INSTRUCTIONS
- Answer all questions in section A
- In section B, answer question 16(compulsory) and any other three questions
- Candidates should answer the questions in English.

QUESTIONS
SECTION A (40 Marks)
Answer all questions in this section
- State three precautions that should be taken to prevent against electrical fire in the computer laboratory (3 marks)
- Identify the most appropriate input device suitable for each of the following tasks:
- Graphic designs and architectural drawing (1 mark)
- Data input by a person with impaired hands (1 mark)
- Sharon has noticed that her stand-alone computer has become unusually slow and hanging frequently. Since she cannot figure out the problem with the computer, she decided to format the hard disk.
- State two data recovery measures she has to take before formatting the hard disk (2 marks)
- State two corrective measures she should have taken before resorting to formatting the hard disk
(2 marks)
- The capacity of a computer’s RAM is 4GB
- State one function of the RAM in the computer (1 mark)
- Calculate the number of nibbles the memory can support if another RAM of 512MB RAM was added. (3 marks)
- The independent Electoral and Boundaries Commission (IEBC) has decided to transmit election results from the constituency level to the headquarters in Nairobi through the internet. Explain two data security threats that are likely to be faced during this transmission. (4 marks)
- The icons below represent commands used in a DTP package to manipulate graphics.
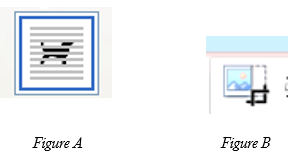
State the use of each of the icons labeled Figure A and Figure B (2 marks) - Explain the importance of each of the following in word processing
- tab stops (2 marks)
- word wrap (2 marks)
- State the use of each of the following symbols in a system flowchart:
- (1 mark)
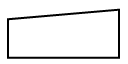
- (1 mark)

- (1 mark)
- State two ways in which power failure is a threat to data security (2 marks)
- Pesa Tele Company has realized that someone is illegally gaining access to their data in their computer networks. Name two computer professionals that the company should consult and their roles. (2 marks)
- State two factors that determine the cost of an operating system (2 marks)
- The examination processing system of Mamboleo high school requires entry of students’ monthly CAT marks at the end of each month. At the end of the term, the system generates a student’s termly report form.
- Name this type of data processing mode (1 mark)
- State two advantages of this data processing approach (2 marks)
- An organization has offices in Nairobi and Kampala. The management intends to network the computers in these offices. State two factors that they need to consider when choosing a physical network topology to use. (2 marks)
- Apart from sending and receiving mails, state other two functions of an email. (2 marks)
- Distinguish between an index key and a primary key field as used in databases (2 marks)
SECTION B (60 Marks)
Answer question 16 (Compulsory) and any other three questions
-
- Using a suitable example, explain the term mnemonics as used in programming (2 marks)
- An interpreter is a programming language translator that converts high level languages to machine code. State three characteristics of an interpreter (3 marks)
- The figure below shows a flowchart. Use it to answer the questions that follow:
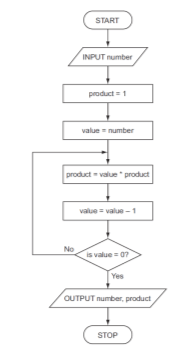
- Determine all the outputs of the flowchart if the input is the number three. (3 marks)
- Explain what happens if the number zero is input. (1 mark)
- Write a pseudocode for the flowchart above (6 marks)
-
- With an aid of a diagram, describe time sharing mode as used in data processing. (4 marks)
- Explain the function of each of the following in system documentation:
- User Manual (2 marks)
- Invalid data (2 marks)
- State two functions that are specific to networking operating systems (2 marks)
- Mwanzo mpya holding is a company that deals with selling of computers and computer parts. State three benefits of advertising their business through the internet. (3 marks)
- Distinguish between the integrated software and software suite (2 marks)
-
- Perform the binary arithmetic
111.01 + 1011.111 – 101.011
And convert the answer to decimal notation (4 marks) - Using two’s complements and 8 bit notation, subtract 1110 from 810 leaving your answer in binary notation (5 marks)
- The figure below is an extract of a spreadsheet showing what students had targeted to score and the actual score in a computer remedial class.
A
B
C
D
1
NAME
TARGET SCORE
ACTUAL SCORE
PERFORMANCE FACTOR
2
Abdi
40
45
3
Alex
30
65
4
Ben
50
60
5
Betty
30
20
6
Bena
45
45
7
Sheila
70
60
A performance factor is obtained by subtracting the target score from the actual score and dividing the difference by the target score.
Using cell references, write a formula that would be entered in cell- D4 to compute the performance factor (2 marks)
- E2 to display the statement ‘More remedials’ if the performance factor is less than zero, ‘Exempted’ if the factor is greater than zero and ‘optional remedials’ if otherwise. (4 marks)
- Perform the binary arithmetic
-
- Kenya Wildlife Service (KWS) is a government agency whose part of their responsibility is to conserve wildlife. State three ways they can use ICT to achieve their goal. (3 marks)
- State the role of each of the following data communication devices:
- Gateway (1 mark)
- Brouter (1 mark)
- Codec (1 mark)
- Explain two circumstances under which phased changeover strategy would be preferred when implementing a new system. (4 marks)
- State three reasons why the fibre optic cable has become a very popular data communication media in most organizations today (3 marks)
- A local bank had its electronic money transfer system attacked by a computer criminal. In their meeting over the matter, the Board of Directors instructed the CEO not to report the matter to the law enforcement agencies but to deal with it internally. State two reasons why the board of directors took such a decision. (2 marks)
-
- An architectural firm uses a computer system for designing building plans. State three advantages of using CAD software instead of DTP software to perform this function. (3 marks)
- State three reasons why it is necessary to create table relationships during database design (3marks)
- Explain two circumstances under which the use of robots may be preferred in manufacturing industries (4 marks)
- The growth of the internet has led to the rise of many social networking sites. State three negative impacts of these social networking services offered over the internet. (3 marks)
- A student was advised to use ergonomic keyboard while typing his project documentation. State two health problems that can be solved when the advice is taken. (2 marks)

