Instructions to candidates
- This paper consists of two sections: A and B
- Answer all the questions in section A
- Answer question 16 and any other three questions from section B
- All answers must be written in the spaces provided on the question paper.
- Identify three advantages of using computers in banking (3mks)
- List three facilities that will ensure proper ventilation in a computer lab (3mks)
- Give two main functions of a computer input device. (2mks)
- What are turnaround documents? (1mk)
- Using examples, distinguished between:
- Primary and secondary storage (1mk)
- Fixed and removable disks (1mk)
- Ann connected new multimedia speakers to her computer and tried to play her favorite music CD, but no sound came out. Suggest two problems that might have occurred (2mks)
- Explain the following considerations when purchasing software (2mks)
- Authenticity
- Portability
- Give three ways in which operating systems are classified into (3mks)
- Peter tried to retrieve a document file following all the steps correctly. The filename did not appear in file list box. State three causes for this. (3mks)
- State the use of the following objects in databases. (3mks)
- Tables
- Forms
- Query
-
- Explain the meaning of the following as used in computer programming. (2mks)
- Syntax
- Semantic
- List three ways in which data integrity can be compromised. (3mks)
- Explain the meaning of the following as used in computer programming. (2mks)
-
- Mobile phones have become common ICT devices. Explain some of the powerful capabilities that come with some of the latest embedded operating systems (3mks)
- List two disadvantages of fiber optic cable over twisted wires. (2mks)
- Describe any two types of data processing methods. (2mks)
- State two advantages of USB port over the parallel port (2mks)
- Differentiate between the terms signal Attenuation and Noise as used in data communication. (2mks)
SECTION B
Answer question 16 and any other three questions in this section
-
- State three advantages of low -level languages (3mks)
- Give two differences between a compiler and an interpreter. (2mks)
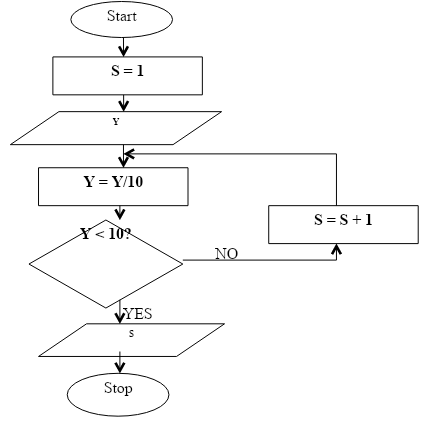
- Study this flowchart and use it to answer the questions that follow.
- Give the expected output from the flowchart when the value of Y is:
- 48 (1 marks)
- 9170 (2 marks)
- – 800 (2 marks)
- Write the pseudo code that can be used to create a program represented by the above Flowchart.
- Give the expected output from the flowchart when the value of Y is:
-
- Use two complement to perform the following arithmetic operations
- 1510 − 1210 (4mks)
- 101112 − 10112 (3mks)
- 10112 is a ones complement binary representation of negative number using four bits work out the likely positive equivalent in base 10. (4mks)
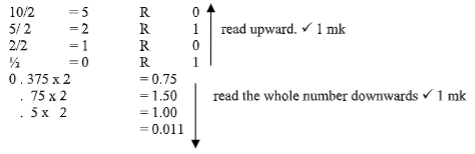
- Convert the decimal fraction 10.37510 into its binary equivalent (3mks) Whole numbers
- Assuming the existence of base five, list the numbers used in the number system (1mk)
- Use two complement to perform the following arithmetic operations
-
- State and explain two disadvantages that will come about if a network was to be installed in your school. (4mks)
- Discuss two disadvantages of wireless networks. (4mks)
- Write the following abbreviation in full. (2mks)
- F.T.P
- H.T.T.P
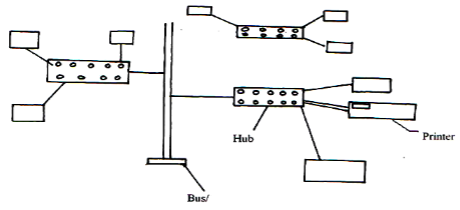
- With the aid of a diagram, discuss Hybrid topology. (4mks)
- Discuss four advantages of network. (2mks)
-
- Explain why a computer is able to display the correct time and date when it has just been switched on. (2mks)
- Discuss two types of special memories found in a Computer System. (4mks)
-
- Define a Bus with reference to a computer system. (1mk)
- List two examples of buses. (2mks)
- Distinguish between a power cable and interface cable. (2mks)
