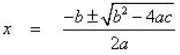QUESTIONS
- Name the two common types of system units and differentiate them. (2 marks)
- Define the following characteristics of a computer system. (2 marks)
- Versatile
- Reliable
- State any three types of computer programme documentation. (3marks)
- Name any three effects of ICT on health. (3marks)
- List one function of a bridge in computer network. (1mark)
-
- Convert 11110001101112 to its octal equivalent (1mk)
- Convert 512.258 to its base 10 equivalent. (2mks)
- With an aid of a diagram, differentiate between selection control structure and iteration control structure. (4marks)
-
- Auki company is in the process of computerizing its services. List four measures that should be put into consideration to protect the users in their computerized areas. (2 marks)
- Give two reasons why powder and liquid extinguishers are not recommended unlike gaseous extinguishers. (2 marks)
- Without proper marketing, a business cannot survive in a competitive environment hence computers are being used in a number of ways to enhance marketing. List any three ways of ensuring this is affected. (3 marks)
- Describe the following terms as used in computers. (3 marks)
- Tab Key
- Space bar
- Clicking
- Control unit is an essential component of the CPU. Describe the functions of the control unit. (2marks)
-
- Differentiate between buffers and Registers. (2 marks)
- Speech recognition devices are used to capture natural sound and convert the input into digital form. State two problems related to speech recognition devices. (2 marks)
- Define Solid-state storage and give two examples. (2 marks)
-
- Explain how a pixel affects the resolution of a monitor. (1 mark)
- List two types of computer output on microform (COM). (2 marks)
-
- Give three advantages of using ATM cards. (3marks)
- Differentiate between pasteboard and master page as used in DTP. (2 marks)
SECTION B (60 Marks)
Answer Question 16 (Compulsory) and any other three questions from this section.
-
- State two advantages and two disadvantages of high level programming language. (2 Marks)
- State three situations when REPEAT .. UNTIL structure can be used in writing a program. (3marks)
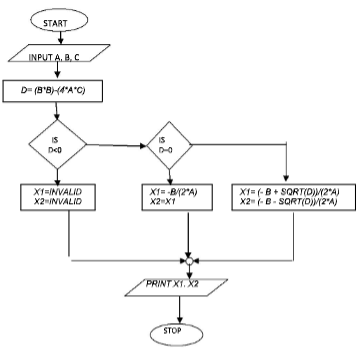
- The roots of the equation ax2 + bx + c = 0 are given by the formula below:
Study the pseudocode for the above formula and then draw a flowchart to represent it. (10marks)
BEGIN
INPUT A, B, C
D= (B*B)-(4*A*C)
IF D<0 THEN
X1=INVALID
X2=INVALID
ELSE
IF D=0 THEN
X1= -B/(2*A)
X2=X1
ELSE
IF D>0 THEN
X1= (- B + SQRT(D))/(2*A)
X2= (- B - SQRT(D))/(2*A)
END IF
END IF
END IF
PRINT X1, X2
STOP
-
- In order to generate information from data items, a set of processing activities have to be performed on the data items in a specific sequence depending on the desired result. Draw a well labeled diagram to illustrate data processing cycle. (2 marks)
- A data entry clerk experiences some common errors when typing. Most of the time, she finds that:
- After every calculation, the result is less than the expected number of digits required e.g. 345.7896543 the result is given as 345.789.
- Different characters are typed wrongly, for example instead of typing 12873457 she types 128734S7. Identify the two types of errors commonly experienced by the clerk during data processing in (i) and (ii) above respectively. (2 marks)
- State two ways a user can ensure data accuracy is maintained during data processing. (2 marks)
-
- State three advantages of a computerized filing system as used in data processing. (3 marks)
- State two disadvantages of a serial file organization method in computing. (2 marks)
- Differentiate between distributed processing and interactive processing modes; stating one application area of each.
(4 marks)
-
- Write the following acronyms in full as used in operating systems.