MARKING SCHEME
|
SECTION A (40 marks) |
|
|||||||||||||||||||||||||
|
QN |
RESPONSES |
MARKS |
||||||||||||||||||||||||
|
1. |
|
3 |
||||||||||||||||||||||||
|
2. |
|
1 |
||||||||||||||||||||||||
|
1 |
|||||||||||||||||||||||||
|
3. |
|
2 |
||||||||||||||||||||||||
|
2 |
|||||||||||||||||||||||||
|
4. |
|
2 |
||||||||||||||||||||||||
|
512 MB = 512 000 000 bytes 4GB = 4 000 000 000 bytes ; Total RAM capacity = 4 512 000 000 bytes 1 byte = 8 bits 4512 000 000 bytes = ? bits = 36096000000 bits 1 nibble = 4 bits ? nibbles = 36096000000 bits ; 36096000000 ÷ 4 = 9 024 000 000 nibbles |
1 1 1 |
|||||||||||||||||||||||||
|
5. |
|
2 |
||||||||||||||||||||||||
|
6. |
Figure A – for text wrapping/ placing image behind text Figure B – for cropping/hiding unwanted parts of an image/trimming/cutting |
1 1 |
||||||||||||||||||||||||
|
7. |
2 2 |
|||||||||||||||||||||||||
|
8. |
|
1 1 |
||||||||||||||||||||||||
|
9. |
|
2 |
||||||||||||||||||||||||
|
10. |
( First 2 × 1) |
2 |
||||||||||||||||||||||||
|
11. |
|
2 |
||||||||||||||||||||||||
|
12. |
- It is simple to develop ( First 2 × 1) |
1 2 |
||||||||||||||||||||||||
|
13. |
|
2 |
||||||||||||||||||||||||
|
14. |
|
2 |
||||||||||||||||||||||||
|
15. |
An index key is a field that is used to speed up access of data in a database while a primary key is a field that uniquely indentifies each record in a database |
2 |
||||||||||||||||||||||||
|
SECTION B (60 Marks) |
||||||||||||||||||||||||||
|
16. a) |
Award 1 mark for correct explanation and 1 mark for suitable example |
2 |
||||||||||||||||||||||||
|
b) |
|
3 |
||||||||||||||||||||||||
|
c) i) |
Award 1 mark for each correct iteration (3 × 1) |
|||||||||||||||||||||||||
|
ii) |
The loop is executed infinitely many times |
1 |
||||||||||||||||||||||||
|
iii) |
Start √ ½ Input number √ ½ Product =1 √ ½ Value =number √ ½ REPEAT √ 1 Product = Value * Product √ ½ Value = Value- 1 √ ½ UNTIL Value = 0 √ 1 Output number, product √ ½ Stop √ ½ |
6 |
||||||||||||||||||||||||
17. a) |
This is a processing mode where many users have access to a centralized computer apparently at the same time. Each user is allocated a time slice for accessing the CPU. A user whose task requires more time than what is allocated is send back to the queue. For example, four users are apportioned equal time slice in each round until they are done.
Incomplete Job back to queue |
1 1 2 |
||||||||||||||||||||||||
|
b) |
|
2 2 |
||||||||||||||||||||||||
|
c) |
|
2 |
||||||||||||||||||||||||
|
d) |
|
3 |
||||||||||||||||||||||||
|
e) |
Integrated software refers to a single program that contains many different applications while software suite refers to related software that is bundled together and sold as a package |
2 |
||||||||||||||||||||||||
|
18. a) |
111.01 10011.001 1011.111 -101.011 10011.001 1101.110 Convert 1101.011 to decimal
X 10 = 8 + 4 + 0 + 1 + 0 + 0.25 + 0.125 = 13.375 |
1 1 1 1 |
||||||||||||||||||||||||
|
b) |
Convert 1110 to binary 10112 Convert 810 to binary 10002 000010002 - 000010112 ones complements of 00001011 11110100 Twos complements 11110100 +1 11110101 00001000 + 11110101 = 11111101 Deny one mark if 8 bit notation is not used |
½ ½ 1 1 1 1 |
||||||||||||||||||||||||
|
c) |
No mark if equal sign is omitted |
2 |
||||||||||||||||||||||||
|
4 |
|||||||||||||||||||||||||
|
19. a) |
|
3 |
||||||||||||||||||||||||
|
b) |
|
1 1 1 |
||||||||||||||||||||||||
|
c) |
|
2 2 |
||||||||||||||||||||||||
|
d) |
|
3 |
||||||||||||||||||||||||
|
e) |
|
2 |
||||||||||||||||||||||||
|
20. a) |
|
3 |
||||||||||||||||||||||||
|
b) |
|
3 |
||||||||||||||||||||||||
|
c) |
|
4 |
||||||||||||||||||||||||
|
d) |
|
3 |
||||||||||||||||||||||||
|
e) |
(First 2 ×1) |
2 |
||||||||||||||||||||||||
Download Computer Studies Paper 1 Questions and Answers - Nginda Girls Mock Examination 2023.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students
