QUESTIONS
SECTION A (40 marks)
Answer all the questions in this section.
- Identify the transmission mode used when communicating with the devices listed below. (2marks)
- Public address system
- Phone chat via WhatsApp
-
- List two categories of system software(2marks)
- A warranty is an agreement between the buyer and the seller. It spells out terms and conditions after selling a product in case of failure or malfunction. Describe any three basic requirements a good warranty should cover. (3 marks)
- Beryl does not understand why computers are said to be Automatic at the same time they have No Intelligent Quotient (IQ) (2marks)
- Vero a student from Nyamira Girls lives in a house with full internet access. She spends most of her time on phone and Desktop computer. State any three social issues associated with doing this. (3 marks)
- The following are symbols of some keys on the keyboard. Name the keys represented by the symbols (2marks)
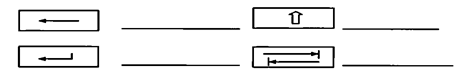
- Give three reasons that might have necessitated the development of Second generation computers (3 marks)
- Millicent wrote a program but it did not behave as expected. Describe two types of errors that may hinder the program from running or run but give invalid results. (2marks)
- Describe two password options that Ms-Word employ to protect its documents. (2marks)
- Mention two limitations of using counterfeit software. (2marks)
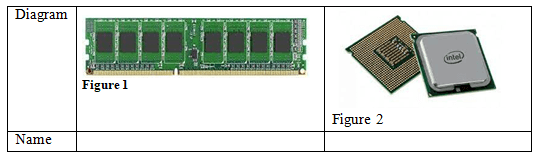
- Name the computer parts listed below. (2marks)
- Describe the following functions of the operating system. (3marks)
- Network Management
- Security
- Interrupt Handling
- State three ways in which computer virus infection can be prevented other than through restricting the usage of removable storage media (3marks)
-
- Define the term normalization. (1 mark)
- State a reason to justify why database administrators usually perform normalization when creating a database for an organization. (2marks)
- Mention three factors to consider when choosing a file organization method. (3marks)
- As Jayden was entering data into the computer, He typed byocott instead of boycott.
- Identify the type of error made by Jayden (1 Mark)
- Other than using direct data entry devices, state two other methods Jayden can use to avoid the error (2 Marks)
SECTION B (60 marks)
Answer questions 16 and any other three questions from this section.
-
- Describe the following qualities of an algorithm. (2marks)
- Definiteness
- Finiteness
- Describe the three essential programming constructs which form the basis of structured programming (3 marks)
- State two advantages of low-level languages(3 marks)
- The table below shows the monthly charges applicable to different amount of water consumed by clients in a particular town
In addition to the consumption, the amount of the water bill will consist of a standing charge of Kshs 200 and a sewerage fee equivalent to 20% of the consumption.Volume of Water consumed in m3 Consumption in Kshs 0-10 200 10-20 350 20-30 500 Over 30 1000
Write a pseudo code for a program that prompts a user to enter the volume of water consumed per month. The program then computes and output the amount of the water bill in a year. (7 marks)
- Describe the following qualities of an algorithm. (2marks)
-
- The table below is an extract from a spreadsheet use it to answer the questions that follow
A B C D E F 1 Customer Number Product Name Quantity Unit Cost Total Type Remark 2 145321 Malomalo 20 100 2000 Bronze 3 145361 Kisambo 40 200 8000 Silver 4 156784 Weeti 40 400 16000 Gold 5 123454 Wheat 20 50 1000 Bronze 6 453218 Nyozi 10 10 100 Bronze GRAND TOTAL 27100 - Identify the Ms-Excel feature that is used in cell A1 and B1 to enable the texts appear the way they are. (1mark)
- Name the data type in cell E4 and F3. (2marks)
- Use absolute reference to represent a formula that is used to calculate total for wheat (2 marks)
- Suggest how named reference can be used to calculate the GRAND TOTAL. (3marks)
- Write a formula that will classify product type base on the total as shown in the table below. (2 marks)
Total Type 0-5000 Bronze 5001-10000 Silver 10001 and Above Gold
- State the difference between Cc and Bcc. (2marks)
- Mention three factors to consider when choosing an ISP. (3marks)
- The table below is an extract from a spreadsheet use it to answer the questions that follow
-
- What is the binary equivalent of 12⁄32 base 10 (4marks)
- What is the decimal equivalent of the number 1.01112? (3 marks)
- Explain four control measures that can be taken to avoid unauthorized access to data in a Computer system or data. (4 marks)
- List four career opportunities in the field of ICT. (2marks)
- With reference to DTP describe the following terms. (2marks)
- Gutter
- Stroke
-
- State two circumstances under which a system analyst may prefer to use questionnaire instead of observation during facts finding. (2marks)
- Mention three operational factors that a system analyst need to consider when sourcing for hardware and software to be used with the proposed system. (3marks)
