COMPUTER STUDIES (Theory)
PAPER 1
INSTRUCTIONS TO CANDIDATES
- Write your name and Admission number in the spaces provided above
- Answer all questions in section A
- In section B, answer question 16(compulsory) and any other three questions
- Candidates should answer the questions in English.
SECTION A (40 Marks)
Answer all questions in this section
- Name the storage device that was introduced in each of the following computer generations
- Second Generation (1 mark)
- Third Generation (1 mark)
- Fourth generation (1 mark)
- Fifth generation (1 mark)
- Mr. Tom, a games teacher at Tatu secondary school wants to invite several schools for basketball tournament. He was advised to use mail merging technique to create invitation letters for the respective schools to be invited. State two advantages of using this technique to create the letters. (2 marks)
- Susan came across the following examples of software while revising for her computer studies exam: Linux, Quickbooks, Lotus wordpro, Windows 7,
Classify each as either system software or application software. (2 marks)
Linux……………………………………………………………………..
Quickbooks……………………………………………………………….
Lotus wordpro……………………………………………………………
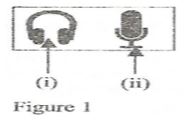
Windows 7………………………………………………………………. - Figure 1 below shows symbols of ports in a computer system. Identify the peripheral device that is connected to each of them.
- Distinguish between main memory and secondary memory as used in computers (2 marks)
Five star hotel has decided to pay its suppliers using electronic payment method. State two benefits the hotel will benefit from making this decision. (2 marks) - Annet would like to develop system documentation that will assist users when learning how to use her system. State four contents that such documentation should have. (4 marks)
- State a circumstance under which the following features could be applied to a publication
- Text wrapping (1 mark)
- Object grouping (1 mark)
- Kennedy would like to edit a document prepared using word processing program. Name four editing keyboard keys that he could use to achieve his objective. (2 marks)
-
- State two ways an inserted formula can be applied to other cells in a spreadsheet (2 marks)
- Suzzie, a secretary at Achievers secondary school carries out her daily duties using computers and suffers wrist strain. State two ways she would use to reduce wrist strain. (2 marks)
- Sarah noticed that after copying a video file in her flash disk from a cyber café in town, the video file self-replicated in the flash disk filling all the available memory space.
- State one possible cause for such occurrence (1 mark)
- State two ways that can be used to prevent the occurrence of such incidences (2 marks)
- Kirundi Secondary school would like to introduce the use of internet in the school’s computer lab. Explain three security issues that the students are likely to be exposed to. (2 marks)
-
- State two characteristics of a primary key field in a database system (2 marks)
- State one advantage of the auto save feature in a word processing program (1 mark)
- State two advantages of using random file organization method in storage devices. (2 marks)
- Wireless Fidelity (WiFi) has become one of the most popular modes of internet connection in recent days. State two reasons for this trend. (2 marks)
- Explain a reason why bcc option could be used when sending an email (2 marks)
SECTION B (60 Marks)
Answer question 16 (Compulsory) and any other three questions
-
- Andrew would like to develop a system using a programming language. State three factors he should consider when selecting the appropriate language (3 marks)
- State the meaning of the following terms as used in programming:
- Interpreter (1 mark)
- Editor window (1 mark)
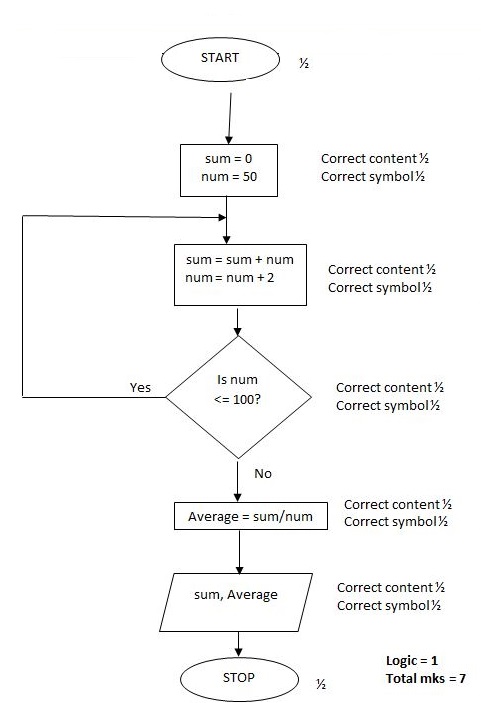
- Dennis designed the pseudo code below for a program that would be used for calculating the sum and average of all even numbers between 50 and 100 and display the results.
