)
- Program documentation is categorized as either technical documentation or user –oriented documentation Classify each of the following documentation components as either technical or user oriented
- Program flowchart (1 mark)
- Error handling procedures (1 mark)
- Source code (1 mark)
- The figure below shows a flowchart Use it to answer the questions that follow:
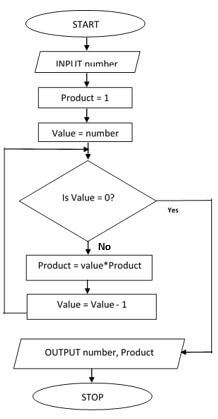
- Name the control structure used in the flowchart (1 mark)
- Determine all the outputs of the flowchart if the input is the number is five (3 marks)
- Write a pseudocode for the flowchart above (5 marks)
-
- The table below shows items extracted from Computer Studies subject score calculations spreadsheet Use it to answer questions (i) to (ii)
Using cell references only, write a function that may have been used to compute the following:A
B
C
D
1
Paper
Weight
Score
Weighted Score
2
Paper one
0.3
80
24
3
Paper two
0.4
70
28
4
Paper three
0.3
60
18
5
6
Average Weighted Score
22.66
- the weighted score in D3 (2 marks)
- Average weighted score in cell D6 (2 marks)
- Explain how social engineering is a threat to data security (2 marks)
- State the function of each of the following parts of a spreadsheet window
- Formula bar (1 mark)
- Name box (1 mark)
- State two functions of a select query in a database (2 marks)
- State two characteristics of command line operating systems that make them suitable for configuring computer networks (2 marks)
- When purchasing a word processing software, Atieno was advised to consider its user friendliness State three features that the software should have for her to conclude that it is user friendly: (3 marks)
- The table below shows items extracted from Computer Studies subject score calculations spreadsheet Use it to answer questions (i) to (ii)
-
- State two characteristics of open systems that make them better than closed systems (2 marks)
- State the function of each of the following during system construction:
- Programming language (1 mark)
- Invalid data (1 mark)
- Explain two reasons an organization may change an existing information system (4 marks)
- A school decided to change from a manual examination processing system to an online examination processing system using parallel change over strategy State three challenges they are likely to face when using this changeover strategy (3 marks)
- Peter was assigned the responsibility of designing the school magazine State two reasons why he would prefer to use DTP software and not a word processor (2 marks)
- The use of ICT has affected every aspect of human life either negatively or positively State two ways in which ICT has negatively affected the music industry (2 marks)
-
- A bank with many networked branches uses a data processing mode whereby each branch does its processing independently and then forwards the results to a central computer at the headquarters for final processing
- Identify this data processing mode (1 mark)
- State two advantages of this data processing mode (2 marks)
- State two reasons why accumulation of dust should be avoided in the computer lab (2 marks)
- For each of the following, identify the most appropriate internet service:
- Real time exchange of text messages (1 mark)
- Personal website for sharing personal opinions on a particular subject (1 mark)
- Enable people in different geographical locations to hold live meetings (1 mark)
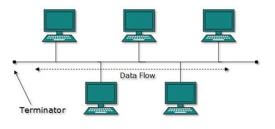
- Tom a network designer was tasked to set up a local area network for Mwangaza Technical institute He was provided with 4 computers, coaxial cables, 1 printer and 2 terminators With aid of a well labelled diagram, design the most appropriate network topology that could have been set up by Tom (3 marks)
- State two circumstances that may necessitate a network administrator to use a bridge in LAN (2 marks)
- Explain a reason why single mode fibre optic cable is preferred for long distance transmission of data signals (2 marks)
- A bank with many networked branches uses a data processing mode whereby each branch does its processing independently and then forwards the results to a central computer at the headquarters for final processing
-
- One of the characteristics of solid state drives (SSD) is the use of electronic circuits to store data Explain how binary logic is used to represent data in these devices (2 marks)
- Convert 170510 to its binary equivalent (3 marks)
- Using twos complements and 8 bit notation, perform the following subtraction:
2910 – 1510 (4 marks) - Perform the following binary arithmetic