- Describe two advantages of parallel changeover. (2marks)
- Name any two wireless communication devices (2Marks)
- Describe two factors to consider when choosing a transmission media (2marks)
- The Chairman IEBC has called upon a System Analyst to implement an electronic rating system. He intends to use voter’s fingerprints, Identity cards and voter’s cards as security measures to ensure free and fare elections. Recommend with reasons four input devices that they should use/buy.(4marks)
- The following records were entered in a database
Date Class Registration No 1/1/2007 East 1425-A 1/1/2008 North 1426-A 1/1/2008 North 1426-B - Suggest a validation rule for date given that it should be not before 1/1/2006 (2marks)
- List the records that will be displayed after running the following criteria? (2marks)
- <>#1/1/2008ondate
- 1426-A on class
- Write the input mask for registration No (1mark)
- Choose the most appropriate data type for Date and Registration No (2marks)
- Explain the following terms as used in Word Processing (3marks)
Word Wrap
Orientation
Indenting - State three specifications that should be set in the print dialog box when printing a document (3 marks)
- State two major reasons why organizations are opting for telecommuting. (2 marks)

MARKING SCHEME
-
- Public address system
Simplex - Phone chat via WhatsApp
Duplex/Half Duplex
- Public address system
-
-
- √ Firmware;
- √ Networking software;
- √ Operating system;
- √ Utilities
-
- √ Period/duration/scope of cover: The warranty should specify the duration of time covered.
- √ Service agreement/level: The warranty should indicate the type of service to be provided.
- √ Cost implication/ liability agreement: Cost sharing between the dealer and the buyer in the event of any loss or malfunction.
- √ Call out response.
-
-
- It said to automatic because once it is given the correct it will be a position to execute numerous tasks without user intervention
- NO IQ because a computer purely depend on the installed program without the programs the computer cannot any task
-
- Dehumanization
- Internet addiction
- Flaming
- Drug trafficking
- Cyber terrorism
- Access to inappropriate content
- Intrusion to private information
- Fraud
- Symbols of some keyboard keys:
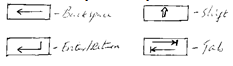
-
- A lot of heat that was generated by the first generation computers
- High power consumption that was experienced with the first generation computers
- The large size of the first generation
- The vacuum tube which usually breaks
- Very low processing of capability of the first generation computer
-
- Password open – This password grant access to the document
- Password to modify – This password give the authority to modify the content of the document
-
- Introduce malware in your computer
- Malfunction
- Lack of essential components
- Incompatibilities issues
- Figure 1
- RAM
Figure 2 - Processor
- RAM
-
- Network management
The operating system is responsible for facilitating connectivity and managing communication using communication protocols - Security
Operating system provide mechanism of protecting information and programs installed in the computer. This usually achieved through password, biometric systems, backup, system restore etc. - Interrupt handling
Operating system have interrupt handler which study the cause of the interrupt and then take the necessary actions order to solve the interrupt without interfering with normal sequential execution
- Network management
-
- Smart browsing
- Install latest antivirus versions and update regularly
- Always scan email attachment before downloading
-
- It is the process of decomposing fields into separate but related tables
- To minimize data redundancy in the database
-
- Method of access
- Storage media
- Frequency of update
-
- Transposition error
- Double entry of data for validation and verification
Using error detection and correction software
Or any other correct response
Method @ 1 Mark
Total = 2 *1 Mark
= 2 Marks
-
-
- Definiteness
Each step of an algorithm must be precisely defined; the actions to be carried out must be rigorously and unambiguously specified for each case - Finiteness
An algorithm must always terminates after a finite number of steps
SEQUENCE
In Sequence control, the computer reads instructions from a program file line-by-line starting from the first line sequentially towards the end of the file. This is called Sequential program execution.
Start → Statement 1 → Statement 2 → Statement n → End
SELECTION (DECISION)
Selection involves choosing a specified group of instructions/statements for execution.
In Selection control, one or more statements are usually selected for execution depending on whether the condition given is True or False
ITERATION (LOOPING / REPETITION)
Looping refers to the repeated execution of the same sequence of statements to process individual data. This is normally created by an unconditional branch back to a previous/earlier operation.
