- State the two functions of the control unit (2 marks)
- Decoding signals
- Sending timing and controls to all the components of the computer
- Explain four reasons which make microcomputers suitable for personal computing work. (2 marks)
- Reduced cost, i.e. are cheaper than the minicomputers and mainframe computers
- Have high processing speeds
- Are small in size (occupy less office space).
- Consume less power
- Are versatile (i.e. can be used for many different tasks).
- Are more reliable in doing various functions than the early mainframe computers.
- State the functions of the following keyboard key combinations (3mks)
- CTRL + ESC:
- Opens the START menu
- ALT + F4
- Close the currently active program
- CTRL + ALT + DEL:
- restart
- CTRL + ESC:
- Distinguish between an integrated software and a software suite (2mks)
- An integrated software package is a single application which combines the most commonly used functions and commands or interface of many productivity software programs.
- A software suite, also known as application suite, is a software package that has several applications that work well together available and sold as a single unit.
- Differentiate between embedded computers and dedicated computers (2mks)
- Dedicated computer system is a general purpose computer confined to perform only one function for reasons of efficiency e.g database server, Webserver etc embedded computer is a computer within an electronic or mechanical device to control its functions e.g in traffic light controller, Mp3 player, and digital watches.
- Give three reasons why a company may prefer a tailor made software over off the shelf software (3mks)
- The solutions it offers give the greatest depth, and flexibility possible in meeting the needs of an organization.
- The software developer delivers and installs the software and trains the end users in the use of the new software.
- They perform tasks that the general purpose software cannot perform.
- This kind of software can be quickly changed when the needs of the organisation change, since the source code belongs to the company.
- Explain the function of the following registers (2mks)
- Instruction registers
- Hold the instruction are just about to be processed
- Address registers
- Hold address of the next piece of instruction to be processed.
- Instruction registers
-
- Explain how a computer system can be protected from intruders(2mks)
- install security alarms
- use CCTV cameras
- employ security officers
- use passwords and user access security level
- State any two laws governing protection of information (2mks)
- Data be not transferred to other countries without the owner’s permission.
- Data and information should be kept secure against loss or exposure.
- Data and information should be accurate and up to date.
- Data and information be collected used and kept for specified lawful purposes.
- Explain how a computer system can be protected from intruders(2mks)
-
- What is the meaning of graphics as used in word processing? (1mk)
- Any non-text images
- Give two sources of graphics in the computer (2 mks)
- Clip art
- Scanners
- Drawing using drawing tools
- From a file
- What is the meaning of graphics as used in word processing? (1mk)
- State the cursor action when the following keyboard keys are pressed (2mks)
- Delete key
- Remove a character to the right of the cursor
- Insert key
- A newly typed character will replace the character at the cursor position
- Pgup (page up) key
- Will move the cursor one screen towards the beginning of the document
- Pgdwn (page down) key
- Will move the cursor one screen to the end of the document
- Delete key
- Identify the parts of the following e-mail address labeled A, B, C and D (4mks)
A – Name of the individual or organization
B – Name, of the host computer in the network on which the email account is hosted.
C – Identifies the type of the organization or institution offering a particular service, i.e. commercial organization
D – Name of the country where the site is located, i.e. Kenya
-
- What is a search engine?(1mk)
- A special program that collects and stores links to information websites allowing users to search its database for them.
- Give four examples of search engines you know. (2mks)
- google.com
- yahoo.com
- hotmail.com
- What is a search engine?(1mk)
-
- Define the following terms as used in a worksheet. (2mks)
- Columns
- These are fields that make up the worksheet of a spreadsheet, and are identified by letters. They run vertically from top downwards.
- Rows
- These are the records that form a worksheet, and are identified by numbers. They run horizontally from left to right.
- Columns
- Distinguish between absolute cell reference and relative cell reference (2mks)
Relative Referencing- When you copy a formula from one place to another in the same or different worksheet, Excel adjusts the cell references in the formula relative to their new positions in the worksheet
Absolute referencing; - An absolute cell reference displays the exact address of the cell regardless of the position of the cell that contains the value using the absolute cell references. A formula does not change when copied to a new location like how relative cell reference adjusts the formula while it is copied.
- When you copy a formula from one place to another in the same or different worksheet, Excel adjusts the cell references in the formula relative to their new positions in the worksheet
- Define the following terms as used in a worksheet. (2mks)
-
- State one data processing file (1mk)
- Master file
- Transaction file
- Reference file
- Backup file
- Explain the file named above in 14. a) (2mks)
- Master file, main file that contain permanent records of a particular entry.