START
Set sum to 0
FOR num = 0 to 100 DO
num = num + 1
Sum = num + sum
Average = sum/count
END
PRINT Sum, Average
STOP- After carrying out a dry run of the pseudocode, Dennis found out errors in it. Identify three logical errors that he might have found. (3 marks)
- Draw a flowchart for a corrected version of the pseudo code in part (i) above (7 marks)
-
- The table below shows items extracted from David’s retail shop spreadsheet. Use it to answer questions (i) to (ii)
A B C D 1 Item Unit Price Quantity Total Cost 2 Bread 60 10 3 Milk 50 15 4 Matchbox 20 10 5 Tooth paste 120 10 6 Total amount - Using cell references only, write a function that would be used to calculate the total cost of milk (2 marks)
- Using a cell references only, write a formula that would be used to calculate the total amount spent on all items. (2 marks)
- Distinguish between hacking and cracking as used in computer security (2 marks)
- State the function of each of the following parts of a spreadsheet window
- Formula bar (1 mark)
- Name box (1 mark)
- State the circumstance under which OLE object data type is suitable when designing a table in a database (1 mark)
- Explain the function of a flowchart in system design (2 marks)
- Distinguish between multi user operating system and multi-tasking operating system (2 marks)
- When purchasing a printer, Atieno was advised to consider its compatibility and that it should be plug and play. State the meaning of these two terms:
- Compatibility (1 mark)
- Plug and play (1 mark)
- The table below shows items extracted from David’s retail shop spreadsheet. Use it to answer questions (i) to (ii)
-
- Explain one challenge likely to be experienced in a closed system (1 mark)
- Every organization requires an information system
- Define an information system (1 mark)
- Explain two reasons an organization may change an existing information system (4 marks)
- Testing systems after construction is a very critical process in systems development. State three areas an effective testing should cover. (3 marks)
- Using suitable examples, distinguish between layout based DTP software and graphical based DTP software. (3 marks)
- The use of ICT has affected every aspect of human life. State three ways ICT in which ICT can be used to enhance physical fitness of the members of the society. (3 marks)
-
- Distinguish between freeware and open source software (2 marks)
- Describe how operating systems handle the following in a computer system
- Errors (1 mark)
- Interrupts (1 mark)
- State the purpose of the following in a computer
- Cache Memory (1 mark)
- System clock (1 mark)
- Motherboard (1 mark)
- Mark, an employee of an institution used his computer to access his boss’s computer to get some confidential information and gave it to one of its clients at a fee.
- State the type of crime committed by Mark (1 mark)
- State two ways of protecting data against the crime committed by Mark (2 marks)
- Using two’s complements, perform the calculation 4110 - 1510 leaving your answer in decimal notation (5 marks)
-
- Identify four data collection methods that may be used in data processing cycle (2 marks)
- State three benefits of using time sharing data processing mode in a leaning institution (3 marks)
- Differentiate between webmaster and web designer (2 marks)
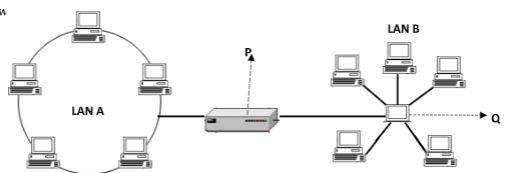
- The network set up below is formed by combining two LANs. Use it to answer the questions (i) – (v) below.