- Differentiate between the different types of RAM. (4mks)
-
-
- Define a system. (1mk)
- Explain system entropy. (2mks)
- State three circumstances that can lead to development of information systems (3mks)
- Distinguish parallel changes over from straight change over as used in system implementation. (2mks)
- Discuss two fact finding methods. (4mks)
- Differentiate an open system from a closed system. (2mks)
- List two responsibilities of a system analyst. (2mks)
-

MARKING SCHEME
SECTION A
- Identify three advantages of using computers in banking (3mks)
- Speed and accuracy
- Easy to access information
- Easy to update records
- Requires less space for storage
- Improves data security and privacy
- List three facilities that will ensure proper ventilation in a computer lab (3mks)
- Large & enough windows and doors
- Installing air conditioning system
- Avoid overcrowding of either machines or people in the room
- Give two main functions of a computer input device. (2mks)
- Accepts data & instructions from the user and sends them into the CPU. V
- Converts data into a form that the computer can understand (i.e., machine-Sensible/readable form)
- What are turnaround documents? (1mk)
- These are documents produced as output and which can be re-used as input by the computer
- Using examples, distinguished between:
- Primary and secondary (1mk)
- Primary storage devices are accessed directly by the CPU, while secondary storage is not
- Fixed and removable disks (1mk)
- Fixed disks are mounted inside the computer system unit, e.g. Hard disk.
- Removable disks are not hosed inside the system unit & are portable, e.g. floppy disk, Jazz disk, Zip disk, flash disk, CD- R, CD – RW, DVD
- Primary and secondary (1mk)
- Ann connected new multimedia speakers to her computer and tried to play her favorite music CD, but no sound came out. Suggest two problems that might have occurred (2mks)
- Volume control was too low
- Loose or improper connection to the sound card
- Speakers not powered
- Multimedia not supported
- Lack of analogue cable connecting the optical drive to the motherboard or sound card
- Sound card drivers not installed
- Explain the following considerations when purchasing software (2mks)
- Authenticity
- It is the genuineness, validity or legitimacy of software. The copy of the software you buy should be accompanied by the license and certificate of authenticity of the developer.
- Portability
- It refers to whether a program can be copied or installed in more than one computer
- Authenticity
- Give three ways in which operating systems are classified into (3mks)
- The number of users they handle
- The number of tasks they execute concurrently
- Human computer interface
- Peter tried to retrieve a document file following all the steps correctly. The filename did not appear in file list box. State three causes for this. (3mks)
- The file may not have been saved
- The file may have been deleted
- The file may be located in a different folder from the one she was trying to retrieve from (or may have been moved).
- The file may have been destroyed by a computer virus.
- State the use of the following objects in databases. (3mks)
- Tables -To store related records
- Forms -They act as screens for entering, changing & viewing data in tables
- Query-Searching for specific records/Data manipulation/Selecting
-
- Explain the meaning of the following as used in computer programming. (2mks)
- Syntax -these are rules that govern the arrangement of commands in a particular language
- Semantic - the meaning attached to every command in a particular language.
- List three ways in which data integrity can be compromised. (3mks)
- Natural disasters such as fires, floods and earthquakes.
- Human errors e.g. inaccurate data entry, accidental deletion.
- Worms and viruses.
- Hardware malfunctions.
- Fraud.