- GUI - (½ mark)
- WIMP- (½ mark)
- State three factors considered when choosing an operating system for use in a computer. (3 marks)
- An operating system manages and organizes a computer system using the following structures: File, Folder and Drive. State the meaning of the underlined items respectively. (3 marks)
-
- Differentiate between error handling and interrupt handling as used in operating systems. (2 marks)
- State three reasons why most network technicians prefer using command line operating systems to configure networking equipment. (3 marks)
- Disk management is one important aspect in secondary storage in computer systems. Explain the following tools used by an operating system to manage disks in the computer. (3 marks)
- Formatting
- Partitioning
- Defragmentation
- Write the following acronyms in full as used in operating systems.
-
- Define the following terms as used in networking. (3marks)
- Network
- Intranet
- Browser
- The World Health Organization is global entity that deals with health issues around the world. It has computer networks linking its regional and continental offices using internet. State two importance of the Internet to such organization. (2 marks)
- Mr. Zuma, the Principal of a school wishes his school to have an internet connection in a bid to improve its service delivery. Mention four internet connectivity requirements that must be present to enable the connection. (2 marks)
- Explain the following as used in e-mail:
- Inbox- (1 mark)
- Drafts-. (1 mark)
-
- Failure of information systems is a major concern in the security of data in computing systems. State two causes of such failure. (2 marks)
- Explain the following computer crimes.
- Fraud (1 mark)
- Industrial espionage (1 mark)
- Excluding passwords, state two other security control measures used to guard against unauthorized access to computers in a network. (2 marks)
- Define the following terms as used in networking. (3marks)
-
- Convert the 1010.0112 to decimal equivalent. ( 3 marks)
- Perform the following number system conversions. (3 marks)
- 342.258 to binary.
- 50310 to hexadecimal
- Compute the binary arithmetic given below: (3 marks)
10111 + 10001 + 101 - Using 8-bit notation, perform the twos Complement of 2510 -1510, leaving your answer in binary. (4marks)
MARKING SCHEME
- Name the two common types of system units and differentiate them. (2 marks)
- Tower
- Desktop
- Desktop -the monitor is placed on top of the system unit. The tower types the monitor rests on the table
- Define the following characteristics of a computer system. (2 marks)
- Versatile- Computers are flexible in that they can be used to carry out different types of activities such as typing, calculations and playing music.
- Reliable –Computers are more reliable because they do not get tired or bored in the processing repetitive activities
- State any three types of computer programme documentation. (3marks)
- User oriented
- Operator oriented
- Programmer oriented
- Name any three effects of ICT on health. (3marks)
- Eye strain injury
- Repetitive strain injury
- Electromagnetic injury
- List one function of a bridge in computer network
- Reduce traffic by dividing a busy network into segments
- Expand size of network segment
- Address filtering (determining which segment is appropriate for the message to be delivered to)
-
- Convert 11110001101112 to its octal equivalent (1mk)
- 170678
- Convert 512.258 to its base 10 equivalent. (2mks)
- 330.32812510
- Convert 11110001101112 to its octal equivalent (1mk)
- With an aid of a diagram, differentiate between selection control structure and iteration control structure. (4mks)
Selection
Looping -
- Auki company is in the process of computerizing its services. List four measures that should be put into consideration to protect the users in their computerized areas. (2 marks)
- Power cables should be insulated
- Providing standard furniture
- Proper ventilation
- Painting the wall with less reflective paints.
- Overcrowding should be avoided.
- Give two reasons why powder and liquid extinguishers are not recommended unlike gaseous extinguishers. (2 marks)
- Liquid –based extinguisher may cause rusting and corrosion of computer components
- Powder particles may increase friction, clogging and wearing of movable computer parts
- Auki company is in the process of computerizing its services. List four measures that should be put into consideration to protect the users in their computerized areas. (2 marks)
- Without proper marketing, a business cannot survive in a competitive environment hence computers are being used in a number of ways to enhance marketing. List any three ways of ensuring this is affected. (3 marks)
- Electronic Commerce or e-business
- Electronic presentation
- Advertising
- Describe the following terms as used in computers. (3 marks)
- Tab Key- It is used to move the cursor at set horizontal intervals on the same line such as 0.5inch,1.0 inch etc.