- Identify the network devices labelled:
P ………………………………………………………. (1 mark)
Q……………………………………………………….. (1 mark) - State the importance of device P in the network (1 mark)
- What is the name given to the combined topology in the figure above (1 mark)
- Identify the network topology A and B
P ………………………………………………………. (1 mark)
Q……………………………………………………….. (1 mark) - State two problems a network administrator may encounter in management of LAN A (2 marks)
- Identify the network devices labelled:
MARKING SCHEME
-
- Magnetic tapes/magnetic core
- Magnetic disks/floppy disks
- Optical disks/hard disks
- Solid state devices/hard disks/ cloud storage
-
- It a fast method of creating the letters without copying and pasting/saves time
- The recipient list can be re used
- Ensures consistency/uniformity of letters generated (First 2 × 1)
-
- System software
- Application software
- Application software
- System software
-
- Speakers/earphone/headphones
- Microphone
-
- Main memory stores data temporarily while secondary memory stores data permanently (for back up)
- Data in main memory is directly accessible by the CPU while data in secondary memory must go through main memory in order to be accessed by the CPU
- Main memory usually has lower storage capacities while secondary memory has higher storage capacities
(Any correct difference, Award 2 or 0)
-
- Minimizes security risks associated with handling cash money
- Transactions can be done conveniently at any time of the day or night
- Faster in making payment
- Saves processing costs e.g. travelling, labour etc. (First 2 × 1)
-
- How to load and exit the system
- How to perform tasks in the system
- Error handling procedures
- How to install the system
- Minimum software and hardware requirements (First 4 × 1)
-
- When you want to determine how text will behave around a graphic
- When you want to put several objects as one block
-
- Arrow keys
- Page up
- Page down
- Home key
- End key
- Insert key
- Delete key
- Backspace (First 4 × ½ )
Accept correct symbol
-
-
- By copying and pasting
- Use of the auto fill command (First 2 × 1)
-
- Use of wrist rest pad
- Taking frequent breaks
- Use of ergonomic keyboard (First 2 × 1)
-
-
-
- Worm virus attack/virus attack
-
- Avoid using flash disks on infected computers
- Scan storage devices for viruses using updated antivirus software
- Scan any file for viruses before downloading or copying them to the storage device (First 2 × 1)
-
-
- Spread of viruses
- Recruitment/exposure to terrorist gangs/drug trafficking
- Cyber bullying
- Fraud
- Hacking (First 3 × 1)
-
-
- It is unique/does not allow duplicates
- Cannot be empty/null (First 2 × 1)
- Prevents data loss in case of abrupt power loss or disruption
-
-
- Data access is fast
- Faster to update data since no need of sorting
- Records can be of different sizes (First 2 × 1)
-
-
- Covers a wide geographical area
- Allows users to roam without losing access to the network
- It is easy to remove or add nodes
- Enables communication where laying of cables is not feasible (First 2 × 1)
- When the sender does not want the recipients of an email to know other persons who received the similar mail.
-
-
-
- The availability of the relevant translator
- Whether the programmer is familiar with the language/ level of skill of the programmer
- Ease of learning and use
- Purpose of the program, i.e., application areas such as education, business, scientific, etc.
- Execution time/speed
- Development time (First 3 × 1)
-
- Interpreter is a language translator that converts each line of a high level programming code to machine code
- Editor window is an interface in a language translator where a programmer enters the source code.
-
-
- The range starts from 0 to 100 instead of 50 to 100
- Increment is num = num + 1 instead of num = num + 2
- The variable count is not assigned to the total count of numbers entered i.e. count =num
- The computation of average should be outside the loop
NB: omission of ENDFOR is a syntax error!
