- This paper consists of TWO sections; A and B.
- Answer ALL questions in section A.
- Answer question 16 and any other THREE questions from section B.

Questions
SECTION A (40 marks)
Answer ALL the questions in the section in the spaces provided.
- Describe the following input/output terms as used in computer systems. Give an example for each (3marks)
- Read
- Write
- Using relevant examples distinguish between a formula and function. (3marks)
- A publisher intends to use a desktop publishing programme to create a publication which is to have many graphics. State three ways in which the graphics may be acquired for this purpose. (3 marks)
- The management of an organisation intends to purchase a printer. State three factors that they should consider during the purchase (3 marks)
- State three reasons why it is important to define data types of fields in a database correctly. (3 marks)
- An engineering company requires a computer system to design roads and bridges. (2 marks)
Explain one suitable choice for:- output device;
- software.
- State three circumstances under which the use of wireless communication would be preferred in data communication. (3 marks)
- Headache, back and neck pain may result from the use of computers. State how each of them can be minimized (2 marks)
- Headache
- Back & Neck Pain
- Explain the importance of each of the following in word processing:
- tab stops; (2 marks)
- Section breaks. (2 marks)
- State three problems associated with using e-mail technology for communication (3 marks)
- State two ways in which each of the following can be prevented
- Software errors (1 mark)
- Computer fraud (1 mark)
- Differentiate between analogue data and digital data as used in computers (2 marks)
- State four properties that an operating system displays about a file (2 marks)
- State the functions of each of the following keys on the computer keyboard (2 marks)
- backspace;
- insert (ins)
- Give three file organization methods in a computer (3 marks)
-
- State three ways in which a programmer can make program code easy to fol1ow (3 marks)
- Study the flowchart below and use it to answer the questions that follows;
- State the output of the above program flowchart for the inputs given below (3 Marks)
Amount = 15,000, 14,000 and 23,000 respectively - State the purpose of the flowchart (1 Mark)
- Write a pseudocode for the flowchart in question (16. c) above (8 Marks)
- State the output of the above program flowchart for the inputs given below (3 Marks)
-
- Interpret each of the following spreadsheet formula:
- = countif(A2:A9, “>=E7”) (2 marks)
- =sumif(B2 :B10, “WP”, D3 :D11) (2 marks)
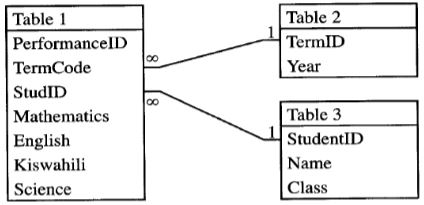
- The figure below shows relationships between tables in a database.
Identify two primary and two foreign keys used in the relationship. (4 marks) -
- Convert the hexadecimal number C7D16 to its equivalent decimal number (2 Marks)
- Using the twos compliment and 8-bit notation subtract 27 from 12 leaving your answer in binary notation (5 Marks)
- Interpret each of the following spreadsheet formula:
-
- Explain three circumstances under which observation method may be preferred during data collection (6 marks)
- Describe each of the following types of maintenance
- Perfective; (2 marks)
- Corrective; (2 marks)
- Adaptive. (2 marks)
- Name three approaches that may be used to replace an old system with a new computerized system (3 marks)
-
- With the aid of a diagram, describe the time sharing mode in computer data processing (5 marks)
- A company’s management has opted to use computers to process data. State four factors that the management needs to consider when selecting the company data processing mode. (4 marks)
- Describe each of the following validation checks as used in data processing
- Preserve check (2 marks)
- Data type check (2 marks)
- Check digit (2 marks)
-
- State the function of each of the following
- Network Interface Card (1 mark)
- Modem (1 mark)
- Repeater (1 mark)
- Crimping tool (1 mark)
- State any two reasons why the fibre optic cable is preferred for data transmission over the other cables (2 marks)
- State three functions of networking operating systems other than providing network security. (3 marks)
- A company has three branches X, Y and Z where X is the headquarter. The local area network (LAN) at X is directly connected to the LAN at Y and directly to the LAN at Z. Explain two benefits of having the LAN at Y also directly connected to the LAN at Z. (4 marks)
- The figure below shows a network topology . use it to answer the questions that follows:
- What is the name of the topology? (1 mark)
- What is the work of the part labelled T. (1 mark)
- State the function of each of the following

Marking Scheme
- Explain the following input/output terms as used in computer systems. Give an example for each (4marks)
- Read
- This is inputing data in a computer e.g. keyboard (Correct @1mk, Example @ 1mk)
- Write
- This is outputting data from a computer after processing. E.g output to a monitor (Correct @1mk, Example @ 1mk)
- Read
- Using relevant examples distinguish between a formula and function. (3marks)
- Formula is a mathematical expression that creates a relationship between cells to return a new value like = A2+A3+A4
- Functions are inbuilt formula that the user can quickly use instead of having to create a new each time a calculation has to be carried out like =sum(A2:A4)
(Correct difference @ 2mks)
(Examples each ½ mk)
- A publisher intends to use a desktop publishing programme to create a publication which is to have many graphics. State three ways in which the graphics may be acquired for this purpose. (3 marks)
- Using digital camera
- Scanning the graphics from other sources
- Downloading from the internet
- Drawing from scratch/Drawing tools
- Clip art
(correct @ 3mks)
- The management of an organisation intends to purchase a printer. State three factors that they should consider during the purchase (3 marks)
- Volume of work to be printed.