- Malicious deletion or changing of data.
- Explain the meaning of the following as used in computer programming. (2mks)
-
- Mobile phones have become common ICT devices. Explain some of the powerful capabilities that come with some of the latest embedded operating systems (3mks)
- Wireless communication (LAN)
- Icons in form of commands
- Voice recognition
- Multimedia e.g video MP3 player
- Java applications
- List two disadvantages of fiber optic cable. (2mks)
- Connectivity devices and the media are expensive.
- Installation is default because the cable must be carefully handled.
- It is relatively complex to configure.
- Mobile phones have become common ICT devices. Explain some of the powerful capabilities that come with some of the latest embedded operating systems (3mks)
- Describe any two types of data processing methods. (2mks)
- Manual – Use of a pen and a paper
- Mechanical – Use of typewriter and calculators
- Electronic – Use of computers
- State two advantages of USB port over the parallel port (2mks)
- Faster data transfer rate
- Supports multiple devices
- Differentiate between the terms signal Attenuation and Noise as used in data communication. (2mks)
- Attenuation is loss of signal strength over distance while noise is deterioration of signal quality
SECTION B
-
- State three advantages of low -level languages (3mks)
- The program instructions can be executed by the processor much faster as complex instructing are already broken down into smaller simpler ones
- The CPU can easily understand low – level languages without or with little translation
- They have a close control over the hardware, are highly efficient and allow direct control of each operation
- They require less memory space
- They are stable
- Not commonly used, hence can be used to code secret programs
- Give two differences between a compiler and an interpreter. (2mks)
Interpreters Compilers Translates the source program one instruction at a time. Translates the entire source code at once before execution Translates the program each time it runs hence slower than the compiler Executes faster than the interpreter since the object code can be stored and retrieved when required Interpreted object code occupies less space than the compiled one Since compiled object files are larger than the
interpreted ones, they thus occupy large space - Study this flowchart and use it to answer the questions that follow.
- Give the expected output from the flowchart when the value of Y is:
- 48 (1 marks)
Solution:
Y = 48
= 48/10
= 4.8
4.8 < 10 YES
Y = 4.8
S = 1 - 9170 (2 marks)
Solution:
Y = 9170
= 9170/10
= 917
917 <10 NO
∴ S = S + 1
= 1 + 1
S = 2
917/10 = 91.7
91.7 < 10 NO
∴ S = 2 + 1 = 3
Y = 91.7/10 = 9.17
9.17 < 10 YES
∴ S = 3 - –800 (2 marks)
−800/10 = −80
−80 < 10 YES
∴ S = 1
- 48 (1 marks)
- Write the pseudocode that can be used to create a program represented by the above Flowchart.
Start
S=1
Read
Repeat Y
Y = Y/10
IF (Y <10) THEN
S = S + 1
ENDIF
UNTIL Y < 10
PRINT S
Stop
- Give the expected output from the flowchart when the value of Y is:
- State three advantages of low -level languages (3mks)
-
- Use two complement to perform the following arithmetic operations
- 1510 −1210 (4mks)
1510
= 11112
1210= 11002 ✓1 mk
Ones complement of = 11002 = 00112 ✓ (1mk)
2c5 of 0011 = 0011+ 1 = 0100 ✓mk
Therefore: 11112
+ 01002
Overflow bit 10112
0011 +
= 00112 ✓1 mk - 101112- 10112 (3mks)
Ones complement of 010112 = 101002 ✓1 mk
2c5 = 10101
Therefore 10111
10101✓ 1
1 01100
01100 ✓1
- 1510 −1210 (4mks)
- 10112 is a ones complement binary representation of negative number using four bits work out the likely positive equivalent in base 10. (4mks)
1011 →-ve number
0100 →+ve number ✓1
= 1 x 22 = 4
✓1 ✓1 ✓1 - Convert the decimal fraction 10.37510 into its binary equivalent (3mks)
Whole numbers
Combine the two
= 10102 + 0.0112 ✓1mk
= 1010.0112 ✓1 mk - Assuming the existence of base five, list the numbers used in the number system (1mk)
Base five numbers
0, 2, 3, 4 ✓ 1mk
- Use two complement to perform the following arithmetic operations
-
- State and explain two disadvantages that will come about if a network was to be installed in your school. (4mks)
- High initial cost – The cost of buying network hardware and software is very high.