-
-
-
-
-
- =PRODUCT(B3,C3)
- = SUM(D2:D5) or
=D2+D3+D4+D5
- Hacking refers to gaining unauthorized access to a computer system by breaking codes or passwords while cracking is the gaining unauthorized access to a computer system by trying out to identify weak access points in the system
(award 2 or 0) -
- Formula bar displays whatever is entered in the active cell
- Name box shows the cell address of the active cell or range
- It is used when the type of data in the field is an image or graphic
- Used to depict the overall functionality of a system in a diagrammatic form
- Multi user o/s allow more than one users to access system resources apparently at the same time while multi-tasking o/s allow a single CPU to process more than one tasks apparently at the same time (award 2 or 0)
-
- Ability of the printer to fit and work harmoniously with existing hardware
- Ability of the printer to be automatically detected, installed and be ready to use by the operating system.
-
-
- They degrade fast and become obsolete since they do not redefine to match the changes in the environment
-
- An information system is the arrangement of people, data, processes and information that work together to support and improve the day-today operations of a business
-
- New opportunities: - a chance to improve the quality of internal processes and service delivery in the organization may arise. Invention of new systems which are more successful than the existing ones
- Problems: - these are undesirable circumstances that prevent the organization from achieving its goals
- Directive: - these are new requirements imposed by the management, government, or external influences.
- Change in technology
- Change is user needs (First 2 × 2)
-
- Extreme data: this is data of the right data type but in the lower or upper boundary of the expected values
- Normal data (valid data): this is data that the program should accept. It is data within the required range
- Abnormal data (invalid data): this is data that is out of the range. it is data that the program should not accept
- Layout based DTP is DTP software that enables the user to design pages of a publication based on different layout designs e.g. Ms Publisher, pagemaker, Indesign while graphic based DTP enable one to edit and format objects such as pictures, images, etc. e.g. photoshop, CorelDraw
-
- Download videos on the internet which are used to guide exercises
- Used to design automated computerized equipment used in exercising e.g. robots in gyms, simulation of running fields
- Use of the internet to research on physical fitness strategies
- Use of social media, blogs, videos etc. to create awareness/mobilization on the benefits of physical fitness (First 3 × 1)
-
- Freeware refers to software that is made freely available to the user while open source is software whose source code is freely made available to users
-
- The o/s alerts the user of errors that may arise out of illegal operations, hardware or software failure. It may also make suggestions of possible solutions to the problem
- A critical request causes the processor to stop executing the current process to attend to it, before returning to the process that had been interrupted
-
- Enhance performance of the microprocessor by providing fast speed retrieval of data
- Regulates timing and speed of all computer functions
- Enables communication between the computer’s internal components (components in the system unit)/where all internal components are mounted
-
- Fraud
-
- Motivate workers
- Use of passwords/user access levels/user accounts
- Use of log files
- Physical restrictions (First 2 × 1)
-
2 41 2 20R1 2 10R0 2 5R0 2 2R1 2 1R0 2 0R1
2 15 2 7R1 2 3R1 2 1R1 2 0R1
4110 = 1010012
1510 =11112
41 – 15 = 101001 – 1111
= 101001 - 001111
1C’s of 001111 is 110000
2C’s is 110001
101001 + 110001 = (1)011010 ; ignore the overflow bit 011010
Convert 011010 to decimal notation
(0 × 25) + (1 × 24) + (1 × 23) +(0 × 22) + (1 × 21) + (0 × 20)
0 + 16 + 8 + 0 + 2 + 0 = 26
-
-
- Observation
- Questionnaires
- Interviews
- Document review/study of available documents
- Direct data capture (First 4 × ½ )
-
- Users are able to interact through terminals
- File update/trouble shooting is easy since it is done at the central computer
- Easy control through the central computer
- File enquiry is possible (First 3 × 1)
- A webmaster oversees/supervises the daily activities/maintenance and operations of a website while web designer creatively designs and codes websites
-
- P - Bridge
- Q – Switch/ hub
-
-
- Interconnects two segments of a network/divides a large network into segments
- Reduces traffic congestion in the network
- Hybrid topology/tree topology
-
- A – Ring topology
- B – Star topology
-
- Lack of a focal point making troubleshooting difficult
- Modification will be difficult since removing one node may affect the entire network (First 2 × 1)
-
-
Download Computer Studies Paper 1 Questions and Answers - MECS Cluster Joint Mock Exams 2021/2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students