INSTRUCTIONS TO CANDIDATES
- Write your Name,Admission number and Stream in the spaces provided above
- Answer all questions in section A
- In section B,answer question 16(compulsory) and any other three questions
SECTION A (40 MARKS)
- Give importance of having the following in computer laboratory (3mks)
- Standard furniture in the laboratory.
- Antiglare screen
- UPS
- Distinguish between ROM and RAM (2mks)
- Explain the following computer crimes (2mks)
- Fraud
- Alteration
- Explain the following statements
- Firewalls (1mk)
- Data encryption (1mk)
- Differentiate between the following terms as used in word processing (3mks)
- Drop Cap and Case
- Superscript and subscript
- Indent and tab
- A school librarian asked you for an expert advice on the printer to use. She wanted to know the difference between impact and non-impact printers and TWO examples of each.
What would be your advice?
Difference. (2mk)
Examples - Describe the following terms as used in internet
- Webpage (1mk)
- Blog (1mk)
- Hyperlinks (1mk)
- Web portal (1mk)
-
- Give four advantages of DTP over a word processor (2mks)
- Differentiate between the following
- Kerning and tracking (2mk)
- Margins and column guides (2mks)
- Explain the term simulation (1mk)
- Differentiate between baseband and broadband signal as used in networking (2mks)
- Baseband signal
- Broadband signal
- Explain how the operating system controls the following resources (3mks)
- Processor
- Main memory
- Input and output devices
- What is deadlock in reference to operating systems (2mks)
-
- The most popular type of electronic data storage currently use magnetic disk storage such as hard disk or Winchester disk. Give two reasons as to why they are popular (2mks)
- Outline two advantages of hard disk over floppy disk (2mks)
- State two advantages of using a barcode reader for data entry at a point of sale terminal (2 marks)
- Explain two ways of protecting data and information against unauthorized access (2mks)
SECTION B (60 Marks)
Answer question 16 (Compulsory) and any other three questions -
- State any three differences between an Interpreter and a Complier (3mks)
- State the stage of program development in which (2mks)
- A flowchart would be drawn.
- The programmer would check whether the program does as required
- User guide would be written
- The requirement specification would be written
- Study the flowchart below and answer the questions that follow
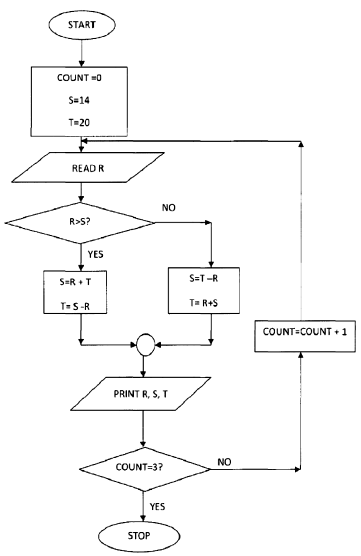
- What would be the output if the following values were input 40,20,15,1 (4mks)
- Write a pseudo code for the flowchart in question 16c) (6mks)
-
- Identify the following flow chart symbols (2 marks)

- State and explain three circumstances when observation method may be preferred during data collection in system development (6marks)
- State two ways of verifying data being entered into a computer system for processing (2 marks)
- A computer user entered the number 5.66894 and it displayed 5.66, He entered the number again for the second time and it displayed 5.67. State the types of errors that occurred in both instances. (2 marks)
- State three specifications that should be set in the print dialog box when printing a document (3 marks)
- Identify the following flow chart symbols (2 marks)
-
- Explain two ways in which hardware failure is a threat to data security (4 marks)
- A retailer uses a spreadsheet program to calculate profits. The figure below shows the spreadsheet
A B C D E F 1 Items Cost price Selling Price Profit Items sold Total Profit 2 Sugar 305 350 45 32 1440 3 Bread 100 120 20 45 900 4 Flour 200 220 20 32 640 5 Rice 107 130 23 89 2047 - Which row contains labels only? (1 mark)
- Write the formula that has been entered in:
Cell F2 (2 marks)
- State two disadvantages of the flat file database model (2 marks)
- State two reasons why table relationships are created during database design (2 marks)
- The principal of Molo Academy Boys keeps the following student details in a database: Name,
Address, Town, Date of birth, Marks scored, Fees paid- Name the most suitable primary key in the database. Give a reason for your answer (1 mark)