- Maintenance cost below e.g. consumables like toners should be affordable.
- Speed of printing.
- Type of work to be printed; type of paper, paper size/user needs /range of capability.
- Type of printout whether colour is required or not.
- Compatibility with the existing hardware
- Initial cost
- availability of in the market
(correct @ 3mks)
- State three reasons why it is important to define data types of fields in a database correctly. (3 marks)
- Memory use optimisation when the program is loaded;
- Assist in trapping errors during data input;
- So that appropriate computation can be performed;
- Increase speed of processing.
(correct @ 3mks)
- An engineering company requires a computer system to design roads and bridges. (2 marks)
Explain one suitable choice for:- Output device: A plotter because it prints large size drawings to high precision.
- software: A CAD software because it facilitates in the design of engineering drawings.
(correct @1mk each)
- State two circumstances under which the use of wireless communication would be preferred in data communication. (3mks)
- When the targetted recipients are many and diverse e.g. different platforms, devices, geographical locations.
- When the sender or receiver is mobile and it in practical to use wired media.
- When there is no space or it is inconvenient to lay cables e.g in a congested town.
- When the distance of travel is very big e.g extraterestial communication.
(correct @1mk each)
- Headache, back and neck pain may result from the use of computers. State how each of them can be minimized (2 marks)
- Headache
- Use of filters/antiglare
- Proper lighting
- Regular break
- Back & Neck Pain
- Proper/correct furniture for the computer
- Correct position of the screen
- Correct sitting posture
- Taking a break
(correct @2mks)
- Explain the importance of each of the following in word processing:
- tab stops; (2 marks)
- When tabs stops are set, they allow aligning of the text into columns
(correct @2mks)
- When tabs stops are set, they allow aligning of the text into columns
- Section breaks. (2 marks)
- Section breaks allow splitting of a document into different sections so that different formatting styles can be applied on different sections. (correct @2mks)
- tab stops; (2 marks)
- State three problems associated with using e-mail technology for communication (3 marks)
- Threats to privacy
- Organization “system admn” can snoop into peoples’ mails
- Email can be unsolicited/ spam mail
- Messages can be sent to masses of people without their consent
- Vulnerability to machine failure
- Emails can be overwhelming when many messages are received leading to email overload and going through each of them can be taxing
- Email can be faked
- Email attached can be a source of viruses
- Email technology not available to all/ Technology illiteracy
- Encourage illicit communication such as immoral behavior.