- Space bar- It is used to insert spaces between characters on words when typing
- Clicking- Pressing and releasing the left mouse button once. A click often selects an Icon or Menu.
- Control unit is an essential component of the CPU. Describe the functions of the control unit. (2marks)
- The control unit is responsible for coordinating all the activities of the C.P.U
- To coordinate these activities, the control unit uses a system clock that sends command signals
-
- Differentiate between buffers and Registers. (2 marks)
- Buffers are special memories that are found in input/output devices. Input data are held in the input buffer while processed output is held in output buffer.
- A register is located inside the microprocessor hold one piece of data at a time one inside the C.P.U e.g. Accumulator, Instruction Register, Address Register and storage register
- Speech recognition devices are used to capture natural sound and convert the input into digital form. State two problems related to speech recognition devices. (2 marks)
- Recognition rate is slow –the number of words in English and the number of words which can be said at a given point (known as branching factor) mean that response rates are still relatively slow.
- Limited vocabularies –most systems are still limited to words in isolation; connected speech is much harder to get right than segmented speech. A computer may not respond to a voice command that has speech related problems like accents, Inflations and varying tones.
- Speaker variability–The speed, pitch, range, rhythm. Intonation, loudness and pronunciation of an individual can vary (especially if they a have a cold).
- Homophones –Some words e.g. see and sea, sound the same.
- Problems of speech context –A computer cannot understand different contexts and meanings of speech because it is ‘literal minded’.
- Background noise –Can upset voice input without a shielded mouthpiece on the microphone.
- Differentiate between buffers and Registers. (2 marks)
- Define Solid-state storage and give two examples. (2 marks)
- A non-volatile storage that employ integrated circuits rather than mechanical, magnetic or optical technology. They are referred to solid state because they do not have movable parts in its read/write storage mechanism.
-
- Explain how a pixel affects the resolution of a monitor. (1 mark)
- A pixel is the smallest unit of a digital image or graphic that can be displayed and represented on a digital display device. The higher the number of pixel, the clearer and excellent images formed on the screen. Less pixel results to less clear and poorer display on the screen.
- List two types of computer output on microform (COM). (2 marks)
- Microfiche
- Microfilm
- Explain how a pixel affects the resolution of a monitor. (1 mark)
-
- Give three advantages of using ATM cards. (3marks)
- It is secure
- It is convenient since services are available to customers at any time
- It allows for personal enquires
- Differentiate between pasteboard and master page as used in DTP (2 marks)
- Pasteboard: The background that lies behind your document. It is a convenient space to put things if you need to move text or images between pages. You can also place items on the pasteboard until you decide where to position them on the page. Any text or images that you place on the pasteboard won't be printed.
- Master page: A page used in designing the general layout that will be replicated in all other pages in the publication.
- Give three advantages of using ATM cards. (3marks)
SECTION B (60 Marks)
-
- State two advantages and two disadvantages of high level programming language (2 Marks)
- Advantages of high level programming
- High level languages are machine independent hence portable
- High level languages are user friendly
- They are easy to learn
- High level language programs are easy to debug
- They are more flexible hence they enhance the creativity of the programmer thus increasing productivity
- Disadvantages of high level programming
- High level languages are executed much slower than low level programming languages
- High level languages have to be translated into machine code before execution
- One instruction translates into several machine code instructions hence requires more storage space.