- For each item in the student details table above, indicate the most appropriate data type to be used in the database. (3
marks)
-
- What is Virtual reality (2mks)
- Explain the following interactive equipment used in virtual reality (2mks)
- Head gear
- Body suit
-
- What is Artificial Intelligence? (2mks)
- Explain three components of an experts system (6mks)
- Most computerized security systems make use of Biometric analysis ,name three physical features of human beings that can be considered in this analysis (3mks)
-
- A computer technician found it necessary to disable a firewall when working on a computer system connected to a computer network. State two reasons that may have necessitated disabling of the firewall(2 marks)
- State two differences between infrared transmission and Bluetooth transmission (2 marks)
The diagram below shows four common network topologies A, B, C and D.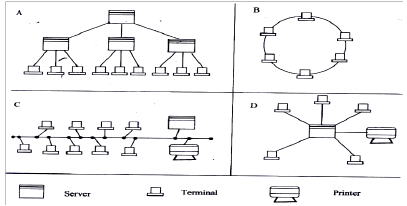
-
- Name the network topologies labeled A, B, C and D. (4marks) A……………………………………………………………………………………………
B……………………………………………………………………………………………
C……………………………………………………………………………………………
D…………………………………………………………………………………………… - State the role of the device labeled “server” in topology A (1 mark)
- State two problems associated with network topology B. (2 marks)
- Name the network topologies labeled A, B, C and D. (4marks) A……………………………………………………………………………………………
- Explain why the single mode fiber optic cable is preferred for long distance transmission (2marks)
- State two ways a networking operating system provides data security in a network (2marks)

MARKING SCHEME
- Give importance of having the following in computer laboratory (3mks)
- Standard furniture in the laboratory.
To avoid poor posture during machine use this may lead to strain, injury and limb fatigue - Antiglare screen
To avoid eye strain and fatigue caused by over bright cathode ray tube monitors (CRT) - UPS
- Temporary power supply to the computer to allow the user to save the work (power back up)
- Stabilize power (clean unstable power supplied from the main source to clean stable voltage)
- Standard furniture in the laboratory.
- Distinguish between ROM and RAM (2mks)
- Data and instruction stored in Rom are those required to remain unchanged for long period of time
- RAM (Random Access Memory )its content can can be read directly regardless of the sequence in which it is stored.
- Its content is held temporarily and content lost,is lost once the computer is turned off.
- Explain the following computer crimes (2mks)
- Fraud-Use of computer to conceal information or cheating other people with the aim of getting money (1x1=1mk)
- Alteration-Changing the data or information without permission with aim of mis informing others(1x1=1mk)
- Explain the following statements
- Firewalls-
- Is a program or hardware or a combination of both that filters the information of both that filters the information coming through the internet into a computer
OR - it is a program that filters the information coming through the internet into a computer (1mk)
- Is a program or hardware or a combination of both that filters the information of both that filters the information coming through the internet into a computer
- Data encryption (1mk)
- It is the ecoding of data during storage or transmission so that it cannot be understood by those who do not have encryption key.
- The word scrambling can be used in palce of encoding or
- Software or device that filters data between different networks by enforcing the host network access control policy
- Firewalls-
- Differentiate between the following terms as used in word processing (3mks)
- Drop cap is a large character at the start of paragraph that occupies more than one line downwards while text case is capitalization of text(you can switch from either lower or uppercase)
- A superscript appears just above the rest of the characters while subscript appears just below other characters .
- An indent is a white space at the beginning of each line while tabs are used to add uniform spacing in the line of text
follows.
- A computer novice came to you for expert advice on the best printer to use.He wanted to know the difference between impact and non impact printers and TWO examples of each.