(correct @3mks)
- State two ways in which each of the following can be prevented
- Software errors (1 mark)
- Use of anti-virus software
- Update system frequently
- Purchase software from authentic sources
- Test the software before implementation
- Test syntax/logic
- Proper training
- Proper enactment of laws
(correct @1mk)
- Computer fraud (1 mark)
- Data encryption
- Password protection
- Audit trail
- Surveillance system
(correct @1mk)
- Software errors (1 mark)
- Differentiate between analogue data and digital data as used in computers (2 marks)
- Analogue data uses values that changes continuously between instances while digital data are values that change from one value to the next in step by step sequence
(correct @2mks)
- Analogue data uses values that changes continuously between instances while digital data are values that change from one value to the next in step by step sequence
- State four properties that an operating system displays about a file (2 marks)
- File size
- Date modifies
- File type
- File name
- Author
- Date created
- Time created
- Hidden
- Archived
(correct @2mks)
- State the functions of each of the following keys on the computer keyboard (2 marks)
- backspace;
- Moves the display cursor one position backwards, deletes the character at the position and shifts back the text after that position by one position (correct @1mk)
- insert (ins)
- When insert is selected, keys add characters to the screen at the cursor (insertion point) without deleting those already there. (correct @1mk)
- backspace;
- Give three file organization methods in a computer (3 marks)
- Serial (heap)
- Sequential
- Random
- Indexed sequential (correct @3mks)
-
- State three ways in which a programmer can make program code easy to fol1ow (3 marks)
- Using modules or short blocks of program/functions/procedures;
- Making internal documentation / comments;
- Using meaningful variable names and user words in the program;
- Using indent to represent nested statement:
- Using blank lines to separate blocks of code statement;
- Test formatting of reserved words e.g. bolding
- Study the flowchart below and use it to answer the questions that follows;
- State the output of the above program flowchart for the inputs given below (3 Marks)
- Amount = 15,000, 14,000 and 23,000 respectively
Balance Amount New Balance Output 34 000 15 000 19 000 "New Balance", balance 19 000 14 000 5 000 "New Balance", balance 5 000 23 000 -17 000 "Out of Cash"
- Amount = 15,000, 14,000 and 23,000 respectively
- State the purpose of the flowchart (1 Mark)
- The flowchart is used to check the account balance and allow withdrawal if the balance is more than 0. Withdrawal is done only three times
- Purpose @ 1 Mark
- Write a pseudocode for the flowchart in question (16. c) above (8 Marks)
- Start
Balance=34000
For count =1 to 3 do
Input amount
Balance = Balance – Amount
WHILE Balance>= 0 then
Print “New Balance”, Balance
COUNT = COUNT + 1
END WHILE
Print “out of cash”
End for
Print “limit reached”
Stop
SS- @1
INIT -@ 1
LOOP - @2
INPUT - @1
PROCESS- @1
OUTPUT - @1
LOGIC - @1
Start
Balance=34000
For count =1 to 3 do
Input amount
Balance = Balance – Amount
If Balance>= 0 then
Print “New Balance”, Balance
Else
Print “out of cash”
End if
End for
Print “limit reached”
Stop
START
COUNT =1
BALANCE = 34500
REPEAT
IF COUNT <=3 THEN
INPUT AMOUNT
BALANCE=BALANCE-AMOUNT
PRINT “NEW BALANCE” BALANCE
COUNT=COUNT + 1
UNTIL BALANCE <0
PRINT “OUT OF CASH”
ELSE
PRINT “LIMIT REACHED”
END IF
STOP
- Start
- State the output of the above program flowchart for the inputs given below (3 Marks)
- State three ways in which a programmer can make program code easy to fol1ow (3 marks)
-
- Interpret each of the following spreadsheet formula:
- = countif(A2:A9, “>=E7”) (2 marks)
- Count those value in the range A2 :A9 with values greater than or equal to the value in cell E7
(correct @2mks)
- Count those value in the range A2 :A9 with values greater than or equal to the value in cell E7
- =sumif(B2 :B10, “WP”, D3 :D11) (2 marks)
- Sum the values in the cell range D3 : D11 for records whose corresponding values in cell range B3 : B11 equals to “WP”
(correct @2mks)
- Sum the values in the cell range D3 : D11 for records whose corresponding values in cell range B3 : B11 equals to “WP”
- = countif(A2:A9, “>=E7”) (2 marks)
- The figure below shows relationships between tables in a database.
Identify two primary and two foreign keys used in the relationship. (4 marks)- Primary keys
- TermiD
- StudentiD
- Foreign keys
- TermCode
- StudID
-
- Convert the hexadecimal number C7D16 to its equivalent decimal number (2 Marks)
- C – 12
7 – 7
D – 13
(12*16*16) + (7*16) + 13
3072 + 112 + 13 = 319710
OR
C-1100
7-0111
D-1101
C7D16 = 1100011111012
(1*211) + (1*210) + (1*26) + (1*25) + (1*24) + (1*23) + (1*22) + (1*20)
2048 + 1024 + 64 + 32 + 16 + 8 + 4 + 1
= 319710
- C – 12
- Using the twos compliment and 8-bit notation subtract 27from 12 leaving your answer in binary notation (5 Marks)
- 27 – 11011– 00011011
12 – 1100 – 00001100
1s C of 27 – 11100100
+1
2s C of 27 – 11100101
+ 00001100
11110001
- 27 – 11011– 00011011
- Convert the hexadecimal number C7D16 to its equivalent decimal number (2 Marks)
- Interpret each of the following spreadsheet formula:
-
- Explain three circumstances under which observation method may be preferred during data collection (6 marks)
- When the subjects that are being observed need not be made aware of the fact
- When there is need to collect data without interfering with the working of the subjects
- When there is need to directly see what subjects do rather than rely on what they tell you