- They do not make efficient use of computer memory and the processor
Or any other correct response
Advantage @ ½ Mark
Disadvantage @ ½ Mark
Total = (2 X ½ Mark) + (2 X ½ Mark) = 2mrks
- State three situations when REPEAT .. UNTIL structure can be used in writing a program
- When the instructions are to be executed at least once
- When the number of loops is not known at the beginning of the program
- When the instructions are to be executed if the condition is false
Or any other correct response Situation @ 1 Mark Total = 3 X 1 Mark = 3 Marks
- The roots of the equation ax2 + bx + c = 0 are given by the formula
Study the pseudocode below and draw a flowchart./
Start/ stop @ ½ Mark Input @ ½ Mark
Evalute D @ ½ Mark 2 decisions @ 1
Mark Process @ 1 Mark Logic @ 1
Mark Output @ ½ Mark
Total = ½ + ½ + ½ + 1 + 1 + 1 + ½ = 5 Marks
- State two advantages and two disadvantages of high level programming language (2 Marks)
-
- In order to generate information from data items, a set of processing activities have to be performed on the data items in a specific sequence depending on the desired result. Draw a well labeled diagram to illustrate data processing cycle. (2 marks)
- A data entry clerk experiences some common errors when typing. Most of the time, she finds that:
- After every calculation, the result is less than the expected number of digits required e.g. 345.7896543 the result is given as 345.789.
- Different characters are typed wrongly, for example instead of typing 12873457 she types 128734S7.
Identify the two types of errors commonly experienced by the clerk during data processing in (i) and (ii) above respectively.
(2 marks)- Truncation error
- Misreading error
- State two ways a user can ensure data accuracy is maintained during data processing. (2 marks)
- Using modern data capture devices (direct data capture) such as barcode readers, optical character readers, digital cameras etc., which capture/enter data with minimum user involvement.
- Design user interfaces that minimizes chances of invalid data entry.
- Double entry checks
- Use of error detection and correction software when transmitting and processing data.
- Use of automated data verification and validation routines in the data processing system.
-
- State three advantages of a computerized filing system as used in data processing. (3 marks)
- information takes up much less space than the manual filing
- it is much easier to update or modify information
- it offers faster access and retrieval of data
- It enhances data integrity and reduces duplication
- It enhances security of data if proper care is taken to secure it.
- State two disadvantages of a serial file organization method in computing. (2 marks)
- It is cumbersome to access because you have to access all proceeding records before retrieving the one being searched.
- Wastage of space on medium in form due inter-record gaps in storage.
- It cannot support modern high speed requirements for quick record access.
- Differentiate between distributed processing and interactive processing modes; stating one application area of each. (4 marks)
- Distributed:
- Various geographically dispersed computers are linked by communication lines and all the computers linked belong to the same organization.
- The computers are located at various departments or business sites for the individual departments or the business site to be served individually by its own computer resources.
- All the branches have intelligent terminals (usually microcomputers) linked to a big computer at the head office. Data from the branches is sent to the master where it is processed.
- Interactive:
- Occurs if the computer & the terminal user can communicate with each other.
- It allows a 2-way communication between the user & the computer.
- As the program executes, it keeps on prompting the user to provide input or respond to prompts displayed on the screen.
- The user makes the requests and the computer gives the responses.
- The data is processed individually and continuously, as transactions take place and output is generated instantly according to the request made by user.
- Distributed:
- State three advantages of a computerized filing system as used in data processing. (3 marks)
- In order to generate information from data items, a set of processing activities have to be performed on the data items in a specific sequence depending on the desired result. Draw a well labeled diagram to illustrate data processing cycle. (2 marks)
-
- Write the following acronyms in full as used in operating systems.
- GUI - Graphical User Interface (½ mark)
- WIMP - Windows, Icons, Menus and Pointers/ pointing devices. (½ mark)
- State three factors considered when choosing an operating system for use in a computer. (3 marks)
- The hardware configuration of the computer e.g. Memory Capacity, processor speed & hard disk capacity.
- The application software intended for the computer.
- The user friendliness
- The documentation available
- The cost of the operating system.
- Reliability and security provided by the operating system.
- The number of processors & hardware it can support.
- The number of users it can support.
- The type of computers in terms of size and make. For example, some earlier Apple computers would not run Microsoft Operating System.
- An operating system manages and organizes a computer system using the following structures:
File, Folder and Drive. State the meaning of the underlined items respectively. (3 marks)- Files
- A file is a collection of related data given a unique name for ease of access, manipulation and storage on a backing storage.