11101011 – 100110 + 10100111
leave your answer in decimal notation (4 marks) - State two challenges associated with the use of voice input for securing computer systems (2 marks)

MARKING SCHEME
|
QN |
RESPONSES |
MARKS |
||||||||||||||||||||||
|
1. |
|
1 1 1 1 |
||||||||||||||||||||||
|
2. |
Line spacing refers to the vertical distance between lines of text while character spacing refers to the fixing of characters too close/condense or far apart/expanding from each other Accept correct illustration (Award 2 or 0) |
2 |
||||||||||||||||||||||
|
3. |
|
3 |
||||||||||||||||||||||
|
4. |
|
3 |
||||||||||||||||||||||
|
5. |
|
3 |
||||||||||||||||||||||
|
6. |
|
2 |
||||||||||||||||||||||
|
7. |
|
3 |
||||||||||||||||||||||
|
8. |
|
1 1 1 |
||||||||||||||||||||||
|
9. |
|
2 |
||||||||||||||||||||||
|
10. a) |
|
2 |
||||||||||||||||||||||
|
b) |
|
2 |
||||||||||||||||||||||
|
11. |
|
3 |
||||||||||||||||||||||
|
12. |
|
2 |
||||||||||||||||||||||
|
13. |
(Do not accept input mask, validation text, caption, indexed ) (First 3 × 1) |
3 |
||||||||||||||||||||||
|
14. |
Guide for marking: look out for whether a candidate relates errors to any of the measures of data integrity i.e. accuracy, completeness, relevance and timeliness. |
2 |
||||||||||||||||||||||
|
15. |
|
2 |
||||||||||||||||||||||
|
SECTION B (60 MARKS) |
||||||||||||||||||||||||
|
16.a) |
(Do not accept characteristics that are generic to all high level programming languages such as portable, easy to debug, user friendly etc.) (First 3 × 1) |
3 |
||||||||||||||||||||||
|
b) |
|
1 1 1 |
||||||||||||||||||||||
|
c) i) |
While Loop/Looping/repetition |
1 |
||||||||||||||||||||||
|
ii) |
1st Iteration number = 5, product = 1, Value = 5 Is 5 = 0 ? No Product = 5 * 1 = 5 Value = 5 – 1 = 4 2nd Iteration product = 5, Value = 4 Is 4 = 0 ? No Product = 4 * 5 = 20 Value = 4 – 1 = 3 3rd Iteration product = 20, Value = 3 Is 3 = 0 ? No Product = 20 * 3 = 60 Value = 3– 1 = 2 4th Iteration product = 60, Value = 2 Is 2 = 0 ? No Product = 60 * 2 = 120 Value = 2– 1 = 1 5th Iteration product = 120, Value = 1 Is 1 = 0 ? No Product = 120 * 1 = 120 Value = 1– 1 = 0 6th Iteration product = 120, Value = 0 Is 0 = 0 ? Yes Exit loop Product = 120 Number = 5 |
3 |
||||||||||||||||||||||
|
iii) |
START INPUT number ½ Product = 1 ½ Value = number ½ WHILE Value = 0 DO ½ Product = value * product ½ Value = Value – 1 ½ ENDWHILE ½ OUTPUT number, product ½ STOP Logic flow = 1 |
5 |
||||||||||||||||||||||
|
17. a) |
For each case, award 1 mark for correct function name & 1 mark for correct range |
2 2 |
||||||||||||||||||||||
|
b) |
Through social engineering computer criminals are able to solicit for private and confidential data such information system login details from unsuspecting persons which they use to get unauthorized access to data. |
2 |
||||||||||||||||||||||
|
c) |
|
1 1 |
||||||||||||||||||||||
|
d) |
|
2 |
||||||||||||||||||||||
|
e) |
|
|||||||||||||||||||||||
|
f) |
|
3 |
||||||||||||||||||||||
|
18. a) |
|
2 |
||||||||||||||||||||||
|
b) |
|
1 1 |
||||||||||||||||||||||
|
c) |
Award 1 mark for stating and 1 mark for explanation (First 2 × 2) |
4 |
||||||||||||||||||||||
|
d) |
|
3 |
||||||||||||||||||||||
|
e) |
|
2 |
||||||||||||||||||||||
|
f) |
|
2 |
||||||||||||||||||||||
|
19. a) |
|
1 |
||||||||||||||||||||||
|
ii) |
|
2 |
||||||||||||||||||||||
|
b) |
|
2 |
||||||||||||||||||||||
|
c) |
|
1 1 1 |
||||||||||||||||||||||
|
d) |
Evidence of a backbone/bus cable - 1 mark Two terminators on the ends of the backbone – 1 mark Nodes connected to the bus – 1 mark |
3 |
||||||||||||||||||||||
|
e) |
|
2 |
||||||||||||||||||||||
|
f) |
|
2 |
||||||||||||||||||||||
|
20. a) |
|
2 |
||||||||||||||||||||||
|
b) |
1710 = 100012 0.05 × 2 = 0.10 0.10 × 2 = 0.20 0.20 × 2 = 0.40 0.40 × 2 = 0.80 0.80 × 2 = 1.60 0.60 × 2 = 1.20 0.20 × 2 = 0.40 0.05 = 0. 0000112 so 17.05 = 10001.0000112 |
1 1 1 |
||||||||||||||||||||||
|
c) |
2910 = 101112 1510 =11112 8bit notation 00010111 00001111 00010111 – 00001111 Twos complements 11110000 + 1 = 11110001 00010111 + 11110001 = (1) 00001000 Ignore the overflow bit; 00001000 |
|||||||||||||||||||||||
|
d) |
11101.011 – 100.110 = 11000.101 11000.101 + 10100.111 = 101101.100 (1 × 25) + (0 × 24) + (1 × 23) +(1 × 22) + (0 × 21) + (1 × 20) + (1 × 2-1) + (0 × 2-2)+ (0 × 2-3) 32 + 8 + 4 + 1 + 0.5 = 45.5 |
1 1 1 1 |
||||||||||||||||||||||
|
e) |
|
Download Computer Studies Paper 1 Questions and Answers - MECS Pre Mock Exams 2023.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students