- When nature of data can only be collected via observation e.g. traffic flow
- When collecting data in situation that subjects may be unwilling to give information
- Describe each of the following types of maintenance
- Perfective; (2 marks)
- Type of maintenance done to make the system better in its operation e.g. adding a module in a system
- Corrective; (2 marks)
- Type of maintenance done to correct errors in the system e.g. wrong results during addition
- Adaptive. (2 marks)
- Type of maintenance that is done to make the system to adapt the changing technology e.g. Changing the system because of new operating system
- Perfective; (2 marks)
- Name three approaches that may be used to replace an old system with a new computerized system (3 marks)
- Direct approach
- Parallel approach
- Phased approach
- Pilot approach
- Explain three circumstances under which observation method may be preferred during data collection (6 marks)
-
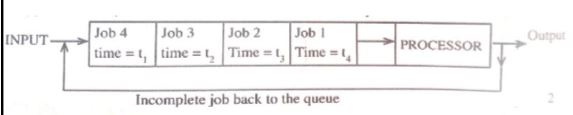
- With the aid of a diagram, describe the time sharing mode in computer data processing (5 marks)
- This is a processing mode in which a central processor serves two or more users with different requirements. The processor time is divided equally among the tasks in the queue. A user whose task requirements are more than is apportioned is sent back to the queue. For example, four jobs requiring times t1, t2, t3 and t4 to complete is apportioned equal time in each round until when they are done
- This is a processing mode in which a central processor serves two or more users with different requirements. The processor time is divided equally among the tasks in the queue. A user whose task requirements are more than is apportioned is sent back to the queue. For example, four jobs requiring times t1, t2, t3 and t4 to complete is apportioned equal time in each round until when they are done
- A company’s management has opted to use computers to process data. State four factors that the management needs to consider when selecting the company data processing mode. (4 marks)
- The optimization of processing time
- The time factor required for decision arising from the processed data
- The ease of development, use and maintenance
- The control over the resources e.g. files, I/O devices etc.
- The need for the shared resources among several users who may afford purchasing their own facilities as in time sharing configuration
- The volume of work involved
- The cost of acquiring the relevant hardware, software, media etc. and the cost of maintenance
- The nature of the task to be processed.
- Describe each of the following validation checks as used in data processing
- Preserve check (2 marks)
- It is a measure that ensure that the data item is in its original status
- Data type check (2 marks)
- It is a measure that ensures that correct data type is entered for each field
- Check digit (2 marks)
- This is a number calculated by the computer to make sure that the other numbers in the sequence have been entered properly.
- Preserve check (2 marks)
- With the aid of a diagram, describe the time sharing mode in computer data processing (5 marks)
-
- State the function of each of the following
- Network Interface Card (1 mark) - A device that creates a physical link to the computer and the transmission media
- Modem (1 mark) - modem converts a signal from digital to analog form for the purpose of transmission over the transmission media
- Repeater (1 mark) - receives a signal from one section of a network, clean it to remove any distortion, boosts/amplifies it and sends it to another section
- Crimping tool (1 mark) - Used to terminate cables / used to attach RJ 45 to cable
- State any two reasons why the fibre optic cable is preferred for data transmission over the other cables (2 Marks)
- Fiber optic transmission is faster. ...
- Fiber optic transmission can cover greater distances. ...
- Fiber optic cables are impervious to electromagnetic interference (EMI) ...
- Save space and enhance cable management. ...
- Fiber optics are future-proof.
- Extremely High Bandwidth:
- Low Security Risk:
- Light Weight:
- State three functions of networking operating systems other than providing network security. (3 marks)
- Provide access to network resources;
- Supporting network services like protocols;
- Support communication;
- Respond to requests from applications;
-
- A company has three branches X, Y and Z where X is the headquarter. The local area network (LAN) at X is directly connected to the LAN at Y and directly to the LAN at Z. Explain two benefits of having the LAN at Y also directly connected to the LAN at Z. (4 marks)
- Speed of communication between Y and Z is increased since the traffic between the two branches can be re-routed through the link YZ;
- If either XZ or XY is down, the three branches can still communicate;
- If the HQ systems fail, the two branches Y and Z can communicate using this link.
- The figure below shows a network topology . use it to answer the questions that follows:
- What is the name of the topology? (1 mark)
- Bus topology
- What is the work of the part labelled T. (2 marks)
- Terminator in a backbone is used to prevent data signal from bouncing back/absorb signals.
- What is the name of the topology? (1 mark)
- State the function of each of the following
Download Computer Studies Paper 1 Questions and Answers - Bunamfan Cluster Pre Mock Exam 2022.
Tap Here to Download for 50/-
Get on WhatsApp for 50/-
Why download?
- ✔ To read offline at any time.
- ✔ To Print at your convenience
- ✔ Share Easily with Friends / Students