- Transaction (movement) file, used to hold input data during transaction processing.
- Reference file, mainly used for reference or look-up purposes.
- Backup file, used to hold copies (backups) of data or information from the computers fixed storage (hard disk).
- State one data processing file (1mk)
- Give one reason to the growth of communication industry in Kenya (1mk)
- Technological and scientific advancement
- Civilization
- Growth of economy
- Good governance
SECTION B (60MARKS)
-
- List two examples of;
- Third generation languages (2mks)
- Pascal
- FORTRAN
- BASIC
- COBOL
- Object oriented languages (2mks)
- Simula
- Small talk
- Java
- C++
- Third generation languages (2mks)
- Define (2mks)
- Object code
- It is a machine code produced by a computer
- It is an output of a translator
- It is a translated source code
- Translated program code
- Source code
- This is a program written in the specific programming language
- Untranslated program code
- Program in human understandable
- Object code
- Differentiate between a compiler and an interpreter
Compiler Interpreter
Fast in translation Relatively slow translate line by line
Translate whole program at once Translate line by line take less memory
Take up large memory space Take less memory every time program is run hence
Saves time because Exe file is saved Every time program is run hence consume time - Write a pseudocode to accept a car number and the rental period, and calculate the total amount earned by the company when a car is leased. (7mks)
START
PRINT ENTER CAR NUMBER
PRINT ENTER NUMBER OF DAYS
IF NUMBER OF DAYS>=7THEN
(NUMBER OF DAYS X 2500) – (NUMBER OF DAYS X 2500) 25%
ELSE
NUMBER OF DAYS X 2500 END IF
- List two examples of;
-
- Three parameters that determines the magnitude of a number (3 mks)
- Absolute value: Magnitude of a digit in the number line. For example, digit 2 in 423 has an absolute value of 2 according to its value in a number line.
- Place value: Position of a digit in the number, whether ones, tens, hundreds and so on. For example, digit 2 in 423 has a place value of tens hence the total value is 20.
- Base value: Radix of the number system that is being used. For example, 32 and 310 mean three base two and three base ten respectively, and have different values.
- Using two’s complement, show how the arithmetic below would be carried out on a 8 - bit computer system. (+54) - (+29) (5mks)
Solution;
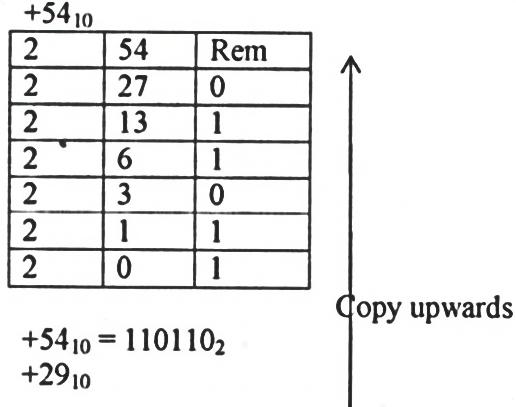
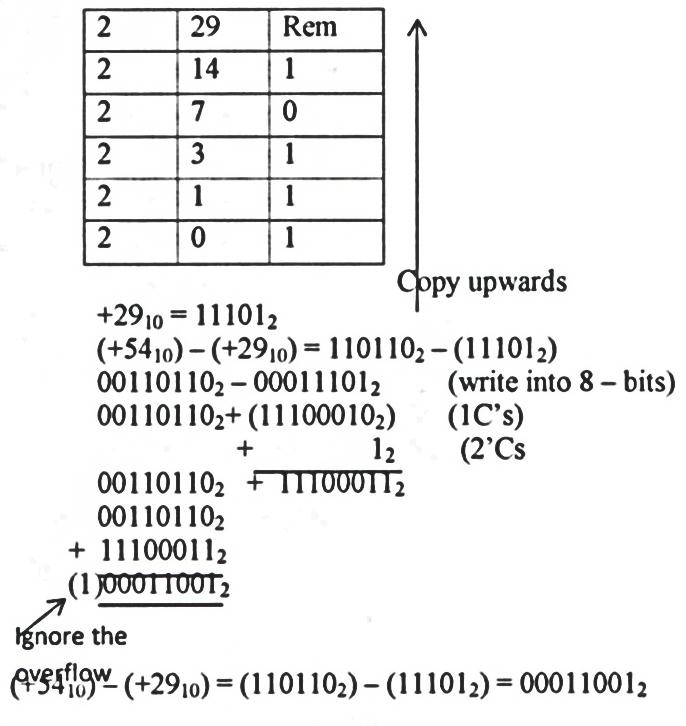
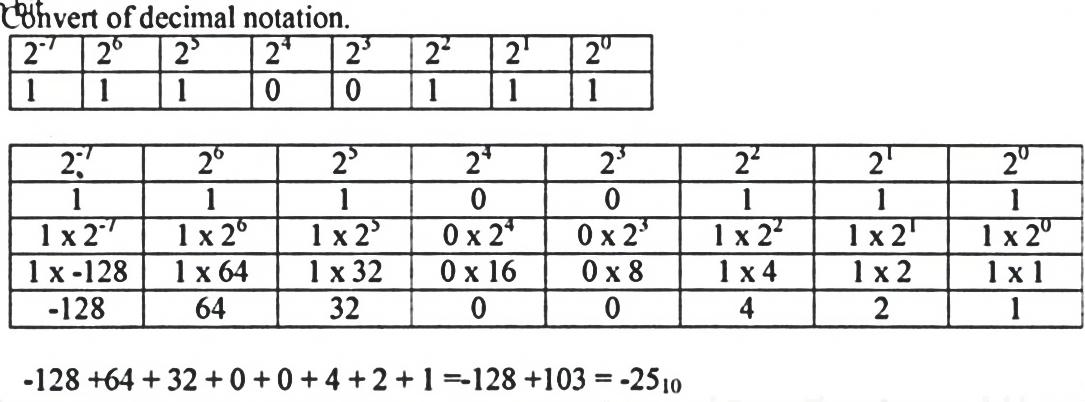
- Convert of decimal notation. (5mks)
- A word is a group of bits accessed as a unit whereas a word length is the number of bits in a word. (2mks)
- Three parameters that determines the magnitude of a number (3 mks)
-
- State the meaning of the following operating systems terms:
- Interrupt (1mk)
- Stoppage of an executing program temporarily so as to allow for another with a higher priory to run
- Trouble shooting.
- Seeking / searching of a solutions to a problem in
- Clock speed.
- Speed of instruction processing by processor.
- Interrupt (1mk)
- Differentiate the following
- disk compression and disk defragmentation