What would be your advice? (3mks)
Impact printer,the printing head element comes into physical contact with the stationery.An inked ribbon placed between the printing head element creates the imprints when the printing head strikes while in non impact,the printing head element does not come into contact with the stationery,but by other means like thermal and electrostatic.Diffrence in printing speed,number of copies produced,cost of technology,noise when printing is acceptable: impact e.g dot matrix,daisy wheel,golf ball,drum,chain;non impact e.g thermal, inkjet, electrostatic,laser,,xerographic. - Describe the following terms as used in internet
- Webpage-A page in a website (1mk)
- Blog-A website which enables one to post or submit his or her personal details to a website ;so that the details can be accessed from the wesite (1mk)
- Hyperlinks -text or graphic which opens another wepage or website when chicked (1mk)
- Web portal-a website that function as a point of access to information on the world Wide Web (1mk)
-
- DTP-Has several design templates for various publications
- Is more powerful in manipulating graphics /texts
- Enables formatting and manipulation of individual text and frames separately
- Enables complex documents format printing
- Differentiate between the following
- Kerning –fixing visual denseness of pairs of characters in text Tracking-Spacing between characters in text
- Margins-Space around the text in the four edges of a documents Column guides-Non printable guides for column layout
- DTP-Has several design templates for various publications
- Explain the term simulation (1mk)
Process of creating a model of a real object, concept in order to experiment the behavior of a real object - Differentiate between baseband and broadband signal as used in networking (2mks)
- Baseband signal-Digital signal transmitted through a digital channel without modulation (1mk)
- Broadband signal-A group of analog signals transmitted through a common channel but with varying signal frequency (1mk)
- Explain how the operating system controls the following resources (3mks)
- Processor-the O.S assigns tasks one by one to avoid competition
- Main memory- the OS determines which task should occupy the main memory at any given time.
- Input and output devices-the OS controls data input and information output
- What is deadlock in reference to operating systems (1mk)
Is a situation that results when several tasks complete for a resources which is held and not being released for use by another task. -
- A magnetic disk is a direct access storage media (DASD)that permits the computer to find data directly on the disk.
- Hard disk provides greater storage capacity than the floppy disk (1mk)
- The following numbers was entered by acomputer user into a system 5.66894 and the first time it displayed 5.66 on the screen,he entered it again and it displayed 5.67;explain the type of errors that occurred during data processing (2mks)
The first time it was trunctation error which results from having a real number that has along fraction part which cannot fit in the allocated memory space while the second time it was rounding error which results from raising or lowering a digit in a real number to the required number. - Explain two ways of protecting data and information against unauthorized access (2mks)
- Password protection-A password to open or exit the database file i.e lets any user who wishes to do any action (2mks)
- Data encryption –If the database is to be sent electronically encryption secures the data from un authorixzed access
- User and group permission to users on data base object such as queries form and reports
- User level security-This features is used to assign permission to users in order to limit user access to certain databse object
-
- State any three differences between an Interpreter and a Complier (3mks)
Compiler Interpreter It translates the entire source code into the object code equivalent It translates the source code statement at a time to its equivalent source code Its object code is stored therefore the execution is fast The object code is not stored ,so each time an execution has to take place it has to b e translated thus the execution is slower. since the object code is stored ,it occupies a lot of storage spaces It does not require a lot of storage space since the object code is not stored. - State the stage of program development in which (2mks)
- A flowchart would be drawn.
In design stage - The programmer would check whether the program does as required
Program testing and debugging - User guide would be written
Documentation - The requirement specification would be written
Analysis
- A flowchart would be drawn.