Advantagesof low - level languages- The CPU can easily understand low - level languages without or with little translation
- The program instructions can be executed by the processor much faster as complex instructions are already broken down into smaller simpler ones
- They have a closes control over the hardware, are highly efficient and allow direct control of each operation
- They require less memory space
- They are stable i.e. do not crash once written
- Not commonly used, hence can be used to code secret programs
- Definiteness
- Start
Set counter =1
Set S_Charge= 200
Set Bill =0
REPEAT
Enter Volume of Water
IF Volume >0 and <=10 Then
Consumption =200
Else
IF Volume >10 and <=20 Then
Consumption =350
Else
IF Volume >20 and <=30
Consumption =500
Else
Consumption =1000
End if
End if
End if
Sewerage = 0.2x Consumption
Bill = Bill+S_Charge+Consumption+Sewerage
Counter = counter +1
UNTIL Counter =12
Print Bill
Stop
-
-
-
- Wrap text
- E4 Formula/Function
F3 Function - =Product ($c$5:$D$5) or =$c$5:$D$5
- Rename E2 to E6 as Total
=Sum(Total ) - =IF(E2>=10001,"Gold",IF(E2>=5001, "Silver", "Bronze"))
Award 1 correct function
Award 1mark bracket to bracket
- CC field to send a copy of the email to people just to keep them in the loop while the BCC field is used when you want to send an email to multiple recipients but do not want any of them to know about the other people you have sent them to
-
- Cost
- Speed
- Cost
- Type of connection
- Reliability
- Customer support
-
-
- It is the same as 0.34375 Writing the number in decimal =1
0.34375 x 2 =0.6875 Multiplying by =1
0.6875 x 2 = 1.375 Reading correct values = 1
0.375 x 2 = 0.75 Answer =1
0.75 x 2 = 1.5
0.5 x 2 = 1.0 = 0.010112 - 1 x 2º + 0 x 2-1 + 1 x 2-2 + 1 x 2-3 + 1 x 2-4
1 + 0 + 1 x ¼ + 1 x 1/8 + 1 x 1/16 = 1 + 0.25 + 0.125 + 0.00625
= 1.3812510
Converting the whole number part=0.5
Converting the decimal number part=1
Addition =0.5
Answer =1 3 -
-
- Restricting access to the computer room: It is done to ensure that only authorized people to the room
- Reinforcing weak access points: Access points within a room can be the doors, windows, and the roof among others.
- Encryption of data transmitted through a network: This is converting data to a type that only the sender and the receiver are able to understand.
- Use of password: A password is a group of characters , numbers or both that is used to restrict access to a computer or file.
- Enforce network security: In a network sharing of resources should be restricted.
-
- Database administrators
- Network managers
- Computer technicians
- Trainers
- System analysts
-
-
- Gutter
The inside margins closest to the spine of a book or the blank space between two facing pages in the center of a newsletter or magazine is known as the gutter. The gutter space includes any extra space allowance needed to accommodate the binding of books, - Stroke
Refer to a line style
- Gutter
- It is the same as 0.34375 Writing the number in decimal =1
-
-
-
- When the people you need to gather information from are vastly dispersed
- When the analyst want to collect confidential information
- When limited amount of information is required from a large number of people
-
- Reliability
- Compatibility
- Upgradeability
- User needs
-
- Costly to run two systems
- Cross checking is difficult
- Require more staff hence training required for additional staff
- The benefits of the new system are not realized by the entire organization immediately
-
- Access points.
- Wireless Antennae
- PCMCIA Card
-
- Cost
- Bandwidth
- Attenuation rate
- Reliability
- Ease of Installation
- Distance
-
-
- Biometric scanner: It captures biometric details like fingerprints
- Digital camera: captures the voters photographs
- Keyboard: key in the voters details
- Mouse: issue command to the computer.
-
-
- <#01/01/2006#
-
- <>#1/1/2008 on date
Date Class Registration No 1/1/2007 East 1425-A 1/1/2008 North 1426-B - 1426-A on class
Date Class Registration No 1/1/2008 North 1426-A
- <>#1/1/2008 on date
- 0000-L
- Date –Date
Registration No – Text -
- Word wrap
The feature that automatically move a word or cursor to the beginning of the next line if does not fit at the end of the current line - Orientation
Refer to the position of the page in relation to the text which can either landscape or portrait - Indenting
Refer to moving the text way from the margin
- Word wrap
- Number of copies
Printer name
Paper size
Page range- It saves on the office space and allows workers to work at their convenient times
- It also reduces the office conflicts that may be encountered by staff 2
Download Computer Studies Paper 1 Questions and Answers - MECS Cluster Joint Mock Examinations 2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students