- Disk compression is squeezing contents of a disk to occupy less space while disk defragmentation is putting together the scattered parts of a file for easy retrieval.
- Disk partitioning and disk formatting
- Partitioning is dividing a disk into two or more logical drive while disk formatting is preparation of a disk for data storage
- disk compression and disk defragmentation
- The operating system has several functions in a computer, explain how the operating system performs the following functions (4mks)
- Error handling
- The operating system has many ways of alerting the user of errors he/ she makes. The operating system being a manager that oversees all the activities of the computer, it monitors all the user activities. Due to this, the operating system has the ability to identify errors made by the and where possible suggestions on how to correct the errors are made. On the other hand, the operating system monitors the status of the computer system by performing error checks on both hardware and software.
- Resource control and allocation
- The operating system uses the IRQ number to identify the resource being requested by processes, poor resource allocation would result to an undesirable condition referred to as deadlock (this is whereby a process holds the a requested resource and fails to release it, yet it is requesting for a resource held by another process)
- Error handling
-
- Runtime problems
- Restart the computer
- Corrupted registry
- Use of emergency repair disk to restore the files
- Runtime problems
- State the meaning of the following operating systems terms:
-
- Giving examples, differentiate between hard system and soft system (4mks)
- Hard systems: These are systems whose goals & objectives are dearly defined, and the outcomes from their processes are predictable and can be modeled accurately.
- Example: Stock management system in a supermarket
- Soft systems: These are usually the human activity systems whose boundaries keep on changing and their goals & objectives usually conflict, and may not be captured clearly at any one given time. This is because; they are based on human factors such as attitudes & preferences. It is difficult to clearly define their exact measures of performance.
- Example of soft systems: A Political system:
- Explain the following system characteristics(2mks)
- System control
- It is the method by which a system adapts to changes in the environment in order to give the expected output or to pet form to the expected level.
- Sub-systems
- This means that, a system does not exist alone, but it is composed of subsystems, which are also made up of other subsystems
- System control
-
- What is a closed system? (1mk)
- A Closed system is that which does not interact or communicate with its environment. It does not communicate to or receive communication from its environment.
- Give three characteristics of a closed system (2mks)
- Closed systems do not receive inputs or give output to their environment.
- A closed system can correct or control itself; hence, it does not obtain modification from its environment.
- A closed system has a limited scope when providing the services of the organization.
- The variables in a closed system are self-contained.
- A closed system is rigid & mathematical.