- Folder
- A named storage location where files are stored.
- A container of files.
- Also referred to as directories –Directories originate form a special directory called the root directory or folder.
- Drives
- A drive is a medium that is capable of storing and reading information that is not easily removed like a disk.
- Files
-
- Differentiate between error handling and interrupt handling as used in operating systems. (2 marks)
- Error handling
- The OS has many ways of reporting to the user of any errors that occur during program execution. It does this by monitoring the status of the computer system & performing error checks on both hardware and software.
- When the user makes an error, the OS through the Kernel determines the cause of the error, and prints diagnostic messages on the screen suggesting appropriate routines of how the error can be corrected.
- In case of a fatal error that cannot be corrected, the program will be suspended permanently. E.g., the user program will prematurely terminate when it encounters an illegal operation, such as, dividing a no. by 0 or if it attempts to read a data file that had not been opened.
- Interrupt handling
- An Interrupt is a break from the normal sequential processing of instructions in a program.
- Each hardware device communicates to the processor using a special number called the Interrupt Request number (IRQ). Therefore, when an interrupt occurs, control is passed to the Kernel, which determines the cause of the interrupt. The processor stops executing the current program to wait for the corrective response of the user. Control is returned to the program that was interrupted once corrective action has been taken.
- Error handling
- State three reasons why most network technicians prefer using command line operating systems to configure networking equipment. (3 marks)
- A CLI can be a lot faster and efficient than any other type of interface.
- It is secure since the expert only knows the commands.
- A CLI requires less memory to use in comparison to other interfaces.
- A CLI doesn't require high graphics, hence a low-resolution monitor can be used.
- A CLI does not require Windows to run
- Differentiate between error handling and interrupt handling as used in operating systems. (2 marks)
- Disk management is one important aspect in secondary storage in computer systems. Explain the following tools used by an operating system to manage disks in the computer. (3 marks)
- Formatting
- Writing electronic information (tracks and sectors) on the disk so that the computer can recognize the disk as a valid storage device and data can be stored.
- The formatting process sets up a method of assigning addresses to the different areas. It also sets up an area for keeping the list of addresses. Without formatting there would be no way to know what data is where.
- Partitioning
- The act or practice of dividing the storage space of a hard disk drive into separate data areas known as partitions.
- Defragmentation
- Sometimes called defragging or disk optimization is a software-controlled operation that reduces the amount of fragmentation in file systems by moving the scattered parts of files so that they once again are contiguous (attached).
- The OS does this by physically organizing the contents of the disk to store the pieces of each file close together and contiguously (elements of memory are said to be contiguous if they are adjacent to one another and appear to be connected).
- Formatting
- Write the following acronyms in full as used in operating systems.
-
- Define the following terms as used in networking. (3marks)
- Network
- A collection 2 or more computers connected together using transmission media (e.g., telephone cables, or Satellites) for the purpose of communication and sharing of resources.
- Intranet
- Internal corporate network that uses the infrastructure of the Internet and the World Wide Web.
- Browser
- A browser (short for web browser) is a computer program/software that accesses webpages and displays them on the computer screen. It is the basic software that is needed to find, retrieve, view and send information over the internet.
- Network
- The World Health Organization is global entity that deals with health issues around the world. It has computer networks linking its regional and continental offices using internet. State two importance of the internet to such organization. (2 marks)
- Communication with other organizations, with your members, with your staff, with your supporters and donors through e-mails, messenger, web pages, mail lists, web site message boards. The Internet greatly offers rapid communication on a global scale. It even delivers an integrated multimedia entertainment that any other mass medium cannot offer.
- Publishing your message to the world using online books, journals, press releases, workshops, conferences, lectures. Websites with conference proceedings, PDF (Portable Document Format) files of your publications, blogs, newsfeeds etc. support publishing.