- Security issues – The data on the network is prone to illegal access threats.
- Discuss two disadvantages of wireless networks. (4mks)
- Difficult to establish or configure
- Initial cost is very high
- Write the following abbreviation in full. (2mks)
- F.T.P
- File Transfer Protocol
- H.T.T.P
- Hyper text transfer protocol
- F.T.P
- With the aid of a diagram, discuss Hybrid topology. (4mks)
- Discuss four advantage of network. (2mks)
- Resource sharing
- Distributed processing
- Cost effectiveness
- Reliability
- State and explain two disadvantages that will come about if a network was to be installed in your school. (4mks)
-
- Explain why a computer is able to display the correct time and date when it has just be switched on. (2mks)
- Because it is set and stored in a special memory known as the complementary metal – oxide semiconductor (cmos) chip which is powered by cmos battery
- Discuss two types of special memories found in a Computer System. (4mks)
- Buffers – Special memories found in the input / output devices.
Cache – Fast type of RAM found in the processor. - Register - Hold one piece of date at a time and are found in the ALU
- Buffers – Special memories found in the input / output devices.
-
- Define a Bus with reference to a computer system. (1mk)
- Bus – This are electronic pathways or links
- List two examples of buses. (2mks)
- Data, Address and Bus
- Define a Bus with reference to a computer system. (1mk)
- Distinguish between a power cable and interface cable. (2mks)
- A power cable is used to transmit data from the source (socket) to the computer while interface cables are special cables used to connect peripheral cables to the system unit.
- Differentiate between the different types of RAM. (4mks)
- Static RAM – is a fast type of RAM located inside the microprocessor
- Dynamic RAM – is a relatively slow type of RAM. It has the tendency for the stored charge to leak a way even with constant power supply hence requires periodic recharging.
- Explain why a computer is able to display the correct time and date when it has just be switched on. (2mks)
-
-
- Define a system. (1mk)
- Is a set of organized components which intersect in a given environment and within a specified boundary to achieve collective goals.
- Explain system entropy. (2mks)
- It means decay where a system slowly becomes useless to the user due to improvement in user requirements
- Define a system. (1mk)
- State three circumstances that can lead to development of information systems (3mks)
- New opportunity
- Problems
- Directives
- Distinguish parallel changes over from straight change over as used in system implementation. (2mks)
- Parallel change over both old and new systems are run parallel to end other for some time until users have confidence in new system is stopped and discarded and the new system started immediately. While in straight change over the system is immediately implemented and the old one discarded
- Discuss two fact finding methods. (4mks)
- Interviews – it is carried out with relevant stakeholders in order to get views about the current system.
- Questionnaires – Special purpose document that allows a person to collect information and opinions from people who receive and respond to it.
- Observation – Require the observer to participate or watch closely as a person performs activities in order to learn about the system.
- Automated method – Used when one wants to get actual data which may be difficult to get through interviews,observation or questionnaires.
- Differentiate an open system from a closed system. (2mks)
- An Open system is that which interacts and communicates with its environment constantly. It receives inputs from & gives output to the environment.
- A closed system is that which does not interact or communicate with its environment. It does not communicate to or receive communication from its environment.
- List two responsibilities of a system analyst. (2mks)
- Review an existing system and making recommendation on how to improve or implement an alternative system
- Working hand in hand with programmers to construct a computerized system.
- Coordinating training of new system users and owners.
-
Download Computer Studies Paper 1 Questions and Answers - Momaliche Post Mock 2020 Exam.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students