- What is a closed system? (1mk)
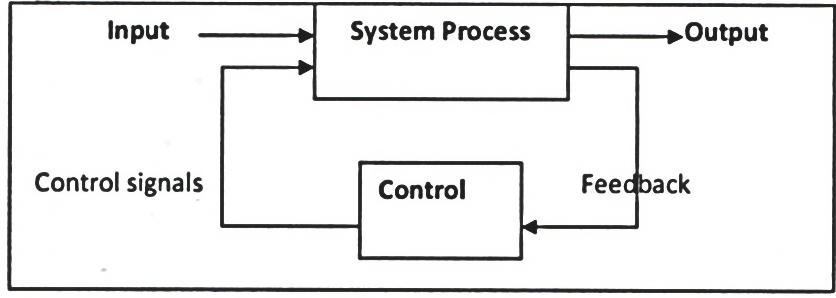
- Why is feedback necessary in a system? (2mks)
- Feedback is a check within a system, which ensures that the objectives of the system are achieved. They assist the system by monitoring the environment in which it operates in order to find out any deviation. If any deviation is detected, then the appropriate steps are taken to rectify this error.
- Draw a diagram to shows a system that is controlled through feedback (4mks)
- Giving examples, differentiate between hard system and soft system (4mks)
-
- Define the term Multiplexing as used in networking (1mk)
- Multiplexing is the process of sending multiple data signals over the same medium, e.g., a wire conductor can be made to carry several data signals either simultaneously or at different times
- Describe the following signal wave properties
- Frequency of a wave is the number of cycles (vibrations) that the wave makes per second. It is measured in Hertz (Hz)
- Wavelength is the distance between two adjacent crests or troughs, and is measured in metres (M).
- Amplitude is the maximum displacement disturbance) of the medium from equilibrium (rest) caused by the wave.
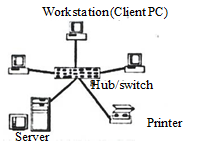
- Use a diagram to distinguish between ring and star network topologies (2 marks)
- Ring topology
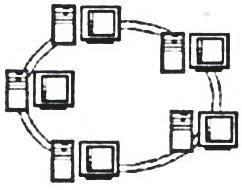
- Data flows from one computer to another in one direction, and each computer actively participates in data transfer from one Star topology station to the other.
- Star topology
- It consists of computers and other devices, each connected to a common central server called the Hub. However, to connect to the central machine, each computer uses a separate cable.
- Nodes communicate across the network bypassing data signals through the hub, i.e., any two computers (workstations) in the network communicate through the central machine.
- When the hub receives data from a transmitting computer, it broadcasts the message to all the other nodes on the network.
- Ring topology
- Give one advantage and one disadvantage of each of c) above
Advantages of Ring topology
- They use a short length cable.
- Simple to install.
- Provides high performance for many users.
- Provides an orderly network in which every device has access to the token and can transmit data.
Disadvantages of Ring topology
- Failure of one computer or the cable will affect the rest in the entire network.
- Modification is difficult because; adding or removing a device can disrupt the entire network,
- Troubleshooting can be difficult.
Advantages of Star topology
- Allows key networking resources such as concentrators & servers to be centralized.
- Easy to configure
- Enhances operational survivability
- The hub isolates the network cables from each other. Even if a wire between a workstation and the hub breaks or develops a bad connection, the rest of the network remains operational.
- Simple to control
- It can be extended easily, since a workstation is simply connected to the hub.
- Provides flexibility in adding or deleting devices.
Disadvantages of Star topology- If the central switch node (Hub) fails, it may bring down the entire network.
- It is costly because: each workstation is connected to the central concentrator by is own dedicated cable (i.e., it requires a lot of cables).
- Installation is time consuming, because each node forms a segment of its own.
- May require a special device for signal regeneration across the network.
-
- What is virtual reality? (1mk)
- human being psychologically immersed in artificial environment generated by the computer
- Describe four essential equipment to achieve virtual reality (4mks)
- Headgear- This is a components made up of two display screens and sound systems that channel images and sound from the source to the eyes and ears in order to present a stereo 3D sound effect in the virtual world
- Gloves- Worn on hands to allow the user navigate through and interact with virtual objects
- Body suit- Is made up of conductor wires wound in a rubber suit to sense body movement and relay the data into the virtual reality system which will then adjust the user's position
- Virtual reality software- Is a software that stimulates all aspects of virtual reality world
- What is virtual reality? (1mk)
- Define the term Multiplexing as used in networking (1mk)
Join our whatsapp group for latest updates
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Download COMPUTER STUDIES PAPER 1 Marking Scheme - 2017 KITUI MOCK EXAMINATION.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students