- Study the flowchart below and answer the questions that follow
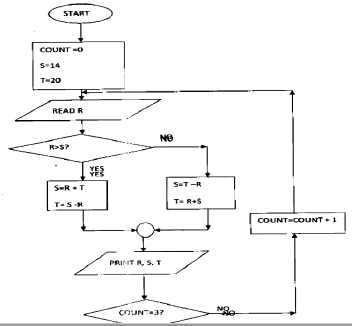
- What would be the output if the following values were input 40,20,15,1 (2mks)
Award ½ mark for each correct row max 2 marksCOUNT R S T 0 40 14 20 1 20 60 20 2 15 0 20 3 1 19 20 - Write a pseudo code for the flowchart in question 16c) (8mks) (iii)
- START - AWARD MARKS AS FOLLOWS
COUNT =0 START /STOP@ ½ MARK each max
S=14 1mark
T=20 Initialization @ 1mark
REPEAT Loop @ 1mark
READ R input @ 1 mark
IF R˃S THEN SELECTION @ 1 MARK
S=R+T iNcrement @ 1 mark
T=R-S Output @1 mark
ELSE Logic @ 1 mark
S=T-R
T=R+S
PRINT R,S,T
STOP
COUNT =COUNT +1
UNTI COUNT =3
STOP
- What would be the output if the following values were input 40,20,15,1 (2mks)
- State any three differences between an Interpreter and a Complier (3mks)
-
- Report (First 2 × 1) 1
Disk master file/database 1 -
- When the data to be collected is too technical to explain in words or writing
- When first hand information is required
- When the system analyst wants to increase the reliability of the information obtained (First 3 × 2)
- Double checking/ Double entry – this is entering the data twice and comparing the two copies
Proofing- This involves someone checking the data entered against the original document (First 2 × 1) - First instance – truncation error 1
Second instance – round off error 1 -
- Number of copies
- Printer name
- Paper size
- Page range (First 3 × 1)
- Report (First 2 × 1) 1
-
- Data loss due to total system failure e.g. HD crash;
The experts called upon to repair can access critical/ valuable information;
Data recovery software may be used to make unauthorized backups
(First 2 × 1) -
- Row 1 or 1 1
- =D2*F2 or = PRODUCT(D2,F2) Nomarkifnoequalsign 2
- Unnecessary data duplication Data inconsistencies
Data retrieval is slow (First 2 × 1) -
- To reduce data duplication
- To enable querying of multiple tables (First 2 × 1)
-
- No suitable primary key.
- Reason: none of the field is unique ½
½
Name – text Address – Memo Town – Text
Date of birth – Date/time Marks Scored – number Fees paid – currency
6 correct data types @ ½ mark
- Data loss due to total system failure e.g. HD crash;
-
- What is Virtual reality
A condition in which a person becomes psychologically immersed in a artificial environment generated by a computer (2x1=2 - Explain the following interactive equipment used in virtual reality (2mks)
- Head gear
Advice with tiny screens worn on the head, enable the wearer to view the virtual world. - Body suit
- Head gear
-
- Worn by the user,enable the wearer to explorer the virtual world (c )(i) What is Artificial Intelligence?
Science of designing machines that mimic the intelligence of a human (2x1=2 - Explain three components of an experts system
- User interface-set of software that link computer expert system and its user
- Knowledge base-A database of knowledge of an expert system
- Interference engine-software that applies the rules from a knowledge base to the data provided by the user to draw conclusion (3x2=6)
- Worn by the user,enable the wearer to explorer the virtual world (c )(i) What is Artificial Intelligence?
- Most computerized security systems make use of Biometric analysis ,name three physical features of human beings that can be considered in this analysis (3mks)
- Finger prints
- Voice recognition
- Eye/facial recognition
- What is Virtual reality
-
-
- the firewall may have been blocking the installation of software
- To allow sharing of information/software in the network (First 2 × 1)
- Infrared transmission uses line of sight while Bluetooth transmission is omni–directional
Bluetooth can penetrate barriers while infrared transmission cannot penetrate barriers (First 2 × 1) -
- A – hierarchical/tree topology B – Ring topology
C – Bus topology
D - Star 1 - Controls and coordinates activities in the network/service requests from clients 1
-
- Failure of one node will bring down the entire network
- It is difficult troubleshoot the network
- Adding or removing a node disrupts the entire network (First 2 × 1)
- A – hierarchical/tree topology B – Ring topology
- It allows light to travel in only one direction leading to faster transmission speeds (First 1 × 2)
- Enables creating of user access levels/user accounts Enable creation of passwords
Data encryption
Use of log files (First 2 × 1)
-
Download Computer Studies Paper 1 Questions and Answers - Momaliche Joint Mock Exams 2021/2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students