- Customer support - the people you are helping through your organization. It can help them when you aren't there: email, messenger, web pages, mail lists, and web site message boards. With video-conferencing, podcasting and other great web tools, you can even have workshops and classes online.
- Research on news, issues, papers and literature relevant to your cause. Use of search engines to find materials world-wide, mail lists etc.
- Leisure activities –e.g. online games, videos or music.
A place to do business and many other commercial activities. E.g. e-bay, amazon.com, etc.
- Mr. Zuma, the Principal of a school wishes his school to have an internet connection in a bid to improve its service delivery. Mention four internet connectivity requirements that must be present to enable the connection. (2 marks)
- Transmission/Telecommunication/Network media
- Data Terminal Equipment - A TCP/IP enabled computer with a web browser.
- An account with an Internet Service Provider (ISP).
- Networking equipment such as a modem, router or switch to connect the computer transmission media.
- Explain the following as used in e-mail:
- Inbox: Stores incoming mails (1 mark)
- Drafts: Stores a saved copy of e-mails (usually composed but unsent) for later use. (1 mark)
-
- Failure of information systems is a major concern in the security of data in computing systems. State two causes of such failure. (2 marks)
- Hardware failure due to improper use.
- Unstable power supply as a result of brownout or blackout and vandalism.
- Network breakdown
- Natural disaster
- Program failure/crash
- Explain the following computer crimes.
- Fraud (1 mark)
- Fraud is the use of computers to conceal information or cheat other people with the intention of gaining money or information.
- Industrial espionage (1 mark)
- Involves spying on a competitor to get or steal information that can be used to finish the competitor or for commercial gain. The main aim of espionage is to get ideas on how to counter by developing similar approach or sabotage.
- Fraud (1 mark)
- Excluding passwords, state two other security control measures used to guard against unauthorized access to computers in a network. (2 marks)
- Audit trails
- Firewalls
- Proxy servers
- Log files/security monitors
- Encryption
- User access levels/Multilevel access
- Biometric security
- Failure of information systems is a major concern in the security of data in computing systems. State two causes of such failure. (2 marks)
- Define the following terms as used in networking. (3marks)
-
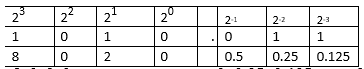
- Convert the 1010.0112 to decimal equivalent. ( 3 marks)
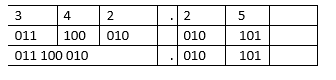
8+ 0 + 2 + 0 0 + l0.25 + 0.125 Ans = 10.37510 - Perform the following number system conversions. (3 marks)
- 342.258 to binary.
Ans = 11100010.0101012 - 50310 to hexadecimal (3 marks)
Ans = 1F7
- 342.258 to binary.
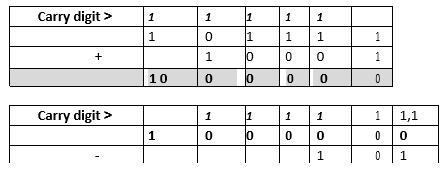
- Compute the binary arithmetic given below: (3)
10111 + 10001 + 101
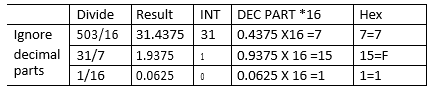
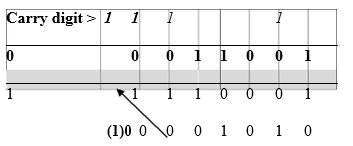
Ans = 111011 - Using 8-bit notation, perform the twos complement of 2510 -1510, leaving your answer in binary. (4 marks)
25 = 00011001
15 = 00001111
Ones complement/Bitwise NOT 15 = 11110000
Twos complement 15 (11110000 + 1) = 11110001
Add the binary of 25 to the twos complement of 15 i.e. 00011001 + 11110001
Ignore overflow bit. Ans = 00001010
- Convert the 1010.0112 to decimal equivalent. ( 3 marks)
Download Computer Studies Paper 1 Questions and Answers - Form 4 Term 3 Opener Exams 2023.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students